大家可能都知道k8s默认有个ui界面,但是呢,一般都使用的是1版本的,今天给大家部署的是2版本页面
完整部署文件 Github 地址:https://github.com/my-dlq/blog-example/tree/master/kubernetes/kubernetes-dashboard2.0.0-deploy
接下来开始部署
部署一共分5个步骤:
1、创建RBAC
2、创建configmap和secret
3、创建dashboard
4、创建metrics-scraper
5、创建访问的serviceaccount
我吧文件直接都配好了放到了百度网盘,你们可以直接下载解压使用
链接:https://pan.baidu.com/s/1wdp-zJE6FqpuJdGYgyESmg
提取码:stzw
完成之后就可以通过web页面访问了
这里使用的是kubeadmin部署的,如果是二进制,需要修改api-server的参数不然无法支持metrics-server服务的
1、创建 Dashboard RBAC 部署文件
cat > k8s-dashboard-rbac.yaml <apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
rules:
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"] - apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"] - apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"] -
apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules: -
apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects: -
kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-systemapiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects: - kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
EOF
部署
kubectl apply -f k8s-dashboard-rbac.yaml
2、创建 ConfigMap、Secret
cat >k8s-dashboard-configmap-secret.yaml<apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kube-system
type: Opaque
data:
csrf: ""
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kube-system
type: Opaque
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kube-system
EOF
3、部署 Dashboard Config & Secret
kubectl apply -f k8s-dashboard-configmap-secret.yaml
创建 Dashboard Deploy 部署文件
cat >k8s-dashboard-deploy.yaml<
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort
ports:
-
port: 443
targetPort: 8443
nodePort: 31001
selector:
k8s-app: kubernetes-dashboardkind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.0.0-rc3
ports:- containerPort: 8443
protocol: TCP
args: - --auto-generate-certificates
- --namespace=kube-system #设置为当前namespace
volumeMounts: - name: kubernetes-dashboard-certs
mountPath: /certs - mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- containerPort: 8443
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs - name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
tolerations: - key: node-role.kubernetes.io/master
effect: NoSchedule
EOF
- name: kubernetes-dashboard
部署 Dashboard Deploy
kubectl apply -f k8s-dashboard-deploy.yaml
4、创建 Dashboard Metrics 部署文件
cat >k8s-dashboard-metrics.yaml<
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kube-system
spec:
ports:
-
port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraperkind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
annotations:
seccomp.security.alpha.kubernetes.io/pod: 'runtime/default'
spec:
containers:- name: dashboard-metrics-scraper
image: kubernetesui/metrics-scraper:v1.0.3
ports:- containerPort: 8000
protocol: TCP
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:- mountPath: /tmp
name: tmp-volume
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
serviceAccountName: kubernetes-dashboard
nodeSelector:
"beta.kubernetes.io/os": linux
tolerations:
- mountPath: /tmp
- containerPort: 8000
- key: node-role.kubernetes.io/master
effect: NoSchedule
volumes: - name: tmp-volume
emptyDir: {}
- name: dashboard-metrics-scraper
EOF
部署 Dashboard Metrics
kubectl apply -f k8s-dashboard-metrics.yaml
5、创建 Dashboard ServiceAccount 部署文件
cat > k8s-dashboard-token.yaml<
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: admin
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io
subjects:
-
kind: ServiceAccount
name: admin
namespace: kube-systemapiVersion: v1
kind: ServiceAccount
metadata:
name: admin
namespace: kube-system
labels:
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
EOF
部署访问的 ServiceAccount
kubectl apply -f k8s-dashboard-token.yaml
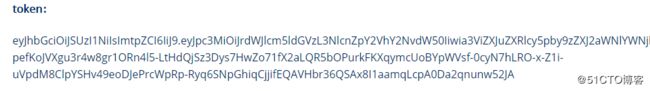
获取 Token
kubectl describe secret/$(kubectl get secret -n kube-system |grep admin|awk '{print $1}') -n kube-system
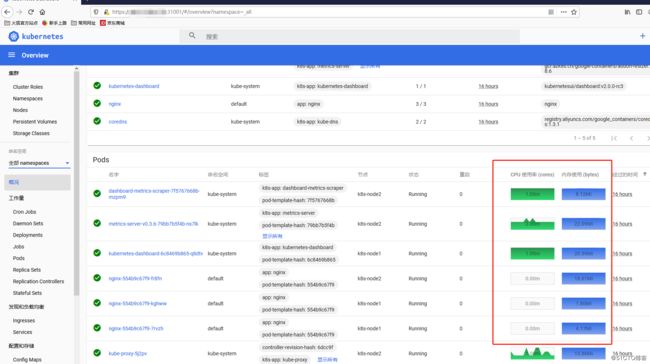
好了2版本的web-ui就完成了
有什么问题可以私信我哈