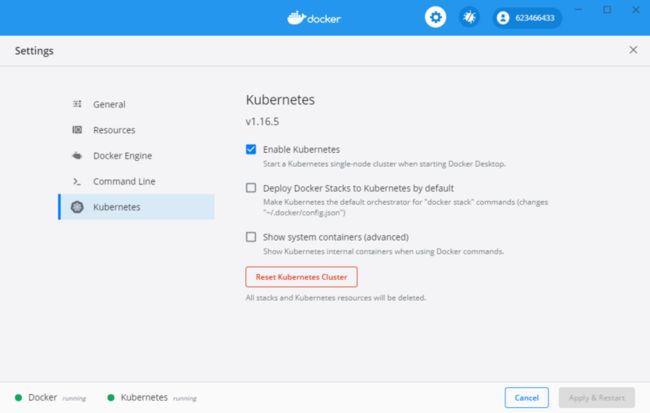
安装docker for desktop
到docker下载对应系统的版本,然后点击下一步安装即可
配置镜像下载源
{
"registry-mirrors": [
"https://dockerhub.azk8s.cn",
"https://registry.docker-cn.com"
],
"insecure-registries": [],
"debug": true,
"experimental": true
}启用kubernetes
上面的方式如果国内用户是无法安装的,国内用户请按照一下方式安装k8s:
- 下载k8s-for-docker-desktop
git clone https://github.com/AliyunContainerService/k8s-for-docker-desktop.git- 提前把Kubernetes需要的Images拉取下来
cd k8s-for-docker-desktop && .\load_images.ps1请使用powershell运行上面的命令,如果报一下错误:
.\load_images.ps1 : 无法加载文件 D:\k8s-for-docker-desktop\load_images.ps1,因为在此系统上禁止运行脚本。有关详细信息,请参阅 https:/go.microsoft.com/fwlink/?LinkID=135170 中的 about_Execution_Policies。上面报错的原因是系统禁止运行脚本,通过一下命令并输入Y开启此功能:
set-executionpolicy remotesigned再次运行.\load_images.ps1即可下载镜像。
- 开启k8s
至此k8s已经安装完成。
安装 Dashboard
通过k8s-for-docker-desktop提供的yml文件安装 Dashboard:
$ cd k8s-for-docker-desktop && kubectl apply -f kubernetes-dashboard.yaml
-- 输出
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
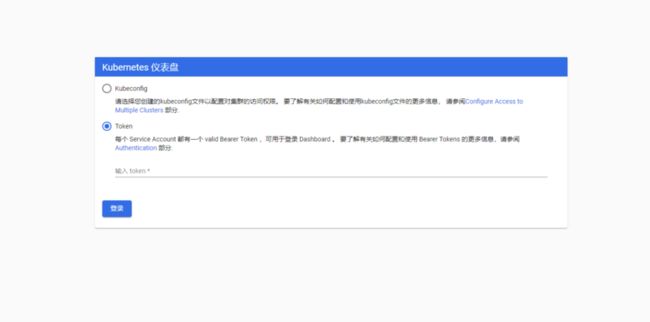
$ kubectl proxy访问dashboard:
http://localhost:8001/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy/#!/login创建 ServiceAccount
我们在本地创建一个 k8s-admin.yaml 文件,创建一个 ServiceAccount 和角色绑定关系,写入如下文件内容:
apiVersion: v1
kind: ServiceAccount
metadata:
name: dashboard-admin
namespace: kube-system
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: dashboard-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kube-system
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io启动服务:
$ kubectl apply -f k8s-admin.yaml获取管理员角色的 secret 名称:
$ kubectl get secrets -n kube-system | grep dashboard-admin | awk '{print $1}'
dashboard-admin-token-fz4wf获取token:
$ kubectl describe secret dashboard-admin-token-dknqx -n kube-system
Name: dashboard-admin-token-fz4wf
Namespace: kube-system
Labels:
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: d95abc09-da72-4535-8995-45590973534f
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ijd5a29rRWpIdFRjQnlJMWFvWjFjcUJCMHdHZ3RmdHIxaXFreERwQ1Z5b28ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tZno0d2YiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZDk1YWJjMDktZGE3Mi00NTM1LTg5OTUtNDU1OTA5NzM1MzRmIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.qaAyhD3H9w2Jum73eS04WUGOBRokxeIf_ujIl1cvIvm_hoRLV84W2_aBz5CkpOizwSJPekvVarNQcEe7np_9SxhUTXhPrZpJIbcVXWR8LnqR4HbnKvBTpR5uPPcjRCyHeNbrEF_NT3SjJdeFz1cK9tXIyt5StOc-3soVwcY8upVdLD-nbSV7VephjfnOLypiFO78T8pUc0sw-PlTEgQJa9ysnGaIIwvjEp7q5Ohhi5eBqTz3spLxJgW0S2ygohiKO5VuKsLe44mt7G7AF0U_1G6E0cJsJl5oaYpaZk3Apqqn8typyj29BDZ8jj02mPeFL3hbocghaoKWfSXknEI6Aw 如果已经熟悉了,可以直接通过组合命令直接获取 token 值:
$ kubectl describe secret dashboard-admin-token-dknqx -n kube-system | grep -E '^token' | awk '{print $2}'