91. kubeadm 安装k8s 1.15版
文章目录
- kubeadm 安装k8s 1.15版
- 环境要求:
- 1. 所有节点安装docker
- 2. 所有节点安装kubeadm
- 3. 使用kubeadm初始化k8s集群
- 4. node节点加入k8s集群
- 5. 为k8s集群配置网络插件
- 6. 为k8s集群配置dashboard服务
- 7. 访问dashboard
- 7.1 解决Google浏览器不能打开kubernetes dashboard方法
- 7.2 kubeconfig文件生成
kubeadm 安装k8s 1.15版
由于二进制安装的k8s: 步骤繁琐,于是就有大佬用ansibe和saltstack来简化二进制安装流程
ansible 一键自动化安装
saltstack 一键自动化安装
kubeadm安装k8s: 需要google官方的docker镜像,需要解决网络问题
环境要求:
| 机器名 | ip地址 | cpu和内存要求 |
|---|---|---|
| kubernetes-master | 10.0.0.24 | 2c2g(关闭swap) |
| kubernetes-node1 | 10.0.0.25 | 2c2g(关闭swap) |
1. 所有节点安装docker
1.配置yum源
curl -o /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-7.repo
wget -O /etc/yum.repos.d/docker-ce.repo https://download.docker.com/linux/centos/docker-ce.repo
2.更改docker源为国内源
sed -i 's+download.docker.com+mirrors.tuna.tsinghua.edu.cn/docker-ce+' /etc/yum.repos.d/docker-ce.repo
yum list docker-ce --showduplicates
3.安装docker并启动
yum install docker-ce -y
systemctl start docker && systemctl enable docker
2. 所有节点安装kubeadm
1.配置yum源
cat <<EOF > /etc/yum.repos.d/kubernetes.repo
[kubernetes]
name=Kubernetes
baseurl=https://mirrors.aliyun.com/kubernetes/yum/repos/kubernetes-el7-x86_64/
enabled=1
gpgcheck=0
repo_gpgcheck=0
gpgkey=https://mirrors.aliyun.com/kubernetes/yum/doc/yum-key.gpg https://mirrors.aliyun.com/kubernetes/yum/doc/rpm-package-key.gpg
EOF
2.安装并启动
yum install kubelet-1.15.5-0 kubeadm-1.15.5-0 kubectl-1.15.5-0 -y
systemctl enable kubelet && systemctl start kubelet
3. 使用kubeadm初始化k8s集群
1.所有节点操作
cat <<EOF > /etc/sysctl.d/k8s.conf
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
EOF
sysctl --system
2.永久关闭swap
swapoff -a
vim /etc/fstab
#UUID=72aabc10-44b8-4c05-86bd-049157d771f8 swap swap defaults 0 0
3.master节点操作
kubeadm init --kubernetes-version=v1.15.0 --image-repository registry.aliyuncs.com/google_containers --pod-network-cidr=10.244.0.0/16 --service-cidr=10.254.0.0/16
注意:如果自己导入的镜像;只需要执行下面的命令即可
[root@kubernetes-master opt]# docker load -i k8s_1.15.tar.gz
kubeadm init --kubernetes-version=v1.15.0 --pod-network-cidr=10.244.0.0/16 --service-cidr=10.254.0.0/16
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
4. node节点加入k8s集群
node节点操作:
将刚才master节点执行命令的返回复制到node执行;切记,别粘我博客的,不然抽你俩大耳刮子
[root@kubernetes-node1 ~]# kubeadm join 10.0.0.24:6443 --token 26wuk1.jw5jnqi6h630nqdi \
--discovery-token-ca-cert-hash
master节点验证查看
[root@kubernetes-master ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
kubernetes-master NotReady master 4m32s v1.15.5
kubernetes-node1 NotReady <none> 45s v1.15.5
5. 为k8s集群配置网络插件
1. 控制节点下载插件:
wget https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml
2. 修改网段范围为查看验证
kubectl create -f kube-flannel.yml
3. 查看所有pod
[root@kubernetes-master ~]# kubectl get all -n kube-system
NAME READY STATUS RESTARTS AGE
pod/coredns-bccdc95cf-gzjm5 1/1 Running 0 9m11s
pod/coredns-bccdc95cf-p9m4r 1/1 Running 0 9m11s
pod/etcd-kubernetes-master 1/1 Running 0 8m13s
pod/kube-apiserver-kubernetes-master 1/1 Running 0 8m23s
pod/kube-controller-manager-kubernetes-master 1/1 Running 0 8m12s
pod/kube-flannel-ds-amd64-chffd 1/1 Running 0 73s
pod/kube-flannel-ds-amd64-xd9w5 1/1 Running 0 73s
pod/kube-proxy-tnhkm 1/1 Running 0 5m44s
pod/kube-proxy-wxqvv 1/1 Running 0 9m11s
pod/kube-scheduler-kubernetes-master 1/1 Running 0 8m5s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kube-dns ClusterIP 10.254.0.10 <none> 53/UDP,53/TCP,9153/TCP 9m26s
NAME DESIRED CURRENT READY UP-TO-DATE AVAILABLE NODE SELECTOR AGE
daemonset.apps/kube-flannel-ds-amd64 2 2 2 2 2 <none> 73s
daemonset.apps/kube-flannel-ds-arm 0 0 0 0 0 <none> 73s
daemonset.apps/kube-flannel-ds-arm64 0 0 0 0 0 <none> 73s
daemonset.apps/kube-flannel-ds-ppc64le 0 0 0 0 0 <none> 73s
daemonset.apps/kube-flannel-ds-s390x 0 0 0 0 0 <none> 73s
daemonset.apps/kube-proxy 2 2 2 2 2 beta.kubernetes.io/os=linux 9m26s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/coredns 2/2 2 2 9m26s
NAME DESIRED CURRENT READY AGE
replicaset.apps/coredns-bccdc95cf 2 2 2 9m11s
4. 查看集群状态
[root@kubernetes-master ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
kubernetes-master Ready master 3h43m v1.15.5
kubernetes-node1 Ready <none> 3h35m v1.15.5
=====================================================================================
如果出现装错机器的话;在要删除的节点上,重置所有kubeadm安装状态:
kubeadm reset
重置过程不会重置或清除iptables规则或IPVS表。如果您希望重置iptables,则必须手动进行:
iptables -F && iptables -t nat -F && iptables -t mangle -F && iptables -X
kubectl 命令补全参数(建议加入开机自启)
source <(kubectl completion bash)
6. 为k8s集群配置dashboard服务
serviceaccount 启动 代表k8s的认证机制 rbac role base access controller 基于角色的访问控制
serviceaccount 账户
role 角色
RoleBingding 角色绑定 授权
deployment:绑定了账户
secret:会自动生成密钥;给我们的dashboard服务使用
1. kubeadm安装k8s 1.15部署dashboard
wget https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
如果下载不下来的话,沾俺贴出来的配置:
===============================================================================================
[root@kubernetes-master dashboard]# cat kubernetes-dashboard.yaml
# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
# ------------------- Dashboard Secret ------------------- #
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
---
# ------------------- Dashboard Service Account ------------------- #
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
---
# ------------------- Dashboard Role & Role Binding ------------------- #
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
# Allow Dashboard to create 'kubernetes-dashboard-key-holder' secret.
- apiGroups: [""]
resources: ["secrets"]
verbs: ["create"]
# Allow Dashboard to create 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
verbs: ["create"]
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics from heapster.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard-minimal
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
---
# ------------------- Dashboard Deployment ------------------- #
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: registry.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
# ------------------- Dashboard Service ------------------- #
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30001
selector:
k8s-app: kubernetes-dashboard
===============================================================================================
2. 修改service类型为NodePort类型
vi kubernetes-dashboard.yaml +162
namespace: kube-system
spec:
type: NodePort #类型
ports:
- port: 443
targetPort: 8443
nodePort: 30001 #端口
......
修改镜像路径:112行
image: registry.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
3.创建dashboard资源
[root@kubernetes-master dashboard]# kubectl create -f kubernetes-dashboard.yaml
[root@kubernetes-master dashboard]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.254.0.10 <none> 53/UDP,53/TCP,9153/TCP 31m
kubernetes-dashboard NodePort 10.254.153.159 <none> 443:30001/TCP 31s
[root@kubernetes-master dashboard]# kubectl get pod -n kube-system -o wide
4. 若没有node标签;请执行以下命令给node节点打标签
[root@kubernetes-master dashboard]# kubectl get nodes --show-labels
NAME STATUS ROLES AGE VERSION LABELS
kubernetes-master Ready master 3h58m v1.15.5 beta.kubernetes.io/arch=amd64,beta.kubernetes.io/os=linux,kubernetes.io/arch=amd64,kubernetes.io/hostname=kubernetes-master,kubernetes.io/os=linux,node-role.kubernetes.io/master=
kubernetes-node1 Ready <none> 3h50m v1.15.5 beta.kubernetes.io/arch=amd64,beta.kubernetes.io/os=linux,kubernetes.io/arch=amd64,kubernetes.io/hostname=kubernetes-node1,kubernetes.io/os=linux
5. 打标签
[root@kubernetes-master dashboard]# kubectl label nodes kubernetes-node1 node-role.kubernetes.io/node=
node/kubernetes-node1 labeled
6. 查看集群
[root@kubernetes-master dashboard]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
kubernetes-master Ready master 3h59m v1.15.5
kubernetes-node1 Ready node 3h52m v1.15.5
7. 访问dashboard
7.1 解决Google浏览器不能打开kubernetes dashboard方法
解决方法:
[root@kubernetes-master ~]# mkdir key && cd key
1.生成证书
openssl genrsa -out dashboard.key 2048
openssl req -new -out dashboard.csr -key dashboard.key -subj '/CN=10.0.0.24'
openssl x509 -req -in dashboard.csr -signkey dashboard.key -out dashboard.crt
2.删除原有的证书secret
kubectl delete secret kubernetes-dashboard-certs -n kube-system
3.创建新的证书secret
kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kube-system
4.查看pod
kubectl get pod -n kube-system
5.删除pod,启动新pod生效
kubectl delete pod -n kube-system kubernetes-dashboard-7c697b776b-zph98
6. 编写yaml文件提升权限
1.创建文件
[root@kubernetes-master dashboard]# cat k8s-admin.yaml
kind: ClusterRoleBinding #角色绑定
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: admin
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
roleRef:
kind: ClusterRole
name: cluster-admin #全局资源角色,集群管理员
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: admin
namespace: kube-system
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin
namespace: kube-system
labels:
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
2. 创建管理员角色
[root@kubernetes-master dashboard]# kubectl create -f k8s-admin.yaml
3. 查看令牌
[root@kubernetes-master dashboard]# kubectl get secrets -n kube-system |grep admin
admin-token-phjfs kubernetes.io/service-account-token 3 23s
4. 查看详细令牌
[root@kubernetes-master dashboard]# kubectl describe -n kube-system secrets admin-token-phjfs
Name: admin-token-phjfs
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin
kubernetes.io/service-account.uid: 31871f01-d24c-4344-9d15-8a69e43a0d6e
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi1waGpmcyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjMxODcxZjAxLWQyNGMtNDM0NC05ZDE1LThhNjllNDNhMGQ2ZSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.DBLurwJxsToOC31b3OkxI10MFxM5m2EN2mgNJr9-lYwVVXa-6s5N5CEV00debTv83K5Ikgn7pl3D1OtFUeM1WdTkdse1Dlo7ID_NYcEswqYeFs_fcClGY1Bt9bt0Wsm0qGbajJSUkARnJ7LEewKAaRcLXoGiCCxym9ap-noqCofByP0sOdbwBAq-wRlYWgJkufc4LmvlsxMO9D9cWaOpxOnKNsKDnNZpmT15Yh-DBz32GRq4AltH9FX_a4z5rsVX6-ebG50Z5W_n2E9PkcTrovJ2ASLU7rF2SGTABQXE4JEDdlVTUemSYw7IZKAUeqMNgjxSkDfKL1peMsJvItmeqA
kubectl get serviceaccount -n kube-system
kubectl describe serviceaccount admin -n kube-system
kubectl describe secret admin-token-29977 -n kube-system
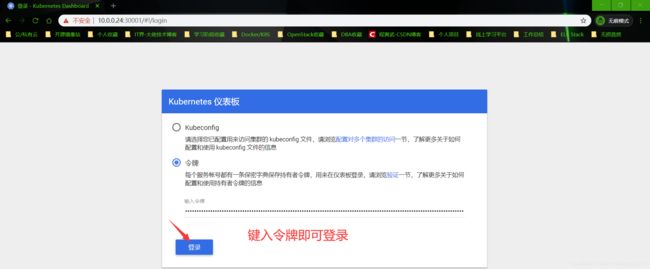
保存查看到的token密钥,就是登录dashboard需要的令牌
7.2 kubeconfig文件生成
DASH_TOCKEN=$(kubectl get secret -n kube-system admin-token-mcqj5 -o jsonpath={.data.token}|base64 -d)
kubectl config set-cluster kubernetes --server=10.0.0.11:6443 --kubeconfig=/root/dashbord-admin.conf
kubectl config set-credentials admin --token=$DASH_TOCKEN --kubeconfig=/root/dashbord-admin.conf
kubectl config set-context admin --cluster=kubernetes --user=admin --kubeconfig=/root/dashbord-admin.conf
kubectl config use-context admin --kubeconfig=/root/dashbord-admin.conf
ext admin --cluster=kubernetes --user=admin --kubeconfig=/root/dashbord-admin.conf
kubectl config use-context admin --kubeconfig=/root/dashbord-admin.conf