Spring-LDAP 服务部署和连接实战
- 安装部署openldap
more start-openldap-docker.sh
#!/bin/bash
#https://github.com/osixia/docker-openldap
docker stop openldap
docker rm openldap
docker run -d \
--privileged=true \
--name=openldap \
-p 389:389 \
-p 636:636 \
-e "LDAP_DOMAIN=example.org" \
-e "LDAP_ADMIN_PASSWORD=kaixin.com" \
-e "LDAP_CONFIG_PASSWORD=kaixin.com" \
-e "LDAP_READONLY_USER=false" \
-e "LDAP_READONLY_USER_USERNAME=readonly" \
-e "LDAP_READONLY_USER_PASSWORD=yourpassword" \
-e "LDAP_RFC2307BIS_SCHEMA=false" \
-v `pwd`/data:/var/lib/ldap \
-v `pwd`/conf:/etc/ldap/slapd.d \
osixia/openldap:1.2.4
#
#测试是否正常
#ldapsearch -x -H ldap://127.0.0.1 -b dc=example,dc=org -D "cn=admin,dc=example,dc=org" -w yourpassword
# OpenLDAP监听的端口:
# 默认监听端口:389(明文数据传输)
# 加密监听端口:636(密文数据传输)
2. 安装部署 ldap-admin start-phpldapadmin-docker.sh (样本代码如下,请根据实际修改)
docker stop phpldapadmin
docker rm phpldapadmin
#下面的变量请根据您的实际情况修改.
ldap_hosts=openldap_host_name (请输入openldap IP地址或域名)
dns_server= 你的dns (如果ldap_hosts是填写的ip 不用写这个dns)
docker run -d \
-p 443:443 \
--dns=${dns_server} \
--name phpladpadmin \
--env PHPLDAPADMIN_LDAP_HOSTS=${ldap_hosts} \
osixia/phpldapadmin:0.7.2 --loglevel debug
echo "如果运行正常,打开网页 https://localhost:443"
echo "Login DN: cn=admin,dc=example,dc=org"
echo "Password: yourpassword"
LDAP简称对应

通过环境变量设置 LDAP 服务器的参数:
LDAP_ORGANISATION: Organisation name. Defaults to Example Inc.
LDAP_DOMAIN: Ldap domain. Defaults to example.org
LDAP_BASE_DN: Ldap base DN. If empty automatically set from LDAP_DOMAIN value. Defaults to (empty)
LDAP_ADMIN_PASSWORD Ldap Admin password. Defaults to admin
LDAP_CONFIG_PASSWORD Ldap Config password. Defaults to config
LDAP_READONLY_USER Add a read only user. Defaults to false
LDAP_READONLY_USER_USERNAME Read only user username. Defaults to readonly
LDAP_READONLY_USER_PASSWORD Read only user password. Defaults to readonly
LDAP_RFC2307BIS_SCHEMA Use rfc2307bis schema instead of nis schema. Defaults to false
- 通过ldapsearch,ldapadd,ldapdelete,ldapmodify等参数查询、新增、删除、修改内容信息
docker exec ldap ldapsearch -x -H ldap://localhost -b dc=example,dc=org -D “cn=admin,dc=example,dc=org” -w admin
docker exec $LDAP_CID ldapadd -x -D “cn=admin,dc=example,dc=org” -w admin -f /container/service/slapd/assets/test/new-user.ldif -H ldap://ldap.example.org -ZZ
https://docs.oracle.com/javase/tutorial/jndi/ldap/exceptions.html
LDAP错误代码
如何映射到JNDI异常LDAP定义了一组状态代码,这些代码随LDAP服务器发送的LDAP响应一起返回(请参阅RFC 2251)。 在JNDI中,错误条件表示为已检查的异常,它们是NamingException的子类。 有关JNDI异常类的概述,请参阅命名异常部分。
LDAP服务提供程序将从LDAP服务器接收的LDAP状态代码转换为NamingException的相应子类。 下表显示了LDAP状态代码和JNDI异常之间的映射。
LDAP状态代码含义异常或操作
0 Success Report success.
1 Operations error NamingException
2 Protocol error CommunicationException
3 Time limit exceeded. TimeLimitExceededException
4 Size limit exceeded. SizeLimitExceededException
5 Compared false. Used by DirContext.search(). Does not generate an exception.
6 Compared true. Used by DirContext.search(). Does not generate an exception.
7 Authentication method not supported. AuthenticationNotSupportedException
8 Strong authentication required. AuthenticationNotSupportedException
9 Partial results being returned. If the environment property “java.naming.referral” is set to “ignore” or the contents of the error do not contain a referral, throw a PartialResultException. Otherwise, use contents to build a referral.
10 Referral encountered. If the environment property “java.naming.referral” is set to “ignore”, then ignore. If the property is set to “throw”, throw ReferralException. If the property is set to “follow”, then the LDAP provider processes the referral. If the “java.naming.ldap.referral.limit” property has been exceeded, throw LimitExceededException.
11 Administrative limit exceeded. LimitExceededException
12 Unavailable critical extension requested. OperationNotSupportedException
13 Confidentiality required. AuthenticationNotSupportedException
14 SASL bind in progress. Used internally by the LDAP provider during authentication.
16 No such attribute exists. NoSuchAttributeException
17 An undefined attribute type. InvalidAttributeIdentifierException
18 Inappropriate matching InvalidSearchFilterException
19 A constraint violation. InvalidAttributeValueException
20 An attribute or value already in use. AttributeInUseException
21 An invalid attribute syntax. InvalidAttributeValueException
32 No such object exists. NameNotFoundException
33 Alias problem NamingException
34 An invalid DN syntax. InvalidNameException
35 Is a leaf. Used by the LDAP provider; usually doesn’t generate an exception.
36 Alias dereferencing problem NamingException
48 Inappropriate authentication AuthenticationNotSupportedException
49 Invalid credentials AuthenticationException
50 Insufficient access rights NoPermissionException
51 Busy ServiceUnavailableException
52 Unavailable ServiceUnavailableException
53 Unwilling to perform OperationNotSupportedException
54 Loop detected. NamingException
64 Naming violation InvalidNameException
65 Object class violation SchemaViolationException
66 Not allowed on non-leaf. ContextNotEmptyException
67 Not allowed on RDN. SchemaViolationException
68 Entry already exists. NameAlreadyBoundException
69 Object class modifications prohibited. SchemaViolationException
71 Affects multiple DSAs. NamingException
80 Other NamingException
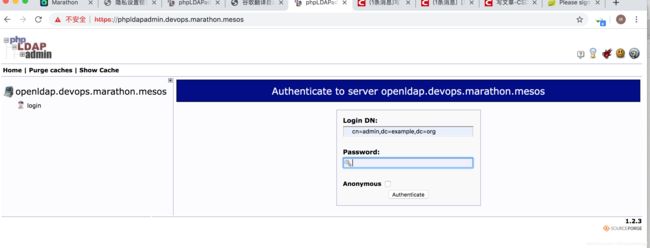
https://youripaddr:443
用户名: cn=admin,dc=example,dc=org
密码:yourpassword
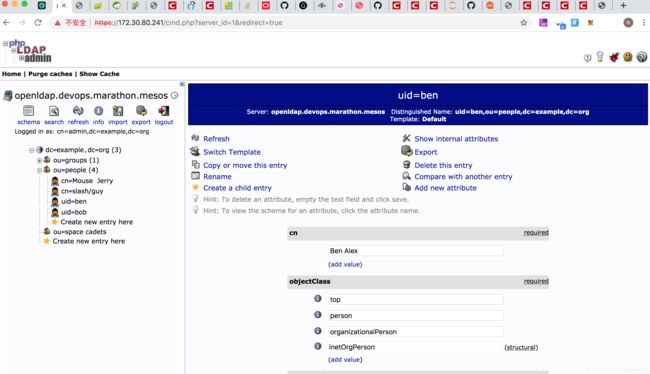
导入或手动创建记录:example.ldif 内容如下
dn: dc=example,dc=org
objectclass: top
objectclass: domain
objectclass: extensibleObject
dc: example
dn: ou=groups,dc=example,dc=org
objectclass: top
objectclass: organizationalUnit
ou: groups
dn: ou=subgroups,ou=groups,dc=example,dc=org
objectclass: top
objectclass: organizationalUnit
ou: subgroups
dn: ou=people,dc=example,dc=org
objectclass: top
objectclass: organizationalUnit
ou: people
dn: ou=space cadets,dc=example,dc=org
objectclass: top
objectclass: organizationalUnit
ou: space cadets
dn: ou=“quoted people”,dc=example,dc=org
objectclass: top
objectclass: organizationalUnit
ou: “quoted people”
dn: ou=otherpeople,dc=example,dc=org
objectclass: top
objectclass: organizationalUnit
ou: otherpeople
dn: uid=ben,ou=people,dc=example,dc=org
objectclass: top
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: Ben Alex
sn: Alex
uid: ben
userPassword: {SHA}nFCebWjxfaLbHHG1Qk5UU4trbvQ=
dn: uid=bob,ou=people,dc=example,dc=org
objectclass: top
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: Bob Hamilton
sn: Hamilton
uid: bob
userPassword: bobspassword
dn: uid=joe,ou=otherpeople,dc=example,dc=org
objectclass: top
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: Joe Smeth
sn: Smeth
uid: joe
userPassword: joespassword
dn: cn=mouse, jerry,ou=people,dc=example,dc=org
objectclass: top
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: Mouse, Jerry
sn: Mouse
uid: jerry
userPassword: jerryspassword
dn: cn=slash/guy,ou=people,dc=example,dc=org
objectclass: top
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: slash/guy
sn: Slash
uid: slashguy
userPassword: slashguyspassword
dn: cn=quote"guy,ou=“quoted people”,dc=example,dc=org
objectclass: top
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: quote"guy
sn: Quote
uid: quoteguy
userPassword: quoteguyspassword
dn: uid=space cadet,ou=space cadets,dc=example,dc=org
objectclass: top
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: Space Cadet
sn: Cadet
uid: space cadet
userPassword: spacecadetspassword
dn: cn=developers,ou=groups,dc=example,dc=org
objectclass: top
objectclass: groupOfUniqueNames
cn: developers
ou: developer
uniqueMember: uid=ben,ou=people,dc=example,dc=org
uniqueMember: uid=bob,ou=people,dc=example,dc=org
dn: cn=managers,ou=groups,dc=example,dc=org
objectclass: top
objectclass: groupOfUniqueNames
cn: managers
ou: manager
uniqueMember: uid=ben,ou=people,dc=example,dc=org
uniqueMember: cn=mouse, jerry,ou=people,dc=example,dc=org
dn: cn=submanagers,ou=subgroups,ou=groups,dc=example,dc=org
objectclass: top
objectclass: groupOfUniqueNames
cn: submanagers
ou: submanager
uniqueMember: uid=ben,ou=people,dc=example,dc=org
- 编写代码测试,简单的LDAP应用。
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.password.LdapShaPasswordEncoder;
@Configuration
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.anyRequest().fullyAuthenticated()
.and()
.formLogin();
}
@Override
public void configure(AuthenticationManagerBuilder auth) throws Exception {
auth
.ldapAuthentication()
.userDnPatterns("uid={0},ou=people")
.groupSearchBase("ou=groups")
.contextSource()
.url("ldap://openldap.devops.marathon.mesos:389/dc=example,dc=org")
.managerDn("cn=admin,dc=example,dc=org")
.managerPassword("kaixin.com")
.and()
.passwordCompare()
.passwordEncoder(new LdapShaPasswordEncoder())
.passwordAttribute("userPassword");
}
//.url("ldap://openldap.devops.marathon.mesos:389/dc=example,dc=org")
}
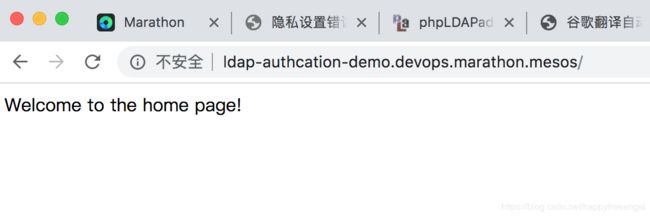
验证:
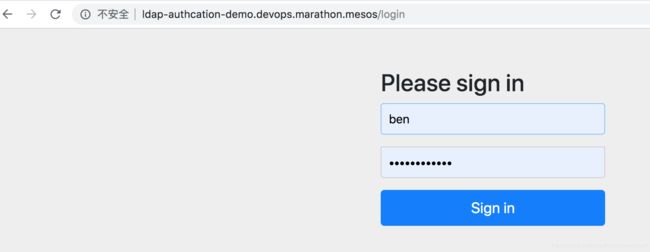
输入:ben 密码: benspassword1

输入:ben 密码: benspassword
github 样本代码下载
https://github.com/HappyFreeAngel/spring-ldap-example.git