实验部分参考官方文档
Use bridge networks中的Configure the default bridge network部分
配置bridge接口
这里我用的是kvm虚拟的两个docker-server,virt-manager给两个docker-server分别添加一块网卡,要保证添加的两块网卡桥在宿主机上的同一块网卡上(可通二层帧)
实验为采用linux bridge实现的跨主机容器间访问
配置网桥
启动docker-server
[root@docker_server ~]# cat /etc/sysconfig/network-scripts/ifcfg-ens8
TYPE=Ethernet
DEFROUTE=yes
NAME=ens8
DEVICE=ens8
ONBOOT=yes
#IPADDR=192.168.200.221
#NETMASK=255.255.255.0
#DNS1=223.5.5.5
#DNS2=223.6.6.6
BRIDGE=br0
[root@docker_server ~]# cat /etc/sysconfig/network-scripts/ifcfg-br0
TYPE=Bridge
NAME=br0
DEVICE=br0
ONBOOT=yes
IPADDR=192.168.200.221
NETMASK=255.255.255.0
DNS1=223.5.5.5
DNS2=223.6.6.6
[root@docker_server ~]# brctl show
bridge name bridge id STP enabled interfaces
br-08c4b7268bdf 8000.02422257f591 no
br-82dcffbba4a6 8000.024231c34aab no vethab6df91
br0 8000.52540022bdbe no ens8
vethb1cc8b0
docker0 8000.0242604e5600 no
[root@docker_server ~]#
两台配置相同,docker-server-2 为192.168.200.222(其实这里不配ip也可)
重启网络服务
官方示例配置
{
"bip": "192.168.1.5/24",
"fixed-cidr": "192.168.1.5/25",
"fixed-cidr-v6": "2001:db8::/64",
"mtu": 1500,
"default-gateway": "10.20.1.1",
"default-gateway-v6": "2001:db8:abcd::89",
"dns": ["10.20.1.2","10.20.1.3"]
}
这里我的配置为
docker-server
[root@docker_server ~]# cat /etc/docker/daemon.json
{
"registry-mirrors": ["https://docker.mirrors.ustc.edu.cn", "https://registry.docker-cn.com"],
"hosts": ["tcp://0.0.0.0:2375", "unix:///var/run/docker.sock"],
"bridge": "br0",
"fixed-cidr": "192.168.200.1/28",
"mtu": 1500,
"default-gateway": "192.168.200.1",
"dns": ["192.168.200.1"]
}
[root@docker_server ~]#
docker-server-2
[root@docker_server-2 ~]# cat /etc/docker/daemon.json
{
"registry-mirrors": ["https://docker.mirrors.ustc.edu.cn", "https://registry.docker-cn.com"],
"hosts": ["tcp://0.0.0.0:2375", "unix:///var/run/docker.sock"],
"bridge": "br0",
"fixed-cidr": "192.168.200.16/28",
"mtu": 1500,
"default-gateway": "192.168.200.1",
"dns": ["192.168.200.1"]
}
[root@docker_server-2 ~]#
说明:
bridge为要桥接的接口
fixed-cidr为“可变长子网掩码的网络化分”
mtu为网络传输单元大小
默认网关
dns
官方文档给出的配置有bip参数,经过试验bip和bridge不能同时存在,官方文档没有说明,但是实现现象表明,在配置了bridge参数后,docker daemon会获取bridge网卡的ip/掩码信息。
[root@docker_server ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
ef9a10b968d2 bridge bridge local
82dcffbba4a6 dockertestdomaincom_default bridge local
e3dfd7c5cc81 host host local
08c4b7268bdf my-net bridge local
ef2b78ba950f none null local
[root@docker_server ~]# docker network inspect bridge
[
{
"Name": "bridge",
"Id": "ef9a10b968d25cc2269ff0777428943d47041e527e94b781095cf70569014cff",
"Created": "2018-10-17T09:45:23.539327032+08:00",
"Scope": "local",
"Driver": "bridge",
"EnableIPv6": false,
"IPAM": {
"Driver": "default",
"Options": null,
"Config": [
{
"Subnet": "192.168.200.0/24",
"IPRange": "192.168.200.0/28",
"Gateway": "192.168.200.221",
"AuxiliaryAddresses": {
"DefaultGatewayIPv4": "192.168.200.1"
}
}
]
},
"Internal": false,
"Attachable": false,
"Ingress": false,
"ConfigFrom": {
"Network": ""
},
"ConfigOnly": false,
"Containers": {
"8111207de8621a7db205a9cd0fa86dbbde499fc20130db7c762650c186fcf5af": {
"Name": "wb1",
"EndpointID": "c131d27b58b2b006047716e44923229d1874d716d88926bc11f4ba615ad1a640",
"MacAddress": "02:42:c0:a8:c8:02",
"IPv4Address": "192.168.200.2/24",
"IPv6Address": ""
}
},
"Options": {
"com.docker.network.bridge.default_bridge": "true",
"com.docker.network.bridge.enable_icc": "true",
"com.docker.network.bridge.enable_ip_masquerade": "true",
"com.docker.network.bridge.host_binding_ipv4": "0.0.0.0",
"com.docker.network.bridge.name": "br0",
"com.docker.network.driver.mtu": "1500"
},
"Labels": {}
}
]
[root@docker_server ~]#
[0] 0:root@docker_server:~*Z
启动容器
两台docker-server上分别启动容器
docker run -it --name ub1 docker.testdomain.com/username/nginx:cus bash
TIPS:如果网络配置非默认bridge,需要加--network my-net指定
docker-server上的ub1
root@a2dfe83daf2f:/# ifconfig
eth0 Link encap:Ethernet HWaddr 02:42:c0:a8:c8:03
inet addr:192.168.200.3 Bcast:192.168.200.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:16 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1184 (1.1 KB) TX bytes:0 (0.0 B)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
docker-server-2上的ub1
root@c513adc9f3f6:/# ifconfig
eth0 Link encap:Ethernet HWaddr 02:42:c0:a8:c8:10
inet addr:192.168.200.16 Bcast:192.168.200.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:28496 errors:0 dropped:0 overruns:0 frame:0
TX packets:442 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1812150 (1.8 MB) TX bytes:21412 (21.4 KB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:454 errors:0 dropped:0 overruns:0 frame:0
TX packets:454 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:50848 (50.8 KB) TX bytes:50848 (50.8 KB)
互ping
64 bytes from 192.168.200.3: icmp_seq=54 ttl=64 time=2.75 ms
64 bytes from 192.168.200.3: icmp_seq=55 ttl=64 time=2.60 ms
64 bytes from 192.168.200.3: icmp_seq=56 ttl=64 time=2.76 ms
64 bytes from 192.168.200.3: icmp_seq=57 ttl=64 time=2.90 ms
64 bytes from 192.168.200.3: icmp_seq=58 ttl=64 time=2.66 ms
64 bytes from 192.168.200.3: icmp_seq=59 ttl=64 time=2.56 ms
^C
--- 192.168.200.3 ping statistics ---
59 packets transmitted, 17 received, +28 errors, 71% packet loss, time 58041ms
rtt min/avg/max/mdev = 2.391/2.781/3.120/0.224 ms, pipe 4
root@c513adc9f3f6:/#
q:
这里不知道为什么ping了大概10秒才通,研究了很久都没找到答案
因为宿主机也是网桥链接的两个docker-server,所以理论上在docker-server上抓的包应该和宿主机上一致
然后在kvm宿主机上抓arp包发现总有一些oui Unknown
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on br200, link-type EN10MB (Ethernet), capture size 65535 bytes
16:30:29.561590 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 28
16:30:29.561828 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 46
16:30:29.563177 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:29.564203 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:30.564515 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 28
16:30:30.564777 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 46
16:30:30.565906 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:30.566852 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:31.093076 ARP, Request who-has 192.168.200.98 tell 192.168.200.99, length 28
16:30:31.093394 ARP, Reply 192.168.200.98 is-at 00:50:56:97:3c:d0 (oui Unknown), length 46
16:30:31.566507 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 28
16:30:31.566718 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 46
16:30:31.568073 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:31.568804 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:33.562746 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 28
16:30:33.562990 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 46
16:30:33.564608 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:33.565632 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:34.564578 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 28
16:30:34.564804 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 46
16:30:34.566281 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:34.567275 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:35.566515 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 28
16:30:35.566734 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 46
16:30:35.568165 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:35.569145 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:37.564765 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 28
16:30:37.565025 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 46
16:30:37.566458 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:37.567577 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:38.566508 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 28
16:30:38.566732 ARP, Request who-has 192.168.200.16 tell 192.168.200.1, length 46
16:30:38.568099 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
16:30:38.568761 ARP, Reply 192.168.200.16 is-at 02:42:c0:a8:c8:10 (oui Unknown), length 28
#brctl showmacs br200
port no mac addr is local? ageing timer
3 00:0c:29:0e:eb:46 no 8.03
3 00:1a:a9:15:61:a1 no 4.42
3 00:50:56:97:3c:d0 no 1.89
3 00:50:56:97:5b:b7 yes 0.00
1 02:42:c0:a8:c8:03 no 0.31
2 02:42:c0:a8:c8:10 no 0.31
3 14:58:d0:55:56:48 no 119.98
3 14:58:d0:55:a5:28 no 119.98
3 14:58:d0:55:d5:e0 no 0.12
3 40:a8:f0:c3:1e:b5 no 2.81
3 40:a8:f0:c3:6e:51 no 3.33
3 ec:b1:d7:b5:ca:b0 no 120.05
3 ec:b1:d7:b5:cd:10 no 118.57
3 ec:b1:d7:b5:cf:b0 no 118.54
3 ec:b1:d7:b5:de:10 no 133.44
3 ec:b1:d7:b5:e4:10 no 123.44
3 ec:b1:d7:b6:d5:30 no 137.88
3 ec:b1:d7:b6:d5:b0 no 124.30
3 fc:15:b4:1c:1c:e0 no 0.43
1 fe:54:00:22:bd:be yes 0.00
2 fe:54:00:99:07:20 yes 0.00
后来等到container的arp表老化后,再ping测试,还是需要10秒甚至几十秒的时间才可ping通,在这期间宿主机抓包会发现有大量两个container间反复的arp request/replay交互信息,但container内仍无法获取对方的mac地址,或是获取到了对方的mac,在宿主机可以抓到icmp,但仍然不通,不知道是什么原因。
如果知道,麻烦在评论区告诉我。谢谢。。。
最后关闭icc禁止container间默认互通,实际上是执行了
iptables -P FORWARD DROP
打开itpables自动添加,如果在启动 Docker 服务的时候设定 "ip-forward": true, Docker 就会自动设定系统的 ip_forward 参数为 1
[root@docker_server-2 ~]# cat /etc/docker/daemon.json
{
"registry-mirrors": ["https://docker.mirrors.ustc.edu.cn", "https://registry.docker-cn.com"],
"hosts": ["tcp://0.0.0.0:2375", "unix:///var/run/docker.sock"],
"bridge": "br0",
"fixed-cidr": "192.168.200.16/28",
"mtu": 1500,
"default-gateway": "192.168.200.99",
"dns": ["223.5.5.5", "223.6.6.6"],
"ip-forward": true,
"iptables": true,
"icc": false
}
curl测试nginx
root@feaaa39fd382:/# ping -c2 192.168.200.16
PING 192.168.200.16 (192.168.200.16) 56(84) bytes of data.
64 bytes from 192.168.200.16: icmp_seq=1 ttl=64 time=3.88 ms
64 bytes from 192.168.200.16: icmp_seq=2 ttl=64 time=2.79 ms
--- 192.168.200.16 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 2.795/3.338/3.881/0.543 ms
root@feaaa39fd382:/# curl 192.168.200.16
curl: (7) Failed to connect to 192.168.200.16 port 80: No route to host
root@feaaa39fd382:/#
最后通过--link containerName:alias参数打开访问
[root@docker_server ~]# docker container prune -f
Deleted Containers:
68484597311b69fa46b15bae34f13b9074f98ec74aa84180ffd2f8e3c554507e
ad63679155e356c14f31fa5dfe57d3dfb1179551caf8536b67c105eb36f42eef
Total reclaimed space: 165B
[root@docker_server ~]# docker run -it --name ub1 --link wb1:wb1 docker.testdomain.com/username/ubuntu:net-tools
root@380d99b0fcdd:/# cat /etc/hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
192.168.200.1 wb1 5c39357b5a70
192.168.200.2 380d99b0fcdd
root@380d99b0fcdd:/# curl wb1
Hello World Agin!
root@380d99b0fcdd:/#
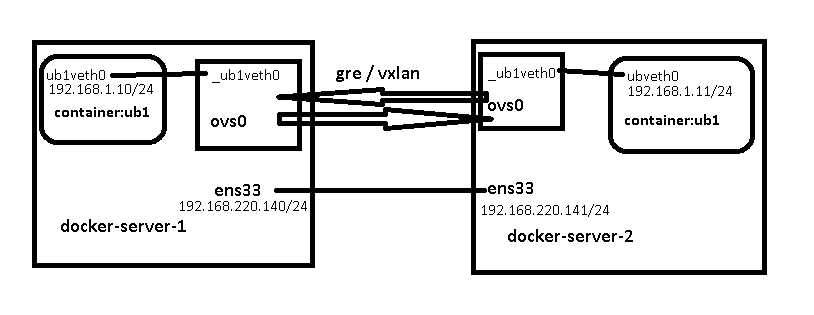
下面是使用ovs进行跨主机连接,其中使用了namespace
参考:
docker容器namespace点对点通信
简要记录一下openvswitch和namespace的搭配使用
先贴个拓扑
两个docker-server的ip地址是直接配在ens33网卡上的,如果想要两个docker-server中的container互通,则需要采用cidr划分不同子网,并添加相应路由实现(通过ip寻址,也就是路由的方式转发package,这被称为三层通讯)
而本文目的是让两个docker-server中的两个同网段的container互通(在ip的package上封装EtherII的帧头,通过mac地址转发package,这被称为二层通讯)
运行一个容器,找到容器的pid,链接到/var/run/netns/中,让ip netns list 能看到这个ns
[root@docker-server-1 ~]#docker run -it --network none docker.testdomain.com/username/ubuntu:net-tools
[root@docker-server-1 ~]# docker container inspect -f '{{.State.Pid}}' ub1
66482
[root@docker-server-1 ~]#ln -sf /proc/66482/ns/net /var/run/netns/ub1
紧接着在创建veth,并给到容器内
[root@docker-server-1 ~]#ip link add ub1veth0 type veth peer name _ub1veth0
[root@docker-server-1 ~]#ip netns exec ub1 ip addr add 192.168.1.10/24 dev ub1veth0
[root@docker-server-1 ~]#ip netns exec ub1 ip link set up dev ub1veth0
将veth的peer添加到ovs0中
[root@docker-server-1 ~]#ovs-vsctl add-port ovs0 _ub1veth0
[root@docker-server-1 ~]#ip link set up dev _ub1veth0
起一个gre隧道(将ip报文封装到gre协议中)
[root@docker-server-1 ~]#ovs-vsctl add-port ovs0 gre1 -- set interface gre1 type=gre option:remote_ip=192.168.220.141
或者起一个VxLAN也可以
[root@docker-server-1 ~]#ovs-vsctl add-port ovs0 vxlan1 -- set interface vxlan1 type=vxlan options:remote_ip=192.168.220.141 options:key=vxlan1key
在docker-server-2中做同样操作,指定容器的ip为192.168.1.11/24,gre的remote_ip为192.168.220.140
最后在docker-server-1上测试
[root@docker-server-1 ~]# docker attach ub1
root@8456b3069020:/#
root@8456b3069020:/# ifconfig
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
ub1veth0 Link encap:Ethernet HWaddr d2:8e:e4:da:40:51
inet addr:192.168.1.10 Bcast:0.0.0.0 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:88 errors:0 dropped:0 overruns:0 frame:0
TX packets:72 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:7872 (7.8 KB) TX bytes:6776 (6.7 KB)
root@8456b3069020:/# ping 192.168.1.11
PING 192.168.1.11 (192.168.1.11) 56(84) bytes of data.
64 bytes from 192.168.1.11: icmp_seq=1 ttl=64 time=10.1 ms
64 bytes from 192.168.1.11: icmp_seq=2 ttl=64 time=2.15 ms
^C
--- 192.168.1.11 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 2.159/6.144/10.130/3.986 ms
root@8456b3069020:/#
tips:
Centos7防火墙INPUT和FORWARD链上自带了icmp的过滤策略,需要将其删除,否则会导致两个container无法通讯
[root@docker-server-1 ~]# iptables -nvL INPUT
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
4 352 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
[root@docker-server-1 ~]# iptables -nvL FORWARD
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER-USER all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DOCKER-ISOLATION-STAGE-1 all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- * br-74fb66d67ceb 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 DOCKER all -- * br-74fb66d67ceb 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- br-74fb66d67ceb !br-74fb66d67ceb 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- br-74fb66d67ceb br-74fb66d67ceb 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- * docker0 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 DOCKER all -- * docker0 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- * virbr0 0.0.0.0/0 192.168.122.0/24 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- virbr0 * 192.168.122.0/24 0.0.0.0/0
0 0 ACCEPT all -- virbr0 virbr0 0.0.0.0/0 0.0.0.0/0
0 0 REJECT all -- * virbr0 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
0 0 ACCEPT all -- docker0 !docker0 0.0.0.0/0 0.0.0.0/0
0 0 REJECT all -- virbr0 * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP all -- docker0 docker0 0.0.0.0/0 0.0.0.0/0
其中:INPUT中这两条删掉
7 798 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
iptables -D INPUT -m conntrack --ctstate INVALID -j DROP
iptables -D INPUT -j REJECT --reject-with icmp-host-prohibited