kali下RsaCtfTool的安装及使用
kali安装gmpy2总是出现各种错误,写个过程。
1.安装方式
压缩包 下载直接解压即可
命令行 git clone https://github.com/Ganapati/RsaCtfTool.git
2.安装
cd RsaCtfTool //进入目录下
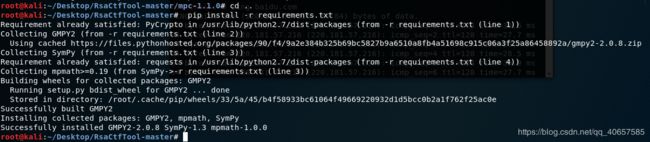
pip install -r requirements.txt //安装python第三方库
可能会报错,没关系,是因为你没安装一些环境
安装配置mpfr和mpc时,时间稍长,不要惊讶
安装mpfr
v= 4.0. 1
wgethttp: // www.mpfr.org/mpfr-current/mpfr-${v}.tar.bz2
tar-jxvf mpfr-${v}. tar.bz2 && cd mpfr- ${v}
./configure
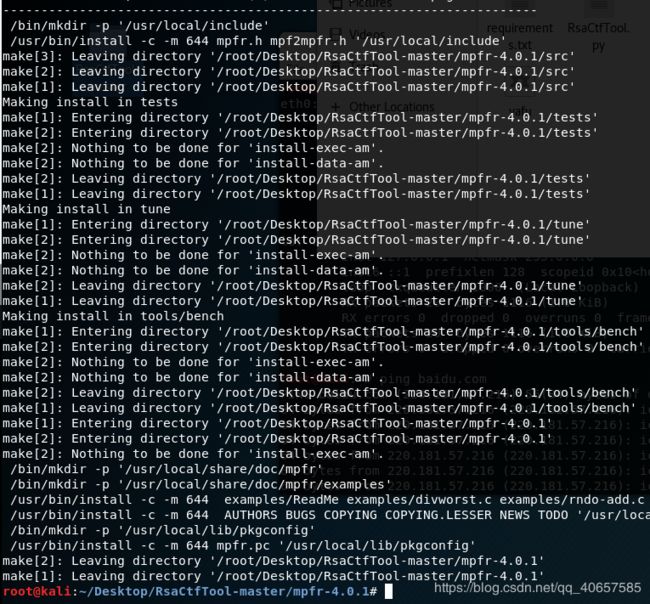
make&& makecheck && make install安装mpc
v=1.1.0
wget ftp://ftp.gnu.org/gnu/mpc/mpc-${v}.tar.gz
tar -zxvf mpc-${v}.tar.gz && cd mpc-${v}
./configure
make && make check && make install #如果报错的话,用make && make install返回RsaCtftool目录下继续安装第三方库
pip install -r requirements.txt以为安装好了,然而
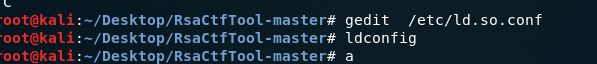
gedit /etc/ld.so.conf //打开文件,添加gmpy2的绝对路径
include /usr/local/lib/python2.7/dist-packages/gmpy2 //加上这句话保存即可
执行ldconfig命令
ldconfigdconfig 命令主要是为了更新 /etc/ld.so.cache 文件,为了加快程序执行时对共享库的定位速度,避免使用收索路径查找共享库的低效率
安装完成
用法
root@kali:~/Desktop/RsaCtfTool-master# python RsaCtfTool.py
usage: RsaCtfTool.py [-h] [--publickey PUBLICKEY] [--createpub] [--dumpkey]
[--ext] [--uncipherfile UNCIPHERFILE]
[--uncipher UNCIPHER] [--verbose] [--private]
[--ecmdigits ECMDIGITS] [-n N] [-p P] [-q Q] [-e E]
[--key KEY]
[--attack {hastads,factordb,pastctfprimes,mersenne_primes,noveltyprimes,smallq,wiener,comfact_cn,primefac,fermat,siqs,Pollard_p_1,all}]
RSA CTF Tool
optional arguments:
-h, --help show this help message and exit
--publickey PUBLICKEY
public key file. You can use wildcards for multiple
keys.
--createpub Take n and e from cli and just print a public key then
exit
--dumpkey Just dump the RSA variables from a key - n,e,d,p,q
--ext Extended dump of RSA private variables in --dumpkey
mode - dp,dq,pinv,qinv).
--uncipherfile UNCIPHERFILE
uncipher a file
--uncipher UNCIPHER uncipher a cipher
--verbose verbose mode (display n, e, p and q)
--private Display private key if recovered
--ecmdigits ECMDIGITS
Optionally an estimate as to how long one of the
primes is for ECM method
-n N Specify the modulus. format : int or 0xhex
-p P Specify the first prime number. format : int or 0xhex
-q Q Specify the second prime number. format : int or 0xhex
-e E Specify the public exponent. format : int or 0xhex
--key KEY Specify the input key file in --dumpkey mode.
--attack {hastads,factordb,pastctfprimes,mersenne_primes,noveltyprimes,smallq,wiener,comfact_cn,primefac,fermat,siqs,Pollard_p_1,all}
Specify the attack mode.
下一篇blog有ras例题