《计算机网络—自顶向下方法》 第二章Wireshark实验1:HTTP
1.基本HTTP GET/response交互
我们开始探索HTTP,方法是下载一个非常简单的HTML文件
非常短,并且不包含嵌入的对象。执行以下操作:
- 启动您的浏览器。
- 启动Wireshark数据包嗅探器,如Wireshark实验-入门所述(还没开始数据包捕获)。在display-filter-specification窗口中输入“http”(只是字母,不含引号标记),这样就在稍后的分组列表窗口中只捕获HTTP消息。(我们只对HTTP协议感兴趣,不想看到其他所有的混乱的数据包)。
- 稍等一会儿(我们将会明白为什么不久),然后开始Wireshark数据包捕获。
- 在浏览器中输入以下内容 http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file1.html 您的浏览器应显示非常简单的单行HTML文件。
- 停止Wireshark数据包捕获。
通过查看HTTP GET和响应消息中的信息,回答以下问题。
在回答以下问题时,您应该打印出GET和响应消息(请参阅Wireshark-入门实验以获取信息),
并指出您在消息中的哪个具体位置找到了回答以下问题的信息。
当您上交作业时,请注明输出,显示您在哪些地方表示了您的答案
(例如,对于我们的课程,我们要求学生用笔标记纸质副本,或用彩色字体在电子副本的中注释文本)。
Frame 244: 632 bytes on wire (5056 bits), 632 bytes captured (5056 bits) on interface 0
Ethernet II, Src: 5a:00:dd:d9:3c:7f (5a:00:dd:d9:3c:7f), Dst: XiaomiCo_c3:ad:2c (a8:9c:ed:c3:ad:2c)
Internet Protocol Version 4, Src: 192.168.43.189, Dst: 128.119.245.12
Transmission Control Protocol, Src Port: 50625, Dst Port: 80, Seq: 1, Ack: 1, Len: 578
Hypertext Transfer Protocol
GET /wireshark-labs/HTTP-wireshark-file1.html HTTP/1.1\r\n
Host: gaia.cs.umass.edu\r\n
Connection: keep-alive\r\n
Cache-Control: max-age=0\r\n
Upgrade-Insecure-Requests: 1\r\n
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36\r\n
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3\r\n
Accept-Encoding: gzip, deflate\r\n
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8\r\n
If-None-Match: "80-59473fb477b28"\r\n
If-Modified-Since: Wed, 09 Oct 2019 05:59:01 GMT\r\n
\r\n
[Full request URI: http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file1.html]
[HTTP request 1/1]
[Response in frame: 253]
服务器向客户机返回的HTTP响应:
Frame 253: 293 bytes on wire (2344 bits), 293 bytes captured (2344 bits) on interface 0
Ethernet II, Src: XiaomiCo_c3:ad:2c (a8:9c:ed:c3:ad:2c), Dst: 5a:00:dd:d9:3c:7f (5a:00:dd:d9:3c:7f)
Internet Protocol Version 4, Src: 128.119.245.12, Dst: 192.168.43.189
Transmission Control Protocol, Src Port: 80, Dst Port: 50625, Seq: 1, Ack: 579, Len: 239
Hypertext Transfer Protocol
HTTP/1.1 304 Not Modified\r\n
Date: Thu, 10 Oct 2019 00:25:50 GMT\r\n
Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16 mod_perl/2.0.10 Perl/v5.16.3\r\n
Connection: Keep-Alive\r\n
Keep-Alive: timeout=5, max=100\r\n
ETag: "80-59473fb477b28"\r\n
\r\n
[HTTP response 1/1]
[Time since request: 0.299829000 seconds]
[Request in frame: 244]
[Request URI: http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file1.html]
1.您的浏览器是否运行HTTP版本1.0或1.1?服务器运行什么版本的HTTP?
答:
浏览器:HTTP/1.1 GET /wireshark-labs/HTTP-wireshark-file1.html HTTP/1.1\r\n
服务器:HTTP/1.1 HTTP/1.1 304 Not Modified\r\n
2.您的浏览器会从接服务器接受哪种语言(如果有的话)?
答:
中文 Accept-Language: zh-CN,zh;q=0.9,en;q=0.8\r\n
3.您的计算机的IP地址是什么? gaia.cs.umass.edu服务器地址呢?
答:
客户机(我的计算机): 192.168.43.189
服务器(gaia.cs.umass.edu): 128.119.345.12
客户机GET请求报文: 244 63.804816 192.168.43.189 128.119.245.12 HTTP 632 GET /wireshark-labs/HTTP-wireshark-file1.html HTTP/1.1
服务器HTTP响应报文:253 64.104645 128.119.245.12 192.168.43.189 HTTP 293 HTTP/1.1 304 Not Modified
4.服务器返回到浏览器的状态代码是什么?
答:
HTTP/1.1 304 Not Modified\r\n
5.服务器上HTML文件的最近一次修改是什么时候?
答:
If-Modified-Since: Wed, 09 Oct 2019 05:59:01 GMT\r\n
6.服务器返回多少字节的内容到您的浏览器?
答:
返回128个字节
7.通过检查数据包内容窗口中的原始数据,你是否看到有协议头在数据包列表窗口中未显示? 如果是,请举一个例子。
答:
【不知道】
2.条件HTTP GET/response交互
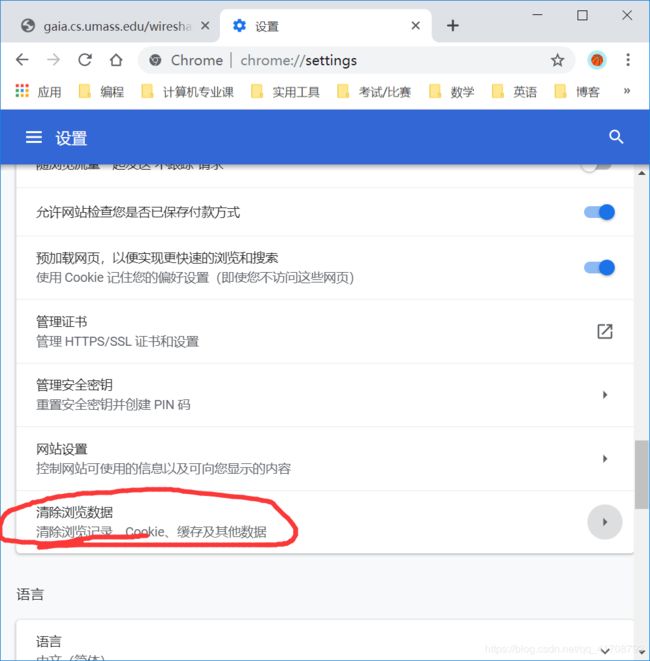
大多数Web浏览器使用对象缓存,从而在检索HTTP对象时执行条件GET。
对于chorme浏览器而言,清缓存的方法:
完成以后,开始进行这个实验,步骤:
- 启动您的浏览器,并确保您的浏览器的缓存被清除,如上所述。
- 启动Wireshark数据包嗅探器。
- 在浏览器中输入以下URL http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file2.html 您的浏览器应显示一个非常简单的五行HTML文件。
- 再次快速地将相同的URL输入到浏览器中(或者只需在浏览器中点击刷新按钮)。
- 停止Wireshark数据包捕获,并在display-filter-specification窗口中输入“http”,以便只捕获HTTP消息,并在数据包列表窗口中显示。
第一次GET请求:
Frame 71: 521 bytes on wire (4168 bits), 521 bytes captured (4168 bits) on interface 0
Ethernet II, Src: 5a:00:dd:d9:3c:7f (5a:00:dd:d9:3c:7f), Dst: XiaomiCo_c3:ad:2c (a8:9c:ed:c3:ad:2c)
Internet Protocol Version 4, Src: 192.168.43.189, Dst: 128.119.245.12
Transmission Control Protocol, Src Port: 51091, Dst Port: 80, Seq: 1, Ack: 1, Len: 467
Hypertext Transfer Protocol
GET /wireshark-labs/HTTP-wireshark-file2.html HTTP/1.1\r\n
Host: gaia.cs.umass.edu\r\n
Connection: keep-alive\r\n
Upgrade-Insecure-Requests: 1\r\n
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36\r\n
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3\r\n
Accept-Encoding: gzip, deflate\r\n
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8\r\n
\r\n
[Full request URI: http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file2.html]
[HTTP request 1/1]
[Response in frame: 75]
第二次GET请求:
Frame 274: 633 bytes on wire (5064 bits), 633 bytes captured (5064 bits) on interface 0
Ethernet II, Src: 5a:00:dd:d9:3c:7f (5a:00:dd:d9:3c:7f), Dst: XiaomiCo_c3:ad:2c (a8:9c:ed:c3:ad:2c)
Internet Protocol Version 4, Src: 192.168.43.189, Dst: 128.119.245.12
Transmission Control Protocol, Src Port: 51111, Dst Port: 80, Seq: 1, Ack: 1, Len: 579
Hypertext Transfer Protocol
GET /wireshark-labs/HTTP-wireshark-file2.html HTTP/1.1\r\n
Host: gaia.cs.umass.edu\r\n
Connection: keep-alive\r\n
Cache-Control: max-age=0\r\n
Upgrade-Insecure-Requests: 1\r\n
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36\r\n
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3\r\n
Accept-Encoding: gzip, deflate\r\n
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8\r\n
If-None-Match: "173-59473fb477358"\r\n
If-Modified-Since: Wed, 09 Oct 2019 05:59:01 GMT\r\n
\r\n
[Full request URI: http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file2.html]
[HTTP request 1/1]
[Response in frame: 282]
1. 检查第一个从您浏览器到服务器的HTTP GET请求的内容。您在HTTP GET中看到了“IF-MODIFIED-SINCE”行吗?
答:
没有看到
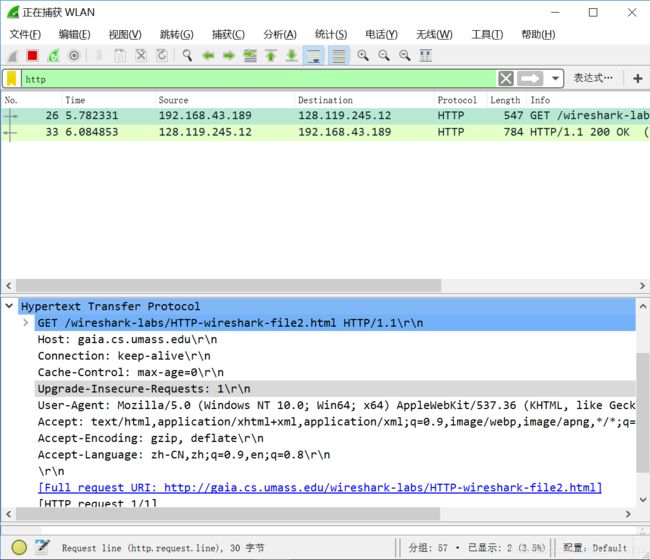
2. 检查服务器响应的内容。服务器是否显式返回文件的内容? 你是怎么知道的?
答:
返回

3. 现在,检查第二个HTTP GET请求的内容。 您在HTTP GET中看到了“IF-MODIFIED-SINCE:”行吗? 如果是,“IF-MODIFIED-SINCE:”头后面包含哪些信息?
答:
看到了
If-Modified-Since: Wed, 09 Oct 2019 05:59:01 GMT\r\n
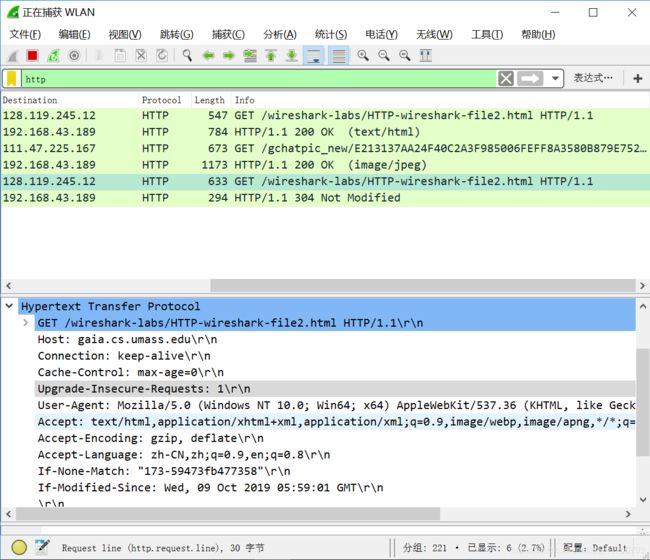
4. 针对第二个HTTP GET,从服务器响应的HTTP状态码和短语是什么?服务器是否明确地返回文件的内容?请解释。
答:
HTTP/1.1 304 Not Modified\r\n
没有明确的返回内容,因为浏览器在第一次请求的时候保存了网页内容到缓存去了,所以可以直接从本地缓存获得网页内容。
3.检索长文件
在我们到目前为止的例子中,检索的文档是简短的HTML文件。 接下来我们来看看当我们下载一个长的HTML文件时会发生什么。按以下步骤操作:
- 启动您的浏览器,并确保您的浏览器缓存被清除,如上所述。
- 启动Wireshark数据包嗅探器
- 在您的浏览器中输入以下URL http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file3.html 您的浏览器应显示相当冗长的美国权利法案。
- 停止Wireshark数据包捕获,并在display-filter-specification窗口中输入“http”,以便只显示捕获的HTTP消息。
客户机发出的GET请求
Frame 26: 547 bytes on wire (4376 bits), 547 bytes captured (4376 bits) on interface 0
Ethernet II, Src: 5a:00:dd:d9:3c:7f (5a:00:dd:d9:3c:7f), Dst: XiaomiCo_c3:ad:2c (a8:9c:ed:c3:ad:2c)
Internet Protocol Version 4, Src: 192.168.43.189, Dst: 128.119.245.12
Transmission Control Protocol, Src Port: 50832, Dst Port: 80, Seq: 1, Ack: 1, Len: 493
Hypertext Transfer Protocol
GET /wireshark-labs/HTTP-wireshark-file3.html HTTP/1.1\r\n
Host: gaia.cs.umass.edu\r\n
Connection: keep-alive\r\n
Cache-Control: max-age=0\r\n
Upgrade-Insecure-Requests: 1\r\n
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36\r\n
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3\r\n
Accept-Encoding: gzip, deflate\r\n
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8\r\n
\r\n
[Full request URI: http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file3.html]
[HTTP request 1/1]
[Response in frame: 37]
服务器的响应
Frame 37: 715 bytes on wire (5720 bits), 715 bytes captured (5720 bits) on interface 0
Ethernet II, Src: XiaomiCo_c3:ad:2c (a8:9c:ed:c3:ad:2c), Dst: 5a:00:dd:d9:3c:7f (5a:00:dd:d9:3c:7f)
Internet Protocol Version 4, Src: 128.119.245.12, Dst: 192.168.43.189
Transmission Control Protocol, Src Port: 80, Dst Port: 50832, Seq: 4201, Ack: 494, Len: 661
[4 Reassembled TCP Segments (4861 bytes): #32(1400), #33(1400), #34(1400), #37(661)]
Hypertext Transfer Protocol
Line-based text data: text/html (98 lines)
-
您的浏览器发送多少HTTP GET请求消息?哪个数据包包含了美国权利法案的消息?
答:
一个HTTP GET请求消息,

Line-based text data: text/html(98 lines):包含了美国权利法案的消息 -
哪个数据包包含响应HTTP GET请求的状态码和短语?
答:
HTTP/1.1 200 OK\r\n:请求的状态码:200短语:OK -
响应中的状态码和短语是什么?
答:
状态码 + 短语(用于解释)
- 2XX Success(成功状态码)
200 表示从客户端发来的请求在服务器端被正常处理
204 该状态码表示服务器接收的请求已成功处理,但在返回的响应报文中不含实体的主体部分
206 该状态码表示客户端进行了范围请求,而服务器成功执行了这部分的GET请求 - 3XX Redirection(重定向状态码)
301 永久性重定向
302 临时性重定向 - 4XX Client Error(客户端错误状态码)
400 该状态码表示请求报文中存在语法错误
401 该状态码表示发送的请求需要有通过HTTP认证的认证信息
403 该状态码表明对请求资源的访问被服务器拒绝了。
404 该状态码表明服务器上无法找到请求的资源 - 5XX Server Error(服务器错误状态码)
500 该状态码表明服务器端在执行请求时发生了错误。
503 该状态码表明服务器暂时处于超负载或正在进行停机维护,现在无法处理请求。
- 需要多少 包含数据的TCP段来执行单个HTTP响应和权利法案文本?
答:
【不知道】
4.具有嵌入对象的HTML文档
现在我们已经看到Wireshark如何显示捕获的大型HTML文件的数据包流量,我们可以看看当浏览器使用嵌入的对象下载文件时,会发生什么,即包含其他对象的文件(在下面的例子中是图像文件) 的服务器。
执行以下操作:
- 启动您的浏览器。
- 启动Wireshark数据包嗅探器。
- 在浏览器中输入以下URL http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file4.html 您的浏览器应显示包含两个图像的短HTML文件。这两个图像在基本HTML文件中被引用。也就是说,图像本身不包含在HTML文件中;相反,图像的URL包含在已下载的HTML文件中。如书中所述,您的浏览器将不得不从指定的网站中检索这些图标。我们的出版社的图标是从 www.aw-bc.com 网站检索的。而我们第5版(我们最喜欢的封面之一)的封面图像存储在manic.cs.umass.edu服务器。
- 停止Wireshark数据包捕获,并在display-filter-specification窗口中输入“http”,以便只显示捕获的HTTP消息。
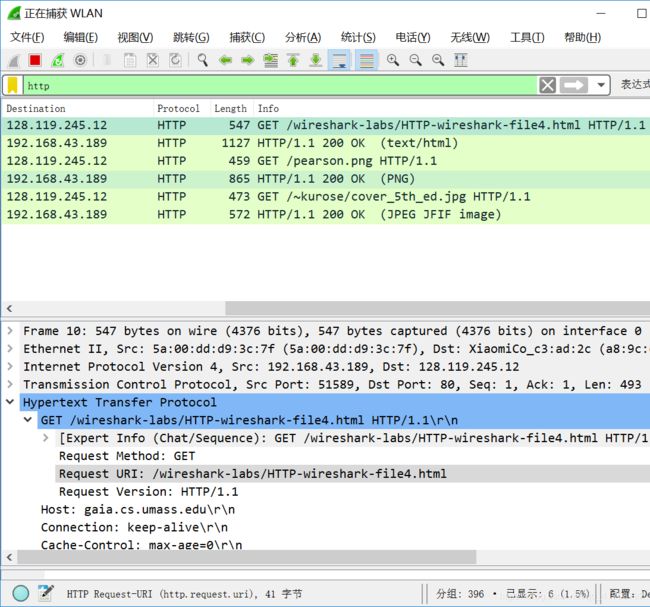
1. 您的浏览器发送了几个HTTP GET请求消息? 这些GET请求发送到哪个IP地址?
答:
三个HTTP GET请求
1:
10 0.435317 192.168.43.189 128.119.245.12 HTTP 547 GET /wireshark-labs/HTTP-wireshark-file4.html HTTP/1.1
2:
17 0.785192 192.168.43.189 128.119.245.12 HTTP 459 GET /pearson.png HTTP/1.1
3:
40 1.200534 192.168.43.189 128.119.245.12 HTTP 473 GET /~kurose/cover_5th_ed.jpg HTTP/1.1
这三个GET请求都是发送到128.119.245.12这个服务器(说明请求的html文档、两张图片都位于这个服务器中)。
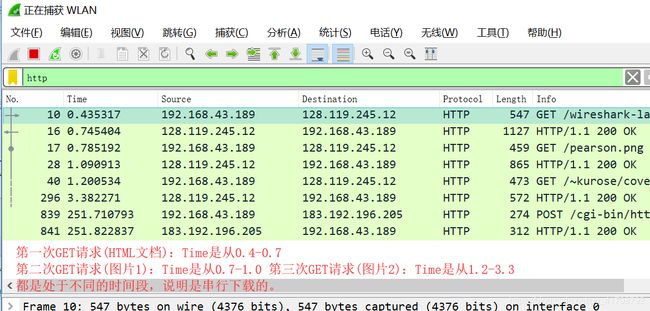
2. 浏览器从两个网站串行还是并行下载了两张图片?请说明。
答:
并行
原因:
5.HTTP认证
最后,我们尝试访问受密码保护的网站,并检查网站的HTTP消息交换的序列。URL http://gaia.cs.umass.edu/wireshark-labs/protected_pages/HTTP-wireshark-file5.html 是受密码保护的。用户名是“wireshark-students”(不包含引号),密码是“network”(再次不包含引号)。所以让我们访问这个“安全的”受密码保护的网站。执行以下操作:
- 请确保浏览器的缓存被清除,如上所述,然后关闭你的浏览器,再然后启动浏览器
- 启动Wireshark数据包嗅探器。
- 在浏览器中输入以下URL http://gaia.cs.umass.edu/wireshark-labs/protected_pages/HTTP-wiresharkfile5.html 在弹出框中键入所请求的用户名和密码。
- 停止Wireshark数据包捕获,并在display-filter-specification窗口中输入“http”,以便只显示捕获的HTTP消息。

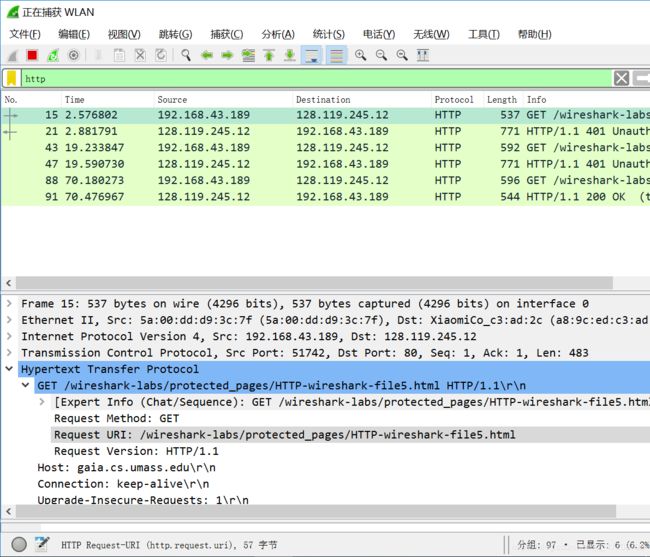

1. 对于您的浏览器的初始HTTP GET消息,服务器响应(状态码和短语)是什么响应?
答:
初始HTTP GET响应:
21 2.881791 128.119.245.12 192.168.43.189 HTTP 771 HTTP/1.1 401 Unauthorized (text/html)
状态码:401
短语:Unauthorized
2. 当您的浏览器第二次发送HTTP GET消息时,HTTP GET消息中包含哪些新字段?
答:
第三次发送HTTP GET消息(我的第二次是输入错误,第三次才是输入正确):
91 70.476967 128.119.245.12 192.168.43.189 HTTP 544 HTTP/1.1 200 OK (text/html)
状态码:200
短语:OK
参考资料:
https://github.com/moranzcw/Computer-Networking-A-Top-Down-Approach-NOTES