SWAN之ikev2协议crl-ldap配置测试
本测试主要验证远程用户carol和网关moon通过LDAP协议由LDAP服务器获取CRL证书的功能,以及对CRL证书进行缓存的设置。测试开始时网关moon和远程用户carol开启了严格CRL策略,但是缓存在本地目录:/etc/ipsec.d/crls/目录下的CRL证书已经过期,因此需要由LDAP服务器winnetou(IP地址:192.168.0.150)重新获得CRL证书,之后,由于设置了chachecrls=yes选项,将获取到的CRL证书缓存到本地目录/etc/ipsec.d/crls/。本次测试拓扑如下:
carol主机配置
carol的配置文件:ikev2/crl-ldap/hosts/carol/etc/ipsec.conf,内容如下,注意其中setup段,strictcrlpolicy和cachecrls字段设置为yes,开启严格的crl检查,并且使能CRL证书缓存功能。
在ca strongswan段中,字段cacert设置CA证书名称,crluri字段指定了ldap服务器的目录地址,由此获取CRL证书更新。
config setup
strictcrlpolicy=yes
cachecrls=yes
ca strongswan
cacert=strongswanCert.pem
crluri="ldap://ldap.strongswan.org/cn=strongSwan Root CA, o=strongSwan Project, c=CH?certificateRevocationList"
auto=add
conn %default
ikelifetime=60m
keylife=20m
rekeymargin=3m
keyingtries=2
keyexchange=ikev2
conn home
left=PH_IP_CAROL
leftcert=carolCert.pem
[email protected]
leftfirewall=yes
right=PH_IP_MOON
rightsubnet=10.1.0.0/16
[email protected]
auto=add
以下carol主机的strongswan配置文件:ikev2/crl-ldap/hosts/carol/etc/strongswan.conf,此处增加ldap插件的加载。
charon {
load = random nonce aes sha1 sha2 md5 pem pkcs1 curve25519 gmp x509 ldap revocation hmac stroke kernel-netlink socket-default updown
}
以下carol主机的iptables配置文件:ikev2/crl-ldap/hosts/carol/etc/iptables.rules,主要关注INPUT和OUTPUT链中增加的以下规则,允许到winnetou主机的LDAP报文(其协议为TCP,端口号为389)。
# allow ldap crl fetch from winnetou
-A INPUT -i eth0 -p tcp --sport 389 -s PH_IP_WINNETOU -j ACCEPT
-A OUTPUT -o eth0 -p tcp --dport 389 -d PH_IP_WINNETOU -j ACCEPT
网关moon的配置文件:ikev2/crl-ldap/hosts/moon/etc/ipsec.conf以及strongswan.conf、iptables.rules配置文件,内容与以上carol主机的配置基本相同,不在列出。
测试准备阶段
配置文件:ikev2/crl-ldap/pretest.dat,除了通常的ipsec连接的启动的语句外,需要注意的是在winnetou主机上启动ldap服务。
winnetou::/etc/init.d/slapd start
测试阶段
配置文件:ikev2/crl-ldap/evaltest.dat。以下测试语句检查moon网关上crl证书的加载、验证以及对远端证书的验证日志。最后,确认命令ipsec listcrls显示的正确性。对于主机carol也要执行相同的检查流程,这里省略。
moon:: cat /var/log/daemon.log::loaded crl from::YES
moon:: cat /var/log/daemon.log::crl is stale::YES
moon:: cat /var/log/daemon.log::fetching crl from.*ldap::YES
moon:: cat /var/log/daemon.log::crl is valid::YES
moon:: cat /var/log/daemon.log::certificate status is good::YES
以下为在moon网关上strongswan进程的日志文件的部分信息,可以看到首先是成功的加载了本地缓存的crl证书:stale.crl,接下来验证crl证书已过期,继而由ldap服务器重新获取证书。最后,使用新的CRL证书替换了本地缓存的旧证书。
moon charon: 00[CFG] loading crls from '/etc/ipsec.d/crls'
moon charon: 00[CFG] loaded crl from '/etc/ipsec.d/crls/stale.crl'
moon charon: 05[CFG] crl caching to /etc/ipsec.d/crls enabled
moon charon: 14[CFG] checking certificate status of "C=CH, O=strongSwan Project, OU=Research, [email protected]"
moon charon: 14[CFG] using trusted certificate "C=CH, O=strongSwan Project, CN=strongSwan Root CA"
moon charon: 14[CFG] crl correctly signed by "C=CH, O=strongSwan Project, CN=strongSwan Root CA"
moon charon: 14[CFG] crl is stale: since Sep 17 09:33:09 2019
moon charon: 14[CFG] fetching crl from 'ldap://ldap.strongswan.org/cn=strongSwan Root CA, o=strongSwan Project, c=CH?certificateRevocationList' ...
moon charon: 14[CFG] using trusted certificate "C=CH, O=strongSwan Project, CN=strongSwan Root CA"
moon charon: 14[LIB] crl #03 is newer - existing crl #01 replaced
moon charon: 14[CFG] crl correctly signed by "C=CH, O=strongSwan Project, CN=strongSwan Root CA"
moon charon: 14[LIB] crl #03 is newer - existing crl #01 replaced
moon charon: 14[CFG] crl is valid: until Nov 15 03:32:58 2019
moon charon: 14[CFG] certificate status is good
moon charon: 14[CFG] reached self-signed root ca with a path length of 0
moon charon: 14[IKE] authentication of '[email protected]' with RSA_EMSA_PKCS1_SHA2_256 successful
moon charon: 14[LIB] crl #03 is newer - existing crl #01 replaced
moon charon: 14[CFG] written crl file '/etc/ipsec.d/crls/adb364fbeaa34eb9f274e7cdf2b1f359e79033b0.crl' (651 bytes)
以下可见本地原本缓存的证书:stale.crl的有效期到2019年9月17(本次测试的时间为:2019年11月1日),已经过期。
$ openssl crl -inform der -in ikev2/crl-ldap/hosts/moon/etc/ipsec.d/crls/stale.crl -text -noout
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CH, O = strongSwan Project, CN = strongSwan Root CA
Last Update: Sep 16 09:33:09 2019 GMT
Next Update: Sep 17 09:33:09 2019 GMT
CRL extensions:
X509v3 Authority Key Identifier:
keyid:7E:A0:7B:77:A5:91:58:79:DF:35:EB:4E:FC:0F:B6:B8:68:AE:A2:47
X509v3 CRL Number:
1
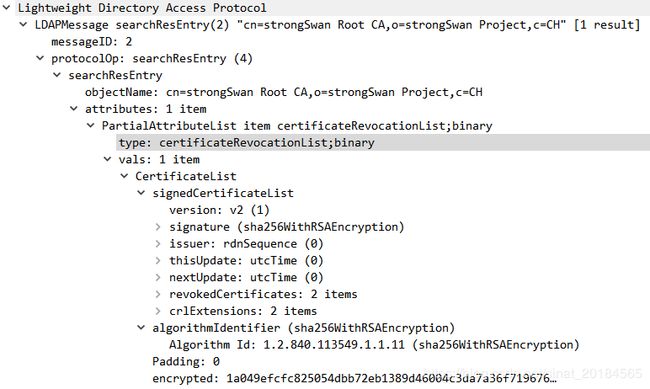
以下为由LDAP服务器获取到的CRL证书,其在有效期内,并且X509v3 CRL Number为3大于以上的stale.crl证书中的CRL Number 1。字段X509v3 Authority Key Identifier的内容作为新的CRL证书的名称,其与CA证书strongswanCert.pem中的字段X509v3 Subject Key Identifier的值相同。
$ openssl crl -inform der -in adb364fbeaa34eb9f274e7cdf2b1f359e79033b0.crl -text -noout
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CH, O = strongSwan Project, CN = strongSwan Root CA
Last Update: Oct 31 03:32:58 2019 GMT
Next Update: Nov 15 03:32:58 2019 GMT
CRL extensions:
X509v3 Authority Key Identifier:
keyid:AD:B3:64:FB:EA:A3:4E:B9:F2:74:E7:CD:F2:B1:F3:59:E7:90:33:B0
X509v3 CRL Number:
3
在本测试开头的carol主机配置的ca strongswan段配置的cacert证书为:strongswanCert.pem,其信息如下所示,可见其X509v3 Subject Key Identifier字段设置为:AD:B3:64:FB:EA:A3:4E:B9:F2:74:E7:CD:F2:B1:F3:59:E7:90:33:B0,而这真是新crl证书的名称。
moon:~# openssl x509 -in /etc/ipsec.d/cacerts/strongswanCert.pem -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 6571418977315253872 (0x5b325ebe3522ee70)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CH, O = strongSwan Project, CN = strongSwan Root CA
Validity
Not Before: Sep 16 09:33:09 2019 GMT
Not After : Sep 16 09:33:09 2029 GMT
Subject: C = CH, O = strongSwan Project, CN = strongSwan Root CA
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (3072 bit)
Modulus:
00:cd:58:4e:f6:0d:dd:7c:8f:ce:da:fa:ad:c0:0f:
...
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:1
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Subject Key Identifier:
AD:B3:64:FB:EA:A3:4E:B9:F2:74:E7:CD:F2:B1:F3:59:E7:90:33:B0
Signature Algorithm: sha256WithRSAEncryption
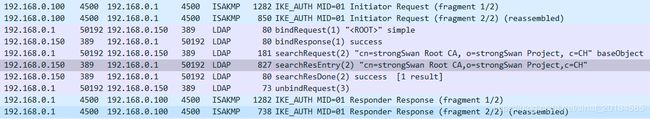
LDAP报文交互如下:
strongswan测试版本: 5.8.1
END