Istio 1.1安装部署实践
3月20日,Istio 1.1版本正式发布,我们已在《全方位解读 | Istio v1.1正式发布》一文中为大家进行了简单介绍。本文将给大家带来详细的部署过程详解,需要说明的是,本文针对单集群安装部署,多集群安装部署会在后续文章中详细说明。
前提条件
-
正确安装配置Kubernetes集群
-
CentOS Linux release 7.5.1804
安装
下载istio 1.1版本
[root@vm157 ~]# wget https://github.com/istio/istio/releases/download/1.1.1/istio-1.1.1-linux.tar.gz
……
2019-03-26 09:39:06 (483 KB/s) - ‘istio-1.1.1-linux.tar.gz’ saved [15736205/15736205]
Istio安装有多种方式,本文根据helm template生成istio部署的配置文件,其他部署方式请参考官方文档。
[root@vm157 ~]# cd istio-1.1.1/
[root@ruffy istio-1.1.1]# helm template ../install/kubernetes/helm/istio-init --name istio-init --namespace istio-system > istio-init.yaml
[root@ruffy istio-1.1.1]# kubectl get crds | grep 'istio.io\|certmanager.k8s.io' | wc -l
[root@ruffy istio-1.1.1]# InternalIp=10.20.1.175
[root@ruffy istio-1.1.1]# helm template install/kubernetes/helm/istio --namespace istio-system \
> --set global.mtls.enabled=true \
> --set global.controlPlaneSecurityEnabled=true \
> --set gateways.istio-ingressgateway.type=NodePort \
> --set grafana.enabled=true \
> --set servicegraph.enabled=true \
> --set servicegraph.ingress.enabled=true \
> --set servicegraph.ingress.hosts={servicegraph-istio-system.${InternalIp}.nip.io} \
> --set tracing.enabled=true \
> --set tracing.jaeger.ingress.enabled=true \
> --set tracing.jaeger.ingress.hosts={jaeger-query-istio-system.${InternalIp}.nip.io} \
> --set tracing.ingress.enabled=true \
> --set tracing.ingress.hosts={tracing-istio-system.${InternalIp}.nip.io} \
> --set kiali.enabled=true \
> --set kiali.ingress.enabled=true \
> --set kiali.ingress.hosts={kiali-istio-system.${InternalIp}.nip.io} \
> --set kiali.dashboard.grafanaURL=http://grafana-istio-system.${InternalIp}.nip.io \
> --set kiali.dashboard.jaegerURL=http://jaeger-query-istio-system.${InternalIp}.nip.io \
> --name istio > ruffy/istio-${InternalIp}.yaml
[root@vm175 istio-1.1.1]# cd ruffy
[root@vm175 ruffy]# ls
istio-10.20.1.175.yaml istio-init.yaml namespace.yaml
根据配置模板部署Isito组件
[root@vm175 istio-1.1.1]# kubectl apply -f ruffy/namespace.yaml
namespace/istio-system created
[root@vm175 istio-1.1.1]# kubectl apply -f ruffy/istio-init.yaml
configmap/istio-crd-10 created
configmap/istio-crd-11 created
serviceaccount/istio-init-service-account created
clusterrole.rbac.authorization.k8s.io/istio-init-istio-system configured
clusterrolebinding.rbac.authorization.k8s.io/istio-init-admin-role-binding-istio-system configured
job.batch/istio-init-crd-10 created
job.batch/istio-init-crd-11 created
[root@vm175 istio-1.1.1]# kubectl apply -f ruffy/istio-10.20.1.175.yaml
poddisruptionbudget.policy/istio-galley created
poddisruptionbudget.policy/istio-ingressgateway created
poddisruptionbudget.policy/istio-policy created
poddisruptionbudget.policy/istio-telemetry created
poddisruptionbudget.policy/istio-pilot created
……
rule.config.istio.io/promhttp created
rule.config.istio.io/promtcp created
rule.config.istio.io/promtcpconnectionopen created
rule.config.istio.io/promtcpconnectionclosed created
handler.config.istio.io/kubernetesenv created
rule.config.istio.io/kubeattrgenrulerule created
rule.config.istio.io/tcpkubeattrgenrulerule created
kubernetes.config.istio.io/attributes created
destinationrule.networking.istio.io/istio-policy created
destinationrule.networking.istio.io/istio-telemetry created
[root@vm157 ~]# cd istio-1.1.1/
[root@ruffy istio-1.1.1]# helm template ../install/kubernetes/helm/istio-init --name istio-init --namespace istio-system > istio-init.yaml
[root@ruffy istio-1.1.1]# kubectl get crds | grep 'istio.io\|certmanager.k8s.io' | wc -l
[root@ruffy istio-1.1.1]# InternalIp=10.20.1.175
[root@ruffy istio-1.1.1]# helm template install/kubernetes/helm/istio --namespace istio-system \
> --set global.mtls.enabled=true \
> --set global.controlPlaneSecurityEnabled=true \
> --set gateways.istio-ingressgateway.type=NodePort \
> --set grafana.enabled=true \
> --set servicegraph.enabled=true \
> --set servicegraph.ingress.enabled=true \
> --set servicegraph.ingress.hosts={servicegraph-istio-system.${InternalIp}.nip.io} \
> --set tracing.enabled=true \
> --set tracing.jaeger.ingress.enabled=true \
> --set tracing.jaeger.ingress.hosts={jaeger-query-istio-system.${InternalIp}.nip.io} \
> --set tracing.ingress.enabled=true \
> --set tracing.ingress.hosts={tracing-istio-system.${InternalIp}.nip.io} \
> --set kiali.enabled=true \
> --set kiali.ingress.enabled=true \
> --set kiali.ingress.hosts={kiali-istio-system.${InternalIp}.nip.io} \
> --set kiali.dashboard.grafanaURL=http://grafana-istio-system.${InternalIp}.nip.io \
> --set kiali.dashboard.jaegerURL=http://jaeger-query-istio-system.${InternalIp}.nip.io \
> --name istio > ruffy/istio-${InternalIp}.yaml
[root@vm175 istio-1.1.1]# cd ruffy
[root@vm175 ruffy]# ls
istio-10.20.1.175.yaml istio-init.yaml namespace.yaml
查看Isito部署状态
[root@vm175 istio-1.1.1]# kubectl -n istio-system get all
NAME READY STATUS RESTARTS AGE
pod/grafana-7b46bf6b7c-xr2lw 1/1 Running 0 2m
pod/istio-citadel-5878d994cc-kfm7p 1/1 Running 0 2m
pod/istio-cleanup-secrets-1.1.1-wlk7p 0/1 Completed 0 2m
pod/istio-galley-6db4964df6-9lpsl 1/1 Running 0 2m
pod/istio-grafana-post-install-1.1.1-44lv7 0/1 Completed 0 2m
pod/istio-ingressgateway-cd5df7bc6-sgh5m 0/1 Running 0 2m
pod/istio-init-crd-10-q5kvp 0/1 Completed 0 3m
pod/istio-init-crd-11-kdd25 0/1 Completed 0 3m
pod/istio-pilot-597dd58685-hsp72 1/2 Running 0 2m
pod/istio-policy-67f66c8b5c-8kqwm 2/2 Running 5 2m
pod/istio-security-post-install-1.1.1-gcjrm 0/1 Completed 0 2m
pod/istio-sidecar-injector-59fc9d6f7d-j9prx 0/1 ContainerCreating 0 2m
pod/istio-telemetry-c5bfc457f-qqzb5 2/2 Running 4 2m
pod/istio-tracing-75dd89b8b4-2t2hl 0/1 ContainerCreating 0 2m
pod/kiali-5d68f4c676-bdltq 1/1 Running 0 2m
pod/prometheus-89bc5668c-7kp8b 0/1 Init:Error 1 2m
pod/servicegraph-57bfbbd697-6tldj 0/1 Running 0 2m
……
NAME DESIRED SUCCESSFUL AGE
job.batch/istio-cleanup-secrets-1.1.1 1 1 2m
job.batch/istio-grafana-post-install-1.1.1 1 1 2m
job.batch/istio-init-crd-10 1 1 3m
job.batch/istio-init-crd-11 1 1 3m
job.batch/istio-security-post-install-1.1.1 1 1 2m
增加grafana和prometheus的ingress文件
Istio-grafana.yaml
[root@vm175 ruffy]# cat istio-grafana-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: grafana
namespace: istio-system
labels:
app: grafana
annotations:
spec:
rules:
- host: granafa-istio.10.20.1.175.xip.io
http:
paths:
- path: /
backend:
serviceName: grafana
servicePort: 3000
Isito-prometheus-ingress.yaml
[root@vm175 ruffy]# cat istio-prometheus-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: istio-prometheus
namespace: istio-system
spec:
rules:
- host: prometheus-istio.10.20.1.175.xip.io
http:
paths:
- path: /prometheus
backend:
serviceName: prometheus
servicePort: 9090
查看部署的组件访问路径
[root@vm175 ruffy]# kubectl -n istio-system get ing
NAME HOSTS ADDRESS PORTS AGE
grafana granafa-istio.10.20.1.175.xip.io 80 5m
istio-prometheus prometheus-istio.10.20.1.175.xip.io 80 5m
istio-servicegraph servicegraph-istio-system.10.20.1.175.nip.io 80 56m
istio-tracing tracing-istio-system.10.20.1.175.nip.io 80 56m
kiali kiali-istio-system.10.20.1.175.nip.io 80 56m
访问kiali时,出现secret不存在的情况,需要通过kiali-secret.yaml文件创建secret,并且重启kiali服务。
Kiali-secret.yaml文件
[root@vm175 ruffy]# cat kiali-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: kiali
namespace: istio-system
labels:
app: kiali
type: Opaque
data:
username: "YWRtaW4="
passphrase: "YWRtaW4="
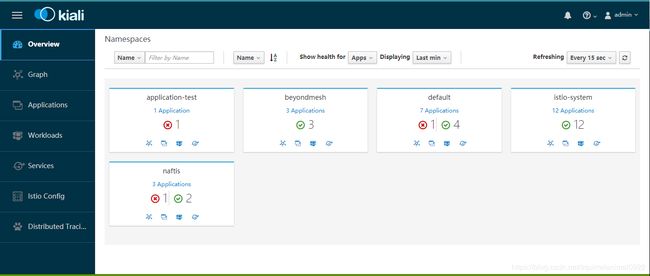
访问Kiali
浏览器输入地址:http://kiali-istio-system.10.20.1.175.nip.io/kiali/
用户名/密码:admin/admin
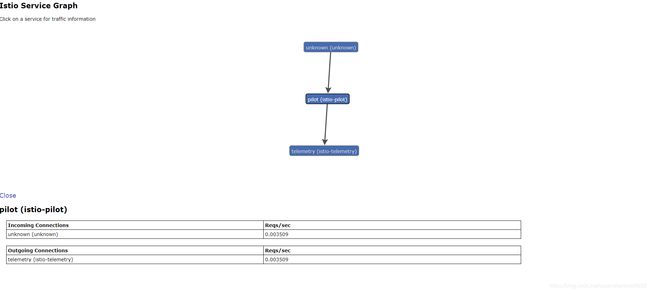
访问servicegraph
浏览器输入地址:http://servicegraph-istio-system.10.20.1.175.nip.io/force/forcegraph.html
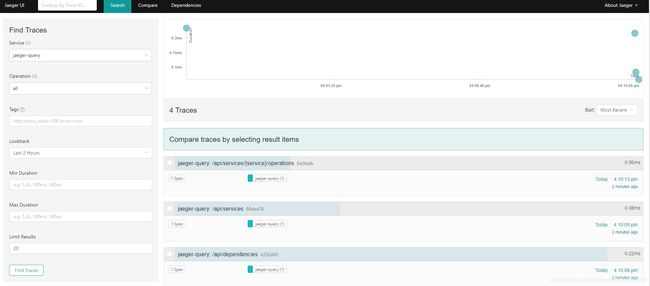
访问tracing
浏览器输入地址:http://servicegraph-istio-system.10.20.1.175.nip.io/force/forcegraph.html
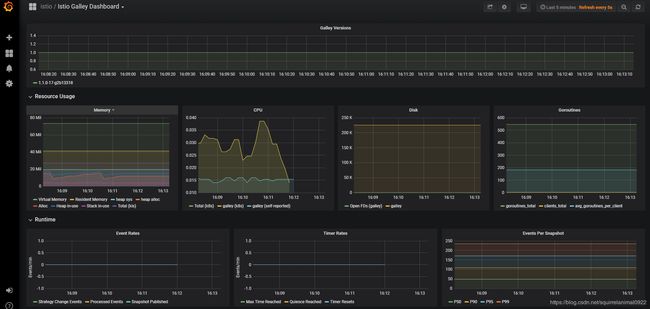
访问granafa
浏览器输入地址:http://granafa-istio.10.20.1.175.xip.io/d/TSEY6jLmk/istio-galley-dashboard?refresh=5s&orgId=1
至此 Istio1.1及其依赖组件搭建完毕。
BoCloud博云技术社区官方交流群已成立,邀请热爱前沿技术的你共同探讨交流。进群方式:添加管理员微信(ID : ruffylining 或 waret87)拉你进群。(发送好友申请时请注明姓名-公司。