测试文件:https://buuoj.cn/files/7b8602971727c6c82ec0d360d5cad2c0/6a428ff2-25d7-403c-b28e-3f980a10a5a2.apk?token=eyJ0ZWFtX2lkIjpudWxsLCJ1c2VyX2lkIjoxOTAzLCJmaWxlX2lkIjoyMTV9.XYmTqw.OyIU1nla76d5HdmzUbwmtT9twOg
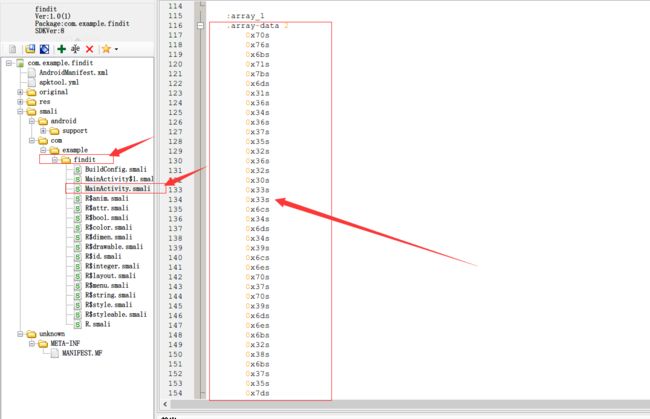
1.APKIDE打开
找到一组十六进制数
转换为字符串之后为
pvkq{m164675262033l4m49lnp7p9mnk28k75}
2.凯撒解密
model = "abcdefghijklmnopqrstuvwxyz" str1 = "pvkq{m164675262033l4m49lnp7p9mnk28k75}" for i in range(1,27): print("key=%d"%i, end='\n') for s in str1: if s.isalpha(): n = model.find(s) s = model[n-i] print(s, end='') print('\n')
key=1
oujp{l164675262033k4l49kmo7o9lmj28j75}key=2
ntio{k164675262033j4k49jln7n9kli28i75}key=3
mshn{j164675262033i4j49ikm7m9jkh28h75}key=4
lrgm{i164675262033h4i49hjl7l9ijg28g75}key=5
kqfl{h164675262033g4h49gik7k9hif28f75}key=6
jpek{g164675262033f4g49fhj7j9ghe28e75}key=7
iodj{f164675262033e4f49egi7i9fgd28d75}key=8
hnci{e164675262033d4e49dfh7h9efc28c75}key=9
gmbh{d164675262033c4d49ceg7g9deb28b75}key=10
flag{c164675262033b4c49bdf7f9cda28a75}key=11
ekzf{b164675262033a4b49ace7e9bcz28z75}key=12
djye{a164675262033z4a49zbd7d9aby28y75}key=13
cixd{z164675262033y4z49yac7c9zax28x75}key=14
bhwc{y164675262033x4y49xzb7b9yzw28w75}key=15
agvb{x164675262033w4x49wya7a9xyv28v75}key=16
zfua{w164675262033v4w49vxz7z9wxu28u75}key=17
yetz{v164675262033u4v49uwy7y9vwt28t75}key=18
xdsy{u164675262033t4u49tvx7x9uvs28s75}key=19
wcrx{t164675262033s4t49suw7w9tur28r75}key=20
vbqw{s164675262033r4s49rtv7v9stq28q75}key=21
uapv{r164675262033q4r49qsu7u9rsp28p75}key=22
tzou{q164675262033p4q49prt7t9qro28o75}key=23
synt{p164675262033o4p49oqs7s9pqn28n75}key=24
rxms{o164675262033n4o49npr7r9opm28m75}key=25
qwlr{n164675262033m4n49moq7q9nol28l75}key=26
pvkq{m164675262033l4m49lnp7p9mnk28k75}
3.get flag!
flag{c164675262033b4c49bdf7f9cda28a75}