Bugku逆向 RE_Cirno
Bugku逆向 RE_Cirno
- 图片解密
- IDA反编译
- python解密
- 栅栏密码解密
- 方法1
- 方法2
图片解密
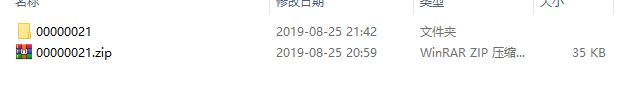
下载下来的文件是一张图片,于是想到用binwalk查看图片内容

发现有个压缩包,用foremost提取一下

IDA反编译
打开exe看了一下除了栅栏的提示外没有任何信息,拖到ida里面
v3 = 115;
v4 = 94;
v5 = 97;
v6 = 114;
v7 = 103;
v8 = 47;
v9 = 107;
v10 = 114;
v11 = 65;
v12 = 48;
v13 = 49;
v14 = 105;
v15 = 117;
v16 = 118;
v17 = 101;
v18 = 48;
v19 = 113;
v20 = 95;
v21 = 99;
v22 = 47;
v23 = 92;
v24 = 116;
v25 = 93;
v26 = 102;
for ( i = 0; i < 24; ++i )
v0 = *(&v3 + i) + 9;
printf(
"琪露诺酱在冻青蛙的路上,突然被9层栅栏反方向围住了,找不到方向,你可以帮助她找到路吗?\n");
system("pause");
return 0;
}
尝试用python写出来
s = [115, 94, 97, 114, 103, 47, 107, 114, 65, 48, 49, 105, 117, 118, 101, 48, 113, 95, 99, 47, 92, 116, 93, 102]
for i in range(24):
print(chr(s[i]+9),end='')
# |gj{p8t{J9:r~n9zhl8e}fo
然后用栅栏密码解密却发现怎么也解不出来
因为菜鸡不会汇编,所以后来我换了Ghidra反编译出来居然还有一个异或???这是个ida的bug嘛??
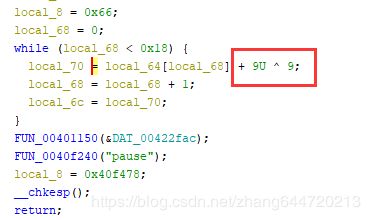
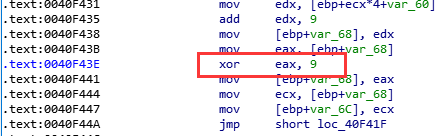
后来回去看了汇编,果然有一个异或

python解密
s = [115, 94, 97, 114, 103, 47, 107, 114, 65, 48, 49, 105, 117, 118, 101, 48, 113, 95, 99, 47, 92, 116, 93, 102]
# while (local_68 < 0x18) {
# local_70 = local_64[local_68] + 9U ^ 9;
# local_68 = local_68 + 1;
# local_6c = local_70;
# }
char = [chr(s[i] + 9 ^ 9) for i in range(24)]
print(''.join(char[::-1])) # 因为上面说的是“反方向围住了”,所以还要把字符串倒一下
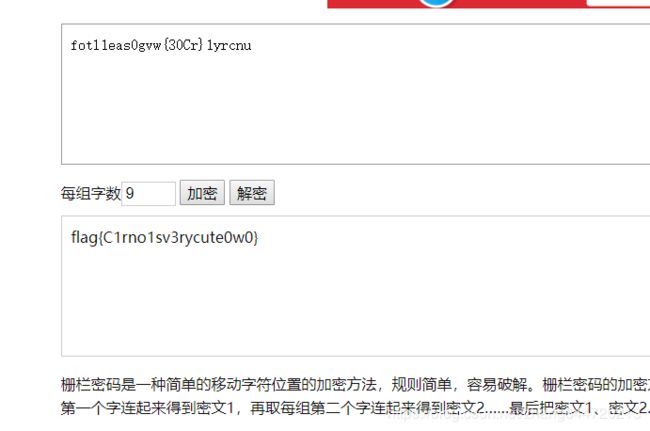
# fotl1eas0gvw{30Cr}1yrcnu
这时发现大括号和flag都出来了
栅栏密码解密
方法1
直接用网页栅栏密码解密就可以了
https://www.qqxiuzi.cn/bianma/zhalanmima.php
方法2
因为有些栅栏密码解码程序不支持自动补全密码,所以需要自己补全
我们可以自己先写随便一串相同原始长度的flag,剩下不够的用 * 补充
abcdefghijklmnopqrstuvwx***
然后手动分割
abcdefghi
jklmnopqr
stuvwx***
再转个圈调换顺序
ajs
bkt
clu
dmv
enw
fox
gp*
hq*
ir*
再合并
ajsbktcludmvenwfoxgp*hq*ir*
发现最后几位每个两位添加了一个 * ,于是我们把flag分割成这样
fotlleas0gvw{30Cr}ly*rc*nu*
用python写一个解密程序,也适用于所有栅栏密码的解密
def decode(flag,num):
length = len(flag) # flag的长度
lines = length // num # 判断共有几层并减一
remainder = num * (lines + 1) - length #相差的数量
# 补全flag
result = flag[:length-lines*remainder]
for i in range(remainder-1,-1,-1):
result += flag[length-(i+1)*lines:length-i*lines] + '*'
# 还原flag
lines += 1
arr = [result[i:i+lines] for i in range(0,len(result),lines)]
flag = ''
for i in range(len(arr[0])):
for j in arr:
flag += j[i]
return flag[:length]
if __name__ == '__main__':
print(decode("fotl1eas0gvw{30Cr}1yrcnu",9))
