安卓逆向之基于frida的AppMon的使用一
安卓逆向之基于frida的AppMon的使用一
- 安卓逆向之appmon的使用一
- 0x01 安装准备
- 0x02 安装过程
- 1、安装依赖包:
- 2、安装逍遥模拟器(创建Android4.4)
- 3、下载frida-server:
- 4、安装frida-server
- 0x03 总结
由于工作需要,我和同事收到几个恶意的样本,在对样本进行拓线时,从样本中获取到了恶意的安卓apk;对样本的逆向分析主要由同事完成,在对样本的数据传输进行调查时,发现抓包工具抓取样本数据不能满足需求,并且通过andriod killer逆向工具分析代码过程及其繁琐,同事找到了一款非常实用的工具 appmon,以下将详述其安装过程。
安卓逆向之appmon的使用一
AppMon is an automated framework for monitoring and tampering system API calls of native macOS, iOS and android apps. It is based on Frida.
It consists of the following components:
AppMon Sniffer - Intercept API calls to figure out interesting operations performed by an App
Appmon Intruder - Manipulate API calls data to create change app’s original behavior
AppMon Android Tracer - Automcatically traces Java classes, methods, its arguments and their data-types in Android APKs
AppMon IPA Installer - Creates and installs “inspectable” IPAs on non-jailbroken iOS devices
AppMon APK Builder - Creates APKs “inspectable” on non-rooted Android devices
0x01 安装准备
该工具可以检测macOS、IOS、Android,(作者的教程中使用了Android手机进行演示,由于分析恶意apk将在Android模拟器中进行)本次将以Android为例;
系统:windows10
开发语言:python2.7
编辑器:pycharm
模拟器:逍遥模拟器(Android4.4)
0x02 安装过程
1、安装依赖包:
项目的作者开发本项目采用的为python2.6版本,由于python2.x版本马上就要停止维护,建议使用pycharm直接安装,后续我和同事将会把项目迁移到python3.x版本,期待我们迁移成功。
直接安装项目中requirements.txt中的包即可

运行项目:python2 appmon.py
如果出错,则可能是依赖包安装时出错,检查依赖包

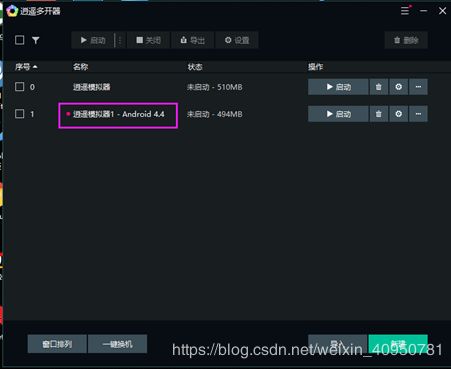
2、安装逍遥模拟器(创建Android4.4)
3、下载frida-server:
地址:https://github.com/frida/frida/releases/latest
Android4.4选用版本:frida-inject-12.8.0-android-x86.xz即可,下载后解压重命名:frida-server

4、安装frida-server
1、 在模拟器安装目录(adb.exe位置)下打开cmd:

2、安装
cmd命令:.\adb.exe push C:\users\XuanJian\Desktop\frida-server data\local\tmp
cmd命令:.\adb.exe shell "chmod 777 data/local/tmp/frida-server"

5、安装一个apk样本:(在运行frida-server之前先运行apk)
6、开启frida-server
cmd命令:./firda-server

7、 查看apk的包名:(可以使用Android killer对apk进行反编译)

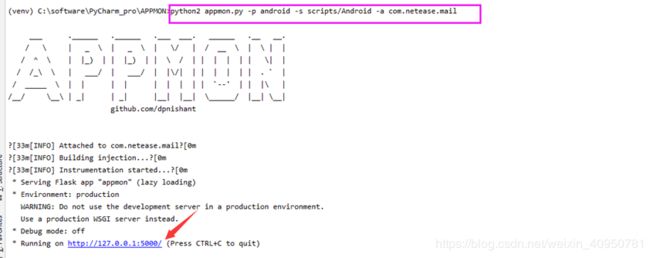
8、 运行appmon
cmd命令:python2 appmon.py -p andriod -s scripts/Android -a com.netease.mail
其中 -p:指定检测平台;
-s:指定运行脚本;
-a:指定包名
0x03 总结
至此,打开appmon的大门,后续将会继续更新appmon的学习,后续工作:
1、开发appmon的使用手册;
2、迁移至python3.x;
3、汉化(可能)