OpenShift 4 之通过设置SDN的NetworkPolicy定义Pod访问策略
文章目录
- NetworkPolicy简介
- 应用环境和测试方法
- 部署测试应用
- 测试验证
- NetworkPolicy策略
- 拒绝所有Pod直接访问
- 只允许来自相同项目的Pod访问
- 只允许来自同一项目的指定Pod访问
- 只允许从其他项目访问
- 只允许从指定的项目访问
- 只允许从指定项目的指定Pod访问
- 只允许从指定的端口访问
- 混合策略
- 其它参考
NetworkPolicy简介
NetworkPolicy是Kubernetes和OpenShift定义通过网络访问Pod的安全策略,利用它可以在不通的Project和Pod之间定义细粒度的应用访问策略。
在NetworkPolicy中以白名单的方式定义了针对“XXX项目”的“XXXPod”可以让“XXX项目”的“XXXPod”通过“XXX方式”访问,不在白名单都无法进行访问。
应用环境和测试方法
部署测试应用
创建如下资源:
$ oc new-project project1
$ oc label namespace project1 name=project1
$ oc new-project project2
$ oc label namespace project2 name=project2
$ oc new-project project3
$ oc label namespace project3 name=project3
$ oc new-app -n project1 openshiftroadshow/parksmap --name=web-db
$ oc new-app -n project1 openshiftroadshow/parksmap --name=web
$ oc new-app -n project1 openshiftroadshow/parksmap --name=db
$ oc new-app -n project1 openshiftroadshow/parksmap --name=mail
$ oc new-app -n project1 openshiftroadshow/parksmap --name=foobar
$ oc new-app -n project1 openshiftroadshow/parksmap --name=foo
$ oc new-app -n project1 openshiftroadshow/parksmap --name=bar
$ oc new-app -n project1 openshiftroadshow/parksmap --name=api
$ oc new-app -n project1 openshiftroadshow/parksmap --name=monitoring
$ oc new-app -n project1 openshiftroadshow/parksmap --name=project1-app
$ oc new-app -n project2 openshiftroadshow/parksmap --name=project2-app
$ oc new-app -n project3 openshiftroadshow/parksmap --name=project3-app
测试验证
通过以下方法验证可从应用的Pod中访问到同一项目或不同项目的应用Service地址。以下是从project1-app的Pod通过Service的CLUSTER-IP访问project2-app的Pod的说明。
$ oc get svc -n project1
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
project1-app ClusterIP 172.30.144.211 <none> 8080/TCP 2m8s
$ oc get pod -n project2 | grep Running
NAME READY STATUS RESTARTS AGE
project2-app-l7jqd 1/1 Running 0 102s
$ oc rsh project2-app-l7jqd
sh-4.2$ curl 172.30.144.211:8080
NetworkPolicy策略
拒绝所有Pod直接访问
- 创建以下内容的deny-all.yaml
kind: NetworkPolicy
apiVersion: networking.k8s.io/v1
metadata:
name: deny-all
spec:
podSelector:
ingress: []
- 将deny-all.yaml的NetworkPolicy策略实施于project1。注意:为了不相互影响,需要将其它策略删除。
$ oc create -f deny-all.yaml -n project1
- 通过“测试验证”步骤确认已经无法从任何项目的Pod访问到project1-app1的Service了。
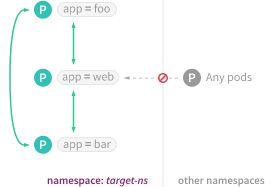
只允许来自相同项目的Pod访问
- 创建以下内容的allow-same-namespace.yaml。
kind: NetworkPolicy
apiVersion: networking.k8s.io/v1
metadata:
name: allow-same-namespace
spec:
podSelector:
ingress:
- from:
- podSelector: {}
- 将allow-same-namespace.yaml的NetworkPolicy策略实施于project1。注意:为了不相互影响,需要将其它策略删除。
$ oc create -f allow-same-namespace.yaml -n project1
- 通过“测试验证”步骤确认只能从project1的Pod访问project1-app的Service了。
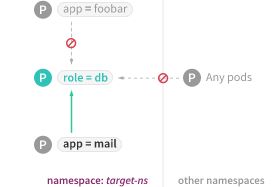
只允许来自同一项目的指定Pod访问
- 创建以下内容的allow-some-app.yaml。
kind: NetworkPolicy
apiVersion: networking.k8s.io/v1
metadata:
name: allow-mail-access-db
spec:
podSelector:
matchLabels:
app: mail
ingress:
- from:
- podSelector:
matchLabels:
app: mail
- 将allow-some-app.yaml的NetworkPolicy策略实施于project1。注意:为了不相互影响,需要将其它策略删除。
$ oc create -f allow-mail-access-db -n project1
- 通过“测试验证”步骤确认只能从mail访问db的Service了。
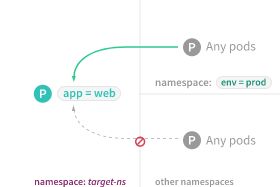
只允许从其他项目访问
- 创建以下内容的allow-from-other-namespace.yaml。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-from-other-namespace
spec:
podSelector:
matchLabels:
app: web-db
ingress:
- from:
- namespaceSelector: {}
- 将allow-some-app.yaml的NetworkPolicy策略实施于project1。注意:为了不相互影响,需要将其它策略删除。
$ oc create -f allow-some-app.yaml -n project1
- 通过“测试验证”步骤确认只能从其它项目的Pod访问web-db的Service了。
只允许从指定的项目访问
- 创建以下内容的allow-from-other-project.yaml。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-from-other-project
spec:
podSelector:
matchLabels:
app: web
ingress:
- from:
- namespaceSelector:
matchLabels:
name: project2
- 将allow-from-other-project.yaml的NetworkPolicy策略实施于project1。注意:为了不相互影响,需要将其它策略删除。
$ oc create -f allow-from-other-project.yaml -n project1
- 通过“测试验证”步骤确认只能从project2项目的Pod访问project1项目web的Service了。
只允许从指定项目的指定Pod访问
- 创建以下内容的allow-other-project-pod.yaml。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-other-project-pod
spec:
podSelector:
matchLabels:
app: db
ingress:
- from:
- namespaceSelector:
matchLabels:
project: project2
podSelector:
matchLabels:
app: mail
注意:以上代码的namespaceSelector和podSelecto是“并且”的关系。而以下代码namespaceSelector和podSelecto是“或者”的关系。
- from:
- namespaceSelector:
matchLabels:
project: project2
- podSelector:
matchLabels:
app: mail
- 将allow-other-project-pod.yaml的NetworkPolicy策略实施于project1。注意:为了不相互影响,需要将其它策略删除。
$ oc create -f allow-other-project-pod.yaml -n project1
- 通过“测试验证”步骤确认只能从project2项目中mail的Pod访问project1项目web的Service了。
只允许从指定的端口访问
- 创建以下内容的allow-port.yaml。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-port
spec:
podSelector:
matchLabels:
app: api
ingress:
- from:
- podSelector:
matchLabels:
app: monitoring
ports:
- protocol: TCP
port: 80
- protocol: TCP
port: 443
- 将allow-port.yaml的NetworkPolicy策略实施于project1。注意:为了不相互影响,需要将其它策略删除。
$ oc create -f allow-port.yaml -n project1
混合策略
如果一个Pod被不同的NetworkPolicy定义了访问策略,则这些访问策略的全集适用于这个Pod。
其它参考
- https://kubernetes.io/docs/concepts/services-networking/network-policies/
- https://blog.openshift.com/whats-new-in-openshift-3-5-network-policy-tech-preview/