- 每日一题——第八十九题
互联网打工人no1
C语言程序设计每日一练c语言
题目:在字符串中找到提取数字,并统计一共找到多少整数,a123xxyu23&8889,那么找到的整数为123,23,8889//思想:#include#include#includeintmain(){charstr[]="a123xxyu23&8889";intcount=0;intnum=0;//用于临时存放当前正在构建的整数。boolinNum=false;//用于标记当前是否正在读取一个整
- SpringBlade dict-biz/list 接口 SQL 注入漏洞
文章永久免费只为良心
oracle数据库
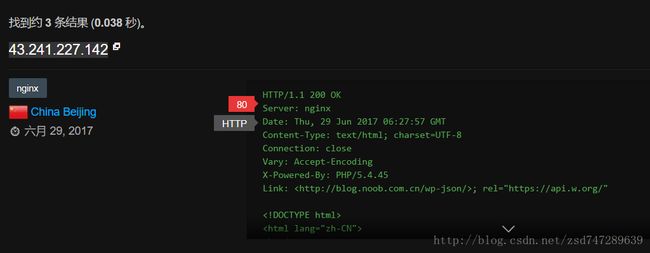
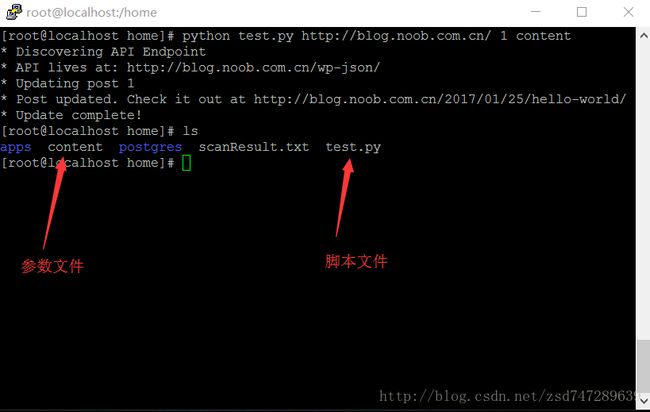
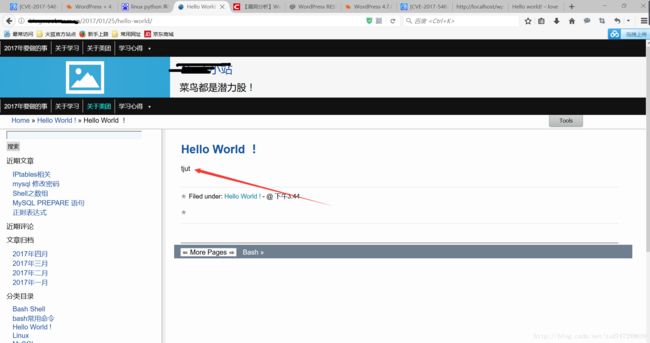
SpringBladedict-biz/list接口SQL注入漏洞POC:构造请求包查看返回包你的网址/api/blade-system/dict-biz/list?updatexml(1,concat(0x7e,md5(1),0x7e),1)=1漏洞概述在SpringBlade框架中,如果dict-biz/list接口的后台处理逻辑没有正确地对用户输入进行过滤或参数化查询(PreparedSta
- 119:虚惊一场
追梦的小蚂蚁
医院体检结果出来了。老a被通知再次去复查,又复查了一遍,结果还是不理想。老a心里有点不痛快了,难不成饭吃到头了?这人生最悲剧的事情就是人没了,钱还没花完。我从明天开始想吃的想喝的一毛都不省,天天抽华子。上班期间,老a掏出华子给人散。老c:“这发什么横财了?都整上了华子了?”老a:“别tm废话,抽不?不抽我装上了!”老c:“哥哥,肯定抽啊,拿来。”老a:“就凭这个哥哥,以后给你天天发华子!”老c:“
- 戴先华2021.4.18《我的第129篇幸运作业》
39f4298779c4
2021.4.18今天小宝和大表姐出去玩,我和婆婆在烧饭,突然小宝冲了进来,告诉奶奶说:“奶奶,奶奶姐姐在亭子里倒了”我一下子看出小宝的紧张,马上跑了出去,发现大外甥女又患了病,看起来心疼极了,整个人面朝地下的倒下了,在地上不停的抽搐,额头摔了一个大泡,整张脸都是紫色的,眼睛边上都出血了,真的是非常紧张,这么多年姐姐两夫妻就这样看着自己的孩子一次次晕倒,姐夫这么多年,年年都拿不出钱回家,使得家一次
- python批量读取tiff文件_Python Pillow批量转换tif格式到jpg
weixin_39557797
最近因为想要整下网站的壁纸,从网站下载了别人整理好的合集压缩包,解压之后,却发现里面的文件都是tif的,tif格式网站和电脑都不认的,根本不能作壁纸。这时候,就需要转换图片格式了,首先我找了几款转换格式的软件,发现效果都不好,要不是不支持tif格式,要不就是转换出来的图片糊的不行。最终,还是决定用Python的Pillow库来写一个脚本,完成这个任务。下面是整个的小脚本----importosim
- el-table实现全选整表,单元一页复选框功能
周bro
vue.jselementuijavascript前端
全选整表单选一页0":popper-append-to-body="false":total="tableData.length":page-size="pageObj.pagesize":page-sizes="[10,50,100]"layout="total,sizes,prev,pager,next"@size-change="handleSizeChange"@current-chang
- 保研日记--哈工大威海计算机学院
faaarii
保研
传送门保研日记--中国海洋大学计算机系保研日记--中国人民大学信息学院(人大信院)保研日记--北京交通大学计算机学院保研材料模板(自我介绍,个人简历,个人陈述,推荐信)哈工大威海计算机学院这次夏令营给我的感觉非常的朴素,哈哈哈哈营员就有四个群,985/211、双一流、双非、四非??没有宣讲会、见面会,在面试开始之前放了一个简短的宣传片。(傲娇,绝对不整那些花里胡哨的哈哈哈)面试有三组老师,分别问你
- 凌云彻喜欢如懿, 他成最惨的人, 终究没有守护好心爱的人!
小狸猫娱乐笔记
《如懿传》最新预告里,令妃发现凌云彻喜欢如懿,令妃要开启黑化模式,整如懿了!凌云彻最后走向十分虐!凌云彻这个人物很痴情,前期被魏嬿婉抛弃了一次后,当魏嬿婉过来找他,他选择了原谅。直到魏嬿婉主动去找皇上,他才真的放弃了,感觉到了绝望。而魏嬿婉希望用他生子的时候也被拒绝了,他是个有原则的人!凌云彻和如懿的关系也许就是在这失望之间,有人扶持,两人算是相互扶持走出低谷,只是如懿有心里爱的人,对凌云彻算是朋
- 《疯狂的外星人》:生活本就如此荒诞,杀不死你的,终将成就你
职心眼儿
文/董小琳了解电影较好的方法是知道它是如何说故事的。——法国评论家安德烈·巴顿早就听闻豆瓣评分6.4的《疯狂的外星人》,口碑两极分化——爱的人,喜欢它的搞笑,符合贺岁档合家欢的观影需求;骂的人,认为剧情牵强,漏洞百出,笑点牵强得像被人瘙痒。结果近54万观众的评分,一半以上的人只给到了及格,甚至还往下的分数。所以,《疯狂的外星人》就铁定是一部烂片了吗?今年过年,在家看了这部作品后,我想,如果电影自己
- 底线
莫向身外求
心中有尺,行事才能有度。做人最重要的是要有底线。守住做人的底线,不忘初心,方得始终。01底线,是过犹不及适可而止有个小孩爱吃糖果,家人就买了一整瓶的糖果送给他,孩子很高兴,手立刻伸进瓶子里抓了一大把,结果手被瓶口卡住,拔不出来,急得大哭。父母对他说:“你放下一点糖果,手便能拿出来了。”孩子看了一眼糖果,不愿意放下,就看着父母哭。父亲说:“手想拿出来,就必须放下一点,要知足,超越了底线,你只能在此干
- discuz discuz_admincp.php 讲解,Discuz! 1.5-2.5 命令执行漏洞分析(CVE-2018-14729)
weixin_39740419
discuz讲解
0x00漏洞简述漏洞信息8月27号有人在GitHub上公布了有关Discuz1.5-2.5版本中后台数据库备份功能存在的命令执行漏洞的细节。漏洞影响版本Discuz!1.5-2.50x01漏洞复现官方论坛下载相应版本就好。0x02漏洞分析需要注意的是这个漏洞其实是需要登录后台的,并且能有数据库备份权限,所以比较鸡肋。我这边是用Discuz!2.5完成漏洞复现的,并用此进行漏洞分析的。漏洞点在:so
- mysql 隐秘后门_【技术分享】CVE-2016-5483:利用mysqldump备份可生成后门
Toby Dai
mysql隐秘后门
预估稿费:100RMB投稿方式:发送邮件至linwei#360.cn,或登陆网页版在线投稿前言mysqldump是用来创建MySQL数据库逻辑备份的一个常用工具。它在默认配置下可以生成一个.sql文件,其中包含创建/删除表和插入数据等。在导入转储文件的时候,攻击者可以通过制造恶意表名来实现任意SQL语句查询和shell命令执行的目的。另一个与之相关的漏洞利用场景可以参考。攻击场景攻击者已经能够访问
- 处理绿盟科技安全评估的系统漏洞
自我修炼的小石头
数据库运维开发工具
如下图一次扫描,中度风险39个,这个是必须要处理的.其中mysql占了36个,一看这个感觉整个人都不好了.但是最后解决的办法也很简单,就是升级.系统版本Redhat7.31.telnet因为要升级openssh,openssl,为了避免意外,首先要开启telnet服务,并把所有相关的包上传到服务器.1.1确认是否安装了telnet和xinetd(默认是没有安装)rpm-qatelnet*rpm-q
- 解决mysql漏洞 Oracle MySQL Server远程安全漏洞(CVE-2015-0411)
dieweidong5625
数据库运维java
有时候会检测到服务器有很多漏洞,而大部分漏洞都是由于服务的版本过低的原因,因为官网出现漏洞就会发布新版本来修复这个漏洞,所以一般情况下,我们只需要对相应的软件包进行升级到安全版本即可。通过查阅官网信息,OracleMySQLServer远程安全漏洞(CVE-2015-0411),受影响系统:OracleMySQLServer/usr/databases.sql//先备份原有所有数据,防止数据丢失。
- 过来人建议:嵌入式工程师怎么突破方向、技能、工资瓶颈?
无际单片机编程
单片机c语言嵌入式硬件嵌入式开发stm32java
上次有老铁说,想提升交际,会来事的能力。这可把我难倒了,因为我也是个社恐,以前工作,看到领导都是掉头走。而且,我个人觉得,没必要刻意去做怎样的人,每个人都有自己性格。不善于交际,不懂说漂亮的话都没关系。但是一定要厚道,真诚,认真做好每一件事,给人留好印象,说不定就有人适时拉自己一把。而且现在,我感觉时代还是有点变化的,不像以前那种酒桌文化,大家更希望的是,把事做好,别啰里吧嗦整那些虚的。这是我做自
- 渗透测试的了解
锅盖'awa'
网络安全小白之路安全性测试安全
文章目录概述一、渗透测试分类1.黑盒测试/外部测试2.白盒测试/内部测试3.灰盒测试/组合测试二、渗透测试-目标分类1、主机操作系统渗透2、数据库系统渗透3、应用系统渗透4、网络设备渗透三、渗透测试过程(七个阶段)1.前期交互阶段(Pre-EngagementInteraction)2.情报搜集阶段(InformationGathering)3.威胁建模阶段(ThreatModeling)4.漏洞
- 【网络安全】漏洞挖掘:php代码审计
秋说
网络安全phpweb安全漏洞挖掘
未经许可,不得转载。文章目录正文正文在应用程序中,通过一个JavaScript注释发现了一个备份ZIP文件。解压后,获取了应用程序的代码,其中包含如下代码片段:代码首先检查变量$action是否等于'convert',如果是,则继续执行。随后对传入的变量$data使用trim()函数去除两端空白字符,并使用eval()函数执行$data的内容。显然,代码对$data没有进行任何过滤或验证,因此可以
- 《出苍茫》 三六二 上古暴龙
佛朗西斯_阿道克
“我在光明城西门的主力损失过半,你终于要出手了。希望你不要让我失望。”海德伯格牢牢的看着塞丹,在自己的心里说道。塞丹整了整自己的魔法长袍,将帽子拉了拉,将自己的脸罩得更加严实,然后他的手中凭空幻化出一支一人多高的魔法杖。这根魔法杖是用白骨制成的,在魔法杖的顶端是一个人类的骷髅,在骷髅的两个眼眶里镶嵌着两枚红色的宝石。这让本就很诡异的骷髅看起来更加的狰狞可怖。塞丹一抖袍袖,露出了自己瘦骨嶙峋的枯槁左
- 怀孕后需要注意些啥?不同月份“注意”不同,孕妈收藏并牢记于心
市区区一品一德呀
整个孕期,如果按足月妊娠来算就是整10个月,40周共280天,这10个月又分为三个阶段,分别是怀孕早、中、晚期。怀孕早期是胚胎分化发育的阶段,当然也是流产和胎停的高发期;到了怀孕中期,也就是孕期中间的三个月,算是比较稳定的阶段,也是孕妈最舒服的阶段;怀孕晚期是最后的三个月,这个阶段胎儿随时可能出生。不同孕期的不同月份,孕妈需要注意的事项也不同。怀孕第一个月:刚怀孕,不少孕妈可能刚发现怀孕,也有的孕
- 内网穿透之EW使用、判断服务器是否出网
板栗妖怪
学习内网渗透
环境搭建使用的是下面文章的环境记一次学习--内网穿透-CSDN博客ew代理然后同样通过thinkphp漏洞写入文件,然后通过蚁剑连接然后上传ew的Linux版本,然后加权执行一层代理正向代理设置正向代理(在ubuntu上),然后kali在proxychain配置文件中连接ubuntu的192.168.244.154的代理端口反向代理在ubuntu上设置反向代理,将连接反弹到kali上的某个端口。然
- 初入职场之漏洞百出—2020-11-22
Sail2019
这是正式入职的第22天,很慌张,越是慌张越是漏洞百出。我今年已经30岁,一直在当学生,这是我正式工作的开始。30岁才初入职场,很多东西才开始学习,原来觉得很简单的事情,现在却手忙脚乱。确实应了一句话,永远没有真正的换位思考。原来以为那些工作自如、生活自如的偶像是付出了10倍努力,现在才知道也学他们付出了更多我们所不知的努力、精力,也积累了很多属于自己的财富。现在不多谈前辈,就谈我自己。我们昨天课题
- 京东规则漏洞大揭秘:如何巧妙利用规则漏洞获取优势?
高省爱氧惠
嘿,小伙伴们!你们知道吗?京东这个大宝藏里其实隐藏着好多神秘的规则漏洞,只要我们巧妙利用,就能轻松获得一些超级优势!氧惠APP(带货领导者)——是与以往完全不同的抖客+淘客app!2024全新模式,我的直推也会放到你下面。主打:带货高补贴,深受各位带货团队长喜爱(每天出单带货几十万单)。注册即可享受高补贴+0撸+捡漏等带货新体验。送万元推广大礼包,教你如何1年做到百万团队。首先,我们要明白,这些规
- 突然十句话
不改初心25
突然十句话第一句生命或许是不断地相遇。换句话说,生命或许本就是不断的错过。丑岛与犀原你们会死的。一个女孩站在马路上朝着飞奔的摩托车大喊。丑岛,那女孩是谁?柄崎踩了一脚油门,轰隆的声音让他的话有点听不清楚。不认识,后座的丑岛摇摇头,漫不经心的说。是谁呢?丑岛还是大概有点印象的。大概是叫犀什么,丑岛整了整头盔,不再去想。濑户,我们来了。濑户三兄弟正坐在废弃工厂的沙包上,直直的盯着柄崎。柄崎咽了咽口水,
- 【漏洞分享】2018年-2024年HVV 6000+个漏洞 POC 合集分享
漏洞文库-Web安全
漏洞复现web安全python安全测试工具网络安全
此份poc集成了Zabbix、用友、通达、Wordpress、Thinkcmf、Weblogic、Tomcat等下载链接:链接:https://pan.quark.cn/s/1cd7d8607b8a
- 【漏洞复现】2023HVV WPS Office 远程代码执行漏洞(RCE)
李火火安全阁
漏洞复现应用安全WPSOffice
文章目录前言声明一、漏洞描述二、影响范围三、漏洞复现服务端的功能客户端的功能四、修复建议前言2023HVV期间曝出的WPSOffice存在RCE漏洞,攻击者可通过该漏洞执行任意命令,获取服务器控制权限。声明请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
- 【漏洞利用】2018年-2024年HVV 6000+个漏洞 POC 合集分享
baiolkdnhjaio
漏洞复现网络安全web安全安全
此份poc集成了Zabbix、用友、通达、Wordpress、Thinkcmf、Weblogic、Tomcat等下载链接:链接:https://pan.quark.cn/s/1cd7d8607b8a
- 遭受挫折打击的王宝强,却在今年春晚成了大赢家,这人的经历让人深思
朱玉林
遭受挫折打击的王宝强,却在今年春晚成了大赢家,这人的经历让人深思朱玉林一提起王宝强,特别对比15年前王宝强第一次在春晚演出,让人不禁感叹,演绎路上的王宝强,不再是当年那个傻里傻气的许三多,而是一个靠自身不断拼搏,经历挫折打击后,逆袭成功,演绎生涯日渐成熟的王宝强。网友注意到,从职场小白的许三多,到演绎大咖的王宝强,人们一起看看职场许三多如何成功逆袭。作为多年前曾出名,后又落入低俗的王宝强,可能是整
- 网络安全测评技术与标准
坚持可信
信息安全web安全网络安全
网络安全测评是评估信息系统、网络和应用程序的安全性,以发现潜在的漏洞和威胁,并确保系统符合安全标准和政策的过程。以下是常见的网络安全测评类型:1.渗透测试(PenetrationTesting)描述:通过模拟真实的攻击,评估系统、网络和应用程序的安全性,识别和修复漏洞。目标:发现系统中的安全漏洞,评估其可能被利用的风险。方法:黑盒测试:测试人员没有系统内部信息,模拟外部攻击者。白盒测试:测试人员拥
- aspcms webshell漏洞复现
青衫木牛马
aspaspcmsgetshell
1.【ip】/admin_aspcms/login.asp访问后台,admin123456登录2.点击【扩展功能】【幻灯片设置】点击【保存】开启代理进行抓包3.在抓取的数据包中修改slideTextStatus字段的值为以下代码并进行发包访问影响文件字段值1%25><%25密码是a影响文件/config/AspCms_Config.asp4.蚁剑连接
- 如何提高网络安全意识
亿林网络安全事业部
网络web安全安全
提升网络安全意识的方法提升网络安全意识是个人和企业都需要重视的问题。以下是一些有效的方法:加强教育和培训:通过参加网络安全培训课程,学习识别网络攻击的常见迹象、安全密码的设置、不点击可疑链接等知识。建立网络安全政策:制定个人网络安全规则,如定期更改密码、不在公共网络上进行敏感操作等。定期更新系统:保持操作系统和软件程序的最新状态,及时修补安全漏洞。加强网络防护:使用防火墙、反病毒软件、入侵检测系统
- redis学习笔记——不仅仅是存取数据
Everyday都不同
returnSourceexpire/delincr/lpush数据库分区redis
最近项目中用到比较多redis,感觉之前对它一直局限于get/set数据的层面。其实作为一个强大的NoSql数据库产品,如果好好利用它,会带来很多意想不到的效果。(因为我搞java,所以就从jedis的角度来补充一点东西吧。PS:不一定全,只是个人理解,不喜勿喷)
1、关于JedisPool.returnSource(Jedis jeids)
这个方法是从red
- SQL性能优化-持续更新中。。。。。。
atongyeye
oraclesql
1 通过ROWID访问表--索引
你可以采用基于ROWID的访问方式情况,提高访问表的效率, , ROWID包含了表中记录的物理位置信息..ORACLE采用索引(INDEX)实现了数据和存放数据的物理位置(ROWID)之间的联系. 通常索引提供了快速访问ROWID的方法,因此那些基于索引列的查询就可以得到性能上的提高.
2 共享SQL语句--相同的sql放入缓存
3 选择最有效率的表
- [JAVA语言]JAVA虚拟机对底层硬件的操控还不完善
comsci
JAVA虚拟机
如果我们用汇编语言编写一个直接读写CPU寄存器的代码段,然后利用这个代码段去控制被操作系统屏蔽的硬件资源,这对于JVM虚拟机显然是不合法的,对操作系统来讲,这样也是不合法的,但是如果是一个工程项目的确需要这样做,合同已经签了,我们又不能够这样做,怎么办呢? 那么一个精通汇编语言的那种X客,是否在这个时候就会发生某种至关重要的作用呢?
&n
- lvs- real
男人50
LVS
#!/bin/bash
#
# Script to start LVS DR real server.
# description: LVS DR real server
#
#. /etc/rc.d/init.d/functions
VIP=10.10.6.252
host='/bin/hostname'
case "$1" in
sta
- 生成公钥和私钥
oloz
DSA安全加密
package com.msserver.core.util;
import java.security.KeyPair;
import java.security.PrivateKey;
import java.security.PublicKey;
import java.security.SecureRandom;
public class SecurityUtil {
- UIView 中加入的cocos2d,背景透明
374016526
cocos2dglClearColor
要点是首先pixelFormat:kEAGLColorFormatRGBA8,必须有alpha层才能透明。然后view设置为透明glView.opaque = NO;[director setOpenGLView:glView];[self.viewController.view setBackgroundColor:[UIColor clearColor]];[self.viewControll
- mysql常用命令
香水浓
mysql
连接数据库
mysql -u troy -ptroy
备份表
mysqldump -u troy -ptroy mm_database mm_user_tbl > user.sql
恢复表(与恢复数据库命令相同)
mysql -u troy -ptroy mm_database < user.sql
备份数据库
mysqldump -u troy -ptroy
- 我的架构经验系列文章 - 后端架构 - 系统层面
agevs
JavaScriptjquerycsshtml5
系统层面:
高可用性
所谓高可用性也就是通过避免单独故障加上快速故障转移实现一旦某台物理服务器出现故障能实现故障快速恢复。一般来说,可以采用两种方式,如果可以做业务可以做负载均衡则通过负载均衡实现集群,然后针对每一台服务器进行监控,一旦发生故障则从集群中移除;如果业务只能有单点入口那么可以通过实现Standby机加上虚拟IP机制,实现Active机在出现故障之后虚拟IP转移到Standby的快速
- 利用ant进行远程tomcat部署
aijuans
tomcat
在javaEE项目中,需要将工程部署到远程服务器上,如果部署的频率比较高,手动部署的方式就比较麻烦,可以利用Ant工具实现快捷的部署。这篇博文详细介绍了ant配置的步骤(http://www.cnblogs.com/GloriousOnion/archive/2012/12/18/2822817.html),但是在tomcat7以上不适用,需要修改配置,具体如下:
1.配置tomcat的用户角色
- 获取复利总收入
baalwolf
获取
public static void main(String args[]){
int money=200;
int year=1;
double rate=0.1;
&
- eclipse.ini解释
BigBird2012
eclipse
大多数java开发者使用的都是eclipse,今天感兴趣去eclipse官网搜了一下eclipse.ini的配置,供大家参考,我会把关键的部分给大家用中文解释一下。还是推荐有问题不会直接搜谷歌,看官方文档,这样我们会知道问题的真面目是什么,对问题也有一个全面清晰的认识。
Overview
1、Eclipse.ini的作用
Eclipse startup is controlled by th
- AngularJS实现分页功能
bijian1013
JavaScriptAngularJS分页
对于大多数web应用来说显示项目列表是一种很常见的任务。通常情况下,我们的数据会比较多,无法很好地显示在单个页面中。在这种情况下,我们需要把数据以页的方式来展示,同时带有转到上一页和下一页的功能。既然在整个应用中这是一种很常见的需求,那么把这一功能抽象成一个通用的、可复用的分页(Paginator)服务是很有意义的。
&nbs
- [Maven学习笔记三]Maven archetype
bit1129
ArcheType
archetype的英文意思是原型,Maven archetype表示创建Maven模块的模版,比如创建web项目,创建Spring项目等等.
mvn archetype提供了一种命令行交互式创建Maven项目或者模块的方式,
mvn archetype
1.在LearnMaven-ch03目录下,执行命令mvn archetype:gener
- 【Java命令三】jps
bit1129
Java命令
jps很简单,用于显示当前运行的Java进程,也可以连接到远程服务器去查看
[hadoop@hadoop bin]$ jps -help
usage: jps [-help]
jps [-q] [-mlvV] [<hostid>]
Definitions:
<hostid>: <hostname>[:
- ZABBIX2.2 2.4 等各版本之间的兼容性
ronin47
zabbix更新很快,从2009年到现在已经更新多个版本,为了使用更多zabbix的新特性,随之而来的便是升级版本,zabbix版本兼容性是必须优先考虑的一点 客户端AGENT兼容
zabbix1.x到zabbix2.x的所有agent都兼容zabbix server2.4:如果你升级zabbix server,客户端是可以不做任何改变,除非你想使用agent的一些新特性。 Zabbix代理(p
- unity 3d还是cocos2dx哪个适合游戏?
brotherlamp
unity自学unity教程unity视频unity资料unity
unity 3d还是cocos2dx哪个适合游戏?
问:unity 3d还是cocos2dx哪个适合游戏?
答:首先目前来看unity视频教程因为是3d引擎,目前对2d支持并不完善,unity 3d 目前做2d普遍两种思路,一种是正交相机,3d画面2d视角,另一种是通过一些插件,动态创建mesh来绘制图形单元目前用的较多的是2d toolkit,ex2d,smooth moves,sm2,
- 百度笔试题:一个已经排序好的很大的数组,现在给它划分成m段,每段长度不定,段长最长为k,然后段内打乱顺序,请设计一个算法对其进行重新排序
bylijinnan
java算法面试百度招聘
import java.util.Arrays;
/**
* 最早是在陈利人老师的微博看到这道题:
* #面试题#An array with n elements which is K most sorted,就是每个element的初始位置和它最终的排序后的位置的距离不超过常数K
* 设计一个排序算法。It should be faster than O(n*lgn)。
- 获取checkbox复选框的值
chiangfai
checkbox
<title>CheckBox</title>
<script type = "text/javascript">
doGetVal: function doGetVal()
{
//var fruitName = document.getElementById("apple").value;//根据
- MySQLdb用户指南
chenchao051
mysqldb
原网页被墙,放这里备用。 MySQLdb User's Guide
Contents
Introduction
Installation
_mysql
MySQL C API translation
MySQL C API function mapping
Some _mysql examples
MySQLdb
- HIVE 窗口及分析函数
daizj
hive窗口函数分析函数
窗口函数应用场景:
(1)用于分区排序
(2)动态Group By
(3)Top N
(4)累计计算
(5)层次查询
一、分析函数
用于等级、百分点、n分片等。
函数 说明
RANK() &nbs
- PHP ZipArchive 实现压缩解压Zip文件
dcj3sjt126com
PHPzip
PHP ZipArchive 是PHP自带的扩展类,可以轻松实现ZIP文件的压缩和解压,使用前首先要确保PHP ZIP 扩展已经开启,具体开启方法就不说了,不同的平台开启PHP扩增的方法网上都有,如有疑问欢迎交流。这里整理一下常用的示例供参考。
一、解压缩zip文件 01 02 03 04 05 06 07 08 09 10 11
- 精彩英语贺词
dcj3sjt126com
英语
I'm always here
我会一直在这里支持你
&nb
- 基于Java注解的Spring的IoC功能
e200702084
javaspringbeanIOCOffice
- java模拟post请求
geeksun
java
一般API接收客户端(比如网页、APP或其他应用服务)的请求,但在测试时需要模拟来自外界的请求,经探索,使用HttpComponentshttpClient可模拟Post提交请求。 此处用HttpComponents的httpclient来完成使命。
import org.apache.http.HttpEntity ;
import org.apache.http.HttpRespon
- Swift语法之 ---- ?和!区别
hongtoushizi
?swift!
转载自: http://blog.sina.com.cn/s/blog_71715bf80102ux3v.html
Swift语言使用var定义变量,但和别的语言不同,Swift里不会自动给变量赋初始值,也就是说变量不会有默认值,所以要求使用变量之前必须要对其初始化。如果在使用变量之前不进行初始化就会报错:
var stringValue : String
//
- centos7安装jdk1.7
jisonami
jdkcentos
安装JDK1.7
步骤1、解压tar包在当前目录
[root@localhost usr]#tar -xzvf jdk-7u75-linux-x64.tar.gz
步骤2:配置环境变量
在etc/profile文件下添加
export JAVA_HOME=/usr/java/jdk1.7.0_75
export CLASSPATH=/usr/java/jdk1.7.0_75/lib
- 数据源架构模式之数据映射器
home198979
PHP架构数据映射器datamapper
前面分别介绍了数据源架构模式之表数据入口、数据源架构模式之行和数据入口数据源架构模式之活动记录,相较于这三种数据源架构模式,数据映射器显得更加“高大上”。
一、概念
数据映射器(Data Mapper):在保持对象和数据库(以及映射器本身)彼此独立的情况下,在二者之间移动数据的一个映射器层。概念永远都是抽象的,简单的说,数据映射器就是一个负责将数据映射到对象的类数据。
&nb
- 在Python中使用MYSQL
pda158
mysqlpython
缘由 近期在折腾一个小东西须要抓取网上的页面。然后进行解析。将结果放到
数据库中。 了解到
Python在这方面有优势,便选用之。 由于我有台
server上面安装有
mysql,自然使用之。在进行数据库的这个操作过程中遇到了不少问题,这里
记录一下,大家共勉。
python中mysql的调用
百度之后能够通过MySQLdb进行数据库操作。
- 单例模式
hxl1988_0311
java单例设计模式单件
package com.sosop.designpattern.singleton;
/*
* 单件模式:保证一个类必须只有一个实例,并提供全局的访问点
*
* 所以单例模式必须有私有的构造器,没有私有构造器根本不用谈单件
*
* 必须考虑到并发情况下创建了多个实例对象
* */
/**
* 虽然有锁,但是只在第一次创建对象的时候加锁,并发时不会存在效率
- 27种迹象显示你应该辞掉程序员的工作
vipshichg
工作
1、你仍然在等待老板在2010年答应的要提拔你的暗示。 2、你的上级近10年没有开发过任何代码。 3、老板假装懂你说的这些技术,但实际上他完全不知道你在说什么。 4、你干完的项目6个月后才部署到现场服务器上。 5、时不时的,老板在检查你刚刚完成的工作时,要求按新想法重新开发。 6、而最终这个软件只有12个用户。 7、时间全浪费在办公室政治中,而不是用在开发好的软件上。 8、部署前5分钟才开始测试。