2)***的优点:
3)ipsec
ipsec协议是一个三层的隧道协议,标准的安全协议
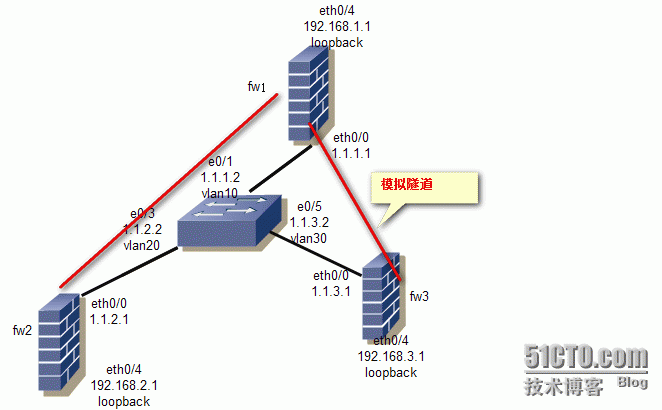
拓扑图
4)交换机的配置
创建vlan10 vlan20 vlan30 分别将Ethernet0/1 Ethernet0/3 Ethernet0/5 加入对应的vlan
配置ip
interface Vlan-interface10
ip address 1.1.1.2 255.255.255.0
#
interface Vlan-interface20
ip address 1.1.2.2 255.255.255.0
#
interface Vlan-interface30
ip address 1.1.3.2 255.255.255.0
5)Fw1配置
[H 3C ]sysname fw1
[fw1]int eth0/4
[fw1-Ethernet0/4]ip add 192.168.1.1 24 (配置端口ip)
[fw1-Ethernet0/4]loopback(由于实验没有连线,配置loopback口)
[fw1-Ethernet0/4]int eth0/0
[fw1-Ethernet0/0]ip add 1.1.1 .1 24
[fw1-Ethernet0/0]quit
[fw1]ip route-static 0.0.0 .0 0 1.1.1.2 (fw1是网络中的末梢设备需要配置默路由)
[fw1]firewall zone untrust(防火墙的端口需要加入区域)
[fw1-zone-untrust]add interface eth0/4
[fw1-zone-untrust]quit
第一条隧道(fw1-----fw2)
[fw1]acl number 3000 match-order auto(创建扩展的访问控制列表)
[fw1-acl-adv-3000]rule 10 permit ip source 192.168.1.0 0.0.0 .255 destination 192.168.2.0 0.0.0.255
(定义规则允许来源192.168.1.0网段到192.168.2.0网段)
[fw1-acl-adv-3000]quit
[fw1]ipsec proposal tran1(创建名字叫tran1的安全提议)
[fw1-ipsec-proposal-tran1]encapsulation-mode tunnel(报文封装采用隧道模式)
[fw1-ipsec-proposal-tran1]transform esp(采用esp的安全协议)
[fw1-ipsec-proposal-tran1]esp authentication-algorithm md5(采用md5校验算法)
[fw1-ipsec-proposal-tran1]esp encryption-algorithm des(采用des加密算法)
[fw1-ipsec-proposal-tran1]quit
[fw1]ipsec policy policy1 10 manual(创建名字为policy1 编号为10 的ipsec策略)(manual手工方式协商配置)
[fw1-ipsec-policy-manual-policy1-10]security acl 3000(引用访问控制列表)
[fw1-ipsec-policy-manual-policy1-10]proposal tran1(引用安全提议tran1)
[fw1-ipsec-policy-manual-policy1-10]sa spi outbound esp 12345(设置出去的spi)
[fw1-ipsec-policy-manual-policy1-10]sa spi inbound esp 54321(设置进来的spi)
[fw1-ipsec-policy-manual-policy1-10]sa string-key outbound esp abcdefg(设置出去的验证秘钥)
[fw1-ipsec-policy-manual-policy1-10]sa string-key inbound esp qazwsx(设置进来的验证秘钥)
[fw1-ipsec-policy-manual-policy1-10]tunnel local 1.1.1 .1(本端地址)
[fw1-ipsec-policy-manual-policy1-10]tunnel remote 1.1.2 .1(对端地址)
[fw1-ipsec-policy-manual-policy1-10]quit
[fw1]int eth0/0
[fw1-Ethernet0/0]ipsec policy policy1(端口上使用安全策略)
[fw1-Ethernet0/0]q
[fw1]
第二条隧道(fw1-----fw3)
[fw1]acl number 3001 match-order auto(创建3001的扩展访问控制列表)
[fw1-acl-adv-3001]rule 10 permit ip source 192.168.1.0 0.0.0 .255 destination 192.168.3.0 0.0.0.255
[fw1-acl-adv-3001]rule 20 deny ip source any destination any
[fw1-acl-adv-3001]quit
[fw1]ipsec proposal tran2
[fw1-ipsec-proposal-tran2]encapsulation-mode tunnel
[fw1-ipsec-proposal-tran2]transform esp
[fw1-ipsec-proposal-tran2]esp encryption-algorithm des
[fw1-ipsec-proposal-tran2]esp authentication-algorithm md5
[fw1-ipsec-proposal-tran2]quit
[fw1]ipsec policy policy1 20 manual
[fw1-ipsec-policy-manual-policy1-20]security acl 3001
[fw1-ipsec-policy-manual-policy1-20]proposal tran2
[fw1-ipsec-policy-manual-policy1-20]tunnel local 1.1.1 .1
[fw1-ipsec-policy-manual-policy1-20]tunnel remote 1.1.3 .1
[fw1-ipsec-policy-manual-policy1-20]sa spi outbound esp 123456
[fw1-ipsec-policy-manual-policy1-20]sa spi inbound esp 654321
[fw1-ipsec-policy-manual-policy1-20]sa string-key inbound esp qwerty
[fw1-ipsec-policy-manual-policy1-20]sa string-key outbound esp zxcvbn
6)Fw2配置
[H 3C ]sysname fw2
[fw2]int eth0/4
[fw2-Ethernet0/4]ip add 192.168.2.1 24
[fw2-Ethernet0/4]loopback
[fw2-Ethernet0/4]int eth0/0
[fw2-Ethernet0/0]ip add 1.1.2 .1 24
[fw2-Ethernet0/0]quit
[fw2]ip route-static 0.0.0 .0 0 1.1.2.2
[fw2]firewall zone untrust
[fw2-zone-untrust]add interface eth0/4
[fw2-zone-untrust]quit
[fw2]acl number 3000 match-order auto
[fw2-acl-adv-3000]rule 10 permit ip source 192.168.2.0 0.0.0 .255 destination 192.168.1.0 0.0.0.255
[fw2-acl-adv-3000]rule 20 deny ip source any destination any
[fw2-acl-adv-3000]quit
[fw2]ipsec proposal tran1
[fw2-ipsec-proposal-tran1]encapsulation-mode tunnel
[fw2-ipsec-proposal-tran1]transform esp
[fw2-ipsec-proposal-tran1]esp encryption-algorithm des
[fw2-ipsec-proposal-tran1]esp authentication-algorithm md5
[fw2-ipsec-proposal-tran1]quit
[fw2]ipsec policy policy1 10 manual
[fw2-ipsec-policy-manual-policy1-10]security acl 3000
[fw2-ipsec-policy-manual-policy1-10]proposal tran1
[fw2-ipsec-policy-manual-policy1-10]tunnel local 1.1.2 .1
[fw2-ipsec-policy-manual-policy1-10]tunnel remote 1.1.1 .1
[fw2-ipsec-policy-manual-policy1-10]sa spi inbound esp 12345
[fw2-ipsec-policy-manual-policy1-10]sa spi outbound esp 54321
[fw2-ipsec-policy-manual-policy1-10]sa string-key inbound esp abcdefg
[fw2-ipsec-policy-manual-policy1-10]sa string-key outbound esp qazwsx
[fw2-ipsec-policy-manual-policy1-10]quit
[fw2]int eth0/0
[fw2-Ethernet0/0]ipsec policy policy1
[fw2-Ethernet0/0]quit
7)fw3配置
[H 3C ]sys
[H 3C ]sysname fw3
[fw3]int eth0/4
[fw3-Ethernet0/4]ip add 192.168.3.1 24
[fw3-Ethernet0/4]loopback
[fw3-Ethernet0/4]int eth0/0
[fw3-Ethernet0/0]ip add 1.1.3 .1 24
[fw3-Ethernet0/0]quit
[fw3]ip route-static 0.0.0 .0 0 1.1.3.2
[fw3]firewall zone untrust
[fw3-zone-untrust]add interface eth0/4
System View: return to User View with Ctrl+Z.
[fw3]acl number 3000 match-order auto
[fw3-acl-adv-3000]rule 10 permit ip source 192.168.3.0 0.0.0 .255 destination 192.168.1.00.0.0.255
[fw3-acl-adv-3000]rule 20 deny ip source any destination an
[fw3-acl-adv-3000]quit
[fw3]ipsec proposal tran2
[fw3-ipsec-proposal-tran2]encapsulation-mode tunnel
[fw3-ipsec-proposal-tran2]transform esp
[fw3-ipsec-proposal-tran2]esp authentication-algorithm md5
[fw3-ipsec-proposal-tran2]esp encryption-algorithm des
[fw3-ipsec-proposal-tran2]quit
[fw3]ipsec policy policy1 10 manual
[fw3-ipsec-policy-manual-policy1-10]security acl 3000
[fw3-ipsec-policy-manual-policy1-10]proposal tran2
[fw3-ipsec-policy-manual-policy1-10]tunnel local 1.1.3 .1
[fw3-ipsec-policy-manual-policy1-10]tunnel remote 1.1.1 .1
[fw3-ipsec-policy-manual-policy1-10]sa spi inbound esp 123456
[fw3-ipsec-policy-manual-policy1-10]sa spi outbound esp 654321
[fw3-ipsec-policy-manual-policy1-10]sa string-key inbound esp zxcvbn
[fw3-ipsec-policy-manual-policy1-10]sa string-key outbound esp qwerty
[fw3-ipsec-policy-manual-policy1-10]quit
[fw3]int eth0/0
[fw3-Ethernet0/0]ipsec policy policy1
[fw3-Ethernet0/0]quit
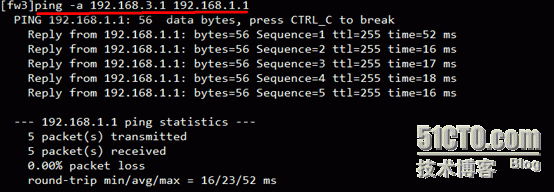
8)验证测试