Low:
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '
Your image was not uploaded.';
}
else {
// Yes!
echo "
{$target_path} succesfully uploaded!";
}
}
?>
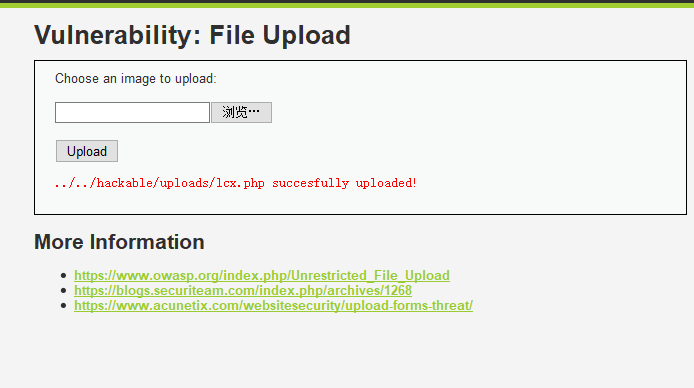
上传漏洞是有限制的,第一能上传上去,第二上传上去的文件可以被执行,第三上传路径已知
低级别就直接传一句话木马
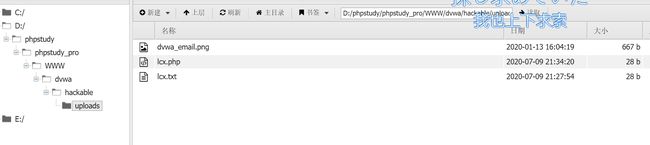
暴露出路径,蚁剑连就好
Medium:
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
// Is it an image?
if( ( $uploaded_type == "image/jpeg" || $uploaded_type == "image/png" ) &&
( $uploaded_size < 100000 ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '
Your image was not uploaded.';
}
else {
// Yes!
echo "
{$target_path} succesfully uploaded!";
}
}
else {
// Invalid file
echo '
Your image was not uploaded. We can only accept JPEG or PNG images.';
}
}
?>
嗯,对上传文件的类型大小有限制,文件类型必须是jpeg或者png,大小不能超过100000B
把lcx.php改成lcx.png,上传用burp suite抓包,把filename改成lcx.php即可,再用蚁剑连
如果PHP版本低的话Magic_quote_gpc=off,可以试试 00截断
当然一般不会有
High:
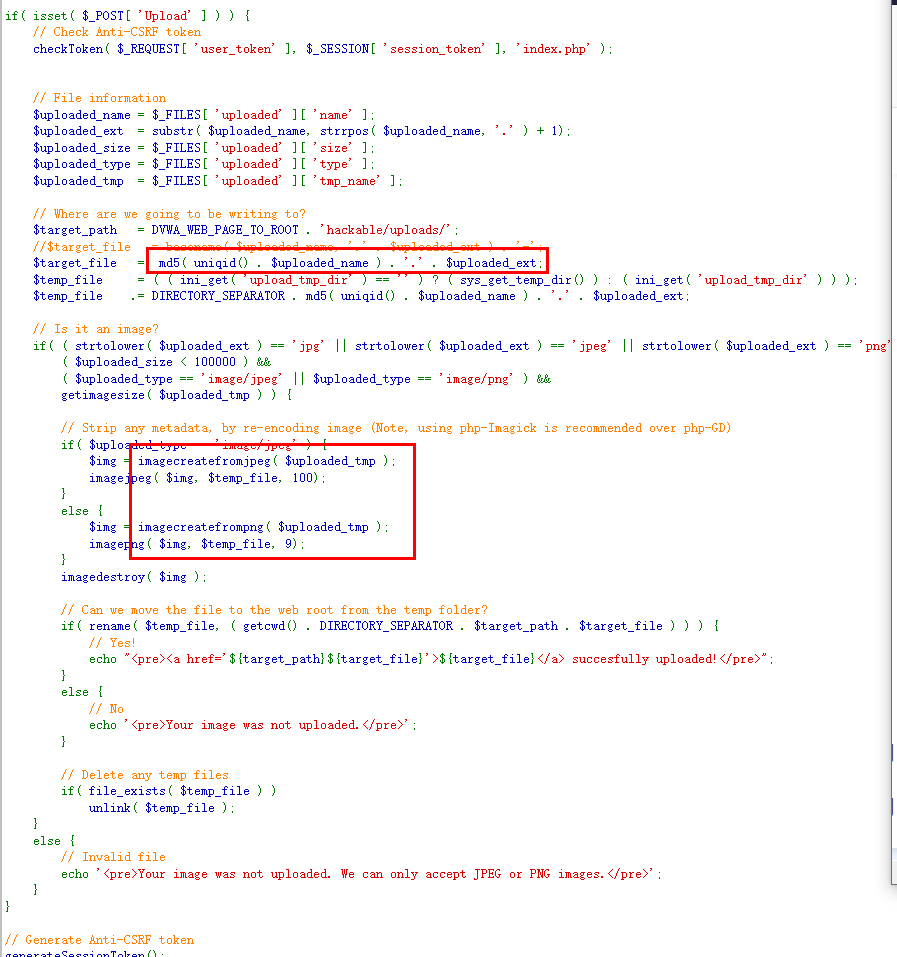
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Is it an image?
if( ( strtolower( $uploaded_ext ) == "jpg" || strtolower( $uploaded_ext ) == "jpeg" || strtolower( $uploaded_ext ) == "png" ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $uploaded_tmp, $target_path ) ) {
// No
echo '
Your image was not uploaded.';
}
else {
// Yes!
echo "
{$target_path} succesfully uploaded!";
}
}
else {
// Invalid file
echo '
Your image was not uploaded. We can only accept JPEG or PNG images.';
}
}
?>
熟悉的strrpos(string,find,start)函数,找find在string中最后一次出现的位置,start为开始搜索位置
getimagesize函数用于获取图像大小及相关信息,成功返回一个数组,失败则返回 FALSE
大致是判断了文件类型是否为.jpg .jpeg .png之一,且类型必须是图片
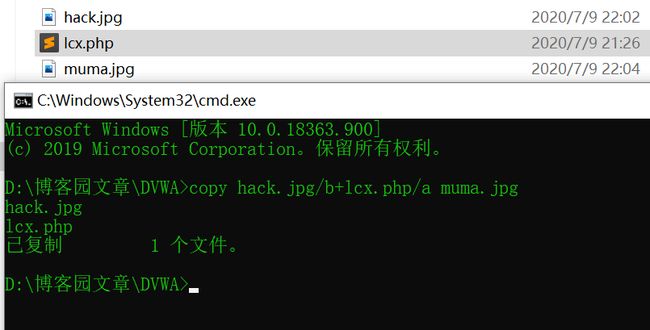
老办法,copy做一图片马
做完上传,蚁剑连接拿shell
Impossible:
此级别下首先就把上传文件重命名了,还有上传后也不显示路径了