AES128-ecb加解密
问题
最近使用AES加解密的过程中遇到了一些问题,我这段采用的是openssl的AES.h的库进行加密的,因为传输的数据并不重要,考虑到并发性和安全性的原因,采用了AES128-ecb的加密模式,然而在和对方写的C#的程序对接时发现无法实现互相加解密。
解决方法
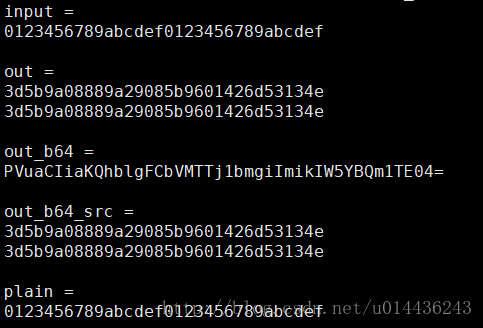
其实原因很简单,犯了个低级错误,AES128-ecb加密密钥采用了256位(32字节)的形式,而AES加密的位数是和密钥长度挂钩的,然后若是用256位的密钥则C#中相当于用AES256-ecb进行加密了,而c中因为调用的函数接口的原因,key截断为了128位还是使用的128位加密,这时候不同库间加解密通信会失败。因此AES128的密钥长度不要超过128位。
/*************************************************************************
> File Name: test_aes.c
> Author: Filon
> Created Time: Wed 06 Dec 2017 05:23:08 PM CST
************************************************************************/
#include代码中采用的AES_encrypt()函数AES_decrypt() 函数就是默认的电子密码本(ecb:electronic book),还有可以看到截断密钥的部分,实现:Link
另外,上面连接的中源码,为了加快加解密速度,是在文件中保存了一系列的表,加密过程中查表来代替计算,其原理看百科更好点。
其实还可以用下面的加密函数来替代AES_encrypt()函数AES_decrypt()这样代码的可读性更高点
void AES_ecb_encrypt(const unsigned char *in, unsigned char *out,
const AES_KEY *key, const int enc)
{
assert(in && out && key);
assert((AES_ENCRYPT == enc) || (AES_DECRYPT == enc));
if (AES_ENCRYPT == enc)
AES_encrypt(in, out, key);
else
AES_decrypt(in, out, key);
}PS: 编译的时候别忘了链接crypto的库,类似于:gcc test_aes.c -o test_aes -lcrypto