K8s第八篇Kubernetes-Dashboard
Kubernetes-Dashboard
Kubernetes Dashboard就是k8s集群的WEBUI,集合了所有命令行可以操作的所有命令。
Kubernetes Dashboard功能:
- 部署容器化的应用。
- 监控应用的状态。
- 执行故障排查任务。
- 管理Kubernetes各种资源。
- 监控集群节点的硬件资源状态。
Github:https://github.com/kubernetes/dashboard
部署Kubernetes-Dashboard:
k8smatser:
[root@k8smaster kubernetes-dashboard]# wget https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
--2020-01-02 14:39:49-- http://et/
Resolving et (et)... failed: Name or service not known.
wget: unable to resolve host address ‘et’
--2020-01-02 14:39:49-- https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.108.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4577 (4.5K) [text/plain]
Saving to: ‘kubernetes-dashboard.yaml’
100%[=================================================================================================>] 4,577 --.-K/s in 0s
2020-01-02 14:39:50 (65.7 MB/s) - ‘kubernetes-dashboard.yaml’ saved [4577/4577]
FINISHED --2020-01-02 14:39:50--
Total wall clock time: 1.3s
Downloaded: 1 files, 4.5K in 0s (65.7 MB/s)
[root@k8smaster kubernetes-dashboard]# ls
kubernetes-dashboard.yaml
[root@k8smaster kubernetes-dashboard]# ls
kubernetes-dashboard.yaml
[root@k8smaster kubernetes-dashboard]# kubectl apply -f kubernetes-dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
[root@k8smaster kubernetes-dashboard]# kubectl patch svc kubernetes-dashboard -n kube-system -p '{"spec":{"type":"NodePort"}}'
service/kubernetes-dashboard patched
[root@k8smaster kubernetes-dashboard]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 53/UDP,53/TCP,9153/TCP 65d
kubernetes-dashboard NodePort 10.104.129.230 443:30152/TCP 2m13s
traefik-ingress-service ClusterIP 10.102.130.108 80/TCP,8080/TCP 16d
traefik-web-ui ClusterIP 10.98.71.71 80/TCP 16d
#镜像下载失败,使用阿里云的镜像源。
[root@k8smaster kubernetes-dashboard]# docker pull registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
v1.10.1: Pulling from google_containers/kubernetes-dashboard-amd64
9518d8afb433: Pull complete
Digest: sha256:0ae6b69432e78069c5ce2bcde0fe409c5c4d6f0f4d9cd50a17974fea38898747
Status: Downloaded newer image for registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
[root@k8smaster kubernetes-dashboard]# docker tag registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1 k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
k8snode1:
[root@k8snode1 kubernetes-dashboard]# docker pull registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
v1.10.1: Pulling from google_containers/kubernetes-dashboard-amd64
9518d8afb433: Pull complete
Digest: sha256:0ae6b69432e78069c5ce2bcde0fe409c5c4d6f0f4d9cd50a17974fea38898747
Status: Downloaded newer image for registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
[root@k8snode1 kubernetes-dashboard]# docker tag registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1 k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
k8snode2:
[root@k8snode2 kubernetes-dashboard]# docker pull registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
v1.10.1: Pulling from google_containers/kubernetes-dashboard-amd64
9518d8afb433: Pull complete
Digest: sha256:0ae6b69432e78069c5ce2bcde0fe409c5c4d6f0f4d9cd50a17974fea38898747
Status: Downloaded newer image for registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
[root@k8snode2 kubernetes-dashboard]# docker tag registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1 k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
自建证书(默认的证书有问题,气死了!!!)
k8smatser:
[root@k8smaster kubernetes-dashboard]# mkdir tls
[root@k8smaster kubernetes-dashboard]# cd tls/
[root@k8smaster tls]# openssl genrsa -out ca.key 2048
Generating RSA private key, 2048 bit long modulus
...............................+++
....................................................+++
e is 65537 (0x10001)
[root@k8smaster tls]# openssl req -new -x509 -key ca.key -out ca.crt -days 3650 -subj "/C=CN/ST=HB/L=WH/O=DM/OU=YPT/CN=CA"
[root@k8smaster tls]# openssl x509 -in ca.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
88:42:bb:1b:0e:f9:2d:a4
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=HB, L=WH, O=DM, OU=YPT, CN=CA
Validity
Not Before: Jan 2 07:13:02 2020 GMT
Not After : Dec 30 07:13:02 2029 GMT
Subject: C=CN, ST=HB, L=WH, O=DM, OU=YPT, CN=CA
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b3:d7:15:32:f9:b0:3e:36:89:a9:70:a2:aa:ae:
12:5c:6a:6c:3f:12:6f:1d:9c:dc:18:cf:c2:40:c3:
81:8c:86:0c:fd:bb:24:e6:6c:aa:c1:b3:d4:45:52:
57:f5:88:ef:aa:74:af:a1:d1:a6:c4:fa:06:63:df:
78:41:69:a8:77:ae:a8:58:d0:11:e9:48:30:ea:a3:
6f:ac:e6:06:a6:75:fa:f0:48:9a:c4:96:ab:90:bd:
d6:eb:0c:7a:a1:4e:6b:c6:bd:0b:93:74:f6:3f:d2:
94:22:87:df:a2:dc:65:0f:aa:b1:45:e3:31:e3:14:
98:9a:b3:39:91:dd:83:05:7e:61:cd:ec:28:27:00:
46:78:1b:cc:df:69:ee:9f:7f:3d:42:4a:65:b2:e3:
b3:e5:f2:20:47:f0:88:06:6b:57:3d:2d:f1:93:12:
8a:17:a5:be:75:bf:73:2f:98:c4:83:02:7f:28:56:
0d:63:18:b0:eb:74:7b:33:e2:03:15:bf:51:74:0d:
2b:2f:3c:09:47:d6:cf:6b:3b:3d:08:d7:1e:a5:8d:
1a:79:f8:49:14:e6:69:7c:67:f3:a8:a4:3d:9f:e2:
6b:4f:cc:95:d5:98:f7:65:e8:cb:94:d3:18:3f:c7:
5d:59:a8:ac:c4:9f:84:ce:40:2b:c6:81:05:f6:82:
b2:b5
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
15:A7:E8:46:43:30:3C:43:02:75:13:98:67:CA:4F:02:53:44:89:4C
X509v3 Authority Key Identifier:
keyid:15:A7:E8:46:43:30:3C:43:02:75:13:98:67:CA:4F:02:53:44:89:4C
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
a4:87:5b:55:67:b5:6a:a6:b6:6a:ae:07:b1:36:85:9c:be:ec:
08:53:74:15:56:9b:a0:5a:99:73:ee:6a:ff:10:b1:11:ff:c7:
e0:9c:15:a5:f8:fb:3e:23:45:e9:de:c6:8f:f2:20:8c:56:21:
a4:0e:51:c9:61:80:35:9a:39:54:81:b2:48:ae:11:70:e8:85:
0c:fc:8f:0e:67:99:22:76:f3:65:3c:30:c4:b6:b4:79:da:99:
0b:0d:54:b2:eb:1f:c3:89:b0:e7:80:36:fc:01:57:87:7b:d9:
7d:4c:85:24:3c:53:38:d0:62:9c:68:c6:12:7d:0a:97:23:ea:
ba:dc:a2:11:d0:54:28:81:83:c7:55:f8:91:cf:eb:43:41:f3:
d3:de:19:0f:55:8d:18:91:2d:5f:ab:44:66:83:08:78:db:04:
46:55:17:96:a1:2b:f0:39:e8:48:4b:88:2a:09:b8:62:fc:50:
13:d1:27:46:0a:de:b3:2d:c4:58:c2:0c:45:cf:8d:3b:69:32:
a5:d8:fd:97:7e:cb:f4:1d:00:ed:bb:24:40:eb:ec:7f:09:6f:
06:eb:db:52:f1:70:88:8b:ad:4f:0e:af:bb:a4:56:29:e7:bd:
42:e4:f0:a7:31:df:6b:2c:bd:8b:30:96:22:b0:56:76:fa:20:
a7:ff:4b:22
[root@k8smaster tls]# openssl genrsa -out dashboard.key 2048
Generating RSA private key, 2048 bit long modulus
.....................................................................+++
..................................................................................... ................................................................................................................+++
e is 65537 (0x10001)
[root@k8smaster tls]# cat > dashboard.cnf < extensions = san
> [san]
> keyUsage = digitalSignature
> extendedKeyUsage = clientAuth,serverAuth
> subjectKeyIdentifier = hash
> authorityKeyIdentifier = keyid,issuer
> subjectAltName = IP:$ip,IP:127.0.0.1,DNS:$ip,DNS:localhost
> EOF
[root@k8smaster tls]# openssl x509 -req -sha256 -days 3650 -in dashboard.csr -out dashboard.crt -CA ca.crt -CAkey ca.key -CAcreateserial -extfile dashboard.cnf
Signature ok
subject=/C=CN/ST=HB/L=WH/O=DM/OU=YPT/CN=192.168.43.136
Getting CA Private Key
[root@k8smaster tls]# cd ../
[root@k8smaster kubernetes-dashboard]# kubectl create secret generic kubernetes-dashboard-certs --from-file="tls/dashboard.crt,tls/dashboard.key" -n kube-system
[root@k8smaster kubernetes-dashboard]# kubectl delete -f kubernetes-dashboard.yaml
secret "kubernetes-dashboard-certs" deleted
serviceaccount "kubernetes-dashboard" deleted
role.rbac.authorization.k8s.io "kubernetes-dashboard-minimal" deleted
rolebinding.rbac.authorization.k8s.io "kubernetes-dashboard-minimal" deleted
deployment.apps "kubernetes-dashboard" deleted
service "kubernetes-dashboard" deleted
[root@k8smaster kubernetes-dashboard]# kubectl create secret generic kubernetes-dashboard-certs --from-file="tls/dashboard.crt,tls/dashboard.key" -n kube-system
secret/kubernetes-dashboard-certs created
[root@k8smaster kubernetes-dashboard]# kubectl apply -f kubernetes-dashboard.yaml
Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply
secret/kubernetes-dashboard-certs configured
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
[root@k8smaster kubernetes-dashboard]# kubectl patch svc kubernetes-dashboard -n kube-system -p '{"spec":{"type":"NodePort"}}'
service/kubernetes-dashboard patched
[root@k8smaster kubernetes-dashboard]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 53/UDP,53/TCP,9153/TCP 65d
kubernetes-dashboard NodePort 10.107.167.69 443:31733/TCP 63s
traefik-ingress-service ClusterIP 10.102.130.108 80/TCP,8080/TCP 16d
traefik-web-ui ClusterIP 10.98.71.71 80/TCP 16d
认证:
- token:通过集群中认证的ServiceAccount的Token值来进行认证。
- 创建ServiceAccount,根据其管理目标,使用rolebinding或clusterrolebinding绑定到合理的role或者clusterrole。
- 获取到此ServiceAccount的secret,查看secret的Token值。
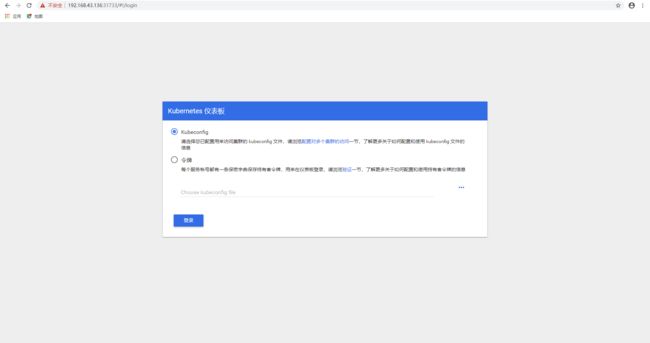
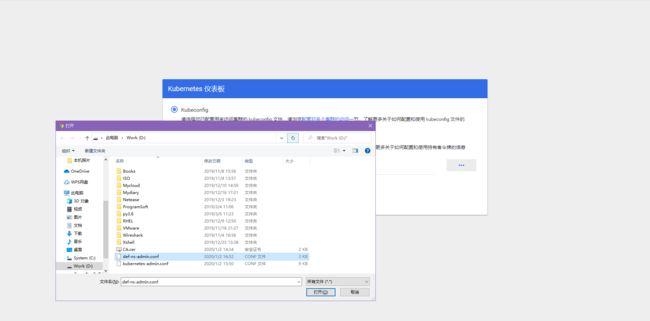
- kubeconfig:
- 创建ServiceAccount,根据其管理目标,使用rolebinding或clusterrolebinding绑定到合理的role或者clusterrole。
- 通过“DEF_NS_ADMIN_TOKEN=$(kubectl get secret SERVICEACCOUNT_SECRET_NAME -o jsonpath={.data.token} | base64 -d) ”这条命令定义DEF_NS_ADMIN_TOKEN变量为ServiceAccount的secret的Token值。
- 生成kubeconfig文件。
- kubectl config set-credentials def-ns-admin --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/def-ns-admin.conf
- kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf
- kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf
创建ServiceAccount(提供token认证):
#创建一个ServiceAccount,绑定到cluster-admin,让它具有对整个k8s集群的控制权限
[root@k8smaster kubernetes-dashboard]# kubectl create serviceaccount dashboard-admin -n kube-system
serviceaccount/dashboard-admin created
[root@k8smaster kubernetes-dashboard]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created
[root@k8smaster kubernetes-dashboard]# kubectl describe secret dashboard-admin-token-txf8r -n kube-system
Name: dashboard-admin-token-txf8r
Namespace: kube-system
Labels:
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: 9f4cd171-7eba-4df8-9bcf-c80c92067769
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdHhmOHIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiOWY0Y2QxNzEtN2ViYS00ZGY4LTliY2YtYzgwYzkyMDY3NzY5Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.rzA3VSSEwcSljh-33jk0bJ7WbHJwi7q2FQnEavhi21GQ_aezI0Bmww1T9R02tlIHALFhHbbAXAyDxmGmbMR6IZyrgAFrUc4ici-KCkh0_u9XSRIH-GhJPBbjyHohMsJFSeLaM4IEI6MaxYVIMujJwe-yizyyO59ou3VmVtORQKMB3BIodY_uVx7mLruppdlmybiMwi3uDKhIPCJZvLN8Nbu4bAHw-8LWWpbN0kzqCoYR12QD4Mtx47HxbEqp_Jv79oOaqfBJlYxKxijZE39t0wGN7WGRaqpRHM7nYMWg9WSNN6FOWlhQGcp5q-auIlx4GzNjeDENj1qAAiTOPwXSrg
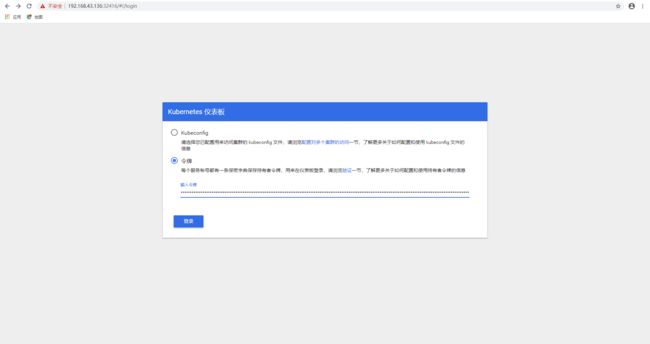
复制dashboard-admin-token-txf8r的Token,粘贴到此处:
创建一个认证文件:
#创建一个serviceaccount,并把它绑定到admin,只具有default名称空间的管理权限。
[root@k8smaster kubernetes-dashboard]# kubectl create serviceaccount def-ns-admin -n default
serviceaccount/def-ns-admin created
[root@k8smaster kubernetes-dashboard]# kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin
rolebinding.rbac.authorization.k8s.io/def-ns-admin created
[root@k8smaster kubernetes-dashboard]# kubectl get secret
NAME TYPE DATA AGE
admin-token-bs7sd kubernetes.io/service-account-token 3 47h
def-ns-admin-token-flw6j kubernetes.io/service-account-token 3 2m4s
default-token-kk2fq kubernetes.io/service-account-token 3 65d
mysql-root-password Opaque 1 12d
[root@k8smaster kubernetes-dashboard]# DEF_NS_ADMIN_TOKEN=$(kubectl get secret def-ns-admin-token-flw6j -o jsonpath={.data.token} | base64 -d)
[root@k8smaster kubernetes-dashboard]# kubectl config set-cluster kubernetes --certificate-authority=./tls/ca.crt --server="https://192.168.43.45:6443" --embed-certs=true --kubeconfig=/root/def-ns-admin.conf
Cluster "kubernetes" set.
[root@k8smaster kubernetes-dashboard]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.43.45:6443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
[root@k8smaster kubernetes-dashboard]# kubectl config set-credentials def-ns-admin --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/def-ns-admin.conf
User "def-ns-admin" set.
[root@k8smaster kubernetes-dashboard]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.43.45:6443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1mbHc2aiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJkNjk1Yzc5OC1jYTU3LTQ0OGItYjY2My1kNGIyZTcxNzFjN2MiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.FAUUbzFpcYaRVtJSdP8ehJf8DQi6wHHcJZjjffGuKeW0IlNEvD20FMm-5W5nXprll4Fbk238mtnnER0IUSchaTH2dj64WDwyLqtlecKI4UzIyZkDWV2JQM8iDGtL7m53XCF9Syw5ajp6RHaPU5U1GDU3ULp79oPZgXKcibY0JA7qSQpVitDiJM80GidT2TiarwXu6tToW5Y9iV0Xt-FrwKvJIcnpGgn3EFycLiA7Pwn-oty7Xi-mGIQW3JGsXC0_rBIBNy578a7ak4tIIEJT-qJE1nnmjNNSUqxqXFPb2aXnoDTST7Y-N_ZCzy_OzxpPvQqKPcr0JY3jpCwmLfMAkw
[root@k8smaster kubernetes-dashboard]# kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf
Context "def-ns-admin@kubernetes" created.
[root@k8smaster kubernetes-dashboard]# kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf
Switched to context "def-ns-admin@kubernetes".
[root@k8smaster kubernetes-dashboard]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.43.45:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: def-ns-admin
name: def-ns-admin@kubernetes
current-context: def-ns-admin@kubernetes
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1mbHc2aiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJkNjk1Yzc5OC1jYTU3LTQ0OGItYjY2My1kNGIyZTcxNzFjN2MiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.FAUUbzFpcYaRVtJSdP8ehJf8DQi6wHHcJZjjffGuKeW0IlNEvD20FMm-5W5nXprll4Fbk238mtnnER0IUSchaTH2dj64WDwyLqtlecKI4UzIyZkDWV2JQM8iDGtL7m53XCF9Syw5ajp6RHaPU5U1GDU3ULp79oPZgXKcibY0JA7qSQpVitDiJM80GidT2TiarwXu6tToW5Y9iV0Xt-FrwKvJIcnpGgn3EFycLiA7Pwn-oty7Xi-mGIQW3JGsXC0_rBIBNy578a7ak4tIIEJT-qJE1nnmjNNSUqxqXFPb2aXnoDTST7Y-N_ZCzy_OzxpPvQqKPcr0JY3jpCwmLfMAkw
把/root/def-ns-admin.conf这个文件复制到宿主机中:
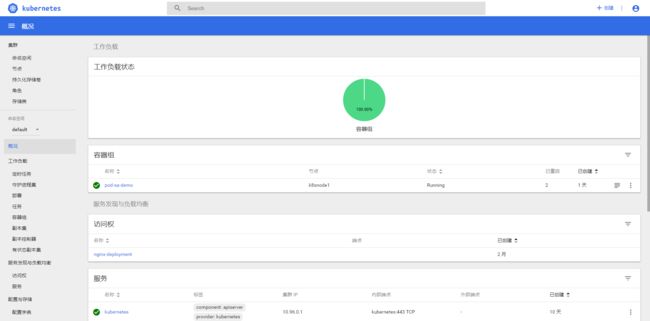
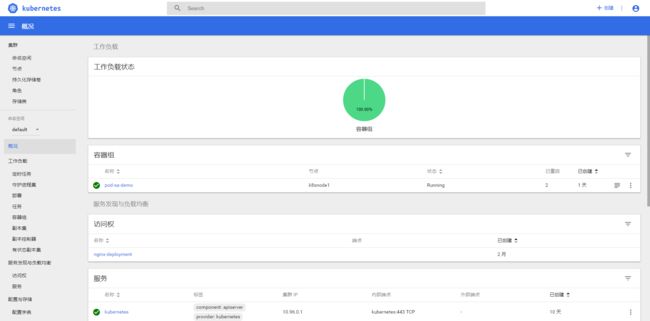
Dashboard界面结构分为三个大的区域:
- 顶部操作区:在这里用户可以搜索集群中的资源、创建资源或退出。
- 左边导航菜单:通过导航菜单可以查看和管理集群中的各种资源。菜单项按照资源的层级分为两类:Cluster 级别的资源 ,Namespace 级别的资源 ,默认显示的是 default Namespace,可以进行切换。
- 中间主体区:在导航菜单中点击了某类资源,中间主体区就会显示该资源所有实例,比如点击 Pods。