kubernetes:资源监控(metrics-server部署、dashboard部署)
kubernetes
- 1. metrics server是什么
- 2. metrics-server部署
- 3. dashboard部署
1. metrics server是什么
Metrics-Server是集群核心监控数据的聚合器,用来替换之前的heapster。
容器相关的 Metrics 主要来自于 kubelet 内置的 cAdvisor 服务,有了Metrics-Server之后,用户就可以通过标准的 Kubernetes API 来访问到这些监控数据。
Metrics API 只可以查询当前的度量数据,并不保存历史数据。
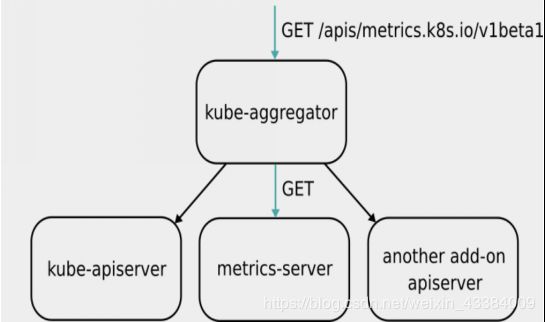
Metrics API URI 为 /apis/metrics.k8s.io/,在 k8s.io/metrics 维护。
必须部署 metrics-server 才能使用该 API,metrics-server 通过调用 Kubelet Summary API 获取数据。
Metrics Server 并不是 kube-apiserver 的一部分,而是通过 Aggregator(聚合器) 这种插件机制,在独立部署的情况下同 kube-apiserver 一起统一对外服务的。
kube-aggregator 其实就是一个根据 URL 选择具体的 API 后端的代理服务器
Metrics-server属于Core metrics(核心指标),提供API metrics.k8s.io,仅提供Node和Pod的CPU和内存使用情况。而其他Custom Metrics(自定义指标)由Prometheus等组件来完成。
2. metrics-server部署
metrics-server官方网站:https://github.com/kubernetes-sigs/metrics-server
[kubeadm@server2 ~]$ wget https://github.com/kubernetes-sigs/metrics-server/releases/download/v0.3.6/components.yaml # 下载部署文件
[kubeadm@server2 ~]$ cat components.yaml
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: system:aggregated-metrics-reader
labels:
rbac.authorization.k8s.io/aggregate-to-view: "true"
rbac.authorization.k8s.io/aggregate-to-edit: "true"
rbac.authorization.k8s.io/aggregate-to-admin: "true"
rules:
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: metrics-server:system:auth-delegator
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:auth-delegator
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: metrics-server-auth-reader
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: extension-apiserver-authentication-reader
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
---
apiVersion: apiregistration.k8s.io/v1beta1
kind: APIService
metadata:
name: v1beta1.metrics.k8s.io
spec:
service:
name: metrics-server
namespace: kube-system
group: metrics.k8s.io
version: v1beta1
insecureSkipTLSVerify: true
groupPriorityMinimum: 100
versionPriority: 100
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: metrics-server
namespace: kube-system
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: metrics-server
namespace: kube-system
labels:
k8s-app: metrics-server
spec:
selector:
matchLabels:
k8s-app: metrics-server
template:
metadata:
name: metrics-server
labels:
k8s-app: metrics-server
spec:
serviceAccountName: metrics-server
volumes:
# mount in tmp so we can safely use from-scratch images and/or read-only containers
- name: tmp-dir
emptyDir: {}
containers:
- name: metrics-server
image: metrics-server-amd64:v0.3.6 # 我将metrics-server-amd64:v0.3.6镜像文件放到了我自己的私有仓库中,所以修改了镜像地址
imagePullPolicy: IfNotPresent
args:
- --cert-dir=/tmp
- --secure-port=4443
ports:
- name: main-port
containerPort: 4443
protocol: TCP
securityContext:
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 1000
volumeMounts:
- name: tmp-dir
mountPath: /tmp
nodeSelector:
kubernetes.io/os: linux
kubernetes.io/arch: "amd64"
---
apiVersion: v1
kind: Service
metadata:
name: metrics-server
namespace: kube-system
labels:
kubernetes.io/name: "Metrics-server"
kubernetes.io/cluster-service: "true"
spec:
selector:
k8s-app: metrics-server
ports:
- port: 443
protocol: TCP
targetPort: main-port
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: system:metrics-server
rules:
- apiGroups:
- ""
resources:
- pods
- nodes
- nodes/stats
- namespaces
- configmaps
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: system:metrics-server
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:metrics-server
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
[kubeadm@server2 ~]$ kubectl apply -f components.yaml # 通过yaml文件自动部署
clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created
clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created
rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created
apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created
serviceaccount/metrics-server created
deployment.apps/metrics-server created
service/metrics-server created
clusterrole.rbac.authorization.k8s.io/system:metrics-server created
clusterrolebinding.rbac.authorization.k8s.io/system:metrics-server created
[kubeadm@server2 ~]$ kubectl -n kube-system get pod -o wide # metrics-server运行成功,但是还无法使用
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
metrics-server-7cdfcc6666-2xxd5 1/1 Running 0 62s 10.244.1.139 server3 <none> <none>
[kubeadm@server2 ~]$ kubectl -n kube-system logs metrics-server-7cdfcc6666-2xxd5 # 会出现无法解析的错误
dial tcp: lookup server4 on 10.96.0.10:53: no such host
原因是没有内网的DNS服务器,所以metrics-server无法解析节点名字。可以直接修改coredns的configmap,讲各个节点的主机名加入到hosts中,这样所有Pod都可以从CoreDNS中解析各个节点的名字
解决方法:在coredns中写入解析地址
[kubeadm@server2 ~]$ kubectl -n kube-system edit cm coredns
ready
hosts {
172.25.60.2 server2
172.25.60.3 server3
172.25.60.4 server4
fallthrough
}
kubernetes cluster.local in-addr.arpa ip6.arpa {
[kubeadm@server2 ~]$ kubectl -n kube-system logs metrics-server-7cdfcc6666-2xxd5 # 再次查看日志,出现x509: certificate signed by unknown authority的错误
解决方法:
Metric Server 支持一个参数 --kubelet-insecure-tls,可以跳过这一检查,但是官方不推荐使用。
[root@server2 ~]# vim /var/lib/kubelet/config.yaml # 启用TLS Bootstrap 证书签发
serverTLSBootstrap: true # 在最后添加
[root@server2 ~]# systemctl restart kubelet
[kubeadm@server2 ~]$ kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
csr-gjf9h 113s kubernetes.io/kubelet-serving system:node:server2 Pending
[kubeadm@server2 ~]$ kubectl certificate approve csr-gjf9h # 绑定证书(证书签名)
certificatesigningrequest.certificates.k8s.io/csr-gjf9h approved
[kubeadm@server2 ~]$ kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
csr-gjf9h 5m14s kubernetes.io/kubelet-serving system:node:server2 Approved,Issued
[kubeadm@server2 ~]$ kubectl top node # server2上绑定了证书,但是server3和server4还没有
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
server2 80m 4% 940Mi 49%
server3 <unknown> <unknown> <unknown> <unknown>
server4 <unknown> <unknown> <unknown> <unknown>
将server3和server4,启用TLS Bootstrap 证书签发
[root@server4 ~]# vim /var/lib/kubelet/config.yaml
serverTLSBootstrap: true
[root@server4 ~]# systemctl restart kubelet
[root@server3 ~]# vim /var/lib/kubelet/config.yaml
serverTLSBootstrap: true
[root@server3 ~]# systemctl restart kubelet
在server2上将server3和server4上的证书签名
[kubeadm@server2 ~]$ kubectl certificate approve csr-bgcws
certificatesigningrequest.certificates.k8s.io/csr-bgcws approved
[kubeadm@server2 ~]$ kubectl certificate approve csr-f8pkn
certificatesigningrequest.certificates.k8s.io/csr-f8pkn approved
[kubeadm@server2 ~]$ kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
csr-bgcws 87s kubernetes.io/kubelet-serving system:node:server3 Approved,Issued
csr-f8pkn 2m17s kubernetes.io/kubelet-serving system:node:server4 Approved,Issued
csr-gjf9h 44m kubernetes.io/kubelet-serving system:node:server2 Approved,Issued
[kubeadm@server2 ~]$ kubectl top node
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
server2 93m 4% 946Mi 49%
server3 25m 2% 368Mi 19%
server4 40m 2% 466Mi 24%
添加epel的源
[root@server2 yum.repos.d]# cat epel-7.repo
[epel]
name=epel
baseurl=http://mirrors.aliyun.com/epel/7/x86_64/
enabled=1
gpgcheck=0
[root@server2 yum.repos.d]# yum install jq # 安装jq,jq在epel源中
[kubeadm@server2 ~]$ kubectl get --raw "/apis/metrics.k8s.io/v1beta1/nodes/server2"|jq
{
"kind": "NodeMetrics",
"apiVersion": "metrics.k8s.io/v1beta1",
"metadata": {
"name": "server2",
"selfLink": "/apis/metrics.k8s.io/v1beta1/nodes/server2",
"creationTimestamp": "2020-05-08T14:35:01Z"
},
"timestamp": "2020-05-08T14:34:21Z",
"window": "30s",
"usage": {
"cpu": "94782555n",
"memory": "1053160Ki"
}
}
3. dashboard部署
Dashboard可以给用户提供一个可视化的 Web 界面来查看当前集群的各种信息。用户可以用 Kubernetes Dashboard 部署容器化的应用、监控应用的状态、执行故障排查任务以及管理 Kubernetes 各种资源。
官方网站:https://github.com/kubernetes/dashboard
[kubeadm@server2 ~]$ wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0/aio/deploy/recommended.yaml # 下载部署文件,如果无法下载到官方网站复制
[kubeadm@server2 ~]$ cat recommended.yaml
# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
apiVersion: v1
kind: Namespace
metadata:
name: kubernetes-dashboard
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kubernetes-dashboard
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kubernetes-dashboard
type: Opaque
data:
csrf: ""
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kubernetes-dashboard
type: Opaque
---
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kubernetes-dashboard
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules:
# Allow Metrics Scraper to get metrics from the Metrics server
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.0.0
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
ports:
- port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraper
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
annotations:
seccomp.security.alpha.kubernetes.io/pod: 'runtime/default'
spec:
containers:
- name: dashboard-metrics-scraper
image: kubernetesui/metrics-scraper:v1.0.4
ports:
- containerPort: 8000
protocol: TCP
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- mountPath: /tmp
name: tmp-volume
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
volumes:
- name: tmp-volume
emptyDir: {}
在私有仓库上传metrics-scraper和dashboard镜像
docker pull kubernetesui/dashboard:v2.0.0
docker pull kubernetesui/metrics-scraper:v1.0.4
docker push reg.westos.org/kubernetesui/dashboard
docker push reg.westos.org/kubernetesui/metrics-scraper
[kubeadm@server2 ~]$ kubectl apply -f recommended.yaml # 部署dashboard
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
[kubeadm@server2 ~]$ kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.98.244.13 <none> 8000/TCP 3m40s
kubernetes-dashboard ClusterIP 10.110.127.113 <none> 443/TCP 3m42s
[kubeadm@server2 ~]$ kubectl edit svc kubernetes-dashboard -n kubernetes-dashboard # 将type改为nodeport,通过外网访问
type: NodePort
[kubeadm@server2 ~]$ kubectl describe svc kubernetes-dashboard -n kubernetes-dashboard
Name: kubernetes-dashboard
Namespace: kubernetes-dashboard
Labels: k8s-app=kubernetes-dashboard
Annotations: Selector: k8s-app=kubernetes-dashboard
Type: NodePort
IP: 10.110.127.113
Port: <unset> 443/TCP
TargetPort: 8443/TCP
NodePort: <unset> 30836/TCP
Endpoints: 10.244.1.140:8443
Session Affinity: None
External Traffic Policy: Cluster
Events: <none>
[kubeadm@server2 ~]$ kubectl get pod -n kubernetes-dashboard -o wide # dashboard运行在server3上
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
dashboard-metrics-scraper-6b4884c9d5-hhhms 1/1 Running 0 10m 10.244.2.125 server4 <none> <none>
kubernetes-dashboard-7b544877d5-2xm64 1/1 Running 0 10m 10.244.1.140 server3 <none> <none>
[kubeadm@server2 ~]$ kubectl get svc -n kubernetes-dashboard -o wide # 查看访问端口为30836
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
dashboard-metrics-scraper ClusterIP 10.98.244.13 <none> 8000/TCP 10m k8s-app=dashboard-metrics-scraper
kubernetes-dashboard NodePort 10.110.127.113 <none> 443:30836/TCP 11m k8s-app=kubernetes-dashboard
[kubeadm@server2 ~]$ kubectl -n kubernetes-dashboard get secrets
NAME TYPE DATA AGE
default-token-h74pl kubernetes.io/service-account-token 3 18m
kubernetes-dashboard-certs Opaque 0 18m
kubernetes-dashboard-csrf Opaque 1 18m
kubernetes-dashboard-key-holder Opaque 2 18m
kubernetes-dashboard-token-s6drj kubernetes.io/service-account-token 3 18m
[kubeadm@server2 ~]$ kubectl -n kubernetes-dashboard describe secrets kubernetes-dashboard-token-s6drj # 查看token
Name: kubernetes-dashboard-token-s6drj
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: kubernetes-dashboard
kubernetes.io/service-account.uid: 16c26a19-386b-4b36-8548-3f41d5c4a2c0
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlNWeUFZZ2lGcXJlaGp3WERKMFdOX19McGttcm5QNW96bFMzenoxY0pVdEUifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi1zNmRyaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjE2YzI2YTE5LTM4NmItNGIzNi04NTQ4LTNmNDFkNWM0YTJjMCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.fkXsWiYHyrgmxcuX2xD_HAO8CIgpMKF5E2IITx_7XAHHiSfTYpz5rVqHSkhQjbWvlmNQ9MP4xZnZtUU76_AWHOgl2oBuwSQFso6Y54J6Rt3JQPGJ3DlxOGrF0wUDK1_6kFSjriHQoTBG8Q6RHRGhylrhoNQ7c-90vzYfP_RgWThSKLOcoJrkxlacR9Pr0FSUnAsFaQXAk3rx4OKFDpUhBa47DEVf2v6sRAgThpblDQo4kQ01dhfLfWyw6LIbd_Il5DV4fKVTZTeMRNmKkrANKzllDYFowFCQYXYOxWZkRXivw0ahVUikZJzkMVXEa4fJIE1cmeLq_10-cG2ktc7dRw
将token粘贴到页面中的token中
[kubeadm@server2 ~]$ kubectl -n kubernetes-dashboard get sa # 使用kubernetes-dashboard服务账户
NAME SECRETS AGE
default 1 23m
kubernetes-dashboard 1 23m
[kubeadm@server2 ~]$ \vi dashrbac.yaml # 用户授权
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
[kubeadm@server2 ~]$ kubectl apply -f dashrbac.yaml
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-admin created
[kubeadm@server2 ~]$ kubectl get apiservices.apiregistration.k8s.io
v1beta1.metrics.k8s.io kube-system/metrics-server True 4h41m