cas5.3.5错误锦集
0.cas jar--https://repo.maven.apache.org/maven2/org/apereo/cas/
1.票根'ST-7--yOPMHIBFVcx8iNRoDW-rCzNgakLAPTOP-E2N0LMKU'不符合目标服务
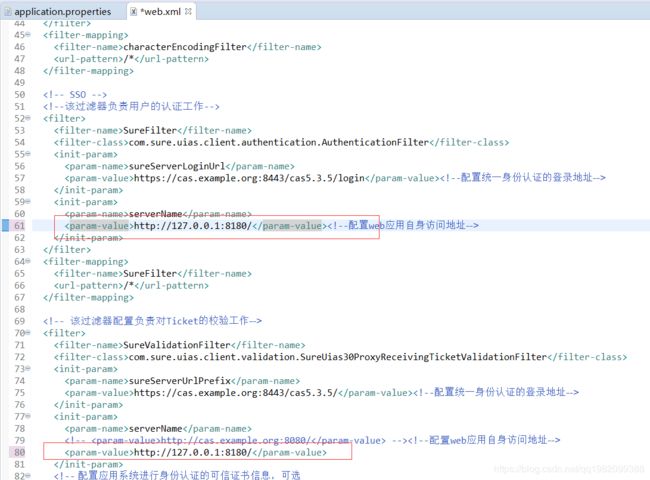
原因:下面的servername应该配置客户端访问的地址:ip+端口
另外:注册服务中services的过滤配置要与此一致,不然cas登录后会出现未授权服务
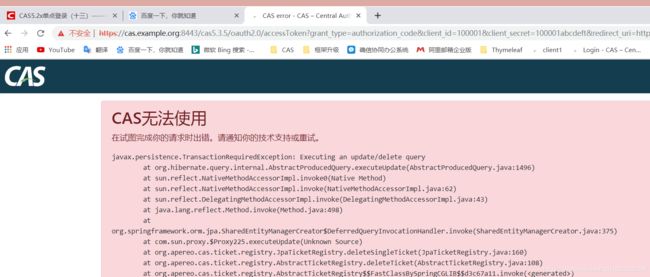
2.加入oauth2.0服务端,正常;再加入jpa票据持久化,发现,获取不到oauth2的accesstoken了,并出现一下异常
解决方式:#numberOfUses 默认是1,但是不能用,最小是2?
cas.authn.oauth.code.numberOfUses=2
mmp这个破问题卡了一个周,实在坑,好尿性
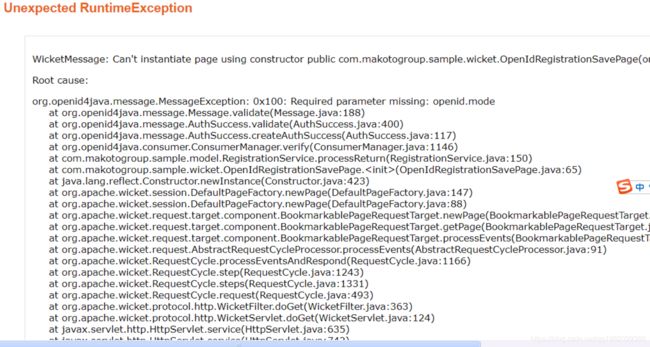
3.单点登出:Cannot delete or update a parent row: a foreign key和map[[empty]]----图忘记截了
解决方式:将oauth_tokens和tgt两个表的fk options 由restrict改为cascade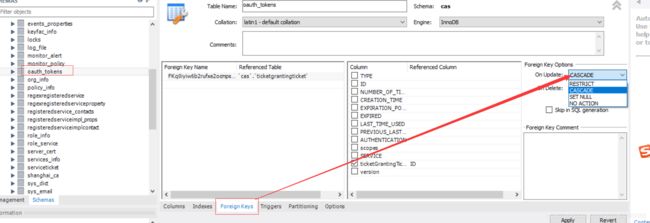
4.添加多行属性返回时,类似异常如下:
解决方法:cas.authn.jdbc.query[0].isolateInternalQueries=false--暂时不报异常了,但是多行属性没有返回。。。
5.cas-management-overlay 添加依赖:注意版本号,否则spring容易冲突
6.cas-management登录后
解决方式:5作废,pom修改如下:---->结果发现依然搞不定,5能解决springjar包冲突,但是会出现登陆后访问不了应用,修改如下,会出现jar包冲突,手动把web-inf-->lib下的冲突jar包删除吧。。。(暂且这样用叭,本渣放弃了)
7.oauth2授权登陆
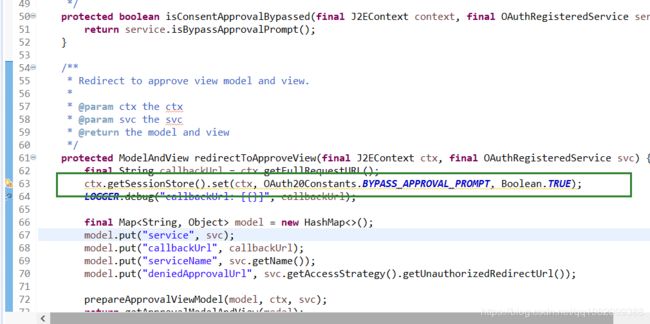
oauth2授权登录的时候,登录后不点击允许,然后新开一个页面也能登录成功啊
解决方法:修改confirm.html页面的点击事件,将true的设置放到点击事件里面,不要提前在后台写死
8.开始saml
8.1客户端导入jar:
cas-client-support-saml-3.5.0.jar
joda-time-2.9.9.jar
8.2客户端配置filter:
org.jasig.cas.client.authentication.Saml11AuthenticationFilter
org.jasig.cas.client.validation.Saml11TicketValidationFilter
8.3客户端添加xml:src\META-INF\cassamlRequestTemplate.xml
8.4服务端添加jar:
aws-java-sdk-core-1.11.332.jar
aws-java-sdk-s3-1.11.332.jar
cas-server-support-saml-5.3.5.jar
cas-server-support-saml-idp-5.3.5.jar
cas-server-support-saml-idp-core-5.3.5.jar
cas-server-support-saml-idp-metadata-5.3.5.jar
cas-server-support-saml-idp-ticket-5.3.5.jar
cas-server-support-saml-idp-web-5.3.5.jar
cas-server-support-saml-mdui-core-5.3.5.jar
idp-attribute-api-3.4.0.jar
idp-attribute-api-3.4.0-sources.jar
idp-attribute-filter-api-3.4.0.jar
idp-attribute-filter-api-3.4.0-sources.jar
idp-attribute-resolver-api-3.4.0.jar
idp-attribute-resolver-api-3.4.0-sources.jar
idp-authn-api-3.4.0.jar
idp-authn-api-3.4.0-sources.jar
idp-core-3.4.0.jar
idp-core-3.4.0-sources.jar
idp-profile-api-3.4.0.jar
idp-profile-api-3.4.0-sources.jar
idp-profile-impl-3.4.0.jar
idp-profile-impl-3.4.0-sources.jar
idp-profile-spring-3.4.0-sources.jar
idp-saml-api-3.4.0.jar
idp-saml-api-3.4.0-sources.jar
idp-saml-impl-3.4.0.jar
idp-saml-impl-3.4.0-sources.jar
idp-schema-3.4.0.jar
idp-schema-3.4.0-sources.jar
idp-session-api-3.4.0.jar
idp-session-api-3.4.0-sources.jar
idwsfconsumer-1.0.0.jar
idwsfconsumer-1.0.0-sources.jar
java-support-7.3.0.jar
java-support-7.3.0-sources.jar
java-support-7.4.0-sources.jar
jdom-1.1.jar
opensaml-messaging-api-3.4.0.jar
spring-extensions-5.4.0.jar
spring-extensions-5.4.0-sources.jar
xercesImpl-2.9.1.jar
xmlsectool-2.0.0-sources.jar
8.5服务端相关application.properties(不晓得有用没用先加上)
#SAML Core
cas.samlCore.ticketidSaml2=false
cas.samlCore.skewAllowance=5
cas.samlCore.issueLength=30
cas.samlCore.attributeNamespace=https://cas.example.org:8443/cas5.3.5/
cas.samlCore.issuer=localhost
cas.samlCore.securityManager=org.apache.xerces.util.SecurityManager
#SAML IdP
cas.authn.samlIdp.entityId=https://cas.example.org:8443/cas5.3.5/idp
cas.authn.samlIdp.scope=example.org
cas.authn.samlIdp.authenticationContextClassMappings[0]=urn:oasis:names:tc:SAML:2.0:ac:classes:SomeClassName->mfa-duo
cas.authn.samlIdp.authenticationContextClassMappings[1]=https://refeds.org/profile/mfa->mfa-gauth
cas.authn.samlIdp.attributeQueryProfileEnabled=true
#SAML Metadata
cas.authn.samlIdp.metadata.location=file:/etc/cas/saml
cas.authn.samlIdp.metadata.cacheExpirationMinutes=30
cas.authn.samlIdp.metadata.failFast=true
cas.authn.samlIdp.metadata.privateKeyAlgName=RSA
cas.authn.samlIdp.metadata.requireValidMetadata=true
cas.authn.samlIdp.metadata.basicAuthnUsername=
cas.authn.samlIdp.metadata.basicAuthnPassword=
cas.authn.samlIdp.metadata.supportedContentTypes=
#samlIdp jpa
cas.authn.samlIdp.metadata.jpa.user=${cas.authn.jdbc.query[0].user}
cas.authn.samlIdp.metadata.jpa.password=${cas.authn.jdbc.query[0].password}
cas.authn.samlIdp.metadata.jpa.driverClass=${cas.authn.jdbc.query[0].driverClass}
cas.authn.samlIdp.metadata.jpa.url=${cas.authn.jdbc.query[0].url}
cas.authn.samlIdp.metadata.jpa.dialect=${cas.authn.jdbc.query[0].dialect}
cas.authn.samlIdp.metadata.jpa.failFastTimeout=1
#cas.authn.samlIdp.metadata.jpa.isolationLevelName=ISOLATION_READ_COMMITTED
cas.authn.samlIdp.metadata.jpa.healthQuery=
cas.authn.samlIdp.metadata.jpa.isolateInternalQueries=false
cas.authn.samlIdp.metadata.jpa.leakThreshold=10
#cas.authn.samlIdp.metadata.jpa.propagationBehaviorName=PROPAGATION_REQUIRED
cas.authn.samlIdp.metadata.jpa.batchSize=1
cas.authn.samlIdp.metadata.jpa.defaultCatalog=
cas.authn.samlIdp.metadata.jpa.defaultSchema=
cas.authn.samlIdp.metadata.jpa.ddlAuto=update
cas.authn.samlIdp.metadata.jpa.autocommit=false
cas.authn.samlIdp.metadata.jpa.idleTimeout=5000
cas.authn.samlIdp.metadata.jpa.dataSourceName=
cas.authn.samlIdp.metadata.jpa.dataSourceProxy=false
#Hibernate-specific properties (i.e. `hibernate.globally_quoted_identifiers`)
cas.authn.samlIdp.metadata.jpa.properties.propertyName=propertyValue
cas.authn.samlIdp.metadata.jpa.pool.suspension=false
cas.authn.samlIdp.metadata.jpa.pool.minSize=6
cas.authn.samlIdp.metadata.jpa.pool.maxSize=18
cas.authn.samlIdp.metadata.jpa.pool.maxWait=2000
cas.authn.samlIdp.metadata.jpa.pool.timeoutMillis=1000
9.设置initfromjson=true:设置regexregisteredservice表的id为主键并自增
10.系统单集成openid能正常使用;在系统已经集成oauth2、saml2、oidc的基础上增加openid出现问题:
经过测试:openid+oauth2--ok;openid+oauth2+saml--ok;
问题根源:有两个cas.js,老版本的cas.js和新版本的cas.js冲突,导致form提交的时候没有将url中的参数提交。