华为HCNA之配置RIPv2认证实验
导语:
RIPv2认证可以降低设备接受非法路由选择更新消息的可靠性,非法的更新消息可能来自试图破坏网络的攻击者,或试图通过欺骗路由器发送数据到错误的目的地址的方法来捕获数据包。RIPv2协议能够通过更新消息所包含的口令来验证某个路由选择消息源的合法性,其方式有两种:简单认证、MD5密文认证方式。
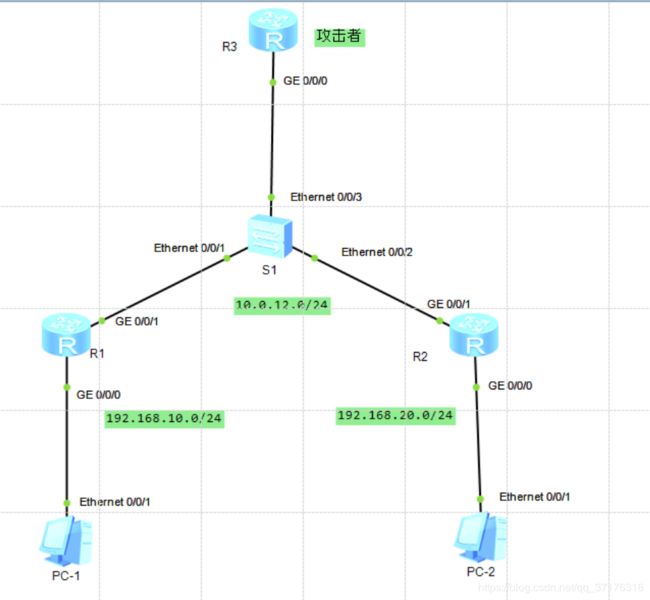
拓扑图:
步骤:
1.基本配置:
如拓扑图和图表所示,完成各个物理设备和接口的配置,并测试连通性:

2.搭建RIP网络:
[R1]rip
[R1-rip-1]version 2
[R1-rip-1]network 192.168.10.0
[R1-rip-1]network 10.0.0.0
[R2]rip
[R2-rip-1]version 2
[R2-rip-1]network 192.168.20.0
[R2-rip-1]network 10.0.0.0
检查R1和R2的路由表信息(仅以R1为例):
[R1]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 11 Routes : 11
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.12.0/24 Direct 0 0 D 10.0.12.1 GigabitEthernet
0/0/1
10.0.12.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
10.0.12.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.10.0/24 Direct 0 0 D 192.168.10.1 GigabitEthernet
0/0/0
192.168.10.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.10.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.20.0/24 RIP 100 1 D 10.0.12.2 GigabitEthernet
0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
3.模拟网络攻击:
配置路由器R3,并查看路由表信息:
[R3]rip
[R3-rip-1]version 2
[R3-rip-1]network 10.0.0.0
[R3]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 9 Routes : 9
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.12.0/24 Direct 0 0 D 10.0.12.3 GigabitEthernet
0/0/0
10.0.12.3/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
10.0.12.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.10.0/24 RIP 100 1 D 10.0.12.1 GigabitEthernet
0/0/0
192.168.20.0/24 RIP 100 1 D 10.0.12.2 GigabitEthernet
0/0/0
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
可以看到此时R3已经获取了R1和R2的路由信息,R3可以向它俩发布许多PING包,造成网络拥塞,形成攻击。
接下来,用R3模拟攻击实验:
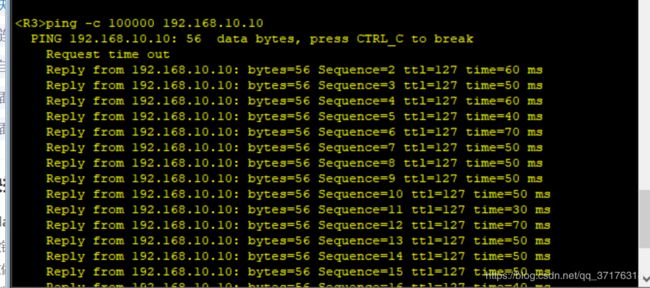
给R3配置两个用户欺骗的环回地址,地址和公司网络的用户地址相同:
[R3]interface LoopBack 0
[R3-LoopBack0]ip address 192.168.10.1 24
[R3]interface LoopBack 1
[R3-LoopBack1]ip address 192.168.20.1 24
[R3]rip
[R3-rip-1]version 2
[R3-rip-1]network 192.168.10.0
[R3-rip-1]network 192.168.20.0
查看R1路由表:
display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 11 Routes : 12
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.12.0/24 Direct 0 0 D 10.0.12.1 GigabitEthernet
0/0/1
10.0.12.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
10.0.12.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.10.0/24 Direct 0 0 D 192.168.10.1 GigabitEthernet
0/0/0
192.168.10.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.10.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.20.0/24 RIP 100 1 D 10.0.12.2 GigabitEthernet
0/0/1
RIP 100 1 D 10.0.12.3 GigabitEthernet
0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
可以看到,R1中到目的地为192.168.20.0/24的路径有两条,这样就会导致有部分信息进入到了欺骗路由R3中,R2同理;
4.配置RIPv2简单验证:
为了避免以上攻击,在R1和R2中配置简单验证,密码huawei:
[R1]interface g0/0/1
[R1-GigabitEthernet0/0/1]rip authentication-mode simple huawei
[R2]interface g0/0/1
[R2-GigabitEthernet0/0/1]rip authentication-mode simple huawei
配置完后等待一段时间,查看R1和R2的路由表:
[R1]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 11 Routes : 11
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.12.0/24 Direct 0 0 D 10.0.12.1 GigabitEthernet
0/0/1
10.0.12.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
10.0.12.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.10.0/24 Direct 0 0 D 192.168.10.1 GigabitEthernet
0/0/0
192.168.10.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.10.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.20.0/24 RIP 100 1 D 10.0.12.2 GigabitEthernet
0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
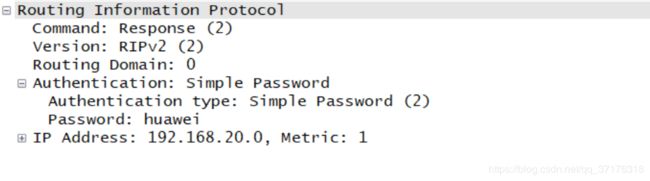
可以看到,欺骗路由消失,路由表恢复正常;
此时,在R1的G0/0/1上抓包,可以看到密码:
5.配置MD5密文验证:
[R1-GigabitEthernet0/0/1]undo rip authentication-mode
[R1-GigabitEthernet0/0/1]rip authentication-mode md5 usual huawei
[R2-GigabitEthernet0/0/1]undo rip authentication-mode
[R2-GigabitEthernet0/0/1]rip authentication-mode md5 usual huawei
查看R1的路由表:
[R1]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 11 Routes : 11
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.12.0/24 Direct 0 0 D 10.0.12.1 GigabitEthernet
0/0/1
10.0.12.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
10.0.12.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.10.0/24 Direct 0 0 D 192.168.10.1 GigabitEthernet
0/0/0
192.168.10.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.10.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.20.0/24 RIP 100 1 D 10.0.12.3 GigabitEthernet
0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
可以看到,欺骗路由也消失了,路由表是正常的;
继续抓包:

可以看到,此时密码没有显示。
至此,RIPv2认证实验就已经完成了!
思考题:
问题:在本实验中,R1和R2上配置了认证,R3没有配置认证,根据分析,R1和R2不会再接收R3发送的不包含认证信息的RIP更新,那R3是否会接收R1和R2发送过来的带有认证信息的RIP更新呢?为什么?
解答:也不会收,因为数据包里认证字段跟自己不匹配,所以路由器不收。单向的路由通常都是没有实际意义的而且(绝大多数应用都需要双向通信)。