OpenLDAP 加密传输
一、自建证书颁发机构
关于证书发布机构的大家,请查看我的博文《CentOS 6使用openssl搭建根CA》。
我下面所操作的是根据前面几篇博文配置好的LDAP,在那上面来进行改动。服务端的IP是192.168.2.10,客户端的IP是192.168.2.11。
二、OpenLDAP 服务端设置
假设我们的CA自建证书和服务器证书都创建好了,CA的公钥是cacert.pem,服务端的证书名称是ldap.crt,私钥文件是ldap.key,所有的文件放到/etc/openldap/certs。
注意,除了Common Name和Email其他的必须一致,而且服务端的Common Name最好使用IP,如果使用域名,服务器的名称必须和配置的一致。
1、×××权限
chown -R ldap.ldap /etc/openldap/certs/* chmod -R 0400 /etc/openldap/certs/*
2、修改slapd.conf
找到有关TLS的设置,修改成如下。
TLSCACertificatePath /etc/openldap/certs TLSCertificateFile /etc/openldap/certs/ldap.crt TLSCertificateKeyFile /etc/openldap/certs/ldap.key
3、开启OpenLDAP SSL功能
打开/etc/sysconfig/ldap,把LDAPS改为yes,如下。
# At least one of SLAPD_LDAP, SLAPD_LDAPI and SLAPD_LDAPS must be set to 'yes'! # # Run slapd with -h "... ldap:/// ..." # yes/no, default: yes SLAPD_LDAP=yes # Run slapd with -h "... ldapi:/// ..." # yes/no, default: yes SLAPD_LDAPI=yes # Run slapd with -h "... ldaps:/// ..." # yes/no, default: no SLAPD_LDAPS=yes
4、加载slapd数据库文件
rm -rf /etc/openldap/slapd.d/* slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/ chown -R ldap.ldap /etc/openldap/ service slapd restart
5、通过CA公钥证书验证OpenLDAP服务端证书的合法性
[root@mldap ~]# openssl verify -CAfile /etc/openldap/certs/cacert.pem /etc/openldap/certs/ldap.crt /etc/openldap/certs/ldap.crt: OK
6、确认当前套接字是否能通过CA的验证
[root@mldap ~]# openssl s_client -connect 192.168.2.10:636 -showcerts -state -CAfile /etc/openldap/certs/cacert.pem CONNECTED(00000003) SSL_connect:before/connect initialization SSL_connect:SSLv2/v3 write client hello A SSL_connect:SSLv3 read server hello A depth=1 C = CN, ST = Shanghai, L = Shanghai, O = wzlinux, OU = ldap, CN = ldap.wzlinux.com verify return:1 depth=0 C = CN, ST = Shanghai, O = wzlinux, OU = ldap, CN = 192.168.2.10 verify return:1 SSL_connect:SSLv3 read server certificate A SSL_connect:SSLv3 read server done A SSL_connect:SSLv3 write client key exchange A SSL_connect:SSLv3 write change cipher spec A SSL_connect:SSLv3 write finished A SSL_connect:SSLv3 flush data SSL_connect:SSLv3 read finished A --- Certificate chain 0 s:/C=CN/ST=Shanghai/O=wzlinux/OU=ldap/CN=192.168.2.10 i:/C=CN/ST=Shanghai/L=Shanghai/O=wzlinux/OU=ldap/CN=ldap.wzlinux.com -----BEGIN CERTIFICATE----- MIIDOTCCAiGgAwIBAgIBAzANBgkqhkiG9w0BAQUFADBvMQswCQYDVQQGEwJDTjER MA8GA1UECAwIU2hhbmdoYWkxETAPBgNVBAcMCFNoYW5naGFpMRAwDgYDVQQKDAd3 emxpbnV4MQ0wCwYDVQQLDARsZGFwMRkwFwYDVQQDDBBsZGFwLnd6bGludXguY29t MB4XDTE2MDgyOTEwMzEyOVoXDTE3MDgyOTEwMzEyOVowWDELMAkGA1UEBhMCQ04x ETAPBgNVBAgMCFNoYW5naGFpMRAwDgYDVQQKDAd3emxpbnV4MQ0wCwYDVQQLDARs ZGFwMRUwEwYDVQQDDAwxOTIuMTY4LjIuMTAwgZ8wDQYJKoZIhvcNAQEBBQADgY0A MIGJAoGBAO7larMYUDs5L95bwqSBWumfADZHyd18H4uDTq00Gh1+cyoDLabCKrjD 1k0novbb5+HLGs9Xu/OcvDfXF3McbbPB02fR6WdNEEqKixpiZ5d0MuVyydENHNE/ dM9BBka8mhZbEQD59fzZrBS7c3LEh3tV51FDNjnFr8Pbu2pKZFq9AgMBAAGjezB5 MAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENl cnRpZmljYXRlMB0GA1UdDgQWBBTYWRvrVAoWO7tSO8rxB9OVWZ1erzAfBgNVHSME GDAWgBTCyje4J9eUwtegjNLxaRu3Ff2OzjANBgkqhkiG9w0BAQUFAAOCAQEAP7rK ejInZsnTNfFpn7ok/DkoLHBngHfUIgLT8da4xwT7v1lyYsIr8rRTyly5q6yc+dlm 3yCXBBRJBRvFGkCZ4cws5JL7jnd3tdkCQ4xrcux8mLAY7+F1sH4jLdPgMirif9nb PAhmMCN0WuAw8bMCh1VbbKsYofQOdzKZiBz+qGVngxLPQ++5nsfi28a2uuKA4BAi fYdyhmMdouoIdA4gHUjjkksPsy2NwIZuG5T01QjraVFqP5Di87qMKchKyewJL9M9 j1yHUoNhhUbA6r3N3ZUGZ2lJijBMBSBuG9KUWvaDuL9W/rUYEF4RluMCWBKpt/Kr kHYQ6NrYE2mVTxaZFg== -----END CERTIFICATE----- --- Server certificate subject=/C=CN/ST=Shanghai/O=wzlinux/OU=ldap/CN=192.168.2.10 issuer=/C=CN/ST=Shanghai/L=Shanghai/O=wzlinux/OU=ldap/CN=ldap.wzlinux.com --- No client certificate CA names sent --- SSL handshake has read 1004 bytes and written 463 bytes --- New, TLSv1/SSLv3, Cipher is AES256-SHA Server public key is 1024 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE SSL-Session: Protocol : TLSv1.2 Cipher : AES256-SHA Session-ID: 2F3DC17790E8889F9E4DD8D372F9D0155EF03C448922C8CAAA14B530253D8B1E Session-ID-ctx: Master-Key: 8F01D070B54D4A0A6333D6A08B2E58EA8A0E3DBAF02D9F989F4A05B59B3C342C55DDB75ED6CD6E0176A87305EC9811E4 Key-Arg : None Krb5 Principal: None PSK identity: None PSK identity hint: None Start Time: 1472466741 Timeout : 300 (sec) Verify return code: 0 (ok) ---
三、OpenLDAP 客户端设置
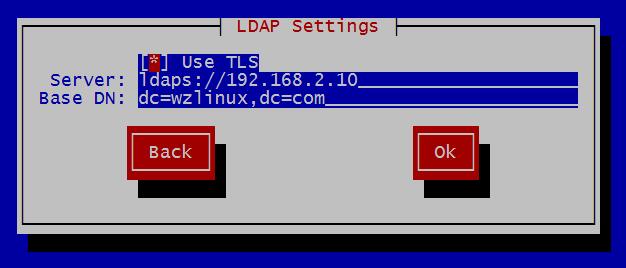
1、使用setup进行配置
备注:如果使用authconfig配置,使用下面代码,根据自己实际情况进行修改:
authconfig --enablemkhomedir \ --enableforcelegacy \ --enablelocauthorize \ --enableldaptls \ --enablemd5 \ --enableldap \ --enableldapauth \ --ldapserver=ldaps://192.168.2.10 \ --ldapbasedn="dc=wzlinux,dc=com" \ --enableshadow \ --update
2、复制CA公钥证书到客户端
把CA的公钥cacert.pem放到/etc/openldap/cacerts/目录下面。
3、编辑/etc/pam_ldap.conf和/etc/nslcd.conf
把 ssl start_tls 改成 ssl on。
4、重新启动nslcd
service nslcd restart
5、通过客户端匿名测试SSL连接是否正常
[root@test01 cacerts]# ldapwhoami -v -x -Z ldap_initialize() ldap_start_tls: Operations error (1) additional info: TLS already started anonymous Result: Success (0)
6、LDAP用户验证密码
[root@test01 ~]# ldapwhoami -D "cn=test3,ou=people,dc=wzlinux,dc=com" -W -H ldaps://192.168.2.10 -v ldap_initialize( ldaps://192.168.2.10:636/??base ) Enter LDAP Password: dn:cn=test3,ou=people,dc=wzlinux,dc=com Result: Success (0)
7、通过LDAP看看是否可以认证账号
[root@test01 ~]# id test3 uid=1001(test3) gid=501(app) groups=501(app) [root@test01 ~]# getent passwd test3 test3:*:1001:501: test3:/home/test3:/bin/bash