实验四十二、×××(IKE)的配置
一、 实验目的
1. 掌握××× (IKE)的配置
2. 理解IKE 在隧道建立过程中的作用
二、 应用环境
IKE (Internet 密钥交换)技术提供额外的特性,使配置IPSec 时更加灵活和容易
三、 实验设备
1. DCR-1751 两台
2. PC 机 两台
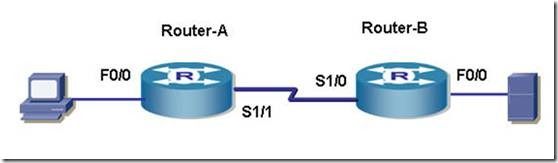
四、 实验拓扑
五、 实验要求
配置表
Router-A Router-B
F0/0 192.168.0.1/24 F0/0 192.168.2.1/24
S1/1 (DCE) 192.168.1.1/24 S1/0 192.168.1.2/24
PC SERVER
IP 192.168.0.10/24 192.168.2.2/24
网关 192.168.0.1 192.168.2.1
结果:
在路由器A 与B 之间建立×××,保护从PC 到SERVER 的数据六、 实验步骤
第一步:路由器A 的配置
Router-A#conf
Router-A_config#ip access-list extended 101 !确定要经过××× 保护的数据流
Router-A_config_ext_nacl#permi ip 192.168.0.0 255.255.255.0 192.168.2.0 255.255.255.0
Router-A_config_ext_nacl#exit
Router-A_config#ip route 0.0.0.0 0.0.0.0 192.168.1.2 !配置静态路由
Router-A_config#crypt isakmp policy 10 !配置IKE 策略
Router-A_config_isakmp#authentication pre-share !设置认证方式
Router-A_config_isakmp#encryption des !设置加密方式
Router-A_config_isakmp#hash md5 !设置数字签名算法
Router-A_config_isakmp#group 1 !设置DH 方式
Router-A_config_isakmp#lifetime 86400 !设置生存期
Router-A_config_isakmp#exit
Router-A_config#crypto isakmp key digital 192.168.1.2 !设置共用密钥
Router-A_config#crypto ipsec transform-set one !设置变换集
Router-A_config_crypto_trans#transform-type esp-des esp-md5-hmac !ESP 加密和验证
Router-A_config_crypto_trans#mode tunnel !设置为隧道模式
Router-A_config_crypto_trans#exit
Router-A_config#crypto map my 10 ipsec-isakmp !配置IPSec 加密映射
Router-A_config_crypto_map#set transform-set one !关联变换集
Router-A_config_crypto_map#set peer 192.168.1.2 !设置对等体地址
Router-A_config_crypto_map#match address 101 !关联需要加密的数据流
Router-A_config_crypto_map#exit
Router-A_config#int s1/1 !进入××× 的接口
Router-A_config_s1/1#crypto map my !绑定IPSec 加密映射
Router-A_config_s1/1#^Z
第二步:查看配置
Router-A#sh crypto isakmp policy !查看IKE 策略
Protection suite of priority 10
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds
Router-A#sh crypto isakmp sa !查看IKE 安全关联(没有建立,为空)
Router-A#sh crypto map !查看IPSec 映射
Crypto Map my 10 ipsec-isakmp
Extended IP access list 101
permit ip 192.168.0.0 255.255.255.0 192.168.2.0 255.255.255.0
peer = 192.168.1.2
PFS (Y/N): N
Security association lifetime: 4608000 kilobytes/3600 seconds
Transform sets={ one,}
Router-A#sh crypto ipsec sa !查看IPSse 关联
Interface: Serial1/1
Crypto map name:my , local addr. 192.168.1.1
local ident (addr/mask/prot/port): (192.168.0.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
local crypto endpt.: 192.168.1.1, remote crypto endpt.: 192.168.1.2
Router-A#sh crypto ipsec transform-set !查看变换集
Transform set one: { esp-des esp-md5-hmac }
will negotiate ={ Tunnel }
第三步:路由器B 的配置
Router-B>ena
Router-B#conf
Router-B_config#ip access-list extended 101
Router-B_config_ext_nacl#permit ip 192.168.2.0 255.255.255.0 192.168.0.0 255.255.255.0
Router-B_config_ext_nacl#exit
Router-B_config#ip route 192.168.0.0 255.255.255.0 192.168.1.1
Router-B_config#crypto isakmp policy 10 !注意与A 要一致
Router-B_config_isakmp#authentication pre-share
Router-B_config_isakmp#hash md5
Router-B_config_isakmp#encryption des
Router-B_config_isakmp#group 1
Router-B_config_isakmp#lifetime 86400
Router-B_config_isakmp#exit
Router-B_config#crypto isakmp key digital 192.168.1.1 !注意与A 要一致
Router-B_config#crypto ipsec transform-set one
Router-B_config_crypto_trans#transform-type esp-des esp-md5-hmac !注意与A 要一致
Router-B_config_crypto_trans#mode tunnel
Router-B_config_crypto_trans#exit
Router-B_config#crypto map my 10 ipsec-isakmp !注意与A 要一致
Router-B_config_crypto_map#set transform-set one
Router-B_config_crypto_map#set peer 192.168.1.1
Router-B_config_crypto_map#match address 101
Router-B_config_crypto_map#exit
Router-B_config#int s1/0
Router-B_config_s1/0#crypto map my
Router-B_config_s1/0#^Z
第四步:查看配置
Router-B#sh crypto isakmp policy
Protection suite of priority 10
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds
Router-B#sh crypto isakmp sa
Router-B#sh crypto ipsec sa
Interface: Serial1/0
Crypto map name:my , local addr. 192.168.1.2
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.0.0/255.255.255.0/0/0)
local crypto endpt.: 192.168.1.2, remote crypto endpt.: 192.168.1.1
Router-B#sh crypto ipsec transform-set
Transform set one: { esp-des esp-md5-hmac }
will negotiate ={ Tunnel }
Router-B#sh crypto map
Crypto Map my 10 ipsec-isakmp
Extended IP access list 101
permit ip 192.168.2.0 255.255.255.0 192.168.0.0 255.255.255.0
peer = 192.168.1.1
PFS (Y/N): N
Security association lifetime: 4608000 kilobytes/3600 seconds
Transform sets={ one,}
第五步:测试
再次查看安全关联:
Router-B#sh crypto isakmp sa
dst src state state-id conn
192.168.1.1 192.168.1.2
192.168.1.1 192.168.1.2
Router-B#sh crypto ipsec sa
Interface: Serial1/0
Crypto map name:my , local addr. 192.168.1.2
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.0.0/255.255.255.0/0/0)
local crypto endpt.: 192.168.1.2, remote crypto endpt.: 192.168.1.1
inbound esp sas:
spi:0x6a83b104(1787015428)
transform: esp-des esp-md5-hmac
in use settings ={ Tunnel }
sa timing: remaining key lifetime (k/sec): (4607996/3073)
outbound esp sas:
spi:0xfe0d0282(4262265474)
transform: esp-des esp-md5-hmac
in use settings ={ Tunnel }
sa timing: remaining key lifetime (k/sec): (4607998/3072)