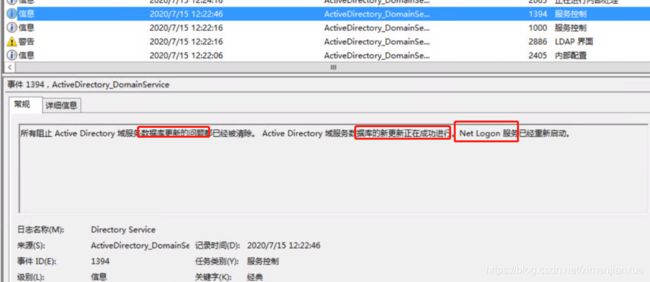
ntds(600)ntdsa:系统错误1453配额不足及恢复过程记录
问题描述
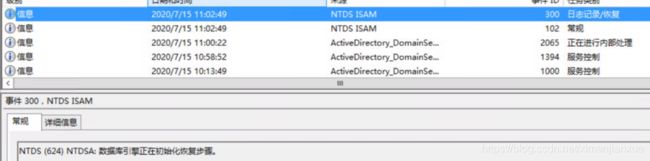
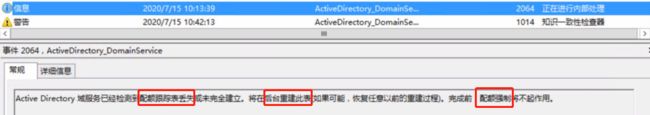
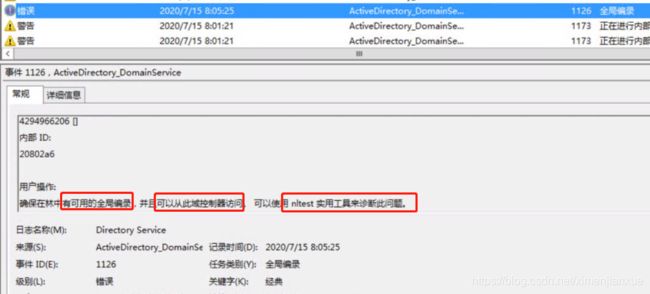
某桌面环境中,突然用户无法登录,经检查域环境中主AD故障,IP地址和主机信息,在VC界面均不现实,登录显示黑屏,重启后AD报:
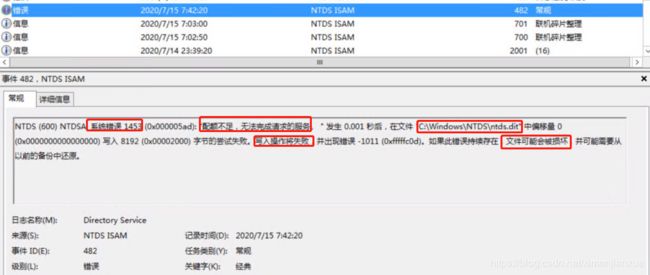
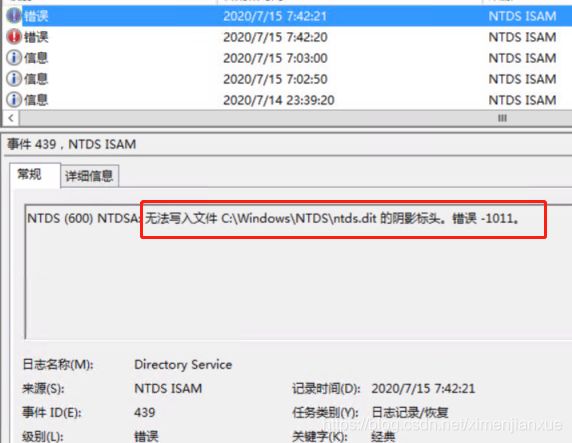
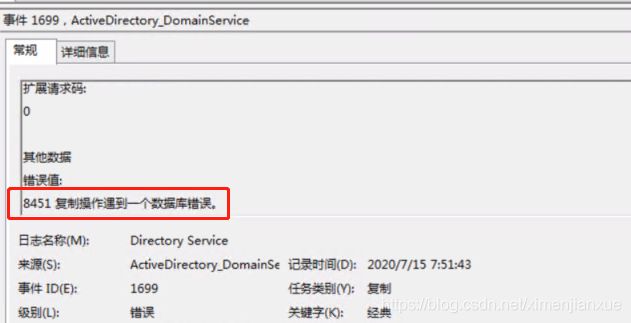
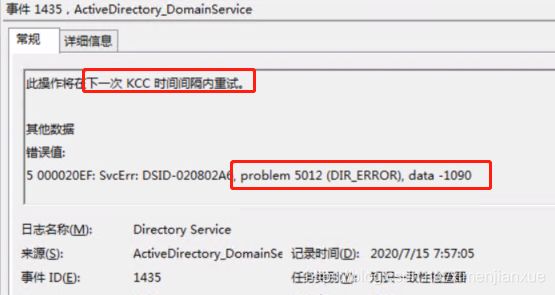
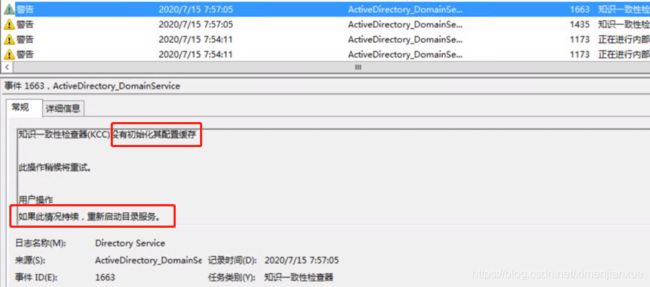
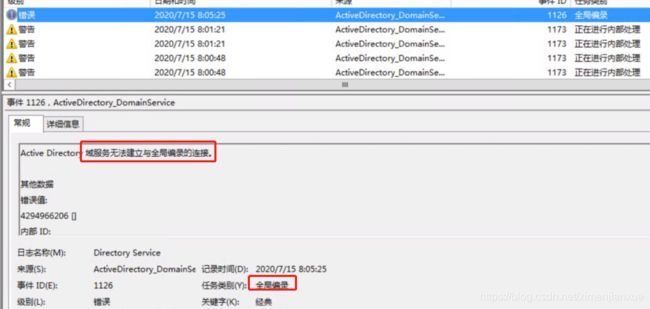
NTDS(600)NTDSA:无法写入文件的阴影标头。
![]()

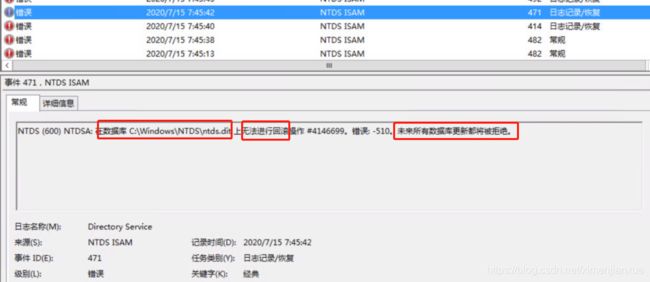
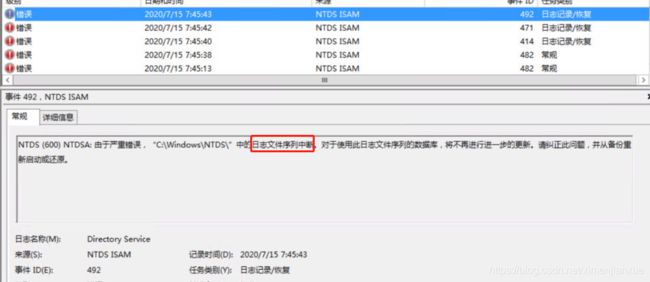

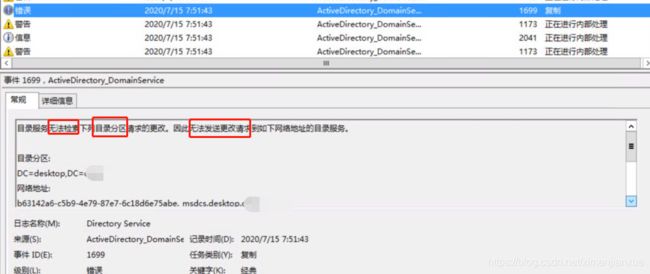




![]()
问题分析
1)首先NTDS是什么?
NTDS:注册表路径HKLM\SYSTEM\CurrentControlSet\Services
The NTDS subkey stores configuration data for Active Directory.
In particular, Active Directory stores domain controller information in this subkey that it uses to restart Active Directory independently and to configure the Active Directory database. Active Directory also saves log file locations in this subkey.
从上述描述可知NTDS是存储AD配置及日志的一个服务,可用于重启和配置AD域控的数据库;
2)使用Dsquery工具单独查看操作主机角色
Dsquery Server –Hasfsmo Schema //查看架构主机
Dsquery Server –Hasfsmo Name //查看域 主机
Dsquery Server –Hasfsmo PDC //查看PDC模拟器主机
Dsquery Server –Hasfsmo RID //查看RID主机
Dsquery Server –Hasfsmo Infr //查看基础结构主机
3)查看域控:
netdom query fsmo
4)域安全通道和信任关系维护工具-- Nltest.exe
1>重新修复建立域主域之间的信任关系
第一步获取当前凭证,然后输入域用户名和密码
Get-Credential
第二步检查本地计算机与其域之间的安全通道的信任关系的状态,来验证安全通道是否正常工作。如果连接失败,则使用 Repair 参数尝试恢复。如果返回flase,则多执行几次 直到返回true即可。如果多次执行仍然失败那只能退域重加了
Test-ComputerSecureChannel -Repair -Credential $cred
或:登录到域控服务器,输入命令:
netdom reset pcname /domain:mydomain
若成功,则会收到以下提示:
已重置从 pcname 到域 mydomain 的安全通道。与计算机 \pcname.mydomain 建立连接。
2>工作站和主域控制器之间的安全通道出现了问题所导致的,我们可以通过重置这连个安全通道来解决此问题,在DC上运行:netdomreset计算机名/domain:域名
作为域成员的每一台工作站或服务器,他们都与域控制器有一个离散的通信通道,该通道称之为安全通道
安全通道的密码和计算机的账户一起存储在所有的域控制器上,对于工作站,默认计算机账户密码的更换周期为30天,如果因某种原因导致计算机账户的密码和lsa机密不同步,netlogon服务就会记录下面一条或者两条错误信息:
从计算机domainmember设置的会话无法验证,安全数据库中引用的账户名称是domainmember$
netlogon事件ID3210
用法:
C:\NTRESKIT>nltest
Usage: nltest [/OPTIONS]
/SERVER: - Specify
/QUERY - Query netlogon service
/REPL - Force replication on BDC
/SYNC - Force SYNC on BDC
/PDC_REPL - Force UAS change message from PDC
/SC_QUERY: - Query secure channel for on
/SC_RESET: - Reset secure channel for on
/DCLIST: - Get list of DC’s for
/DCNAME: - Get the PDC name for
/DCTRUST: - Get name of DC is used for trust of
/WHOWILL:* [] - See if will log on
/FINDUSER: - See which trusted will log on
/TRANSPORT_NOTIFY - Notify of netlogon of new transport
/RID: - RID to encrypt Password with
/USER: - Query User info on
/TIME: - Convert NT GMT time to ASCII
/LOGON_QUERY - Query number of cumulative logon attempts
/TRUSTED_DOMAINS - Query names of domains trusted by workstation
/BDC_QUERY: - Query replication status of BDCs for
/SIM_SYNC: - Simulate full sync replication
/LIST_DELTAS: - display the content of given change log file
/LIST_REDO: - display the content of given redo log file
Additional Comments and Descriptions of the Nltest.exe Switches
/SERVER:: Remotes the Nltest.exe command to the specified server. If this switch is not specified, the command is run from the local computer.
/QUERY Queries the local or specified server for a healthy secure channel to a domain controller, and the status of Directory Services replication with the PDC. This is very helpful in determining the general status of the Netlogon service.
/REPL Force partial synchronization of the local or specified BDC.
/SYNC Forces a full, immediate synchronization of the local or specified BDC.
/PDC_REPL The specified PDC forces a change message to all BDCs.
/SC_QUERY: Verifies the secure channel in the specified domain for a local or remote workstation, server, or BDC. This can be run for a PDC if an explicit trust relationship exists between two domains and the trusted domain is specified.
/SC_RESET: Resets the secure channel between the local or remote workstation, server, or BDC. This can be run for a PDC if an explicit trust relationship exists between two domains and the trusted domain is specified.
/DCLIST: Lists all the domain controllers, PDC, and BDCs in a given domain.
/DCNAME: Lists the primary domain controller for a given domain.
/DCTRUST: Queries and tests the secure channel every time the command is executed. Specify the domain for the local or remote workstation, server, or BDC. This can be run for a PDC if an explicit trust relationship exists between two domains and the trusted domain is specified.
/WHOWILL: Queries the domain and indicates which Domain Controller has the account in their local user account database. This is very useful in determining if a given domain controller contains the user account. If the username specified is that of the currently logged on user, the user’s current password is NOT sent to the domain controller. This is helpful in determining if duplicate accounts exist across several domains.
/FINDUSER: Queries explicit trusted domains for the user specified. This is very useful when determining what trusted domain controller or what trusted domain out of several trusted domains will authenticate a user’s credentials when a Domain name is not specified in the Server Message Block (SMB) packet. Many down-level clients, such as Windows for Workgroups version 3.1 and the real-mode redirector in Windows 95, do not specify a domain name.
/USER: Displays many of the attributes for the specified user account that are maintained in the user account database.
/LOGON_QUERY Specifies the number of attempted logon queries at the console, or over the network.
/TRUSTED_DOMAINS Displays a list of explicit trusted domains.
/BDC_QUERY: List the backup domain controllers in the specified Domain and provides the state of their synchronization.
/LIST_DELTAS: List information from the Netlogon.chg file specifying changes to the user account database.
/LIST_REDO: List information from the Netlogon.chg file specifying changes to the user account database.
Example Output from Nltest.exe
As an example, suppose the TESTD domain trusts the ESS domain, and a computer running Windows NT Workstation called TEST3 is a member of the TESTD domain.
NLTEST can be used to show this trust relationship.
C:>nltest /trusted_domains
Trusted domain list:
ESS
The command completed successfully
To determine the domain controllers in the TESTD domain:
C:>nltest /dclist:testd
List of DCs in Domain testd
\TEST2 (PDC)
\TEST1
The command completed successfully
To determine the domain controllers in the ESS domain:
C:>nltest /dclist:ess
List of DCs in Domain ess
\NET1 (PDC)
The command completed successfully
Below are the secure channels between each domain controller in TESTD and a DC in the ESS domain.
C:>nltest /server:test1 /sc_query:ess
Flags: 0
Connection Status = 0 0x0 NERR_Success
Trusted DC Name \NET1
Trusted DC Connection Status Status = 0 0x0 NERR_Success
The command completed successfully
C:>nltest /server:test2 /sc_query:ess
Flags: 0
Connection Status = 0 0x0 NERR_Success
Trusted DC Name \NET1
Trusted DC Connection Status Status = 0 0x0 NERR_Success
The command completed successfully
The workstation that is a member of the TESTD domain has an implicit trust with a domain controller.
C:>nltest /server:test3 /sc_query:testd
Flags: 0
Connection Status = 0 0x0 NERR_Success
Trusted DC Name \TEST2
Trusted DC Connection Status Status = 0 0x0 NERR_Success
The command completed successfully
To determine if a domain controller can authenticate a user account:
C:>nltest /whowill:ESS bob
[20:58:55] Mail message 0 sent successfully
(\MAILSLOT\NET\GETDC939)
[20:58:55] Response 0: S:\NET1 D:ESS A:bob (Act found)
The command completed successfully
C:>nltest /whowill:testd test
[21:26:13] Response 0: S:\TEST2 D:TESTD A:test (Act found)
[21:26:15] Mail message 0 sent successfully
(\MAILSLOT\NET\GETDC295)
The command completed successfully
NLTEST can be used to find a trusted domain that has a given user account.
C:>nltest /finduser:sweppler
Domain Name: ESS
Trusted DC Name \NET1
The command completed successfully
To verify the status of BDC synchronization:
C:>nltest /bdc_query:testd
Server : \TEST1
SyncState : IN_SYNC
ConnectionState : Status = 0 0x0 NERR_Success
The command completed successfully
Nltest.exe can also be used to synchronize the accounts database from a command line or a batch job.
To run the utility to synchronize the domain from a PDC, type:
C:\ nltest /PDC_Repl
To run the utility from a member server, backup domain controller, or Windows NT workstation, type
C:\ nltest /Server: /PDC_Repl
where PDCName is the actual name of the PDC, not the name of the domain)
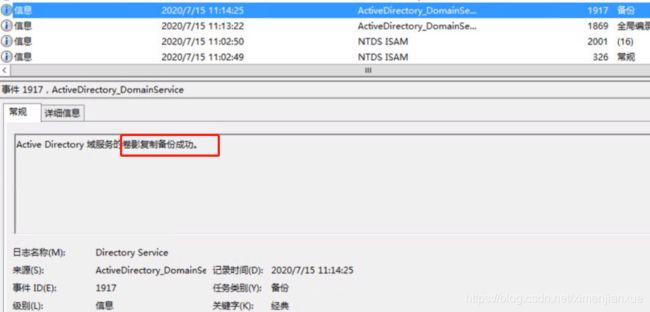
You will see the successful synchronization events in Event Viewer on the primary domain controller, as well as the backup domain controllers.
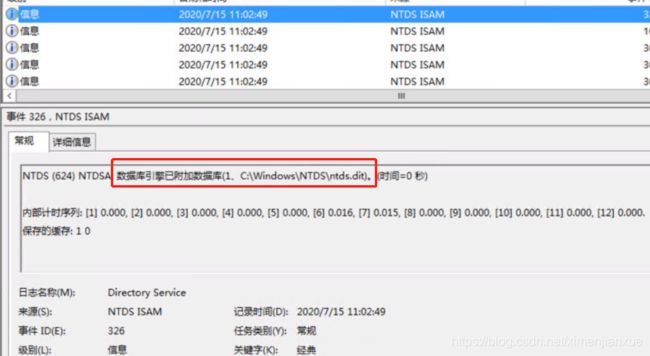
服务恢复后
域控主机角色建议
常见的操作主机角色放置建议如下:
架构主机: 拥有架构主机角色的DC不需要高性能,因为在实际环境中不会经常对Schema进行操作的,除非是经常会对Schema进行扩展,不过这种情况非常的少。但要 保证可用性 ,否则在安装Exchange等会扩展AD架构的软件时会出错。
域命名主机:对占有域命名主机的DC也不需要高性能,在实际环境中也不会经常在森林里添加或者删除域的。但要保证高可用性是有必要的,以保证在添加删除当前林中域时可以使用。 一般建议由同一台DC承担架构主机与域域命名主机角色,并由GC放置在同一台DC中。
PDC模拟器:从上述PDC功能中可以看出,PDC模拟器是FSMO五种角色里任务最重的,必须保持拥有PDC的DC有高性能和高可用性。
RID主机:对于占有RID Master的域控制器,没有必要一定要求高性能,因为给其它DC分配RID池的操作不是经常性发生,但要求高可用性,否则在添加用户时出错。
基础架构主机:对于单域环境,基础架构主机实际上不起作用,因为基础架构主机主要作用是对跨域对象引用进行更新,对于单域,不存在跨域对象的更新。基础架构主机对性能和可用性方面的要求较低。基础架构主机的数据主要来自全局编录服务器(GC),全局编录服务器存储其他域的数据。由于基础架构主机和全局编录服务器不兼容,不要将这2个角色放同一台域控制器中。除非:域中只有一个域控制器,否则不应该将基础架构主机角色指派给全局编录服务器。 又或者域中所有的域控制器都存在全局编录,则无论哪个域控制器均可承担基础结构主机角色。
建议将PDC模拟器,RID主机以及基础结构主机放置在一台性能较好的DC中,且尽量不要配置成GC。
对以上FSMO规划总结如下:
1、占有Domain Naming Master角色的域控制器必须同时也是GC;
2、不能把Infrastructure Master和GC放在同一台DC上;
3、建议将Schema Master和Domain Naming Master放在森林根域的GC服务器上;
4、建议将Schema Master和Domain Naming Master放在同一台域控制器上;
5、建议将PDC Emulator、RID Master及Infrastructure Master放在同一台性能较好的域控制器上;
6、尽量不要把PDC Emulator、RID Master及Infrastructure Master放置在GC服务器上;