云原生Tekton之触发器Trigger
背景
前面的文章讲了tekton中pipeline的教程和使用案例,大家有没有想过,每次都要运行taskrun或者pipelineRun才能真正运行流水线。那怎么做到自动化执行taskrun和pipelineRun呢?我想了下有两种方式:
- 使用client-go去创建taskRun和pipelineRun
- 使用tekton的另一个组件trigger触发器。
单纯运行taskrun和pipelineRun,或者实例化以下task和pipeline,那么选用trigger会比较好,因为不需要额外开发,只需要将每次需要传给task的参数发送给trigger中的eventlistener即可。要是用clien-go的话还要写代码,比较麻烦。下面我就介绍下安装Trigger和运行一个简单的示例。
安装Trigger
安装环境
- 一个版本在1.15以上的k8s集群
- 集群中安装了Tekton的Pipelines组件(可参照我之前的文章)
开始安装
官方安装,运行以下命令:
kubectl apply --filename https://storage.googleapis.com/tekton-releases/triggers/latest/release.yaml
由于里面有些镜像是谷歌镜像,所以我帮大家把镜像拉取下来了,并推送到了dockerhub上,所以大家可以运行以下命令来代替上面的官方命令:
Kubectl apply -f https://github.com/fishingfly/tekton-deploy/blob/master/tekton-trigger-release.yaml
尽量在你的机器上配置阿里云的镜像加速器,那拉取dokcerhub镜像会快点。
查看是否安装成功:
kubectl get pods --namespace tekton-pipelines
看到pod都是running的状态,就是安装成功了。
运行实例
运行以下yaml:
apiVersion: triggers.tekton.dev/v1alpha1
kind: TriggerTemplate
metadata:
name: v1alpha1-task-template
spec:
resourcetemplates:
- apiVersion: tekton.dev/v1alpha1
kind: TaskRun
metadata:
generateName: v1alpha1-task-run-
spec:
taskSpec:
steps:
- name: "hellothere"
image: ubuntu
script: echo "hello there"
---
apiVersion: triggers.tekton.dev/v1alpha1
kind: EventListener
metadata:
name: v1alpha1-task-listener
spec:
# from examples/role-resources/servicaccount.yaml
serviceAccountName: tekton-triggers-example-sa
triggers:
- name: v1alpha1-task-trigger
template:
name: v1alpha1-task-template
---
apiVersion: v1
kind: Secret
metadata:
name: tekton-triggers-example-secret
type: Opaque
stringData:
secretToken: "1234567"
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: tekton-triggers-example-sa
secrets:
- name: tekton-triggers-example-secret
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: tekton-triggers-example-binding
subjects:
- kind: ServiceAccount
name: tekton-triggers-example-sa
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: tekton-triggers-example-minimal
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: tekton-triggers-example-minimal
rules:
# Permissions for every EventListener deployment to function
- apiGroups: ["triggers.tekton.dev"]
resources: ["eventlisteners", "triggerbindings", "triggertemplates"]
verbs: ["get"]
- apiGroups: [""]
# secrets are only needed for Github/Gitlab interceptors, serviceaccounts only for per trigger authorization
resources: ["configmaps", "secrets", "serviceaccounts"]
verbs: ["get", "list", "watch"]
# Permissions to create resources in associated TriggerTemplates
- apiGroups: ["tekton.dev"]
resources: ["pipelineruns", "pipelineresources", "taskruns"]
verbs: ["create"]
运行:
kubectl apply -f examples/v1alpha1-task/v1alpha1-task-listener.yaml
此时看下default命名空间下,看到这样一个pod:el-v1alpha1-task-listener-5967dc5fd-4xmnx 在运行,此时运行以下命令:
kubectl port-forward \
"$(kubectl get pod --selector=eventlistener=v1alpha1-task-listener -oname)" \
8080
然后再起个终端去访问本地的8080端口:
curl -v \
-H 'Content-Type: application/json' \
--data "{}" \
http://localhost:8080
看下deault命名空间下是部署多了一个pod在运行:
kubectl get taskruns | grep v1alpha1-task-run-
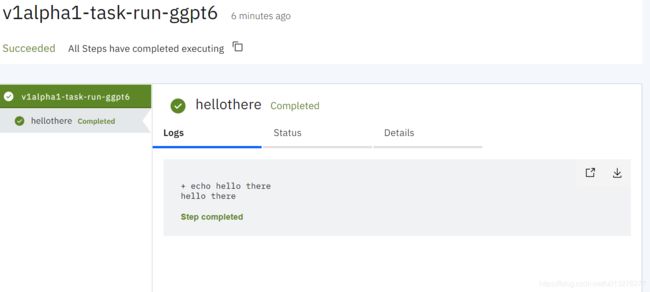
这就完成通过发送Http请求到eventlistner服务然后触发taskrun的实例化的过程。
总结
使用trigger将大大简化我们实例化tekton中资源的过程,trigger不仅可以实例化taskrun、pipelineRun,还能实例化tekton中的其他资源。目前来讲trigger唯一的不足是不能通过trigger来动态删除tekton的资源,相信以后会有改进。
