Kali Linux 渗透测试之主动信息收集(三)——四层之主机发现(TCP、UDP、scapy、Nmap、Hping3)
发现——四层发现
四层发现简介:
-
四层发现虽然使用了端口的探测,但是并不对端口进行解析,只是利用了四层的通讯,通过端口识别目标主机是否存活;
-
最终目的是判断目标IP是否存活;
优点:
- 可路由且结果可靠(根据TCP/UDP探测端口,根据端口返回的结果,探测目标IP是否存活);
- 不太可能被防火墙过滤;
- 甚至可以发现所有端口都被过滤的主机;
缺点:
- 基于状态过滤的防火墙可能过滤扫描;
- 全端口扫描速度慢;
TCP发现:
TCP发现是直接发送ACK数据包,一般来说目标主机存活会返回一个RST数据包以终止这个不正常的TCP连接。也可以发送正常的SYN数据包,如果目标主机返回SYN/ACK或者RST数据包,都可以证明目标主机存活。
UDP发现:
-
如果目标主机是存活的,且UDP目标端口为关闭,目标主机就会返回一个目标端口不可达的数据包,这就可以证明目标主机是存活的;
-
如果目标主机是关闭的,或者目标主机存活且目标端口为开放的状态,都不会有任何数据包返回,不能证明目标主机存活,这也就是UDP发现是选择一个最不常用的端口的原因;
1、scapy
1.1> ACK——TCP Port——RST(发现单个主机)
TCP发现是直接发送ACK数据包,一般来说目标主机存活会返回一个RST数据包以终止这个不正常的TCP连接。也可以发送正常的SYN数据包,如果目标主机返回SYN/ACK或者RST数据包,都可以证明目标主机存活。
root@kali:~# scapy
INFO: Can't import matplotlib. Won't be able to plot.
WARNING: No route found for IPv6 destination :: (no default route?)
WARNING: IPython not available. Using standard Python shell instead.
... ...
>>> i=IP()
>>> t=TCP()
>>> r=(i/t)
>>> r.display()
###[ IP ]###
version= 4
ihl= None
tos= 0x0
len= None
id= 1
flags=
frag= 0
ttl= 64
proto= tcp
chksum= None
src= 127.0.0.1
dst= 127.0.0.1
\options\
###[ TCP ]###
sport= ftp_data
dport= http
seq= 0
ack= 0
dataofs= None
reserved= 0
flags= S
window= 8192
chksum= None
urgptr= 0
options= []
>>> r[IP].dst="192.168.85.150"
>>> r[TCP].flags="A"
>>> r.display()
###[ IP ]###
version= 4
ihl= None
tos= 0x0
len= None
id= 1
flags=
frag= 0
ttl= 64
proto= tcp
chksum= None
src= 192.168.85.149
dst= 192.168.85.150
\options\
###[ TCP ]###
sport= ftp_data
dport= http
seq= 0
ack= 0
dataofs= None
reserved= 0
flags= A
window= 8192
chksum= None
urgptr= 0
options= []
>>> a=sr1(r)
Begin emission:
.Finished sending 1 packets.
*
Received 2 packets, got 1 answers, remaining 0 packets
>>> a.display()
###[ IP ]###
version= 4
ihl= 5
tos= 0x0
len= 40
id= 0
flags= DF
frag= 0
ttl= 64
proto= tcp
chksum= 0xe54
src= 192.168.85.150
dst= 192.168.85.149
\options\
###[ TCP ]###
sport= http
dport= ftp_data
seq= 0
ack= 0
dataofs= 5
reserved= 0
flags= R #返回RST包
window= 0
chksum= 0x8300
urgptr= 0
options= []
###[ Padding ]###
load= '\x00\x00\x00\x00\x00\x00'
>>> r[TCP].dport=8888 #将TCP数据包的目的端口设置为:8888
>>> r.display()
###[ IP ]###
version= 4
ihl= None
tos= 0x0
len= None
id= 1
flags=
frag= 0
ttl= 64
proto= tcp
chksum= None
src= 192.168.85.149
dst= 192.168.85.150
\options\
###[ TCP ]###
sport= ftp_data
dport= 8888 #设置成功,只是设置了一个端口而已,需要从这个端口进入
seq= 0
ack= 0
dataofs= None
reserved= 0
flags= A
window= 8192
chksum= None
urgptr= 0
options= []
>>> a1=sr1(r)
Begin emission:
.Finished sending 1 packets.
*
Received 2 packets, got 1 answers, remaining 0 packets
>>> a1.display()
###[ IP ]###
version= 4
ihl= 5
tos= 0x0
len= 40
id= 0
flags= DF
frag= 0
ttl= 64
proto= tcp
chksum= 0xe54
src= 192.168.85.150
dst= 192.168.85.149
\options\
###[ TCP ]###
sport= 8888
dport= ftp_data
seq= 0
ack= 0
dataofs= 5
reserved= 0
flags= R #返回RST包
window= 0
chksum= 0x6098
urgptr= 0
options= []
###[ Padding ]###
load= '\x00\x00\x00\x00\x00\x00'
>>> a=sr1(IP(dst='192.168.85.150')/TCP(dport=80,flags='A'),timeout=1)
Begin emission:
.Finished sending 1 packets.
*
Received 2 packets, got 1 answers, remaining 0 packets
>>> a.display()
###[ IP ]###
version= 4
ihl= 5
tos= 0x0
len= 40
id= 0
flags= DF
frag= 0
ttl= 64
proto= tcp
chksum= 0xe54
src= 192.168.85.150
dst= 192.168.85.149
\options\
###[ TCP ]###
sport= http
dport= ftp_data
seq= 0
ack= 0
dataofs= 5
reserved= 0
flags= R
window= 0
chksum= 0x8300
urgptr= 0
options= []
###[ Padding ]###
load= '\x00\x00\x00\x00\x00\x00'
1.2>使用python脚本实现多个主机的ACK扫描(即,多主机的发现);
脚本:ACK_ping.py
#!/usr/bin/python
# 该脚本用于实现对整个网段的扫描
from scapy.all import *
prefix="192.168.85."
for addr in range(1,255):
response=sr1(IP(dst=prefix+str(addr))/TCP(dport=80,flags='A'),timeout=0.1,verbose=0)
try:
if int(response[TCP].flags)==4: #标志为:4
print(prefix+str(addr))
except:
pass
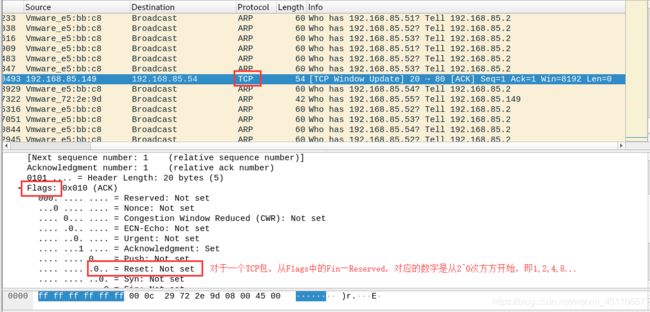
结果如下:并使用Wireshark抓包查看;
root@root:~# python ACK_ping.py
192.168.85.2
192.168.85.152
对于为什么脚本中写的int(response[TCP].flags)==4,是因为当回包是RTS包时,它的值为4时,说明目标主机存活;
Flags: 0x010 (ACK)
000. .... .... = Reserved: Not set
...0 .... .... = Nonce: Not set
.... 0... .... = Congestion Window Reduced (CWR): Not set
.... .0.. .... = ECN-Echo: Not set
.... ..0. .... = Urgent: Not set #...
.... ...1 .... = Acknowledgment: Set #16
.... .... 0... = Push: Not set #8
.... .... .0.. = Reset: Not set #4
.... .... ..0. = Syn: Not set #2
.... .... ...0 = Fin: Not set #1
[TCP Flags: ·······A····]
1.3> UDP发现(扫描单个主机)
- 如果目标主机是存活的且UDP目标端口为关闭状态,目标主机就会返回一个目标不可达的数据包,这就可以证明目标主机存活的;
- 如果目标主机是关闭的,或者目标主机存活且目标端口为开放状态,都不活有任何数据包返回,不能证明目标主机存活,这也就是UDP发现时选择一个最不常用端口的原因;
root@kali:~# scapy
INFO: Can't import matplotlib. Won't be able to plot.
WARNING: No route found for IPv6 destination :: (no default route?)
WARNING: IPython not available. Using standard Python shell instead.
... ...
>>> i=IP()
>>> u=UDP()
>>> r=(i/u)
>>> r.display()
###[ IP ]###
version= 4
ihl= None
tos= 0x0
len= None
id= 1
flags=
frag= 0
ttl= 64
proto= udp
chksum= None
src= 127.0.0.1
dst= 127.0.0.1
\options\
###[ UDP ]###
sport= domain
dport= domain
len= None
chksum= None
>>> r[IP].dst="192.168.85.150"
>>> r[UDP].dport=7345
>>> r.display()
###[ IP ]###
version= 4
ihl= None
tos= 0x0
len= None
id= 1
flags=
frag= 0
ttl= 64
proto= udp
chksum= None
src= 192.168.85.149
dst= 192.168.85.150
\options\
###[ UDP ]###
sport= domain
dport= 7345
len= None
chksum= None
>>> a=sr1(r)
Begin emission:
.Finished sending 1 packets.
*
Received 2 packets, got 1 answers, remaining 0 packets
>>> a.display()
###[ IP ]###
version= 4
ihl= 5
tos= 0xc0
len= 56
id= 45848
flags=
frag= 0
ttl= 64
proto= icmp
chksum= 0x9a70
src= 192.168.85.150
dst= 192.168.85.149
\options\
###[ ICMP ]###
type= dest-unreach
code= port-unreachable
chksum= 0x2993
reserved= 0
length= 0
nexthopmtu= 0
###[ IP in ICMP ]###
version= 4
ihl= 5
tos= 0x0
len= 28
id= 1
flags=
frag= 0
ttl= 64
proto= udp
chksum= 0x4e54
src= 192.168.85.149
dst= 192.168.85.150
\options\
###[ UDP in ICMP ]###
sport= domain
dport= 7345
len= 8
chksum= 0xb67b
>>> r[IP].dst="192.168.85.100"
>>> a=sr1(r,timeout=1)
Begin emission:
.WARNING: Mac address to reach destination not found. Using broadcast.
.Finished sending 1 packets.
.
Received 3 packets, got 0 answers, remaining 1 packets
>>> a=sr1(IP(dst="192.168.85.150")/UDP(dport=7888),timeout=1)
Begin emission:
WARNING: Mac address to reach destination not found. Using broadcast.
.Finished sending 1 packets.
Received 1 packets, got 0 answers, remaining 1 packets
>>> a=sr1(IP(dst="192.168.85.100")/UDP(dport=7888),timeout=1)
Begin emission:
WARNING: Mac address to reach destination not found. Using broadcast.
.Finished sending 1 packets.
Received 1 packets, got 0 answers, remaining 1 packets
>>>
1.4> 使用python脚本实现多个主机的UDP扫描(多个主机发现)
脚本:UDP_ping.py
#/usr/bin/python
# 该脚本用于实现对整个网段的扫描
from scapy.all import *
prefix="192.168.85."
for addr in range(1,255):
response=sr1(IP(dst=prefix+str(addr))/UDP(dport=8888),timeout=0.1,verbose=0)
try:
if int(response[IP].proto)==1:
print(prefix+str(addr))
except:
pass
结果如下:并使用Wireshark抓包查看结果
root@kali:~# python UDP_ping.py
192.168.85.153
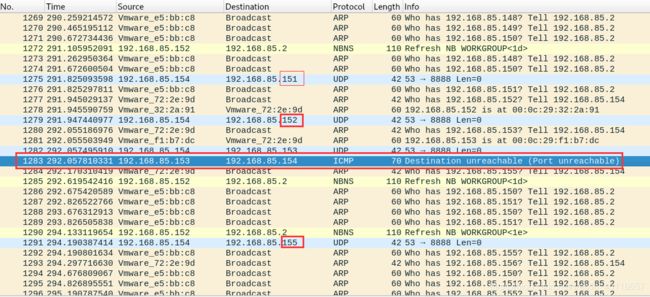
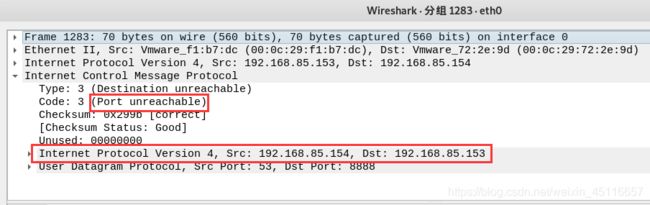
对于脚本中为什么int(response[IP].proto)==1,是因为使用UDP方式扫描目标主机时,使用的是一个最不常见的端口,如果该主机存活,则会返回目标端口不可达,即一个ICMP包;其中,IP协议中的 Protocol: ICMP (1) ,即值为1;
Internet Protocol Version 4, Src: 192.168.37.128, Dst: 192.168.37.131
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 56
Identification: 0x58e3 (22755)
Flags: 0x00
0... .... = Reserved bit: Not set
.0.. .... = Don't fragment: Not set
..0. .... = More fragments: Not set
Fragment offset: 0
Time to live: 128
Protocol: ICMP (1) #ICMP的值为1
......
2、Nmap
-
nmap 221.204.241.150-200 -PU53543 -sn
#使用UDP的方式去扫描多个主机,当返回端口不可达时,即主机存活; -
nmap 221.204.241.150-200 -PA53543 -sn
#使用ACK的方式去扫描多个主机,当收到RST包时,目标主机存活; -
nmap -iL IP.txt -PA80 -sn
#nmap可以扫描指定的IP地址列表,当收到RST包时,目标主机存活;
nmap 192.168.85.145-155 -PU53543 -sn
root@kali:~# nmap 221.204.241.150-200 -PU53543 -sn
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-15 16:53 CST
Nmap done: 51 IP addresses (0 hosts up) scanned in 12.03 seconds

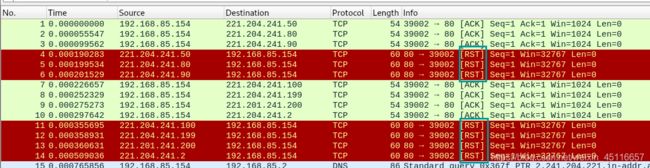
nmap 221.204.241.150-200 -PA53543 -sn
root@kali:~# nmap 221.204.241.150-200 -PA53543 -sn
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-15 16:57 CST
Nmap scan report for 150.241.204.221.adsl-pool.sx.cn (221.204.241.150)
Host is up (0.000035s latency).
Nmap scan report for 151.241.204.221.adsl-pool.sx.cn (221.204.241.151)
Host is up (0.00050s latency).
... ...
Nmap scan report for 197.241.204.221.adsl-pool.sx.cn (221.204.241.197)
Host is up (0.00011s latency).
Nmap scan report for 198.241.204.221.adsl-pool.sx.cn (221.204.241.198)
Host is up (0.000085s latency).
Nmap scan report for 199.241.204.221.adsl-pool.sx.cn (221.204.241.199)
Host is up (0.00012s latency).
Nmap scan report for 200.241.204.221.adsl-pool.sx.cn (221.204.241.200)
Host is up (0.00011s latency).
Nmap done: 51 IP addresses (51 hosts up) scanned in 2.41 seconds
root@kali:~# cat IP1.txt
221.204.241.2
221.204.241.100
221.204.241.50
221.204.241.80
221.201.241.200
221.204.241.90
221.204.241.199
root@kali:~# nmap -iL IP1.txt -PA80 -sn
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-15 17:04 CST
Nmap scan report for 2.241.204.221.adsl-pool.sx.cn (221.204.241.2)
Host is up (0.00011s latency).
Nmap scan report for 100.241.204.221.adsl-pool.sx.cn (221.204.241.100)
Host is up (0.00012s latency).
Nmap scan report for 50.241.204.221.adsl-pool.sx.cn (221.204.241.50)
Host is up (0.00039s latency).
Nmap scan report for 80.241.204.221.adsl-pool.sx.cn (221.204.241.80)
Host is up (0.00032s latency).
Nmap scan report for 221.201.241.200
Host is up (0.000094s latency).
Nmap scan report for 90.241.204.221.adsl-pool.sx.cn (221.204.241.90)
Host is up (0.00029s latency).
Nmap scan report for 199.241.204.221.adsl-pool.sx.cn (221.204.241.199)
Host is up (0.00014s latency).
Nmap done: 7 IP addresses (7 hosts up) scanned in 0.47 seconds
3、Hping3
3.1> 使用hping3 --udp扫描单个主机,当返回端口不可达时,证明主机存活;
root@kali:~# hping3 --udp 221.204.241.2 -c 1
HPING 221.204.241.2 (eth0 221.204.241.2): udp mode set, 28 headers + 0 data bytes
--- 221.204.241.2 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
root@kali:~# hping3 --udp 192.168.85.153 -c 1
HPING 192.168.85.153 (eth0 192.168.85.153): udp mode set, 28 headers + 0 data bytes
ICMP Port Unreachable from ip=192.168.85.153 name=UNKNOWN #ICMP端口不可达,证明主机存活
status=0 port=2647 seq=0
--- 192.168.85.153 hping statistic ---
1 packets transmitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 245.1/245.1/245.1 ms
3.2> 使用shell脚本判断多个主机是否存活;
脚本1:UDP_hping.sh
#!/bin/bash
#Author:橘子女侠
#该脚本用户实现扫描多个IP地址,并将存活主机的ip显示出来
if [ "$#" -ne 1 ]
then
echo "Example ./UDP_hping.sh 172.16.36.0"
fi
prefix=$(echo $1 |cut -d '.' -f 1-3)
for addr in $(seq 1 254)
do
hping3 $prefix.$addr --udp -c 1 >> r.txt
done
grep Unreachable r.txt | cut -d " " -f 5 | cut -d "=" -f 2 >> output.txt
rm r.txt
结果如下: 并使用Wireshark抓包查看;
root@root:~# chmod u+x UDP_hping.sh
root@root:~# ./UDP_hping.sh 221.204.241.0
--- 221.204.241.1 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.2 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.3 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.4 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.5 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.6 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.7 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.8 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.9 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.10 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
......
--- 221.204.241.252 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.253 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.254 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
#!/bin/bash
#Author:橘子女侠
#该脚本用于实现扫描多个IP地址,并将存活主机的IP地址显示出来
if [ "$#" -ne 1 ]
then
echo "Example ./UDP_hping.sh 172.16.36.0"
fi
prefix=$(echo $1 |cut -d '.' -f 1-3)
for addr in $(seq 1 254)
do
hping3 $prefix.$addr -c 1 >> r.txt
done
grep Unreachable r.txt | cut -d " " -f 5 | cut -d "=" -f 2 >> output.txt
rm r.txt
结果如下:并使用Wireshark抓包查看
root@root:~# chmod u+x TCP_hping.sh
root@root:~# ./TCP_hping.sh 221.204.241.0
./TCP_hping.sh:行2: [1: 未找到命令
--- 221.204.241.1 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.2 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.3 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.4 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.5 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.6 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.7 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.8 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.9 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.10 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
......
--- 221.204.241.252 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.253 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
--- 221.204.241.254 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms