Ble - SMP 协议详解
SMP Overview
- 蓝牙的配对过程中,加密是核心步骤,SMP关乎到蓝牙通信的安全。
- 在固定信道0x0006中传输数据,0x0006 LE SMP(secure manager protocol)b
- 整个smp过程根据是否支持ble security connection,设备IO capabilities,是否支持OOB(out of band)总共分为6种情况,最终协商确定1种方式实现smp flow。
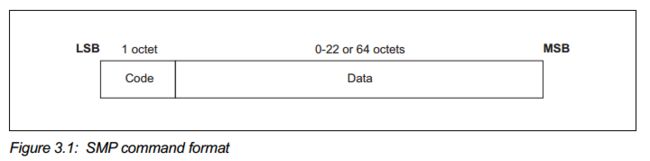
SMP 命令格式
如果支持LE security connect , L2CAP MTU = 65
否则 L2CAP MTU = 23
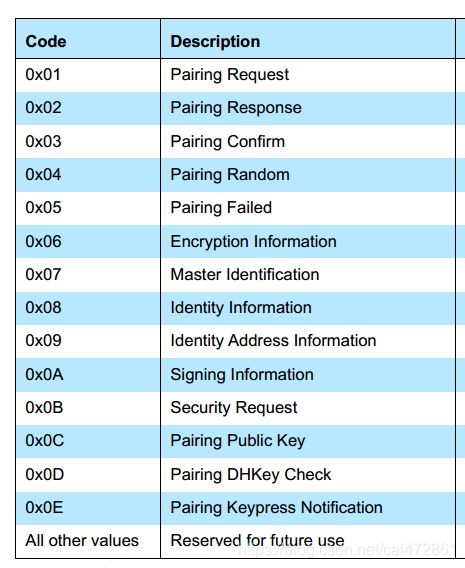
所有的交互从pairing request 开始,如果设备不支持smp,需要回复一个pairing fail event, 携带的reason为not support
超时
开启smp 之前,会起一个timer,
每次完成一个command ,smp timer 会被重置,重新计时
smp 结束之后,这个timer 需要被关闭
如果timer =30s,smp 仍未完成,smp timeout
SMP 流程
smp 过程大概分为四个部分
- step1. 交换信息
- step2. 产生STK/LTK,(short term key,long term key)
- step3. 在stk /ltk的基础上加密link
- step4. 在加密的link中分发 特殊的key
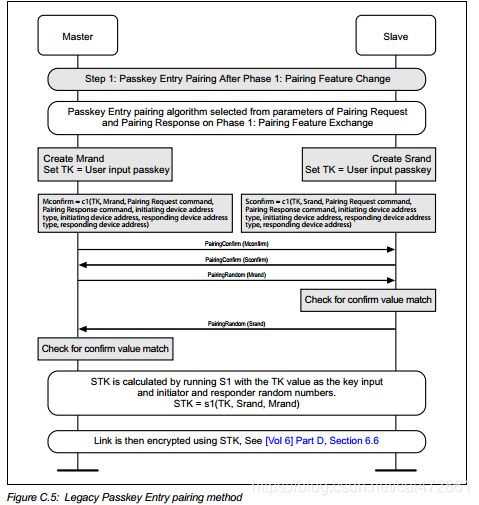
以下配图以LE legacy pairing为例说明:
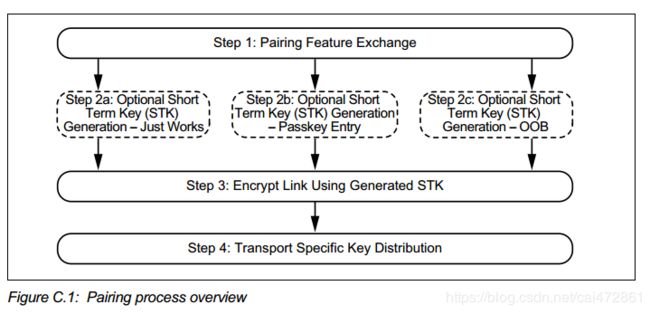
step1:pairing feature exchange
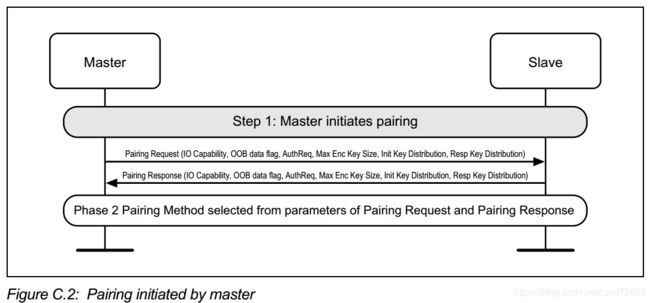
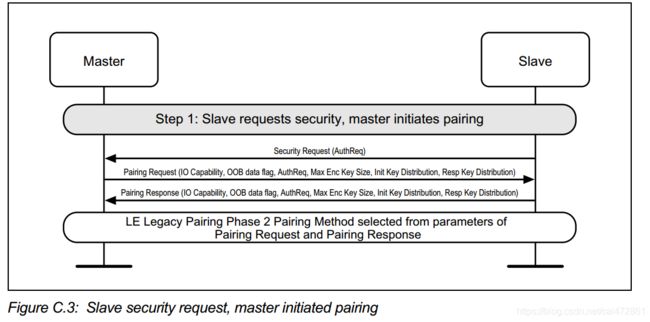
在这一步中,分两种情况,从master发起或者从slave 发起,后半段操作并无区别。
master 收到slave 的request 之后,会主动发起pairing request。
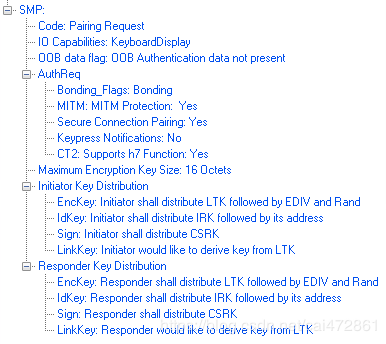
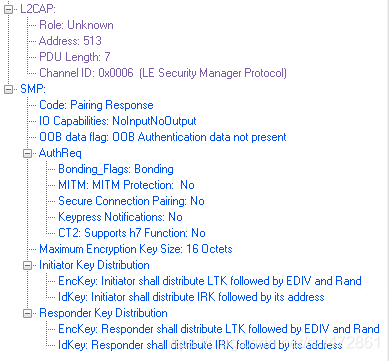
举个例子
根据Secure connection pairing参数,决定SMP第二步有两条分支
LE legacy pairing 和LE Secure Connections,例子中的链接属于LE legacy pairing
step2. AUTHENTICATING AND ENCRYPTING
根据第一步信息的交换,可以决定两个大分支,
再根据IO cap 和OOB等信息,一个大分支都包含三个小分支,
所以整体的SMP配对过程,总共有6种情况出现,详细如下:
LE legacy pairing
LE Secure Connections
- 区别于legacy ble 链接, LE secure connections 包括交换public key 的特殊步骤,
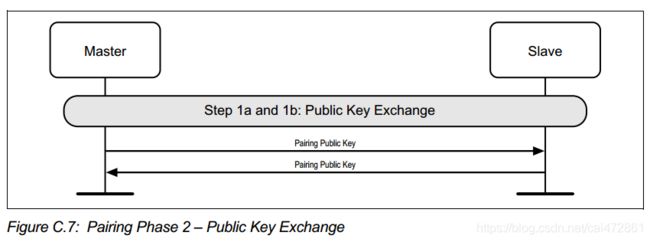
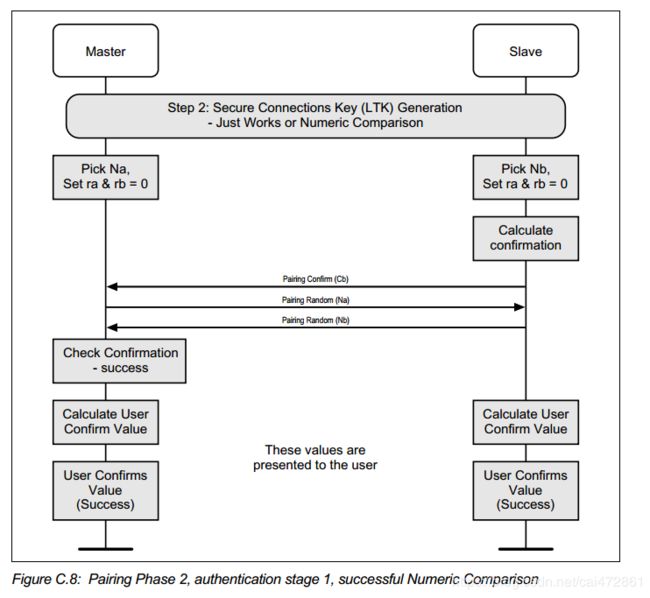
2. 第二个阶段根据OBB和IO Cap 不同,可以分为三种情况。
这一步的核心目的是,双方根据不同的参数,计算Na,Nb,并且进行校核,为下一步计算LTK做准备
just work :ra =rb =0
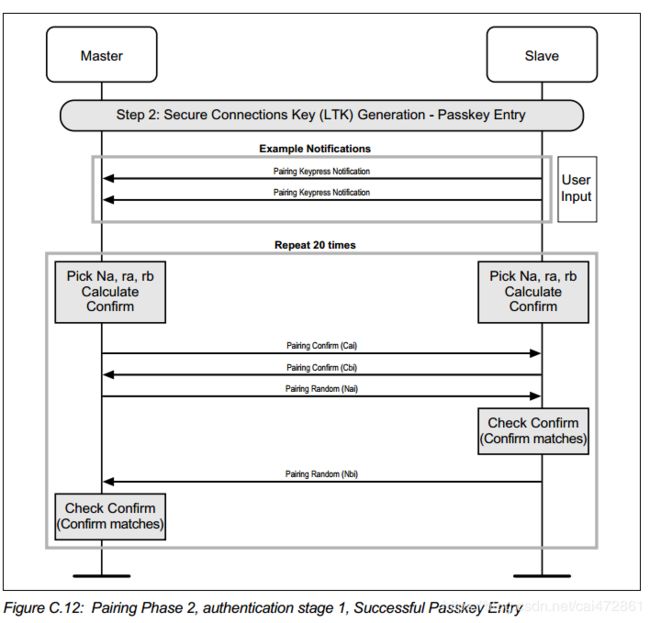
Passkey Entry: master 会接收到slave 输入key,双方都会计算Na,ra,rb,Nb,然后双方校核,重复20次
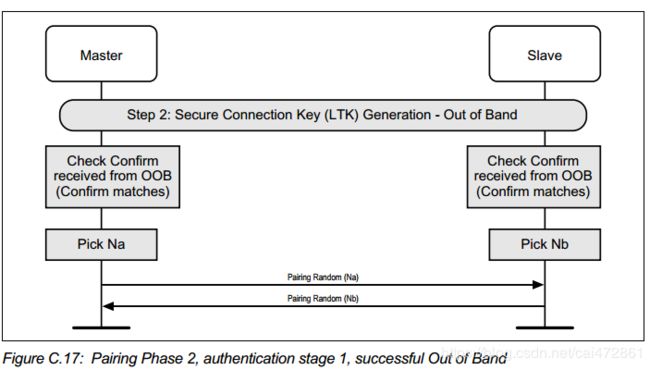
通过oob 管道,双方互换信息,然后计算,核对Na,Nb
3.LTK计算
Once the DHKey generation is complete, the Long Term Key (LTK) is
calculated from the DHKey.
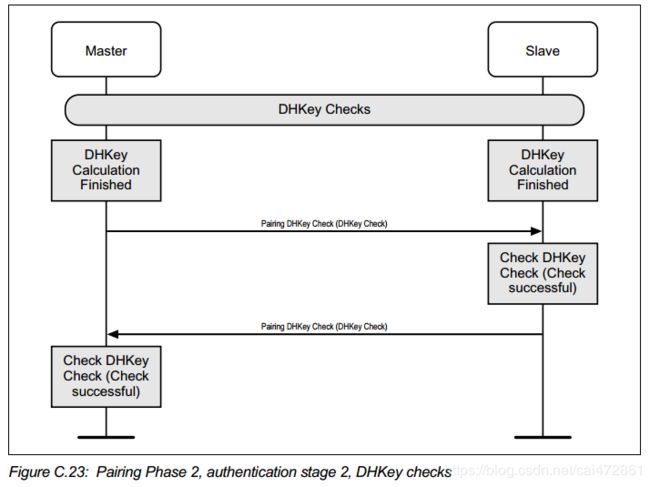
4.DHkey Check,加密 的第二个阶段
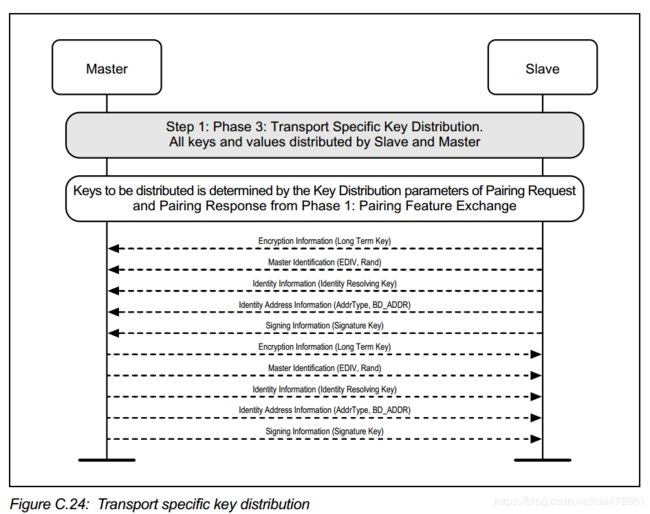
step3 TRANSPORT SPECIFIC KEY DISTRIBUTION
SMP 过程中key 的产生与计算
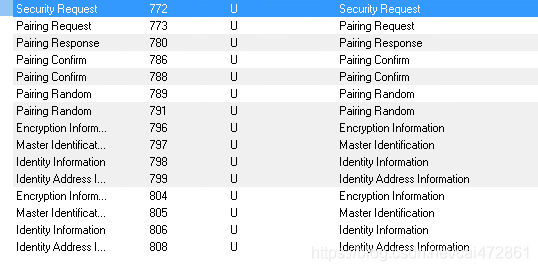
举个栗子
- 772 :slave 发起smp 请求
- 773: master 发起request,携带local 信息
- 780:slave return response, 携带slave 信息
根据双方信息,决定第二步的方式是LE legacy pairing +Just Work, (1/6)
- 786/788: confirm计算及交换
confirm value :16 octots = Mconfirm
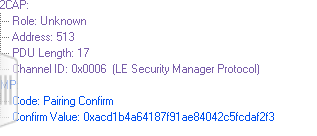
Mconfirm = c1(TK, Mrand,
Pairing Request command, Pairing Response command,
initiating device address type, initiating device address,
responding device address type, responding device address)
重点理解一下c1函数:
c1 (k, r, preq, pres, iat, rat, ia, ra) = e(k, e(k, r XOR p1) XOR p2)
TK值是一个128bit number
在justwork 中tk=0,
passkey entry:tk 0-999999
OOB:tk 128bit
函数e,128bit -AES
128bit key和128bit 一段文本,输出128bit加密数据
encryptedData = e(key, plaintextData)
计算stk使用s1函数
s1(k, r1, r2) = e(k, r’)
三个输入参数都是128bit
r’ 是有r1高位 64bit+ r2低位64bit拼接而成(大端模式)
Mconfirm计算
-
789/791,计算并交换Mrand和Srand
上一步已经计算出local confirm值,这一步获取到对端的random值,需要计算出peer confirm 值,如果相等,则会进一步计算STK
STK = s1(TK, Srand, Mrand)
根据rand和TK值计算
发起端需要使用STK值,加密链接。 -
791-808
最终加密之后交换如下几个信息:
Encryption Information:
此过程中需要根据已经生成的STK产生LTK,重新加密,
交换LTK
所有支持l2cap 加密的设备,都要有能力生成 LTK, EDIV, and Rand.
LTK = d1(ER, DIV, 0)
CSRK = d1(ER, DIV, 1)
d1(k, d, r) = e(k, d’)
d’ = padding || r || d
ER key 产生途径可以是随机产生的128bit或者自定义的值
Master Identification
已经被加密或者根据STK重新加密的时候会分发

Identity Information
交换IRK, 根据对端的IRK,可以解析出对端的随机地址
Note: An all zero Identity Resolving Key data field indicates that a device does
not have a valid resolvable private address
如果全为0,没有可解析的地址,不支持RPA
IRK = d1(IR, 1, 0)
DHK = d1(IR, 3, 0)
DHK不会被分发,只会自己根据交换的参数计算。
The generation of DHK using IR is only applicable when doing LE Legacy Pairing
The generation of IRK using IR is applicable both when doing LE Legacy Pairing and LE Secure Connections Pairing.
IR key 产生途径可以是随机产生的128bit或者自定义的值
Identity Address Information
交换identify addr 和addr type
Signing Information
Connection Signature Resolving Key (CSRK)
通过d1函数产生
综上所述,LE legacy pairing 过程中需要交换的key如下:
LTK
EDIV and Rand
IRK
BD_ADDR
CSRK
核心函数e
再举个栗子
LE security connect +Numeric Comparison
在这种模式下有如下key 会被交换:
- IRK
- BD ADDR
- CSRK
核心函数:
Cipher-based Message Authentication Code (CMAC)
that uses AES-128 as the block cipher function, also known as AES-CMAC
MAC = AES-CMACk(m)
k 128bit key
m可变长度
public key
P256 产生,private key,public key x,public y
当设备获取到对端的public key 之后,开始计算local DHK
DHkey=P256(Ska,Pkb)
输入参数为local private(secret)key和对端的public key
pairing confirm
产生并交换 Ca,Cb

使用到了函数f4
f4(U, V, X, Z) = AES-CMACx (U || V || Z)
Na,Nb,ra,rb是随机值,作为key
核心参数是local 和peer public key x
pairing random
交换随机值,这一步交换的是Na, Nb
DHkey check
传递Ea/Eb, DHkey check value, DHkey 本身不会交换。
计算Ea/Eb需要用到f6
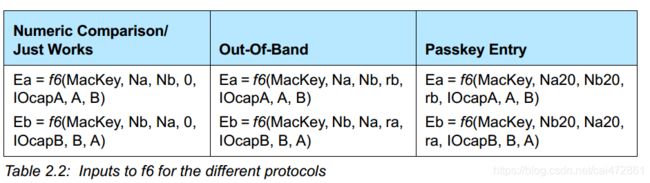
A/B是双方的address,
Mackey 又会引申到需要调用f5实现
MacKey || LTK = f5(DHKey, N_master, N_slave, BD_ADDR_master,BD_ADDR_slave)
f5(W, N1, N2, A1, A2) = AES-CMACt (Counter = 0 || keyID ||N1 || N2|| A1||A2|| Length = 256)||AES-CMACt(Counter = 1 || keyID || N1 || N2|| A1|| A2 ||Length = 256)
counter =0,计算的是MacKey
counter =1,计算的是LTK
在security connect 中,不会交换LTK,根据当前信息,可以计算出local 和peer
w与T的关系
T = AES-CMACsalt (W)
salt 是一个固定值,单词map带assic码,
W此次为计算的DHKey
另外几个常见的函数用法
g2 is used to generate the 6-digit numeric comparison values during authentication stage 1 in the pairing process.
h6 is used to generate the LE LTK from a BR/EDR link key derived from Secure Connections and is used to generate the BR/EDR link key from an LE LTK derived from Secure Connections.
h7 is used to generate intermediate keys while generating the LE LTK from a BR/EDR link key derived from Secure Connections and the BR/EDR link key
from an LE LTK derived from Secure Connections.