华为HCNA之ARP和Proxy ARP实验
导语:
ARP是用来将IP地址转换成MAC地址的协议
拓扑图:
步骤:
1.基础配置
如拓扑图所示,完成实验的各个物理设备和接口的配置
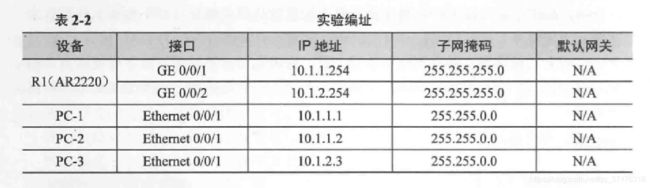
接下来查看主机的ARP表:
PC>arp -a
Internet Address Physical Address Type
可以看到,主机的ARP表为空;
接下来查看R1的ARP表:
[R1]display arp all
IP ADDRESS MAC ADDRESS EXPIRE(M) TYPE INTERFACE VPN-INSTANCE
VLAN/CEVLAN PVC
------------------------------------------------------------------------------
10.1.1.254 00e0-fc89-0476 I - GE0/0/1
10.1.2.254 00e0-fc89-0477 I - GE0/0/2
------------------------------------------------------------------------------
Total:2 Dynamic:0 Static:0 Interface:2
可以看到,R1仅有与之相连的两个接口ARP表项;
测试PC-1到R1和PC-2的连通性,测试PC-3到R1的连通性(自行测试,不贴代码了);
此时,再次查看PC-1和R1的ARP表项:
PC>arp -a
Internet Address Physical Address Type
10.1.1.2 54-89-98-1A-5D-B8 dynamic
[R1]display arp all
IP ADDRESS MAC ADDRESS EXPIRE(M) TYPE INTERFACE VPN-INSTANCE
VLAN/CEVLAN PVC
------------------------------------------------------------------------------
10.1.1.254 00e0-fc89-0476 I - GE0/0/1
10.1.1.1 5489-98c8-5a5c 13 D-0 GE0/0/1
10.1.2.254 00e0-fc89-0477 I - GE0/0/2
10.1.2.3 5489-98d3-3614 13 D-0 GE0/0/2
------------------------------------------------------------------------------
Total:4 Dynamic:2 Static:0 Interface:2
可以看到,此时PC-1和R1的ARP表项都已经变化了
2.配置静态ARP
如果ARP报文中的IP地址和MAC地址被映射错误的话,网关很容易被攻击,如:
[R1]arp static 10.1.1.1 5489-98CF-2803
[R1]display arp all
IP ADDRESS MAC ADDRESS EXPIRE(M) TYPE INTERFACE VPN-INSTANCE
VLAN/CEVLAN PVC
------------------------------------------------------------------------------
10.1.1.254 00e0-fc89-0476 I - GE0/0/1
10.1.2.254 00e0-fc89-0477 I - GE0/0/2
10.1.2.3 5489-98d3-3614 20 D-0 GE0/0/2
10.1.1.1 5489-98cf-2803 S--
------------------------------------------------------------------------------
Total:4 Dynamic:1 Static:1 Interface:2
此时,PC-1的MAC地址被错误配置了,这时,我们用R1和PC-1互相ping验证一下:
[R1]ping 10.1.1.1
PING 10.1.1.1: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 10.1.1.1 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
PC>ping 10.1.1.254
Ping 10.1.1.254: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
Request timeout!
Request timeout!
Request timeout!
--- 10.1.1.254 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
可以看到,此时PC-1和R1无法通信
为了应对ARP欺骗攻击,可以通过静态配置ARP表项来实现,如果静态配置的映射已经出现在ARP中则动态学习到的ARP配置无法进入到ARP表中:
[R1]undo arp static 10.1.1.1 5489-98cf-2803
[R1]arp static 10.1.1.1 5489-98c8-5a5c
[R1]arp static 10.1.1.2 5489-981a-5db8
[R1]arp static 10.1.2.3 5489-98d3-3614
[R1]display arp all
IP ADDRESS MAC ADDRESS EXPIRE(M) TYPE INTERFACE VPN-INSTANCE
VLAN/CEVLAN PVC
------------------------------------------------------------------------------
10.1.1.254 00e0-fc89-0476 I - GE0/0/1
10.1.2.254 00e0-fc89-0477 I - GE0/0/2
10.1.1.1 5489-98c8-5a5c S--
10.1.1.2 5489-981a-5db8 S--
10.1.2.3 5489-98d3-3614 S--
------------------------------------------------------------------------------
Total:5 Dynamic:0 Static:3 Interface:2
配置完成后,在PC-1上进行测试:
PC>ping 10.1.1.254
Ping 10.1.1.254: 32 data bytes, Press Ctrl_C to break
From 10.1.1.254: bytes=32 seq=1 ttl=255 time=47 ms
From 10.1.1.254: bytes=32 seq=2 ttl=255 time=32 ms
From 10.1.1.254: bytes=32 seq=3 ttl=255 time=31 ms
From 10.1.1.254: bytes=32 seq=4 ttl=255 time=47 ms
From 10.1.1.254: bytes=32 seq=5 ttl=255 time=31 ms
--- 10.1.1.254 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 31/37/47 ms
可以看到,恢复正常了。
3.配置Proxy ARP:
[R1]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 10 Routes : 10
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.1.1.0/24 Direct 0 0 D 10.1.1.254 GigabitEthernet
0/0/1
10.1.1.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
10.1.1.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
10.1.2.0/24 Direct 0 0 D 10.1.2.254 GigabitEthernet
0/0/2
10.1.2.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/2
10.1.2.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/2
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
默认情况下,ARP代理功能是关闭的,因此PC-2和PC-3不能联通:
PC>ping 10.1.2.3
Ping 10.1.2.3: 32 data bytes, Press Ctrl_C to break
From 10.1.1.2: Destination host unreachable
From 10.1.1.2: Destination host unreachable
From 10.1.1.2: Destination host unreachable
From 10.1.1.2: Destination host unreachable
From 10.1.1.2: Destination host unreachable
--- 10.1.2.3 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
如果配置ARP代理功能:
[R1]interface g0/0/1
[R1-GigabitEthernet0/0/1]arp-proxy enable
PC>ping 10.1.2.3
Ping 10.1.2.3: 32 data bytes, Press Ctrl_C to break
From 10.1.2.3: bytes=32 seq=1 ttl=127 time=63 ms
From 10.1.2.3: bytes=32 seq=2 ttl=127 time=78 ms
From 10.1.2.3: bytes=32 seq=3 ttl=127 time=47 ms
From 10.1.2.3: bytes=32 seq=4 ttl=127 time=78 ms
From 10.1.2.3: bytes=32 seq=5 ttl=127 time=63 ms
--- 10.1.2.3 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 47/65/78 ms
可以看到,此时PC-2能联通PC-3;
查看PC-2的ARP表:
PC>arp -a
Internet Address Physical Address Type
10.1.2.3 00-E0-FC-89-04-76 dynamic
至此,ARP和Proxy ARP实验完成!
最后,思考一个问题:
在ARP代理开启的情况下,如果在PC-2上PING10.1.2.4(不存在),icmp echo报文是在PC-2还是R1路由器丢掉的?
答:在R1路由器上丢掉的。R1的G0/0/1开启ARP代理后,收到PC-2的广播请求后,R1查看到有10.1.2.0/24的网络,于是R1将G0/0/1的MAC地址返回给PC-2,PC-2已此MAC地址为目的地址将保卫呢发送给R1;R1收到后,在ARP缓存中查找10.1.2.4的映射MAC地址
,但没发现10.1.2.4的映射条目,于是在10.1.2.0/24的网段中广播发送查找10.1.2.4,但是没有找到,于是丢弃icmp echo报文。
