攻防世界 crypto
幂数加密
这个 百度词条了一波 然而 并没有 新的发现 = = 然后发现了 用0位分隔符 然后相加
题目说的是大写 然后 直接大写
WELLDONE
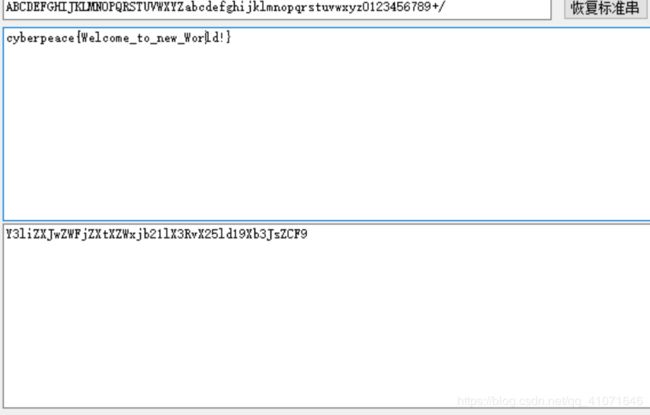
base64
简单的base64加密
Caesar
凯撒密码。。
#!/user/bin/env python
# -*-coding:utf-8 -*-
strs='oknqdbqmoq{kag_tmhq_xqmdzqp_omqemd_qzodkbfuaz}'
str_print='abcdefghijklmnopqrstuvwxyz'
flag=""
for i in range(26):
flag=""
for j in strs:
if j in str_print:
index=str_print.find(j)
index=index-i
if index<0:
index=index+26
flag+=str_print[index]
else:
flag+=j
if 'cyberpeace' in flag:
print flagMorse
莫斯密码。。
#!/user/bin/env python
# -*-coding:utf-8 -*-
map_table = {
'A': '.-', 'B': '-...', 'C': '-.-.',
'D': '-..', 'E': '.', 'F': '..-.',
'G': '--.', 'H': '....', 'I': '..',
'J': '.---', 'K': '-.-', 'L': '.-..',
'M': '--', 'N': '-.', 'O': '---',
'P': '.--.', 'Q': '--.-', 'R': '.-.',
'S': '...', 'T': '-', 'U': '..-',
'V': '...-', 'W': '.--', 'X': '-..-',
'Y': '-.--', 'Z': '--..',
'0': '-----', '1': '.----', '2': '..---',
'3': '...--', '4': '....-', '5': '.....',
'6': '-....', '7': '--...', '8': '---..',
'9': '----.',
',': '--..--', '.': '.-.-.-', ':': '---...', ';': '-.-.-.',
'?': '..--..', '=': '-...-', "'": '.----.', '/': '-..-.',
'!': '-.-.--', '-': '-....-', '_': '..--.-', '(': '-.--.',
')': '-.--.-', '$': '...-..-', '&': '. . . .', '@': '.--.-.'
}
strs="11 111 010 000 0 1010 111 100 0 00 000 000 111 00 10 1 0 010 0 000 1 00 10 110"
strs = strs.replace('1','-')
strs = strs.replace('0','.')
#print strs
strs=strs.split(' ')
#print code
flag=''
for i in strs:
if i=='':
flag+=' '
else:
index=dict(map(lambda t:(t[1],t[0]),map_table.items()))
flag+=index[i]
print 'cyberpeace{'+flag+'}'
flag=flag.lower()
print 'cyberpeace{'+flag+'}'Railfence
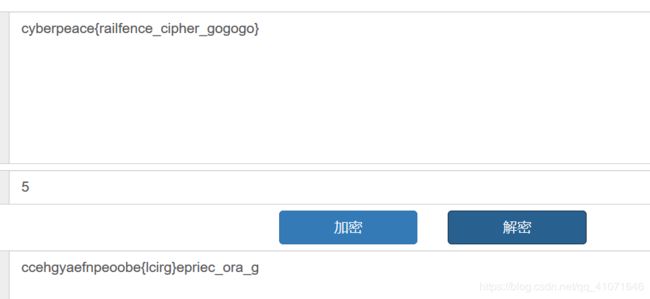
栅栏密码
这个不是普通的栅栏密码 = =
是变异的www 栅栏加密,
解密网站
http://www.atoolbox.net/Tool.php?Id=777
轮换机加密
这里直接用官方wp的脚本吧-=== =写的很好 = ==
#!/user/bin/env python
# -*-coding:utf-8 -*-
import re
sss='''1: < ZWAXJGDLUBVIQHKYPNTCRMOSFE < 2: < KPBELNACZDTRXMJQOYHGVSFUWI < 3: < BDMAIZVRNSJUWFHTEQGYXPLOCK < 4: < RPLNDVHGFCUKTEBSXQYIZMJWAO < 5: < IHFRLABEUOTSGJVDKCPMNZQWXY < 6: < AMKGHIWPNYCJBFZDRUSLOQXVET < 7: < GWTHSPYBXIZULVKMRAFDCEONJQ < 8: < NOZUTWDCVRJLXKISEFAPMYGHBQ < 9: < XPLTDSRFHENYVUBMCQWAOIKZGJ < 10: < UDNAJFBOWTGVRSCZQKELMXYIHP < 11 < MNBVCXZQWERTPOIUYALSKDJFHG < 12 < LVNCMXZPQOWEIURYTASBKJDFHG < 13 < JZQAWSXCDERFVBGTYHNUMKILOP <
'''
m="NFQKSEVOQOFNP"
content=re.findall(r'< (.*?) <',sss,re.S)
print content
iv=[2,3,7,5,13,12,9,1,8,10,4,11,6]
vvv=[]
ans=""
for i in range(13):
index=content[iv[i]-1].index(m[i])
vvv.append(index)
print vvv
for i in range(0,26):
flag=""
for j in range(13):
flag+=content[iv[j]-1][(vvv[j]+i)%26]
print flageasy rsa
确实是easy rsa
假设p=473398607161,q=4511491,e=17 求d 就很简单了
#!/user/bin/env python
# -*-coding:utf-8 -*-
from Crypto.Util.number import *
import gmpy2
import binascii
p=473398607161
q=4511491
e=17
phi=(p-1)*(q-1)
d=gmpy2.invert(e,phi)
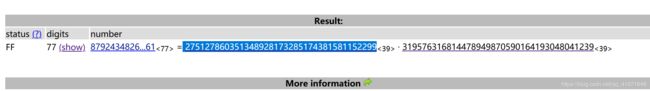
print d275127860351348928173285174381581152299
319576316814478949870590164193048041239
Normal_RSA
这个题目 有了两个文件
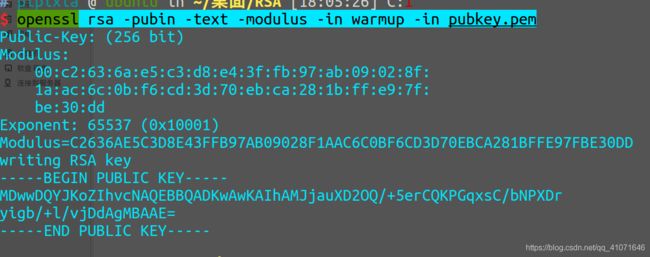
openssl 一把梭
openssl rsa -pubin -text -modulus -in warmup -in pubkey.pem
有了 e 和 n
只需要分解一下 n 然后用 p q e 就可以生成 私钥文件 得出flag
建议分解n 用网站分解
http://www.factordb.com/
275127860351348928173285174381581152299
319576316814478949870590164193048041239
然后生成 私钥文件
python3 rsatool.py -o private.pem -e 65537 -p 275127860351348928173285174381581152299 -q 319576316814478949870590164193048041239
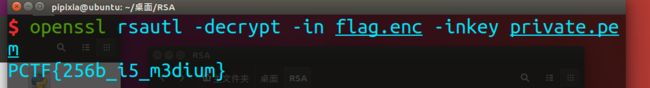
openssl rsautl -decrypt -in flag.enc -inkey private.pem
拿到flag
不仅仅是mouser
就是 摩尔斯+培根
混合编码
先试了一下 base64
出现了
LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw
然后发现 &# 后的的像是asicc 然后试了一下
然后 LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw
再继续base64
/119/101/108/99/111/109/101/116/111/97/116/116/97/99/107/97/110/100/100/101/102/101/110/99/101/119/111/114/108/100
然后在分割一下就是flag
#!/user/bin/env python
# -*-coding:utf-8 -*-
from Crypto.Util.number import *
import gmpy2
import binascii
import base64
s='LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw'
l=['76', '122', '69', '120', '79', '83', '56', '120', '77', '68', '69', '118', '77', '84', '65', '52', '76', '122', '107', '53', '76', '122', '69', '120', '77', '83', '56', '120', '77', '68', '107', '118', '77', '84', '65', '120', '76', '122', '69', '120', '78', '105', '56', '120', '77', '84', '69', '118', '79', '84', '99', '118', '77', '84', '69', '50', '76', '122', '69', '120', '78', '105', '56', '53', '78', '121', '56', '53', '79', '83', '56', '120', '77', '68', '99', '118', '79', '84', '99', '118', '77', '84', '69', '119', '76', '122', '69', '119', '77', '67', '56', '120', '77', '68', '65', '118', '77', '84', '65', '120', '76', '122', '69', '119', '77', '105', '56', '120', '77', '68', '69', '118', '77', '84', '69', '119', '76', '122', '107', '53', '76', '122', '69', '119', '77', '83', '56', '120', '77', '84', '107', '118', '77', '84', '69', '120', '76', '122', '69', '120', '78', '67', '56', '120', '77', '68', '103', '118', '77', '84', '65', '119']
strs=""
for i in l:
strs+=chr(int(i))
print strs
strs= base64.b64decode(strs)
print strs
strs=strs.split('/')
flag=''
print strs
strs=strs[1:]
for i in strs:
flag+=chr(int(i))
print flageasychallenge
这个题目感觉可以放到re里面 = =
#!/usr/bin/env python
# encoding: utf-8
import base64
def encode1(ans):
s = ''
for i in ans:
x = ord(i) ^ 36
x = x + 25
s += chr(x)
return s
def encode2(ans):
s = ''
for i in ans:
x = ord(i) + 36
x = x ^ 36
s += chr(x)
return s
def encode3(ans):
return base64.b32encode(ans)
def decode3(ans):
return base64.b32decode(ans)
def decode2(ans):
s=''
for i in ans:
x = ord(i) ^ 36
x = x - 36
s += chr(x)
return s
def decode1(ans):
s=''
for i in ans:
x = ord(i) - 25
x = x ^ 36
s += chr(x)
return s
print decode1(decode2(decode3('UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E===')))
flag = ' '
print 'Please Input your flag:'
flag = raw_input()
final = 'UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E==='
if encode3(encode2(encode1(flag))) == final:
print 'correct'
else:
print 'wrong'你猜猜
这个题目感觉是个杂项题目。。
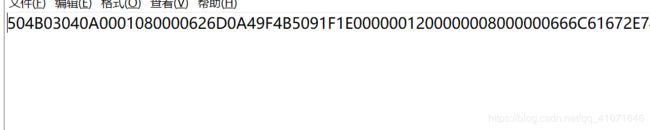
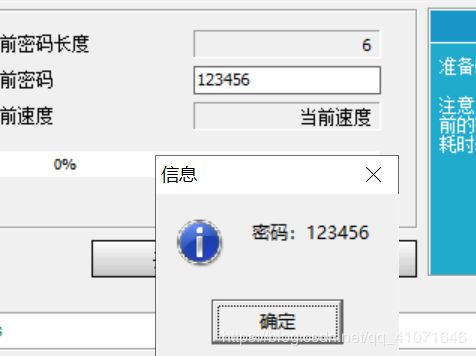
504b 一看就是zip的魔数。。。。 然后 压缩包密码 可以暴力跑出来 很简单的 123456.。。。
enc
这个题目就是很简单的了
打开发现都是
emm 转化成二进制 然后 转化成字符 然后转化成base64解码 然后莫斯解密。。
#!/usr/bin/env python
# encoding: utf-8
import base64
s='ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ZERO ZERO ZERO ONE ZERO ONE ONE ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ONE ZERO ONE ZERO ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ONE ZERO ONE ZERO ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ZERO ZERO ONE ONE ZERO ZERO ONE ONE ONE ZERO ONE ZERO ZERO ONE ONE ZERO ZERO ZERO ONE ZERO ONE ZERO ZERO ZERO ONE ZERO ZERO ONE ONE ONE ONE ZERO ONE ZERO ZERO ONE ONE ONE ONE ZERO ONE'
s=s.replace('ZERO','0')
s=s.replace('ONE','1')
print s
flag=""
for i in s:
if i!=' ':
flag+=i
print flag
strs=""
for i in range(0,len(flag),8):
strs+=chr(int(flag[i:i+8],2))
print strs
base_de=base64.b64decode(strs)
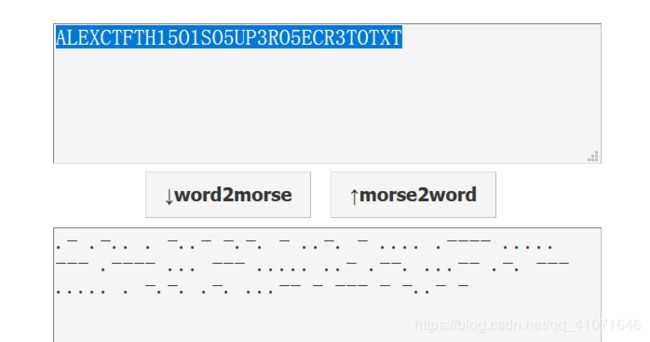
print base_de解出来的答案是ALEXCTFTH15O1SO5UP3RO5ECR3TOTXT
最后 flag ALEXCTF{TH15_1S_5UP3R_5ECR3T_TXT}
告诉你个秘密
这个题目 确实是学到了
转化成 字符 是
cjV5RyBscDlJIEJqTSB0RmhCVDZ1aCB5N2lKIFFzWiBiaE0g
base64解码得
r5yG lp9I BjM tFhBT6uh y7iJ QsZ bhM
然后 这 我就很懵逼了 ,
这是怎么解啊
搜了一波题解 , 然后知道了 就是 字符圈起来就可以了
TONGYUAN
Easy-one
这个题目感觉也算不难
给了一个示例的程序 和文件demo
这个算法很好逆向
但是我发现这个题目好像不太对劲,,
我在证实自己算法的对错的时候 发现一直乱码,,
后来根据demo 然后求了一波k 然后 把demo正确的k 用到了加密文件 发现正确了
然后一波搞定
#!/usr/bin/env python
# encoding: utf-8
import base64
output = open('msg002.enc','rb')
#outpin=open('msg001','rb')
#print outpin.read()
strs=output.read()
k= "VeryLongKeyYouWillNeverGuess"
flags=""
t=0
for i in range(len(strs)):
t=(ord(strs[i])-(ord(k[i%len(k)])^t)-i*i)&0xff
flags+=chr(t)
print flags
with open('deocde2.txt', 'wb') as f:
f.write(flags)
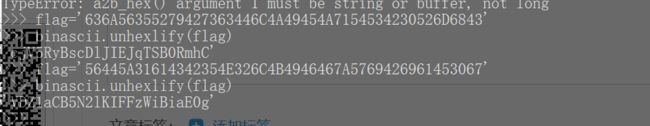
说我作弊需要证据
这个题目有点东西
先跟踪一下tcp流
base64解码一下发现
发现了很多东西。。。
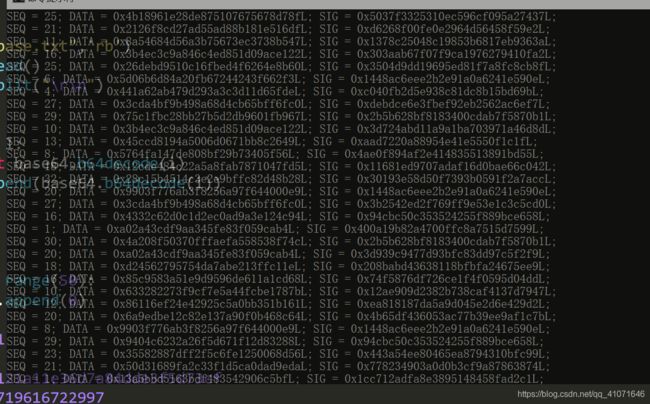
可以看出中间的data 就是 密文, 但是并不是很知道seq sig 是啥意思,,看了一下官方题解
seq 是 标号 或者可以说是顺序, , sig 是 SIG是RSA的签名 利用Alice的公钥对数据进行一次签名验证
知道了 啥都是啥意思 就可以直接写一下代码了,,。
#!/usr/bin/env python
# encoding: utf-8
from Crypto.Util.number import *
import gmpy2
import binascii
import hashlib
import base64
f=open("base.txt",'rb')
strs=f.read()
l=strs.split("\r\n")
s=[]
for i in l:
#print base64.b64decode(i)
s.append(base64.b64decode(i))
#print s
flag=[]
for i in range(50):
flag.append(0)
e=0x10001
n1=0x53a121a11e36d7a84dde3f5d73cf
q1=38456719616722997
p1=44106885765559411
n2=0x99122e61dc7bede74711185598c7
q2=49662237675630289
p2=62515288803124247
s1_phi=(q1-1)*(p1-1)
s2_phi=(q2-1)*(p2-1)
d1=int(gmpy2.invert(e, s1_phi))
d2=int(gmpy2.invert(e, s2_phi))
s=s[:-1]
DATAls=[]
SIGls=[]
SEQls=[]
for i in s:
SEQ=i.split(";")[0]
DATA=i.split(";")[1]
SIG=i.split(";")[2]
SEQ=SEQ.split('=')[1]
DATA=(DATA.split('=')[1])[:-1]
SIG=(SIG.split('=')[1])[:-1]
#print SEQ,DATA,SIG
SEQls.append(int(SEQ))
DATA=int(DATA,16)
C=pow(DATA,d2,n2)
#print chr(C)
DATAls.append(C)
SIG=int(SIG,16)
C=pow(SIG,e,n1)
#print C
SIGls.append(C)
#print SEQls
#print len(DATAls)
for i in range(148):
if DATAls[i]==SIGls[i]:
flag[SEQls[i]]=chr(DATAls[i])
print_flag=""
for i in range(33):
print_flag+=(flag[i])
print print_flag
Easy_Crypto
确实easy
#!/usr/bin/env python
# encoding: utf-8
from Crypto.Util.number import *
import gmpy2
import binascii
import hashlib
import base64
s=list(range(256))
key ='hello world'
f=open('enc.txt','rb')
strr=f.read()
i=0
j=0
for i in range(256):
j=(j+s[i]+ord(key[i%len(key)]))%256
s[i],s[j] = s[j],s[i]
i=0
j=0
flag=""
for m in range(37):
i=(i+1)%256
j=(j+s[i])%256
s[i],s[j] = s[j],s[i]
x=(s[i]+s[j]%256)%256
flag+=chr(ord(strr[m])^(s[x]))
print flag
cr4-poor-rsa
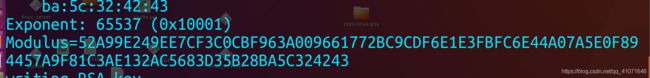
里面 有两个文件 然后openssl一波
openssl rsa -pubin -text -modulus -in warmup -in key.pub
然后求解就ok
#!/usr/bin/env python
# encoding: utf-8
from Crypto.PublicKey import RSA
import gmpy2
import binascii
import hashlib
import base64
n=long(0x52A99E249EE7CF3C0CBF963A009661772BC9CDF6E1E3FBFC6E44A07A5E0F894457A9F81C3AE132AC5683D35B28BA5C324243)
e=long(0x10001)
p = 863653476616376575308866344984576466644942572246900013156919
q = 965445304326998194798282228842484732438457170595999523426901
d = long(gmpy2.invert(e,(p-1)*(q-1)))
c = base64.b64decode("Ni45iH4UnXSttNuf0Oy80+G5J7tm8sBJuDNN7qfTIdEKJow4siF2cpSbP/qIWDjSi+w=")
key = RSA.construct((n,e,d))
print key.decrypt(c)wtc_rsa_bbq
看了好多题解 都是工具一把梭/。。。。
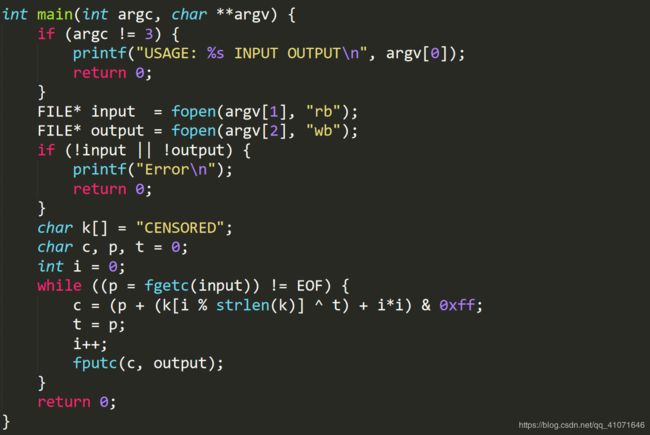
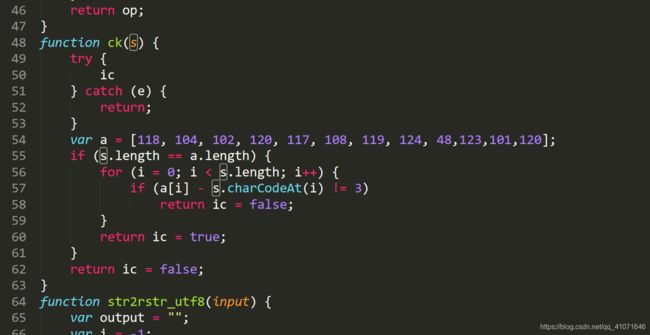
flag_in_your_hand
这个题目没啥说的
看代码。
重点在ck
逆向 出flag就可以了
cr3-what-is-this-encryption
什么都给了 直接求就可以了
#!/usr/bin/env python3
# encoding=utf-8
from Crypto.Util.number import *
import gmpy2
import binascii
import hashlib
import base64
p=0xa6055ec186de51800ddd6fcbf0192384ff42d707a55f57af4fcfb0d1dc7bd97055e8275cd4b78ec63c5d592f567c66393a061324aa2e6a8d8fc2a910cbee1ed9
q=0xfa0f9463ea0a93b929c099320d31c277e0b0dbc65b189ed76124f5a1218f5d91fd0102a4c8de11f28be5e4d0ae91ab319f4537e97ed74bc663e972a4a9119307
e=0x6d1fdab4ce3217b3fc32c9ed480a31d067fd57d93a9ab52b472dc393ab7852fbcb11abbebfd6aaae8032db1316dc22d3f7c3d631e24df13ef23d3b381a1c3e04abcc745d402ee3a031ac2718fae63b240837b4f657f29ca4702da9af22a3a019d68904a969ddb01bcf941df70af042f4fae5cbeb9c2151b324f387e525094c41
c=0x7fe1a4f743675d1987d25d38111fae0f78bbea6852cba5beda47db76d119a3efe24cb04b9449f53becd43b0b46e269826a983f832abb53b7a7e24a43ad15378344ed5c20f51e268186d24c76050c1e73647523bd5f91d9b6ad3e86bbf9126588b1dee21e6997372e36c3e74284734748891829665086e0dc523ed23c386bb520
pvi=(p-1)*(q-1)
n=q*p
d=gmpy2.invert(e,pvi)
print binascii.unhexlify(hex(pow(c,d,n))[2:])
safer-than-rot13
这个看半天,,, 没有看懂和 rot13有啥关系
直接用在线分析的词汇网站看了一波
https://quipqiup.com/
Decode_The_File
这个题目就很骚气了,,
下载文件 出来发现是一堆base64
我们解码写到文件里面 发现了,,、、
是一个 python的库文件
并且里面并没有什么值得有用的信息,
后来知道了这个是base64隐写
base64是 把3个 8bit的 字符 变成 4*6bit
但是如果 不够的话 会把 补零 如果字符是 000000 000000 那么对应表 就是 补上 = =
那么一个字符是 8bit 他就会补 16bit 也就是 两个 = = 加 2bit
其中 4字节只会对base64编码后产生影响 并不会对 编码前产生影响
那么。
这4个字节 就可以加密 造成 base64隐写
解密的方法也算是很简单 就是把 解码 然后在编码
然后再找出了= 之外的不同的地方
#!/usr/bin/env python3
# encoding=utf-8
import base64
import hashlib
import os
import pyDes
import sys
import time
base64str='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
def getindex(str1,str2):
for i in range(len(str1)):
if str1[i]!=str2[i]:
return abs(base64str.index(str1[i]) - base64str.index(str2[i]))
return 0
if __name__ =="__main__":
flag=""
f=open("4b","rb")
strs=f.read()
strs=strs.decode("utf-8")
ls=strs.split("\n")
for lines in ls:
mp=str(base64.b64encode(base64.b64decode(lines)), "utf-8")
offset = getindex(mp,lines)
pads_num = lines.count('=')
if pads_num :
flag+=bin(offset)[2:].zfill(pads_num * 2)
for i in range(0, len(flag), 8):
print(chr(int(flag[i:i + 8], 2)),end='')
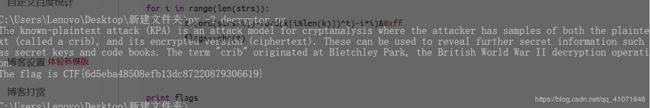
Handicraft_RSA
这个题目有点难顶, 参考链接
https://www.jianshu.com/p/9e0bb146c6d7
给了三个文件
把 output.txt 文件分解一下
有 e 有n 把n 分解一下 然后
写一个脚本就可以拿到flag。。。
脚本就是上面链接的脚本 直接粘上来
import base64
import gmpy2
from Crypto.Util.number import *
from Crypto.PublicKey import RSA
n=21702007965967851183912845012669844623756908507890324243024055496763943595946688940552416734878197459043831494232875785620294668737665396025897150541283087580428261036967329585399916163401369611036124501098728512558174430431806459204349427025717455575024289926516646738721697827263582054632714414433009171634156535642801472435174298248730890036345522414464312932752899972440365978028349224554681969090140541620264972373596402565696085035645624229615500129915303416150964709569033763686335344334340374467597281565279826664494938820964323794098815428802817709142950181265208976166531957235913949338642042322944000000001
p=139457081371053313087662621808811891689477698775602541222732432884929677435971504758581219546068100871560676389156360422970589688848020499752936702307974617390996217688749392344211044595211963580524376876607487048719085184308509979502505202804812382023512342185380439620200563119485952705668730322944000000001
q=155617827023249833340719354421664777126919280716316528121008762838820577123085292134385394346751341309377546683859340593439660968379640585296350265350950535158375685103003837903550191128377455111656903429282868722284520586387794090131818535032744071918282383650099890243578253423157468632973312000000000000001
e=65537
d = gmpy2.invert(e,(p-1)*(q-1))
key = RSA.construct((long(n), long(e), long(d), long(p), long(q)))
msg = base64.b64decode("eER0JNIcZYx/t+7lnRvv8s8zyMw8dYspZlne0MQUatQNcnDL/wnHtkAoNdCalQkpcbnZeAz4qeMX5GBmsO+BXyAKDueMA4uy3fw2k/dqFSsZFiB7I9M0oEkqUja52IMpkGDJ2eXGj9WHe4mqkniIayS42o4p9b0Qlz754qqRgkuaKzPWkZPKynULAtFXF39zm6dPI/jUA2BEo5WBoPzsCzwRmdr6QmJXTsau5BAQC5qdIkmCNq7+NLY1fjOmSEF/W+mdQvcwYPbe2zezroCiLiPNZnoABfmPbWAcASVU6M0YxvnXsh2YjkyLFf4cJSgroM3Aw4fVz3PPSsAQyCFKBA==")
for ss in range(20):
enc = key.decrypt(msg)
msg = enc
print msg