2019独角兽企业重金招聘Python工程师标准>>> ![]()
Introduction
This document will guide you to penetrate web applications step by step. We have followed OWASP (Open Web Application Security Project) and OSSTM (Open Source Security Testing Methodologies) to construct this article.
Objective
The objective of this article is to help the Security Analyst/Penetration Testers/Developers/Ethical Hackers to follow a step by step penetration testing process, discover the vulnerability, and exploit and mitigate the same.
Web Application Penetration Testing
The penetration test emulates what a malicious attacker with bad intentions would harm while they are penetrating the application. This is a test of people, systems and processes that are in place to detect, prevent, and respond to these kinds of attacks.
A Web Application Penetration Test includes the vulnerabilities that are discovered using the information gathering process, with the exploitation (if applicable), and the level of access and success the penetration tester was able to achieve.
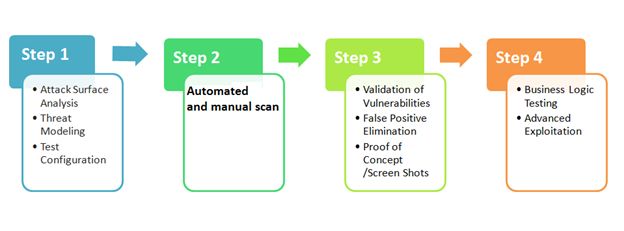
Below are the for steps penetration testing process:
Discover vulnerable systems using automated and manual vulnerability discovery.
Conduct real world attack simulation.
Mitigate threats and secure the platform.
Web Application Vulnerability Assessment
The Web Application Vulnerability Assessment does not include the exploitation phase. It contains the list of vulnerabilities, including the severity and the impact of the vulnerability on the application, along with the recommendations to resolve the same.
Web Application Audit
A Web Application Audit is a more in-depth view at the environment and processes, such as the backend server, database, secure code review, session management, authorization, and DMZ configuration.
It contains all the aspects of web application penetration testing and vulnerability assessment, including the below four phases.
Source Audit
Data Audit
Architecture Audit
Performance Audit
Please refer the above diagram for the classification of the four phases.
Steps to start with the Test
To start with the Web Application Audit, we need to follow the below steps:
Scoping of the Application
Checking for static and dynamic pages
Documenting number of logins and role of the users
Information Gathering
Threat Profiling
Make a list of all possible threats.
Comprehensive tests according to the created threat profile
Report
Report Creation
Internal Verification
Report Submission
The testing will be conducted in two phases.
Automated Test
Using Commercial tools available on the internet. i.e. Acunetix WVS, Netsparker.
Manual Test
Using manual testing tools like Burp Suite, OWASP ZAP Proxy
Burp Suite – Intruder, repeater, sequencer, spider used in the manual test.
Approach to the Web Application Penetration Test
Passive Approach
Understand the logic of the application
Information Gathering
Understand all the access points of the application
Active Approach
Configuration Management Testing.
SSL/TLS Testing
Testing for file extensions
Old, backup and unreferenced files
Testing for HTTP methods
Business Logic Testing
Testing for the business logic of the application
Testing for XSS
Testing for SQLi
Authentication Testing
Credentials transport over an encrypted channel- Check for SSL(https)
Testing for Guessable User Account
Brute Force Testing
Testing for bypassing authentication schema
Testing for vulnerable remember password and password reset
Testing for Logout and Browser Cache Management
Testing for CAPTCHA
Testing Multiple Factors Authentication
Authorization Testing
Authorization Testing
Testing for bypassing authorization schema
Testing for Privilege Escalation
Session Management Testing
Testing for Session Management Schema
Testing for Cookies attributes- http only, secure and time validity
Testing for Session Fixation
Testing for CSRF
The Scoping of the Application
Once the penetration tester has the URL/IP address of the application, he will start working on the scoping of the application. It generally includes the following things.
Gathering client requirements
Preparing a test plan
Profiling test boundaries
Defining Business objectives
Nature and behavior of the application
Describe each factor that builds a practical roadmap towards test execution
Test constraints
Types of testing
White Box
Provided with the complete knowledge of application/server and database along with the business logic of the application
Gray Box
Provided with the partial knowledge of the application/server
Privilege escalation may come under this
Black Box
Zero Knowledge Approach
An only thing that is provided to penetration tester is IP address/URL of the application
Need extra ordinary skills to exploit
Project management and scheduling
Limitations
Need of additional information
Check for the static and dynamic pages
Static page- Page created with HTML that remains the same all the time.
Dynamic page- It is a functional page that is generally connected with the database. For example, a login page.
Documenting number of logins and role of the users
Once the penetration tester has an idea about the scoping, static and dynamic pages, he will move on to analyze the number of logins and the types of users that can login to the particular application. If he is already provided with the list of usernames and passwords, it is a case of white box testing. If not, it will come under black box testing.
Information Gathering
In this phase, a penetration tester collects as much information as he can about the target.
Below is the check list for information gathering.
Spider, Robots and Crawlers
Search Engine Discovery
Testing Web Application Fingerprint
Application Discovery
Analysis of Error Codes
Real time example-
Let us assume I am working on a penetration testing project. My boss came to me and handed me a piece of paper saying that I have spoken to the CIO of the client and we have to start the penetration testing for the company Nous Infosystems. The legal department will be sending you all the documents and confirmation of the authorization. It’s a company you’ve never heard of before.
What now?
The information gathering starts from right here.
Threat Profiling
To ensure the comprehensive testing, it is a very good idea to start with a Threat Profile. A threat is simply the goal of your target. A Threat Profile is a comprehensive list of the threats that are relevant to that application.
These are expressed in terms of security threats.
List out all the possible threats that may harm the web application according to the business logic of the application.
A module-based threat profile should be created for the comprehensive penetration test.
For example:
Threat profile for public module
Threat profile for login module
Threat profile for password change module
Threat profile for logout module
Threat profile for business rule escalation module
Tests according to the threat profile
The threat profile is the key weapon of any attacker. Following the threat profile step by step can lead to discovery of very high and critical vulnerabilities.
Exploitation
Exploitation is the process of gaining control over a system.
End Goal: administrative-level access to the target.
During the penetration testing process, if a pen tester discovers a critical vulnerability that has an exploit or that can be exploited using our own scripts/code, he can use the Metasploit Framework to exploit the target or to develop his own exploit.
Prerequisite:
Scanning of the target.
Vulnerabilities found in the scanning phase.
Steps involved:
Check for the service/version running on the particular port.
Search the vulnerability in the service/version.
Exploit the target using tools like Metasploit..
Covering tracks and maintaining access:
Once exploitation has been done successfully, there are two ways to maintain the access.
Using Backdoors
Using Rootkits
For Example: Netcat, NetBus
Covering the Tracks
Destroying the evidence of presence and activities.
Log files contain the information of every activity that has been done on a computer, so it is very important to remove this log file. There are different ways to remove log files on Windows, Linux and MAC
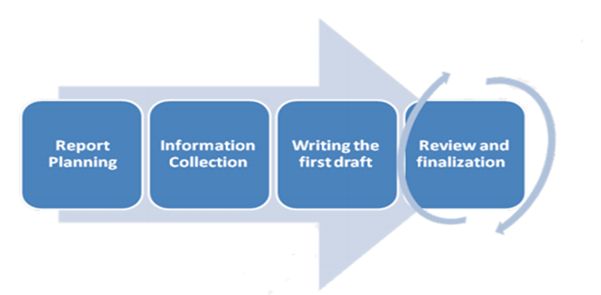
Reporting
A penetration testing report should contain
Below is the elaborated process of writing a penetration testing process.
Executive Summary
Scope
Overall Assessment
Key Vulnerabilities Discovered
Graphical representation of OWASP top 10
Key Findings and Action Items
Observations
Recommended Action Plan
Interpretation of Ratings
Threat Profile
Tools used (Optional)
Result of test cases
Guidelines for Developers
An executive summary.
Detailed description of the vulnerabilities.
Raw output.
Conclusion
A successful web application penetration test can be executed by following OWASP and OSSTM. Both are open source security testing methodologies. By reading this article you should have a great idea about how a web application penetrating test actually works. This article does not include the entire process of the WAPT, rather than it can be used as a reference document. For the most common and top vulnerabilities, refer to:
OWSAP TOP 10
SANS TOP 25
OSSTM (Open Source Security Testing Methodology)
References
https://www.owasp.org/index.php/Main_Page
http://www.isecom.org/research/osstmm.html
http://www.sans.org/
By Abhishek Dashora|April 24th, 2014