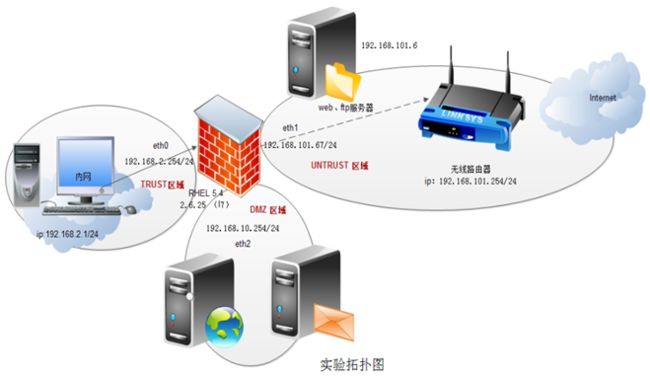
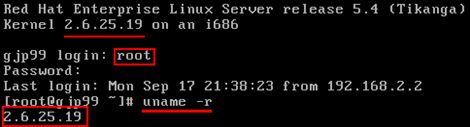
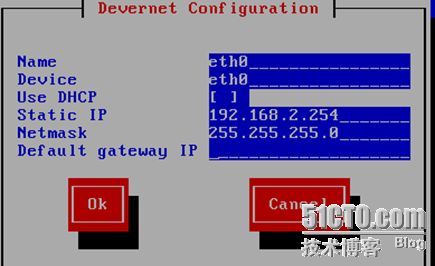
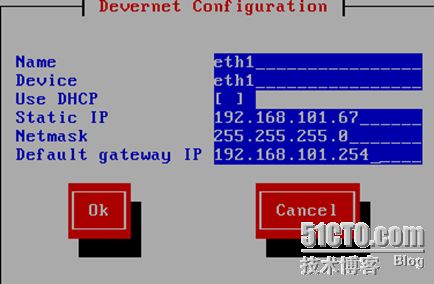
实验综合拓扑图:
注意事项:防火墙由Red Hat Linux 5.4 版本的机器充当,eth0 使用Host-only (vmware 1),eth1 使用Bridge(本地连接),eth2(vmware 2)
前期工作:
iptables 仅能过滤网络层的内容,例如协议、端口等等
如果想要过滤应用层的,需要打上七层协议的补丁包!还需内核支持!
操作步骤如下:
一、重新编译内核
1、合并kernel+layer7补丁
[root@gjp99 ~]# ll
total 48336
-rw------- 1 root root 960 Aug 2 21:30 anaconda-ks.cfg
drwxr-xr-x 2 root root 4096 Aug 2 21:41 Desktop
-rw-r--r-- 1 root root 35556 Aug 2 21:30 install.log
-rw-r--r-- 1 root root 4062 Aug 2 21:30 install.log.syslog
-rw-r--r-- 1 root root 435891 Aug 3 13:55 iptables-1.4.2.tar.bz2
-rw-r--r-- 1 root root 128196 Aug 3 13:55 l7-protocols-2008-10-04.tar.gz
-rw-r--r-- 1 root root 48622017 Aug 3 13:55 linux-2.6.25.19.tar.bz2
-rw-r--r-- 1 root root 174790 Aug 3 13:55 netfilter-layer7-v2.20.tar.gz
[root@gjp99 ~]# cd /usr/src/
[root@gjp99 src]# ll
total 24
drwxr-xr-x 3 root root 4096 Aug 2 21:25 kernels
drwxrwxr-x 21 root root 4096 Oct 23 2008 linux-2.6.25.19
drwxr-xr-x 4 1000 1000 4096 Aug 22 2008 netfilter-layer7-v2.20
drwxr-xr-x 7 root root 4096 Aug 2 21:27 redhat
[root@gjp99 src]# cd linux-2.6.25.19/
[root@gjp99 linux-2.6.25.19]# patch -p1 < /usr/src/netfilter-layer7-v2.20/kernel-2.6.25-layer7-2.20.patch
patching file net/netfilter/Kconfig
patching file net/netfilter/Makefile
patching file net/netfilter/xt_layer7.c
patching file net/netfilter/regexp/regexp.c
patching file net/netfilter/regexp/regexp.h
patching file net/netfilter/regexp/regmagic.h
patching file net/netfilter/regexp/regsub.c
patching file net/netfilter/nf_conntrack_core.c
Hunk #1 succeeded at 208 (offset -2 lines).
patching file net/netfilter/nf_conntrack_standalone.c
patching file include/net/netfilter/nf_conntrack.h
patching file include/linux/netfilter/xt_layer7.h
2、配置新内核
shell> cp /boot/config-2.6.18-8.el5 .config //偷个懒,沿用旧的内核配置
shell> make menuconfig
//配置内核时,在“Networking ---> Networking Options ---> Network Packet filtering framework (Netfilter) ”处主要注意两个地方:
1) Code Netfilter Configuration
//将“Netfilter connection tracking suport (NEW)”选择编译为模块(M),需选取此项才能看到layer7支持的配置。
//将layer7、string、state、time、IPsec、iprange、connlimit……等编译成模块,根据需要看着办。
2) IP: Netfilter Configuration
//将“IPv4 connection tracking support (require for NAT)”编译成模块。
//将“Full NAT”下的“MASQUERADE target support”和“REDIRECT target support”编译成模块。
3、编译及安装模块、新内核
shell> make && make modules_install && make install
//编译安装成后后,重启选择使用新的内核(2.6.25.19)引导系统
注意这里的ftp 要选上
二、重新编译iptables
1、卸载现有iptables
[root@gjp99 ~]# rpm -e iptables --nodeps
[root@gjp99 ~]# tar jxvf iptables-1.4.2.tar.bz2 -C /usr/src/
2、合并iptables+layer7补丁
[root@gjp99 ~]# cd /usr/src/netfilter-layer7-v2.20/iptables-1.4.1.1-for-kernel-2.6.20forward/
[root@gjp99 iptables-1.4.1.1-for-kernel-2.6.20forward]# ls
libxt_layer7.c libxt_layer7.man
[root@gjp99 iptables-1.4.1.1-for-kernel-2.6.20forward]# cp libxt_layer7.c libxt_layer7.man /usr/src/iptables-1.4.2/extensions/
3、编译安装
[root@gjp99 iptables-1.4.1.1-for-kernel-2.6.20forward]# cd /usr/src/iptables-1.4.2/
[root@gjp99 iptables-1.4.2]# ./configure --prefix=/ --with-ksource=/usr/src/linux-2.6.25.19
[root@gjp99 iptables-1.4.2]# make && make install
4、安装l7-protocols模式包
[root@gjp99 ~]# tar zxvf l7-protocols-2008-10-04.tar.gz -C /etc/
[root@gjp99 ~]# mv /etc/l7-protocols-2008-10-04/ /etc/l7-protocols
5. 加载ftp模块
[root@gjp99 iptables-1.4.2]# modprobe ip_nat_ftp
[root@gjp99 iptables-1.4.2]# lsmod
Module Size Used by
ip_nat_ftp 7361 0
案例配置
拓扑图:
工程部门 192.168.2.10--20
软件部门 192.168.2.21--30
经理办 192.168.2.31--40
上班时间 (周一---周五 08:20:00)
工程部门 : 上班时间ftp 不允许http qq 迅雷 下班后无限制
软件部门 : http 不允许非法站点sina ,不允许使用迅雷 ,连接数 最多3个 不允许聊天
不允许使用pplive ,下班后无限制
经理办公室:http qq 都可以,下班后无限制
dmz区域www服务器进行发布
一、准备工作:
1.linux下基本配置
配ip地址(setup命令)
[root@gjp99 ~]# ping 192.168.101.254
PING 192.168.101.254 (192.168.101.254) 56(84) bytes of data.
64 bytes from 192.168.101.254: icmp_seq=1 ttl=64 time=2.29 ms
64 bytes from 192.168.101.254: icmp_seq=2 ttl=64 time=0.685 ms
64 bytes from 192.168.101.254: icmp_seq=3 ttl=64 time=0.507 ms
[root@gjp99 ~]# ping www.baidu.com
PING www.a.shifen.com (119.75.217.56) 56(84) bytes of data.
64 bytes from 119.75.217.56: icmp_seq=1 ttl=56 time=131 ms
64 bytes from 119.75.217.56: icmp_seq=2 ttl=56 time=96.4 ms
64 bytes from 119.75.217.56: icmp_seq=3 ttl=56 time=125 ms
[root@gjp99 ~]# vim /etc/sysctl.conf
7 net.ipv4.ip_forward = 1
[root@gjp99 ~]# sysctl –p 修改生效
net.ipv4.ip_forward = 1
net.ipv4.conf.default.rp_filter = 1
net.ipv4.conf.default.accept_source_route = 0
kernel.sysrq = 0
kernel.core_uses_pid = 1
net.ipv4.tcp_syncookies = 1
kernel.msgmnb = 65536
kernel.msgmax = 65536
kernel.shmmax = 4294967295
kernel.shmall = 268435456
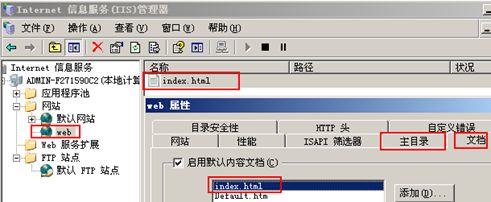
2. 搭建web及ftp服务器(windows server 2003 )
Internet 网上的一台web及ftp服务器:
开始---程序----管理工具-----iis
测试:
ftp服务器的设置:
测试:
二、基本配置及概念理解
1. 配置SNAT允许内网访问外网
[root@gjp99 ~]# iptables -t nat -A POSTROUTING -s 192.168.2.0/24 -o eth1 -j MASQUERADE
[root@gjp99 ~]# iptables -L -t nat -n --line-number 查看
Chain PREROUTING (policy ACCEPT)
num target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
num target prot opt source destination
1 MASQUERADE all -- 192.168.2.0/24 0.0.0.0/0
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
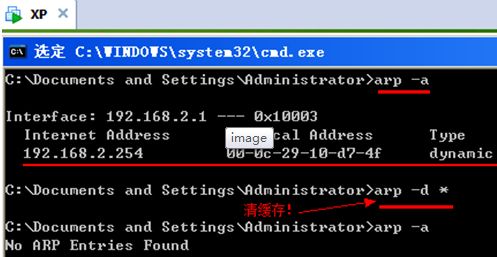
2.客户机测试能否正常访问internet网?
客户机ip:192.168.2.1/24 网关:192.168.2.254 DNS:222.88.88.88
C:\Documents and Settings\Administrator>ping 192.168.101.254
Pinging 192.168.101.254 with 32 bytes of data:
Reply from 192.168.101.254: bytes=32 time=3ms TTL=63
Reply from 192.168.101.254: bytes=32 time=1ms TTL=63
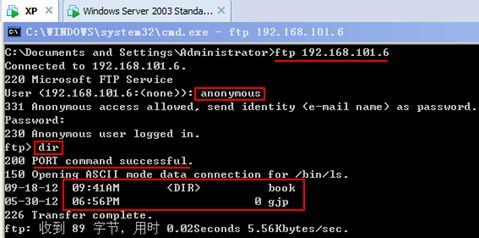
C:\Documents and Settings\Administrator>ftp 192.168.101.6 //ftp无法正常访问
Connected to 192.168.101.6.
220 Microsoft FTP Service
User (192.168.101.6:(none)): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 Anonymous user logged in.
ftp> dir
500 Invalid PORT Command.
150 Opening ASCII mode data connection for /bin/ls.
2.对input 、output 及FORWARD的理解
[root@gjp99 ~]# iptables -L –n // 默认接受,防火墙默认拒绝
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
以防ssh掉线,先把ssh添加进来!
[root@gjp99 ~]# iptables -A INPUT -s 192.168.2.2 -p tcp --dport 22 -j ACCEPT
[root@gjp99 ~]# iptables -P INPUT DROP //由于把ssh先添加过来,所以没有出现中断
[root@gjp99 ~]# iptables -L -v -n
Chain INPUT (policy DROP 1 packets, 229 bytes)
pkts bytes target prot opt in out source destination
93 6340 ACCEPT tcp -- * * 192.168.2.2 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT 51 packets, 2866 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 1036 packets, 97752 bytes)
pkts bytes target prot opt in out source destination
观察由于INPUT需要OUTPUT的响应,所以,input一旦DROP,现在内网是无法ping通网关的!
C:\Documents and Settings\Administrator>ping 192.168.2.254
Pinging 192.168.2.254 with 32 bytes of data:
Request timed out.
Request timed out.
OUTPUT 的响应指向ssh的源ip
[root@gjp99 ~]# iptables -A OUTPUT -d 192.168.2.2 -p tcp --sport 22 -j ACCEPT
[root@gjp99 ~]# iptables -P OUTPUT DROP
[root@gjp99 ~]# iptables -L -n --line-number
Chain INPUT (policy DROP)
num target prot opt source destination
1 ACCEPT tcp -- 192.168.2.2 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy DROP)
num target prot opt source destination
1 ACCEPT tcp -- 0.0.0.0/0 192.168.2.2 tcp spt:22
INPUT 与 OUTPUT 的状态不影响内部主机上网
C:\Documents and Settings\Administrator>ping www.baidu.com IP
Pinging www.a.shifen.com [119.75.218.77] with 32 bytes of data:
Reply from 119.75.218.77: bytes=32 time=40ms TTL=55
Reply from 119.75.218.77: bytes=32 time=38ms TTL=55
上网穿越的是FORWARD,所以,一旦FORWARD被拒绝掉,则内网与外网无法通信!
[root@gjp99 ~]# iptables -P FORWARD DROP
C:\Documents and Settings\Administrator>ping www.baidu.com
Ping request could not find host www.baidu.com. Please check the name and try again.
客户机已无法上网!为了安全,还是默认拒绝为好!
三、工程部门 : 上班时间ftp 不允许http qq 迅雷 下班后无限制
1. 实现ftp的功能!
第一种方法;需要4步:
[root@gjp99 ~]# iptables -t filter -A FORWARD -m iprange --src-range 192.168.2.10-192.168.2.20 -m time --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -p tcp --dport 21 -j ACCEPT
[root@gjp99 ~]# iptables -L -t filter
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 192.168.2.2 anywhere tcp dpt:ssh
Chain FORWARD (policy DROP)
target prot opt source destination
ACCEPT tcp -- anywhere anywhere source IP range 192.168.2.10-192.168.2.20 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri tcp dpt:ftp
Chain OUTPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- anywhere 192.168.2.2 tcp spt:ssh
[root@gjp99 ~]# iptables -t filter -A FORWARD -p tcp --sport 21 -j ACCEPT
[root@gjp99 ~]# iptables -t filter -A FORWARD -p tcp --sport 20 -j ACCEPT
[root@gjp99 ~]# iptables -t filter -A FORWARD -p tcp --dport 20 -j ACCEPT
内网客户机测试:

仅有ip 在192.168.2.10-20才能ftp上!但不能上网,只有这一个服务
[root@gjp99 ~]# iptables -L -v -n --line-number 查看是否有匹配的包!
Chain INPUT (policy DROP 11668 packets, 1093K bytes)
num pkts bytes target prot opt in out source destination
1 1254 86152 ACCEPT tcp -- * * 192.168.2.2 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy DROP 36 packets, 2242 bytes)
num pkts bytes target prot opt in out source destination
1 14 631 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.10-192.168.2.20 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri tcp dpt:21
2 37 2522 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:21
3 15 858 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:20
4 9 396 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:20
Chain OUTPUT (policy DROP 46 packets, 3016 bytes)
num pkts bytes target prot opt in out source destination
1 796 83084 ACCEPT tcp -- * * 0.0.0.0/0 192.168.2.2 tcp spt:22
第二种方法:需要2步!
state模块: (记录你流出的轨迹,自动让你返回!)
标准为 syn ack fin rst
请求 1 0 0 0 NEW
响应 1 1 × × ESTABLISHED
二次特性:我去访问你,后来你又来连接我了 RELATED
[root@gjp99 ~]# iptables -F FORWARD 下游规则清掉,默认规则是清不掉的!
[root@gjp99 ~]# iptables -L -v -n --line-number
Chain INPUT (policy DROP 11736 packets, 1102K bytes)
num pkts bytes target prot opt in out source destination
1 1316 90336 ACCEPT tcp -- * * 192.168.2.2 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy DROP 36 packets, 2242 bytes) 规则已清除!
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy DROP 46 packets, 3016 bytes)
num pkts bytes target prot opt in out source destination
1 848 88772 ACCEPT tcp -- * * 0.0.0.0/0 192.168.2.2 tcp spt:22
配置命令:
[root@gjp99 ~]# iptables -t filter -A FORWARD -m iprange --src-range 192.168.2.10-192.168.2.20 -m time --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -p tcp --dport 21 -j ACCEPT
[root@gjp99 ~]# iptables -t filter -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
查看有数据包匹配!
[root@gjp99 ~]# iptables -L -v -n --line-number
Chain INPUT (policy DROP 12092 packets, 1142K bytes)
num pkts bytes target prot opt in out source destination
1 1531 104K ACCEPT tcp -- * * 192.168.2.2 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy DROP 36 packets, 2242 bytes)
num pkts bytes target prot opt in out source destination
1 20 906 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.10-192.168.2.20 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri tcp dpt:21
2 21 1480 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
Chain OUTPUT (policy DROP 46 packets, 3016 bytes)
num pkts bytes target prot opt in out source destination
1 1026 107K ACCEPT tcp -- * * 0.0.0.0/0 192.168.2.2 tcp spt:22
2.由于FORWARD默认拒绝了,所以默认情况,内部成员是无法上网的,所以,不允许http qq 迅雷就可以不做了,默认即可!
3.下班时间无限制
[root@gjp99 ~]# iptables -t filter -A FORWARD -s 192.168.2.0/24 -o eth1 -m time --timestart 20:01 --timestop 07:59 -j ACCEPT
[root@gjp99 ~]# date
Tue Sep 18 10:34:27 CST 2012
[root@gjp99 ~]# date 091820012012 调整为下班时间测试
Tue Sep 18 20:01:00 CST 2012
内网主机已可以正常上网!
四、软件部门 : http 不允许非法站点sina ,不允许使用迅雷 ,连接数 最多3个 不允许聊天 不允许使用pplive ,下班后无限制
1.允许http 不允许非法站点sina的 配置命令:
[root@gjp99 ~]# iptables -t filter -A FORWARD -m iprange --src-range 192.168.2.21-192.168.2.30 -m time --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -m string --string "sina" --algo bm -j DROP
//网址包含sina的,禁止访问!
[root@gjp99 ~]# iptables -t filter -A FORWARD -m iprange --src-range 192.168.2.21-192.168.2.30 -m time --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -p tcp --dport 80 -j ACCEPT
//允许访问http
[root@gjp99 ~]# iptables -t filter -A FORWARD -m iprange --src-range 192.168.2.21-192.168.2.30 -m time --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -p udp --dport 53 -j ACCEPT
//访问http时,需要dns解析!
查看
[root@gjp99 ~]# iptables -L -v -n --line-number
Chain INPUT (policy DROP 13204 packets, 1275K bytes)
num pkts bytes target prot opt in out source destination
1 2672 189K ACCEPT tcp -- * * 192.168.2.2 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy DROP 46 packets, 2887 bytes)
num pkts bytes target prot opt in out source destination
1 20 906 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.10-192.168.2.20 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri tcp dpt:21
2 33 2775 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
3 12 723 ACCEPT all -- * eth1 192.168.2.0/24 0.0.0.0/0 TIME from 20:01:00 to 07:59:00
4 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.21-192.168.2.30 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri STRING match "sina" ALGO name bm TO 65535
5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.21-192.168.2.30 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri tcp dpt:80
6 0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.21-192.168.2.30 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri udp dpt:53
Chain OUTPUT (policy DROP 46 packets, 3016 bytes)
num pkts bytes target prot opt in out source destination
1 1829 194K ACCEPT tcp -- * * 0.0.0.0/0 192.168.2.2 tcp spt:22
ip 要在软件部门ip范围之内!
问题:禁止访问包含sina的,却能访问?
解决:
1. 把该条目放到第一条
[root@gjp99 ~]# iptables -t filter -I FORWARD 1 -m iprange --src-range 192.168.2.21-192.168.2.30 -m time --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -m string --string "sina" --algo bm -j DROP
2. 删除原来存在的那个条目!
[root@gjp99 ~]# iptables -t filter -D FORWARD 5
3. 查看结果
[root@gjp99 ~]# iptables -L -v -n --line-number
Chain INPUT (policy DROP 14045 packets, 1362K bytes)
num pkts bytes target prot opt in out source destination
1 2878 203K ACCEPT tcp -- * * 192.168.2.2 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy DROP 46 packets, 2887 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.21-192.168.2.30 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri STRING match "sina" ALGO name bm TO 65535
2 20 906 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.10-192.168.2.20 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri tcp dpt:21
3 3605 2087K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
4 172 9572 ACCEPT all -- * eth1 192.168.2.0/24 0.0.0.0/0 TIME from 20:01:00 to 07:59:00
5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.21-192.168.2.30 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri tcp dpt:80
6 0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.2.21-192.168.2.30 TIME from 08:00:00 to 20:00:00 on Mon,Tue,Wed,Thu,Fri udp dpt:53
Chain OUTPUT (policy DROP 46 packets, 3016 bytes)
num pkts bytes target prot opt in out source destination
1 1987 216K ACCEPT tcp -- * * 0.0.0.0/0 192.168.2.2 tcp spt:22
4.测试
注意:时间在你的限制范围之内拒绝,不在这个时间之内都能访问~
[root@gjp99 ~]# date 091811272012
Tue Sep 18 11:27:00 CST 2012
2.不允许使用迅雷 ,连接数 最多3个 不允许聊天 不允许使用pplive ,下班后无限制
iptables网络层过滤,基于端口 协议 所以必须使用7层
内网qq登录成功!
阻止qq登录
[root@gjp99 ~]# iptables -I FORWARD 2 -m iprange --src-range 192.168.2.21-192.168.2.30 -mtime --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -m layer7 --l7proto qq -j DROP
禁止迅雷的使用!
[root@gjp99 ~]# iptables -I FORWARD 2 -m iprange --src-range 192.168.2.21-192.168.2.30 -mtime --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -m layer7 --l7proto xunlei -j DROP
同种方法,可禁止其他的,许多!例如pplive 电驴,msn 等等! 前提必须在这个目录下存在的!否则,不支持
shell> iptables -A FORWARD -m layer7 --l7proto msnmessenger -j DROP
shell> iptables -A FORWARD -m layer7 --l7proto msn-filetransfer -j DROP //MSN聊天工具
shell> iptables -A FORWARD -m layer7 --l7proto xunlei -j DROP //迅雷下载
shell> iptables -A FORWARD -m layer7 --l7proto edonkey -j DROP //电驴下载
shell> iptables -A FORWARD -m layer7 --l7proto bittorrent -j DROP //BT下载
[root@gjp99 protocols]# pwd
/etc/l7-protocols/protocols
控制最大连接数3(限制打开的窗口数量,一个窗口可能有多个连接)
[root@gjp99 protocols]# iptables -I FORWARD 2 -m iprange --src-range 192.168.2.21-192.168.2.30 -mtime --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -p tcp --syn --dport 80 -m connlimit --connlimit-above 3 -j DROP
五、经理办公室:
http qq 都可以,下班后无限制
dmz区域www服务器进行发布
1.允许http qq 上网!
[root@gjp99 protocols]# iptables -A FORWARD -m iprange --src-range 192.168.2.31-192.168.2.40 -mtime --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -p udp --dport 53 -j ACCEPT
[root@gjp99 protocols]# iptables -A FORWARD -m iprange --src-range 192.168.2.31-192.168.2.40 -mtime --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -p tcp --dport 80 -j ACCEPT
[root@gjp99 protocols]# iptables -A FORWARD -m iprange --src-range 192.168.2.31-192.168.2.40 -mtime --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -m layer7 --l7proto qq -j ACCEPT
[root@gjp99 ~]# iptables -A FORWARD -m iprange --src-range 192.168.2.31-192.168.2.40 -mtime --timestart 08:00 --timestop 20:00 --weekdays Mon,Tue,Wed,Thu,Fri -p icmp -j ACCEPT
DNS解析(53)
http:(80)
ping (icmp)
2.测试 下班时间是否没有限制!
[root@gjp99 ~]# date 091820012012
Tue Sep 18 20:01:00 CST 2012
dmz区域www服务器进行发布(vmware 2)
[root@gjp99 ~]# iptables -t nat -A PREROUTING -d 192.168.101.67 -p tcp --dport 80 -i eth1 -j DNAT --to 192.168.10.8
[root@gjp99 ~]# iptables -t filter -A FORWARD -d 192.168.10.8 -p tcp --dport 80 -j ACCEPT
DMZ区域放置一台邮件服务器(参考postfix)
DNAT:
[root@gjp99 ~]# iptables -t nat -A PREROUTING -d 192.168.101.67 -p tcp --dport 25 -i eth1 -j DNAT --to 192.168.10.99
[root@gjp99 ~]# iptables -t filter -A FORWARD -d 192.168.10.99 -p tcp --dport 25 -j ACCEPT
SNAT:
[root@gjp99 ~]# iptables -t nat -A POSTROUTING -s 192.168.10.0/24 -o eth1 -j MASQUERADE
[root@gjp99 ~]# iptables -t filter -A FORWARD -s 192.168.10.99 -p tcp --dport 80 -o eth1 -j ACCEPT
邮件服务器:
ip :192.168.10.99/24 网关:192.168.10.254
修改:vim /etc/resolv.conf dns指向
vim /etc/sysctl.conf 数据包转发功能
第7行: 打开 用sysctl –p 生效!
允许ping
[root@gjp99 ~]# iptables -t filter -A FORWARD -s 192.168.10.99 -p icmp -o eth1 -j ACCEPT
![]()
iptables修改:
DNS 解析添加上!
[root@gjp99 ~]# iptables -t filter -A FORWARD -s 192.168.10.0/24 -p udp --dport 53 -j ACCEPT
[root@gjp99 ~]# iptables -t filter -A FORWARD -d 192.168.10.0/24 -p udp --sport 53 -j ACCEPT
邮件服务器的服务重启
service httpd start
windows server 2003 作为一台dmz区域的客户机
把windows server 2003 的安全级别降低点,可以打开页面
前台:
邮件发不出去,是由于该邮件域名为私有域名,internet网无法到达!
后台管理: