- 《架构300讲》学习笔记(201-250)
newProxyInstance
笔记架构
前言内容来自B站IT老齐架构300讲内容。201小心selectforupdate,有效规避索引选择性锁表202设计模式之建造者模式的用途20320分钟上手ELK日志监控系统分类:【ELK】204设计模式之门面模式Facade205设计模式之适配器模式Adapter206经典设计!如何让RabbitMQ支持消息延迟投递207Docker容器基于NFS实现跨容器文件共享208数据向上追溯场景该如何优
- Pwn,我的栈溢出笔记就该这么写(上)
「已注销」
栈
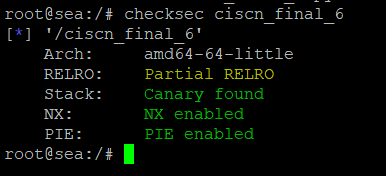
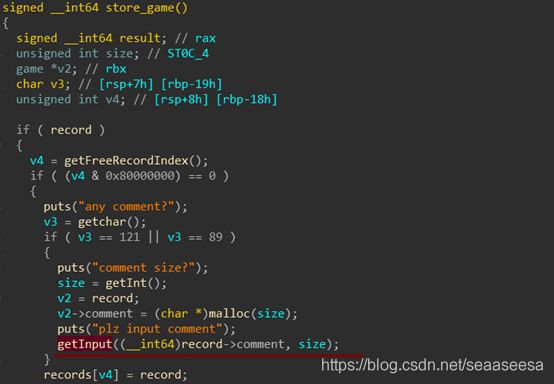
一周的刨坟结束了,忙着搭建维护k8s,该整个小小的笔记了原理篇什么是栈溢出?栈溢出指的是程序向栈中某个变量中写入的字节数超过了这个变量本身所申请的字节数,因而导致与其相邻的栈中的变量的值被改变。栈溢出会导致什么结果?栈溢出漏洞轻则可以使程序崩溃,重则可以使攻击者控制程序执行流程。如何防范栈溢出?(1).金丝雀(canary)1、在所有函数调用发生时,向栈帧内压入一个额外的随机DWORD(数),这个
- ctfshow做题笔记—前置基础—pwn13~pwn19
Yilanchia
笔记学习
文章目录前言一、pwn13二、pwn14三、pwn15(编译汇编代码到可执行文件,即可拿到flag)四、pwn16(使用gcc将其编译为可执行文件)五、pwn17六、pwn18七、pwn19(关闭了输出流,一定是最安全的吗?)前言记录一下pwn13~pwn19,巩固一下学到的知识。一、pwn13知识点:如何使用GCCgccmain.c-oprogram·gcc是调用GCC编译器的命令。·-opro
- ctf-web:php反序列化逃逸 -- GHCTF Escape!
A5rZ
php网络安全
step1寻找利用点随便注册一个进去,能写入文件isadmin){$tmp=file_get_contents("tmp/admin.html");echo$tmp;if($_POST['txt']){$content='';$content.=$_POST['txt'];file_put_contents($_POST['filename'],$content);}}else{$tmp=file
- Linux图形界面中客户端、服务器、窗口管理器之间的关系
谁不小心的
linux系统使用界面linux桌面环境x
作者:刘老师,华清远见嵌入式学院金牌讲师,ARMATC授权培训讲师。很多LINUX初学者在学习linux图形方面的知识时会遇到一些概念,如:X、X11、Xfree86、WM、KDE、GNOME、QT、QT/E、Qtopia、DirectFB、Framebuffer、显卡加速驱动等等。理解它们之间是什么关系,对我们学习来说是非常重要的。写这篇文章的目的,就是想让大家明晰这些概念及它们之间的关系。(部
- CTF中常用的小寄巧
脚底儿
网络网络安全ctf
ctf常用密码本/usr/share/wordlists最常用rockyou.txt需要gunzip解压一下全端口扫描nmap-sS-p1-65535-v192.168.187.1372、nmap扫描主机IP,发现目标主机IP为192.168.59.128nmap-sP-sV192.168.59.0/24主机发现:arp-scan-Ieth0-l^网卡打印可打印字符strings-el536.dm
- 新手必看——ctf六大题型介绍及六大题型解析&举例解题
沛哥网络安全
web安全学习安全udp网络协议
CTF(CaptureTheFlag)介绍与六大题型解析一、什么是CTF?CTF(CaptureTheFlag),意为“夺旗赛”,是一种信息安全竞赛形式,广泛应用于网络安全领域。CTF竞赛通过模拟现实中的网络安全攻防战,让参赛者以攻防对抗的形式,利用各种信息安全技术进行解决一系列安全问题,最终获得“旗帜(Flag)”来获得积分。CTF赛事一般分为两种形式:Jeopardy(解题模式):参赛者通过解
- 可重构智能表面仿真平台
brook1711
RIS
RIScomponentsThisisapythonprojectforRIS(reconfigurableintelligentsurface)simulations.relatedworksMyfirstpaperLinktomypaper/Pdftomypaper:[1]X.Guo,Y.ChenandY.Wang,“Learning-basedRobustandSecureTransmiss
- 第一篇:CTF入门指南:了解CTF的基本概念与比赛形式
菜腿承希
零基础小白入门CTFpythonjava网络安全前端
#零基础小白入门CTF解题到成为CTF大佬系列文章##引言CTF(CaptureTheFlag)是一种网络安全竞赛,参赛者需要通过解决各种安全相关的题目来获取“Flag”,从而得分。CTF题目通常涵盖密码学、逆向工程、漏洞利用、Web安全等多个领域。本系列文章将从零基础开始,逐步带你了解CTF的各个知识点,最终帮助你成为一名CTF大佬。##文章目录1.**CTF入门指南:了解CTF的基本概念与比赛
- 第二篇:CTF常见题型解析:密码学、逆向工程、漏洞利用、Web安全
菜腿承希
零基础小白入门CTFweb安全网络安全
#零基础小白入门CTF解题到成为CTF大佬系列文章##第二篇:CTF常见题型解析:密码学、逆向工程、漏洞利用、Web安全###引言在CTF比赛中,题目类型多种多样,涵盖了网络安全领域的多个方向。掌握这些题型的解题方法,是成为CTF大佬的关键。在本篇文章中,我们将详细解析CTF中常见的四大题型:密码学、逆向工程、漏洞利用和Web安全,帮助你快速入门并掌握解题技巧。---##2.1密码学(Crypto
- 【Crypto】CTF 密码学题目解题思路图
D-river
CTF密码学安全网络安全
CTF密码学题目解题思路图密码学题目├──1.编码/转换│├──1.1Base64││└──步骤:检查填充字符(=),解码工具(CyberChef)。│├──1.2Hex││└──步骤:检查0-9a-f,转换为ASCII。│├──1.3ASCII码││└──步骤:十进制/十六进制转字符。│└──1.4其他编码(摩尔斯、URL等)│└──步骤:识别符号(如.-/),使用专用解码器。│├──2.古典密
- 【Steg】CTF 隐写术题目解题思路图
D-river
CTF安全网络安全
以下是专门针对CTF隐写术(Steganography)的解题思路与步骤树形图,包含常见分类、工具链和关键方法:CTF隐写术题目解题思路图隐写术(Steganography)├──1.图片隐写(ImageSteg)│├──1.1LSB隐写(最低有效位)││├──步骤:StegSolve逐通道分析,提取LSB数据。││└──工具:StegSolve、zsteg、PythonPIL库。│││├──1.
- 自你离开后的第一篇关于MySQL和Hive开发生涯常见函数对比及SQL书写注意事项汇总
二百四十九先森
MySQL
涉及到的任何SQL语句或知识点,未特别注明则表明MySQL和Hive通用。一、时间函数一、时间函数1、时间转换时间戳转指定格式的时间:selectfrom_unixtime(1234567890,格式);格式默认是年月日时分秒,如果不是则需要指定格式。Hive(yyyy-MM-ddHH:mm:ss)。MySQL(%Y-%m-%d%H:%m:%s)。时间字符串转时间戳:selectunix_time
- ctf-web: php原生类利用 -- GHCTF Popppppp
A5rZ
php网络安全
源代码fruit1=$a;}function__destruct(){echo$this->fruit1;}publicfunction__toString(){$newFunc=$this->fruit2;return$newFunc();}}classForbidden{private$fruit3;publicfunction__construct($string){$this->fruit
- centos7升级curl到最新版包含离线安装方法
llody_55
vim
当前版本[root@consul~]#curl-Vcurl7.29.0(x86_64-redhat-linux-gnu)libcurl/7.29.0NSS/3.53.1zlib/1.2.7libidn/1.28libssh2/1.8.0Protocols:dictfileftpftpsgopherhttphttpsimapimapsldapldapspop3pop3srtspscpsftpsmtp
- 使用IDEA拉取GitLab项目
strong-1024
gitlab
使用组长提供的socket和账号密码登录内网的GitLab:打开IDEA新建项目,ProjectfromVersionControl在项目路径后面添加.git:
- ```markdown
伍辰惟
#超越边界:构建优雅的六边形架构(HexagonalArchitecture)hex-arch-kotlin-spring-bootReferenceJVMmultimoduleprojectforareactivemicroserviceandlambdausingahexagonalarchitecture,DDD,Kotlin,SpringBoot,Quarkus,Lambda,Gradle
- 探索未来架构的钥匙:Hex-Arch-Kotlin-Spring-Boot
孟振优Harvester
探索未来架构的钥匙:Hex-Arch-Kotlin-Spring-Boothex-arch-kotlin-spring-bootReferenceJVMmultimoduleprojectforareactivemicroserviceandlambdausingahexagonalarchitecture,DDD,Kotlin,SpringBoot,Quarkus,Lambda,Gradle.项
- [网络安全提高篇] 一二八.恶意软件分析之利用MS Defender实现恶意样本家族批量标注(含学术探讨)
Eastmount
网络安全自学篇web安全恶意软件分析恶意样本家族标注MSDefender
2024新的战场,继续奋斗。“网络安全提高班”新的100篇文章即将开启,包括Web渗透、内网渗透、靶场搭建、CVE复现、攻击溯源、实战及CTF总结,它将更加聚焦,更加深入,也是作者的慢慢成长史。换专业确实挺难的,Web渗透也是块硬骨头,但我也试试,看看自己未来四年究竟能将它学到什么程度,漫漫长征路,偏向虎山行。享受过程,一起加油~前文介绍了IDAPython配置过程和基础用法,然后尝试提取恶意软件
- 二进制安卓清单 binary AndroidManifest - XCTF apk 逆向-2
dilvx
androidxml
XCTF的apk逆向-2题目wp,这是一道反编译对抗题。题目背景AndroidManifest.xml在开发时是文本xml,在编译时会被aapt编译打包成为binaryxml。具体的格式可以参考稀土掘金MindMac做的类图(2014),下面的博客分别是wp和字段解析。攻防世界XCTF【Mobile】APK逆向-2题解正常下载附件,解压后,拖到JADX-gui中去反编译一下,然-掘金Android
- 广工anyview数据结构第六章676869
L比8伯
数据结构
DC06PE67试写一非递归算法,在二叉查找树T中插入元素e。二叉查找树的类型BSTree定义如下typedefstructfKeyTypekey;//其他数据域TElemType;typedefstructBSTNodefTElemTypedata;structBSTNode*lchild,*rchild;BSTNode,*BSTree;实现下列函数StatusInsertBSTI(BSTree
- Centos8部署mongodb报错记录
知本知至
MongoDBmongommsagentMongoDBops
使用mongoops安装mongodb6.0.4副本集报错errorwhileloadingsharedlibraries:libnetsnmpmibs.so.35:cannotopensharedobjectfile:Nosuchfileordirectory解决yuminstallnet-snmpnet-snmp-devel-y建议:初始化系统时把官网上的依赖包都装一遍即yuminstall-
- Django下防御Race Condition漏洞
落沐萧萧
djangopython后端
今天下午在v2ex上看到一个帖子,讲述自己因为忘记加分布式锁导致了公司的损失:我曾在《从Pwnhub诞生聊Django安全编码》一文中描述过关于商城逻辑所涉及的安全问题,其中就包含并发漏洞(RaceCondition)的防御,但当时说的比较简洁,也没有演示实际的攻击过程与危害。今天就以v2ex上这个帖子的场景来讲讲,常见的存在漏洞的Django代码,与我们如何正确防御竞争漏洞的方法。0x01Pla
- 分享一些自认为好用的解码平台
肆——
安全
综合平台:以下是两个含有多种解密网站的平台,可用于完成多数密码解密https://ctf.bugku.com/toolshttp://www.hiencode.com/摩斯密码解密平台:https://www.lddgo.net/encrypt/morse核心价值观解码平台:http://www.hiencode.com/cvencode.html
- 2025年渗透测试面试题总结-腾某讯-技术安全实习生(题目+回答)
独行soc
2025年渗透测试面试指南安全面试护网网络2015年
网络安全领域各种资源,学习文档,以及工具分享、前沿信息分享、POC、EXP分享。不定期分享各种好玩的项目及好用的工具,欢迎关注。目录腾讯-技术安全实习生一、SQL二次注入原理与修复二、SQL注入过滤information的绕过方法三、Redis未授权访问漏洞四、渗透测试标准化流程mermaid五、CTF经典题型案例六、文件下载漏洞利用七、HTTP不出网的命令执行漏洞处理八、隧道通信技术细节(以DN
- 【CTF比赛Web题目快速探测】
D-river
securityweb安全安全
CTF比赛Web题目快速探测一、快速信息收集1.基础信息扫描2.工具自动化辅助二、快速漏洞探测1.高频漏洞靶向测试2.前端相关漏洞三、工具链组合利用1.BurpSuite自动化2.专用工具链3.编码/解码辅助四、常见CTFWeb题快速索引表五、速攻思维导图六、总结在CTF比赛中快速攻克Web题目的核心是“高效信息收集+靶向性漏洞探测”,需结合手动测试与工具链快速定位漏洞类型。以下是一套实战优化流程
- 音频 bug 大全
DEDSEC_Roger
音频人工智能
解决:OSError:libsox.so:cannotopensharedobjectfile:Nosuchfileordirectory运行funasr训练时出现该错误安装个库就好了sudoaptinstalllibsox-dev解决:fatalerror:portaudio.h:Nosuchfileordirectory执行pipinstallPyAudio时出现该错误安装个库就好了sudoa
- 数据库事务,回滚到指定点 oracle java
xiaoyustudiowww
jvmjavaoracle
======oracle表sqlCREATETABLE"SMALL19RAIN"."R_TABLE_STU"("NAME"VARCHAR2(200BYTE),"AGE"NUMBER,"STU_ID"NUMBERNOTNULLENABLE,"DATARAIN"VARCHAR2(200BYTE))SEGMENTCREATIONIMMEDIATEPCTFREE10PCTUSED40INITRANS1MA
- 23种设计模式之《访问者模式(Visitor)》在c#中的应用及理解
yuanpan
设计模式访问者模式c#开发语言
程序设计中的主要设计模式通常分为三大类,共23种:1.创建型模式(CreationalPatterns)单例模式(Singleton):确保一个类只有一个实例,并提供全局访问点。工厂方法模式(FactoryMethod):定义创建对象的接口,由子类决定实例化哪个类。抽象工厂模式(AbstractFactory):提供一个创建一系列相关或依赖对象的接口,而无需指定具体类。建造者模式(Builder)
- MoeCTF 2023 CRYPTO 部分wp
("cat suan_cai_yu")
网络
MoeCTF2023CRYPTO部分wp前言MoeCTF2023CRYPTO方向的部分赛题0x01、baby_e知识点:低加密指数攻击0x02、bad_E知识点:e和phi不互素0x03:bad_random知识点:线性同余算法生成伪随机数0x04.|p-q|知识点:p和q很接近直接爆破0x05.minipack知识点:背包密码,贪心算法总结前言作者通过写文章记录自己的CTF经历,有不对的地方还请
- 深入浅出Java Annotation(元注解和自定义注解)
Josh_Persistence
Java Annotation元注解自定义注解
一、基本概述
Annontation是Java5开始引入的新特征。中文名称一般叫注解。它提供了一种安全的类似注释的机制,用来将任何的信息或元数据(metadata)与程序元素(类、方法、成员变量等)进行关联。
更通俗的意思是为程序的元素(类、方法、成员变量)加上更直观更明了的说明,这些说明信息是与程序的业务逻辑无关,并且是供指定的工具或
- mysql优化特定类型的查询
annan211
java工作mysql
本节所介绍的查询优化的技巧都是和特定版本相关的,所以对于未来mysql的版本未必适用。
1 优化count查询
对于count这个函数的网上的大部分资料都是错误的或者是理解的都是一知半解的。在做优化之前我们先来看看
真正的count()函数的作用到底是什么。
count()是一个特殊的函数,有两种非常不同的作用,他可以统计某个列值的数量,也可以统计行数。
在统
- MAC下安装多版本JDK和切换几种方式
棋子chessman
jdk
环境:
MAC AIR,OS X 10.10,64位
历史:
过去 Mac 上的 Java 都是由 Apple 自己提供,只支持到 Java 6,并且OS X 10.7 开始系统并不自带(而是可选安装)(原自带的是1.6)。
后来 Apple 加入 OpenJDK 继续支持 Java 6,而 Java 7 将由 Oracle 负责提供。
在终端中输入jav
- javaScript (1)
Array_06
JavaScriptjava浏览器
JavaScript
1、运算符
运算符就是完成操作的一系列符号,它有七类: 赋值运算符(=,+=,-=,*=,/=,%=,<<=,>>=,|=,&=)、算术运算符(+,-,*,/,++,--,%)、比较运算符(>,<,<=,>=,==,===,!=,!==)、逻辑运算符(||,&&,!)、条件运算(?:)、位
- 国内顶级代码分享网站
袁潇含
javajdkoracle.netPHP
现在国内很多开源网站感觉都是为了利益而做的
当然利益是肯定的,否则谁也不会免费的去做网站
&
- Elasticsearch、MongoDB和Hadoop比较
随意而生
mongodbhadoop搜索引擎
IT界在过去几年中出现了一个有趣的现象。很多新的技术出现并立即拥抱了“大数据”。稍微老一点的技术也会将大数据添进自己的特性,避免落大部队太远,我们看到了不同技术之间的边际的模糊化。假如你有诸如Elasticsearch或者Solr这样的搜索引擎,它们存储着JSON文档,MongoDB存着JSON文档,或者一堆JSON文档存放在一个Hadoop集群的HDFS中。你可以使用这三种配
- mac os 系统科研软件总结
张亚雄
mac os
1.1 Microsoft Office for Mac 2011
大客户版,自行搜索。
1.2 Latex (MacTex):
系统环境:https://tug.org/mactex/
&nb
- Maven实战(四)生命周期
AdyZhang
maven
1. 三套生命周期 Maven拥有三套相互独立的生命周期,它们分别为clean,default和site。 每个生命周期包含一些阶段,这些阶段是有顺序的,并且后面的阶段依赖于前面的阶段,用户和Maven最直接的交互方式就是调用这些生命周期阶段。 以clean生命周期为例,它包含的阶段有pre-clean, clean 和 post
- Linux下Jenkins迁移
aijuans
Jenkins
1. 将Jenkins程序目录copy过去 源程序在/export/data/tomcatRoot/ofctest-jenkins.jd.com下面 tar -cvzf jenkins.tar.gz ofctest-jenkins.jd.com &
- request.getInputStream()只能获取一次的问题
ayaoxinchao
requestInputstream
问题:在使用HTTP协议实现应用间接口通信时,服务端读取客户端请求过来的数据,会用到request.getInputStream(),第一次读取的时候可以读取到数据,但是接下来的读取操作都读取不到数据
原因: 1. 一个InputStream对象在被读取完成后,将无法被再次读取,始终返回-1; 2. InputStream并没有实现reset方法(可以重
- 数据库SQL优化大总结之 百万级数据库优化方案
BigBird2012
SQL优化
网上关于SQL优化的教程很多,但是比较杂乱。近日有空整理了一下,写出来跟大家分享一下,其中有错误和不足的地方,还请大家纠正补充。
这篇文章我花费了大量的时间查找资料、修改、排版,希望大家阅读之后,感觉好的话推荐给更多的人,让更多的人看到、纠正以及补充。
1.对查询进行优化,要尽量避免全表扫描,首先应考虑在 where 及 order by 涉及的列上建立索引。
2.应尽量避免在 where
- jsonObject的使用
bijian1013
javajson
在项目中难免会用java处理json格式的数据,因此封装了一个JSONUtil工具类。
JSONUtil.java
package com.bijian.json.study;
import java.util.ArrayList;
import java.util.Date;
import java.util.HashMap;
- [Zookeeper学习笔记之六]Zookeeper源代码分析之Zookeeper.WatchRegistration
bit1129
zookeeper
Zookeeper类是Zookeeper提供给用户访问Zookeeper service的主要API,它包含了如下几个内部类
首先分析它的内部类,从WatchRegistration开始,为指定的znode path注册一个Watcher,
/**
* Register a watcher for a particular p
- 【Scala十三】Scala核心七:部分应用函数
bit1129
scala
何为部分应用函数?
Partially applied function: A function that’s used in an expression and that misses some of its arguments.For instance, if function f has type Int => Int => Int, then f and f(1) are p
- Tomcat Error listenerStart 终极大法
ronin47
tomcat
Tomcat报的错太含糊了,什么错都没报出来,只提示了Error listenerStart。为了调试,我们要获得更详细的日志。可以在WEB-INF/classes目录下新建一个文件叫logging.properties,内容如下
Java代码
handlers = org.apache.juli.FileHandler, java.util.logging.ConsoleHa
- 不用加减符号实现加减法
BrokenDreams
实现
今天有群友发了一个问题,要求不用加减符号(包括负号)来实现加减法。
分析一下,先看最简单的情况,假设1+1,按二进制算的话结果是10,可以看到从右往左的第一位变为0,第二位由于进位变为1。
- 读《研磨设计模式》-代码笔记-状态模式-State
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
/*
当一个对象的内在状态改变时允许改变其行为,这个对象看起来像是改变了其类
状态模式主要解决的是当控制一个对象状态的条件表达式过于复杂时的情况
把状态的判断逻辑转移到表示不同状态的一系列类中,可以把复杂的判断逻辑简化
如果在
- CUDA程序block和thread超出硬件允许值时的异常
cherishLC
CUDA
调用CUDA的核函数时指定block 和 thread大小,该大小可以是dim3类型的(三维数组),只用一维时可以是usigned int型的。
以下程序验证了当block或thread大小超出硬件允许值时会产生异常!!!GPU根本不会执行运算!!!
所以验证结果的正确性很重要!!!
在VS中创建CUDA项目会有一个模板,里面有更详细的状态验证。
以下程序在K5000GPU上跑的。
- 诡异的超长时间GC问题定位
chenchao051
jvmcmsGChbaseswap
HBase的GC策略采用PawNew+CMS, 这是大众化的配置,ParNew经常会出现停顿时间特别长的情况,有时候甚至长到令人发指的地步,例如请看如下日志:
2012-10-17T05:54:54.293+0800: 739594.224: [GC 739606.508: [ParNew: 996800K->110720K(996800K), 178.8826900 secs] 3700
- maven环境快速搭建
daizj
安装mavne环境配置
一 下载maven
安装maven之前,要先安装jdk及配置JAVA_HOME环境变量。这个安装和配置java环境不用多说。
maven下载地址:http://maven.apache.org/download.html,目前最新的是这个apache-maven-3.2.5-bin.zip,然后解压在任意位置,最好地址中不要带中文字符,这个做java 的都知道,地址中出现中文会出现很多
- PHP网站安全,避免PHP网站受到攻击的方法
dcj3sjt126com
PHP
对于PHP网站安全主要存在这样几种攻击方式:1、命令注入(Command Injection)2、eval注入(Eval Injection)3、客户端脚本攻击(Script Insertion)4、跨网站脚本攻击(Cross Site Scripting, XSS)5、SQL注入攻击(SQL injection)6、跨网站请求伪造攻击(Cross Site Request Forgerie
- yii中给CGridView设置默认的排序根据时间倒序的方法
dcj3sjt126com
GridView
public function searchWithRelated() {
$criteria = new CDbCriteria;
$criteria->together = true; //without th
- Java集合对象和数组对象的转换
dyy_gusi
java集合
在开发中,我们经常需要将集合对象(List,Set)转换为数组对象,或者将数组对象转换为集合对象。Java提供了相互转换的工具,但是我们使用的时候需要注意,不能乱用滥用。
1、数组对象转换为集合对象
最暴力的方式是new一个集合对象,然后遍历数组,依次将数组中的元素放入到新的集合中,但是这样做显然过
- nginx同一主机部署多个应用
geeksun
nginx
近日有一需求,需要在一台主机上用nginx部署2个php应用,分别是wordpress和wiki,探索了半天,终于部署好了,下面把过程记录下来。
1. 在nginx下创建vhosts目录,用以放置vhost文件。
mkdir vhosts
2. 修改nginx.conf的配置, 在http节点增加下面内容设置,用来包含vhosts里的配置文件
#
- ubuntu添加admin权限的用户账号
hongtoushizi
ubuntuuseradd
ubuntu创建账号的方式通常用到两种:useradd 和adduser . 本人尝试了useradd方法,步骤如下:
1:useradd
使用useradd时,如果后面不加任何参数的话,如:sudo useradd sysadm 创建出来的用户将是默认的三无用户:无home directory ,无密码,无系统shell。
顾应该如下操作:
- 第五章 常用Lua开发库2-JSON库、编码转换、字符串处理
jinnianshilongnian
nginxlua
JSON库
在进行数据传输时JSON格式目前应用广泛,因此从Lua对象与JSON字符串之间相互转换是一个非常常见的功能;目前Lua也有几个JSON库,本人用过cjson、dkjson。其中cjson的语法严格(比如unicode \u0020\u7eaf),要求符合规范否则会解析失败(如\u002),而dkjson相对宽松,当然也可以通过修改cjson的源码来完成
- Spring定时器配置的两种实现方式OpenSymphony Quartz和java Timer详解
yaerfeng1989
timerquartz定时器
原创整理不易,转载请注明出处:Spring定时器配置的两种实现方式OpenSymphony Quartz和java Timer详解
代码下载地址:http://www.zuidaima.com/share/1772648445103104.htm
有两种流行Spring定时器配置:Java的Timer类和OpenSymphony的Quartz。
1.Java Timer定时
首先继承jav
- Linux下df与du两个命令的差别?
pda158
linux
一、df显示文件系统的使用情况,与du比較,就是更全盘化。 最经常使用的就是 df -T,显示文件系统的使用情况并显示文件系统的类型。 举比例如以下: [root@localhost ~]# df -T Filesystem Type &n
- [转]SQLite的工具类 ---- 通过反射把Cursor封装到VO对象
ctfzh
VOandroidsqlite反射Cursor
在写DAO层时,觉得从Cursor里一个一个的取出字段值再装到VO(值对象)里太麻烦了,就写了一个工具类,用到了反射,可以把查询记录的值装到对应的VO里,也可以生成该VO的List。
使用时需要注意:
考虑到Android的性能问题,VO没有使用Setter和Getter,而是直接用public的属性。
表中的字段名需要和VO的属性名一样,要是不一样就得在查询的SQL中
- 该学习笔记用到的Employee表
vipbooks
oraclesql工作
这是我在学习Oracle是用到的Employee表,在该笔记中用到的就是这张表,大家可以用它来学习和练习。
drop table Employee;
-- 员工信息表
create table Employee(
-- 员工编号
EmpNo number(3) primary key,
-- 姓