linux cred管理
I.credential管理
linux系统中,一个对象操作另一个对象时通常要做安全性检查。如一个进程操作一个文件,要检查进程是否有权限操作该文件。
linux内核中,credential机制的引入,正是对象间访问所需权限的抽象;主体提供自己权限的证书,客体提供访问自己所需权限的证书,根据主客体提供的证书及操作做安全性检查。
证书管理术语:
客体:指用户空间程序直接可以操作的系统对象,如进程、文件、消息队列、信号量、共享内存等;每个客体都有一组凭证,每种客体有不同的凭证集
客体所有者:客体凭证集有一部分表示客体所有者;如文件中uid表示文件的所有者
主体:操作客体的对象;除进程外大多数系统对象都不是主体,但在特殊环境下某些对象是主体,如文件在设置F_SETOWN后可以发送SIGIO信号到进程,这时文件就是主体,进程就是客体
行为:主体怎样操作客体,如读写执行文件等
客体上下文:客体被访问时所需权限凭证集
主体上下文:主体的权限凭证集
规则:主体操作客体时,用于安全检查
当主体操作客体时,根据主体上下文、客体上下文、操作来做安全计算,查找规则看主体是否有权限操作客体。
II.进程凭证集
i.cred
进程的凭证集可用结构cred表示,即可以表示主体权限凭证集,也可表示客体被访问时所需权限凭证集;进程描述符中cred和real_cred字段分别指向主体与客体的证书
进程cred结构如下:
93 /*
94 * The security context of a task
95 *
96 * The parts of the context break down into two categories:
97 *
98 * (1) The objective context of a task. These parts are used when some other
99 * task is attempting to affect this one.
100 *
101 * (2) The subjective context. These details are used when the task is acting
102 * upon another object, be that a file, a task, a key or whatever.
103 *
104 * Note that some members of this structure belong to both categories - the
105 * LSM security pointer for instance.
106 *
107 * A task has two security pointers. task->real_cred points to the objective
108 * context that defines that task's actual details. The objective part of this
109 * context is used whenever that task is acted upon.
110 *
111 * task->cred points to the subjective context that defines the details of how
112 * that task is going to act upon another object. This may be overridden
113 * temporarily to point to another security context, but normally points to the
114 * same context as task->real_cred.
115 */
116 struct cred {
117 atomic_t usage;
118 #ifdef CONFIG_DEBUG_CREDENTIALS
119 atomic_t subscribers; /* number of processes subscribed */
120 void *put_addr;
121 unsigned magic;
122 #define CRED_MAGIC 0x43736564
123 #define CRED_MAGIC_DEAD 0x44656144
124 #endif
125 uid_t uid; /* real UID of the task */
126 gid_t gid; /* real GID of the task */
127 uid_t suid; /* saved UID of the task */
128 gid_t sgid; /* saved GID of the task */
129 uid_t euid; /* effective UID of the task */
130 gid_t egid; /* effective GID of the task */
131 uid_t fsuid; /* UID for VFS ops */
132 gid_t fsgid; /* GID for VFS ops */
133 unsigned securebits; /* SUID-less security management */
134 kernel_cap_t cap_inheritable; /* caps our children can inherit */
135 kernel_cap_t cap_permitted; /* caps we're permitted */
136 kernel_cap_t cap_effective; /* caps we can actually use */
137 kernel_cap_t cap_bset; /* capability bounding set */
138 #ifdef CONFIG_KEYS
139 unsigned char jit_keyring; /* default keyring to attach requested
140 * keys to */
141 struct key *thread_keyring; /* keyring private to this thread */
142 struct key *request_key_auth; /* assumed request_key authority */
143 struct thread_group_cred *tgcred; /* thread-group shared credentials */
144 #endif
145 #ifdef CONFIG_SECURITY
146 void *security; /* subjective LSM security */
147 #endif
148 struct user_struct *user; /* real user ID subscription */
149 struct group_info *group_info; /* supplementary groups for euid/fsgid */
150 struct rcu_head rcu; /* RCU deletion hook */
151 };usage:表于证书引用管理
uid:实际用户id
gid:实际用户组id
suid:保存的用户uid
sgid;保存的用户组gid
euid:真正有效的用户id
egid:真正有效的用户组id
securebits:安全管理标识;用来控制凭证的操作与继承
cap_inheritable:execve时可以继承的权限
cap_permitted:可以(通过capset)赋予cap_effective的权限
cap_effective:进程实际使用的权限
cap_bset:主要用于uid=0或euid=0时,execve可以继承的权限,cap_permitted=cap_inheritable+cap_bset,cap_effective=cap_permitted。可以将cap_bset中的权限通过调用capset赋给cap_inheritable
user:主要表示用户信息,如用户进程数、打开文件数等
rcu:RCU删除用
ii.capability
execve时,SETUID置位且用户是root时,权限之间的关系如下(passwd为例):
[redhat@localhost linux-2.6.32.60]$ ll /usr/bin/passwd
-rwsr-xr-x. 1 root root 26980 1月 29 2010 /usr/bin/passwd
[redhat@localhost linux-2.6.32.60]$ ps -f -t pts/1
UID PID PPID C STIME TTY TIME CMD
redhat 5509 2852 0 Jun11 pts/1 00:00:00 bash
root 20771 5509 0 12:02 pts/1 00:00:00 passwd
[redhat@localhost linux-2.6.32.60]$ cat /proc/5509/status
Name: bash
State: S (sleeping)
Tgid: 5509
Pid: 5509
PPid: 2852
TracerPid: 0
Uid: 500 500 500 500
Gid: 500 500 500 500
CapInh: 0000000000000000
CapPrm: 0000000000000000
CapEff: 0000000000000000
CapBnd: ffffffffffffffff
[redhat@localhost linux-2.6.32.60]$ cat /proc/20771/status
Name: passwd
State: S (sleeping)
Tgid: 20771
Pid: 20771
PPid: 5509
TracerPid: 0
Uid: 500 0 0 0
Gid: 500 500 500 500
CapInh: 0000000000000000
CapPrm: ffffffffffffffff
CapEff: ffffffffffffffff
CapBnd: ffffffffffffffff
[redhat@localhost linux-2.6.32.60]$ passwd程序用户是root,且设置SETUID标志,用于普通用户在执行passwd时可以修改需要root权限的/etc/passwd文件。
当运行passwd时,实际用户uid=500(redhat)不变,保存用户suid、有效用户euid均变成0(root),此时权限关系如下:
cap_permitted=cap_inheritable+cap_bset
cap_effective=cap_permitted
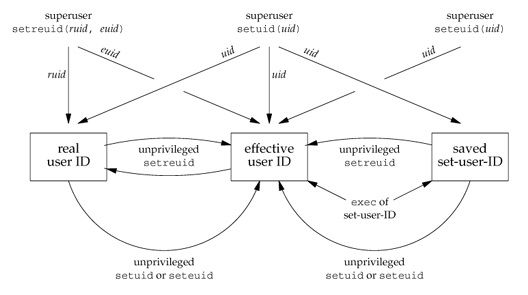
iii.uid
内核中主要有三个用户:uid(实际用户)、euid(有效用户)、suid(保存用户),可通过setuid、seteuid、setreuid系统调用实现用户切换。
setuid规则:
1.当有超级用户权限,修改uid,euid,suid为新用户
2.当没有超级用户权限,新用户id参数等于uid或suid时,修改euid为新用户
3.其它情况不允许,报EPERM错误
三个用户含义如下:
uid:实际用户,只有拥有超级用户权限的进程才能修改uid;在登录/用户切换时,login/su有超级用户权限,调用setuid设置uid,euid,suid为登录用户/切换用户;uid一般保持不变
euid:有效用户,exec时如果SETUID置位则设置成程序文件用户ID,否则euid不变。可以通过setuid设置euid为uid或suid
suid:保存用户,exec时设置成euid。
三个uid之间的关系如下图所示: