Android 常用ADB命令汇总!!! -- 持续补充
ADB 常用命令
- 1.基本命令
- 1.1.显示当前设备
- -adb devices
- 1.2.获取权限,操作Android系统文件
- 1.3.log日志
- - adb logcat
- 1.4.安装及卸载应用
- - adb install
- 1.5.截图和录制视频
- - adb shell screencap
- - adb shell screenrecord
- 2调试工具命令
- 2.1.属性配置工具
- 2.2.ps 工具
- 2.2.grep工具
- 2.2.am工具
- 2.2.pm工具
- 2.2.getevent/sendevent工具
- -adb shell getevent
- -adb shell setevent
- 2.2.dumpsys工具
1.基本命令
1.1.显示当前设备
-adb devices
ThinkPad-T470:~$ adb devices
List of devices attached
2KE0219B16014915 device
1.2.获取权限,操作Android系统文件
-
adb shell /* 进入手机文件目录 */
-
adb root /* 获取权限 */
-
adb remount
/* 将 ‘/system’ 部分置于可写入的模式,默认情况下 '/system’部分是只读模式的。这个命令只适用于已被 root 的设备。在将文件 push 到 ‘/system’ 文件夹之前,必须先输入命令 ‘adb remount’。 -
‘adb remount’ 的作用相当于 ‘adb shell mount -o rw,remount,rw /system’。 */
-
常用更新系统app三连:
-adb root
-adb remount
-adb push path/xxx.apk /system/app/
1.3.log日志
- adb logcat
- adb logcat -c /* 清除日志 */
- adb logcat -s AndroidRuntime /* Android 异常日志 用来排查闪退问题*/
- adb logcat -v threatime >test.log /* 显示日志输出的时间,实际默认显示 ; 通过 >可以将抓取的 log 输出到当前所在目录的test.log内*/
ThinkPad-T470:~$adb logcat -s AndroidRuntime
--------- beginning of crash
08-18 08:50:05.979 21785 21785 E AndroidRuntime: FATAL EXCEPTION: main
08-18 08:50:05.979 21785 21785 E AndroidRuntime: Process: com.google.process.gapps, PID: 21785
08-18 08:50:05.979 21785 21785 E AndroidRuntime: java.lang.RuntimeException: Unable to get provider com.google.android.gsf.settings.GoogleSettingsProvider: java.lang.SecurityException: You need MANAGE_USERS permission to: get the profile parent
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.app.ActivityThread.installProvider(ActivityThread.java:7905)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.app.ActivityThread.installContentProviders(ActivityThread.java:7441)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.app.ActivityThread.handleBindApplication(ActivityThread.java:7334)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.app.ActivityThread.access$2400(ActivityThread.java:308)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.app.ActivityThread$H.handleMessage(ActivityThread.java:2295)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.os.Handler.dispatchMessage(Handler.java:110)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.os.Looper.loop(Looper.java:219)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.app.ActivityThread.main(ActivityThread.java:8347)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at java.lang.reflect.Method.invoke(Native Method)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:513)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:1055)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: Caused by: java.lang.SecurityException: You need MANAGE_USERS permission to: get the profile parent
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.os.Parcel.createException(Parcel.java:2071)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.os.Parcel.readException(Parcel.java:2039)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.os.Parcel.readException(Parcel.java:1987)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.os.IUserManager$Stub$Proxy.getProfileParent(IUserManager.java:1746)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.os.UserManager.getProfileParent(UserManager.java:2605)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at com.google.android.gsf.settings.GoogleSettingsProvider.onCreate(GoogleSettingsProvider.java:153)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.content.ContentProvider.attachInfo(ContentProvider.java:2121)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.content.ContentProvider.attachInfo(ContentProvider.java:2094)
08-18 08:50:05.979 21785 21785 E AndroidRuntime: at android.app.ActivityThread.installProvider(ActivityThread.java:7900)
1.4.安装及卸载应用
- adb install
- adb install -r path/xxx.apk /* -r:强制安装,当已经安装了同包名应用时,覆盖安装 */
- adb shell pm install -r /data/local/tmp/xxx.apk /* 安装的apk来源于设备中 例:data/local/tmp目录 */
- adb shell pm uninstall -k /* -k:卸载应用且保留数据与缓存,不加的话,则全部删除 */
ThinkPad-T470:~$ adb install -r '/home/app-install.apk'
Success
ThinkPad-T470:~
1.5.截图和录制视频
- adb shell screencap
- adb shell screencap -p /sdcard/screen.png
screencap: invalid option -- -
usage: screencap [-hp] [-d display-id] [FILENAME]
-h: this message
-p: save the file as a png.
-d: specify the physical display ID to capture (default: 0)
see "dumpsys SurfaceFlinger --display-id" for valid display IDs.
If FILENAME ends with .png it will be saved as a png.
If FILENAME is not given, the results will be printed to stdout.
ThinkPad-T470:~$ adb shell screencap -p /sdcard/screen.png
ThinkPad-T470:~$ adb pull sdcard/screen.png '/home/桌面/luobo'
- adb shell screenrecord
- adb shell screenrecord --size 1920x480 /sdcard/demorecord.mp4
-!华为10.0手机不支持screenrecord,这一条,待我把adb 命令写完了,回头排查以后再更新-
2调试工具命令
2.1.属性配置工具
adb shell getprop /* 获取属性 */
adb shell setprop /* 设置属性 */
adb shell watchprops /* 观察属性 */
2.2.ps 工具
这个命令在adb 中是查看android系统的进程状态命令
usage: ps [-AadefLlnwZ] [-gG GROUP,] [-k FIELD,] [-o FIELD,] [-p PID,] [-t TTY,] [-uU USER,]
List processes.
Which processes to show (-gGuUpPt selections may be comma separated lists):
-A All -a Has terminal not session leader
-d All but session leaders -e Synonym for -A
-g In GROUPs -G In real GROUPs (before sgid)
-p PIDs (--pid) -P Parent PIDs (--ppid)
-s In session IDs -t Attached to selected TTYs
-T Show threads also -u Owned by selected USERs
-U Real USERs (before suid)
Output modifiers:
-k Sort FIELDs (-FIELD to reverse) -M Measure/pad future field widths
-n Show numeric USER and GROUP -w Wide output (don't truncate fields)
Which FIELDs to show. (-o HELP for list, default = -o PID,TTY,TIME,CMD)
-f Full listing (-o USER:12=UID,PID,PPID,C,STIME,TTY,TIME,ARGS=CMD)
-l Long listing (-o F,S,UID,PID,PPID,C,PRI,NI,ADDR,SZ,WCHAN,TTY,TIME,CMD)
-o Output FIELDs instead of defaults, each with optional :size and =title
-O Add FIELDS to defaults
-Z Include LABEL
ThinkPad-T470:~$adb shell ps -A
USER PID PPID VSZ RSS WCHAN ADDR S NAME
root 1 0 69388 2924 0 0 S init
root 2 0 0 0 0 0 S [kthreadd]
root 3 2 0 0 0 0 I [rcu_gp]
root 7 2 0 0 0 0 I [mm_percpu_wq]
root 8 2 0 0 0 0 S [ksoftirqd/0]
root 9 2 0 0 0 0 I [rcu_preempt]
root 10 2 0 0 0 0 I [rcu_sched]
root 11 2 0 0 0 0 I [rcu_bh]
root 12 2 0 0 0 0 S [migration/0]
root 14 2 0 0 0 0 S [watchdog/0]
2.2.grep工具
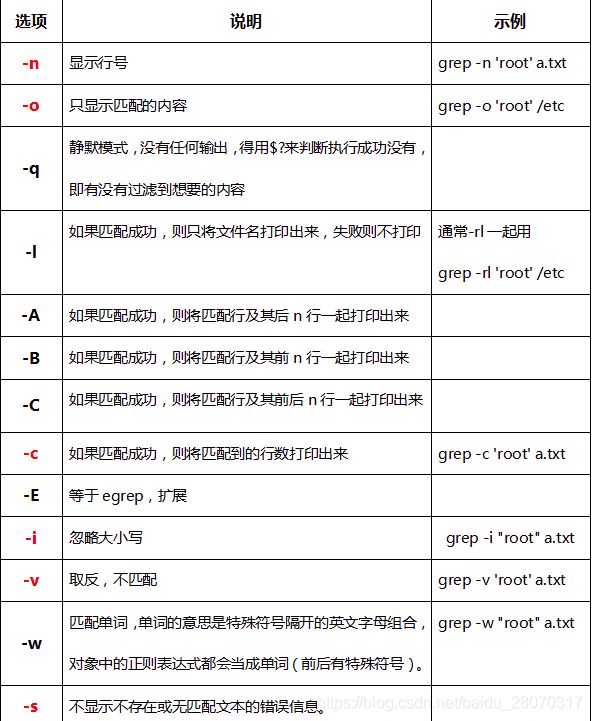
主要功能就是进行字符串数据的对比,能使用正则表达式搜索文本,并将符合用户需求的字符串打印出来。
grep全称是Global Regular Expression Print,表示全局正则表达式版本,它的使用权限是所有用户。grep在数据中查找出一个字符串时,是以整行为单位来进行数据选取的
usage: grep [-abcDEFGHhIiJLlmnOoPqRSsUVvwxZz] [-A num] [-B num] [-C[num]]
[-e pattern] [-f file] [--binary-files=value] [--color=when]
[--context[=num]] [--directories=action] [--label] [--line-buffered]
[pattern] [file ...]
这个指令是 activity manager的缩写。这个命令可以启动Activity、打开或关闭进程、发送广播等操作。
am命令格式如下
adb shell am
ThinkPad-T470:~$ adb shell ps -A |grep "camera" -i
root 99 2 0 0 0 0 S [camera_heap]
cameraserver 929 1 65476 1924 0 0 S cameraserver
media 956 1 7945912 12700 0 0 S CameraDaemon
2.2.am工具
这个指令是 activity manager的缩写。
这个命令可以启动Activity、打开或关闭进程、发送广播等操作。
am命令格式如下
adb shell am < command >
- start [options] < INTENT > :启动activity通过指定的intent参数。具体intent参数参照官方表。
- startservice [options] < INTENT> :
启动service通过指定的intent参数。具体intent跟start命令参数相同。 - force-stop < PACKAGE> : 强制停止指定的package包应用。
- kill [options] < PACKAGE>
:杀死指定package包应用进程,该命令在安全模式下杀死进程,不影响用户体验。参数选项:–user| all | - current: 指定user进程杀死,如果不指定默认为所有users。(关于USER_ID下面会介绍到)
- kill-all :杀死所有的后台进程。
- broadcast [options] < INTENT> :发送一个intent。具体intent参数参照start命令参数。参数选项:–user < USER_ID> | all |
current: 指定user进程杀死,如果不指定默认为所有users。 - instrument [options] < COMPONENT> :测试命令,不多作介绍。
- profile start < PROCESS> < FILE>:在进程中运行profile,分析结果写到里。
- profile stop < PROCESS> :停止profile。
- set-debug-app [options] < PACKAGE>:设置package包应用为debug模式。参数选项:-w|–persistent:等待进入调试模式,保留值。
- clear-debug-app :清空之前用set-debug-app命令设置的package包应用。
2.2.pm工具
列出安装包的信息,如:安装位置,系统所有的安装包等.
- adb shell pm list packages:查看已经安装的包
- adb shell pm list permissions -g -d:查看危险权限列表可以使用命令
- adb shell pm list packages -f -3:列出指定包名的APK位置
- adb shell pm path com.kp.poi :删除某个应用的所有数据(相当于全新安装)
- adb shell pm clear com.UCMobile:禁用/启用某个应用(disable/enable)
- adb shell pm disable com.android.systemui:列出硬件信息:pm list features
查看已经安装的包以及apk路径(-3:只看第三方应用; -s:只看系统应用)
-f: see their associated file.
-d: filter to only show disbled packages.
-e: filter to only show enabled packages.
-s: filter to only show system packages.
-3: filter to only show third party packages.
ThinkPad-T470:~$ adb shell pm list permissions -g -d
Dangerous Permissions:
group:com.google.android.gms.permission.CAR_INFORMATION
permission:com.google.android.gms.permission.CAR_VENDOR_EXTENSION
permission:com.google.android.gms.permission.CAR_MILEAGE
permission:com.google.android.gms.permission.CAR_FUEL
group:android.permission-group.CONTACTS
group:android.permission-group.PHONE
group:android.permission-group.CALENDAR
group:android.permission-group.CALL_LOG
2.2.getevent/sendevent工具
-adb shell getevent
输出所有event设备的基本信息
- 输出格式: 设备名: 事件type 事件code 事件value ,注意数字都是16进制的
ThinkPad-T470:~$ adb shell getevent
add device 1: /dev/input/event4
name: "huawei,ts_extra_key"
add device 2: /dev/input/event0
name: "soundtrigger_input_dev"
add device 3: /dev/input/event3
name: "huawei,ts_pen"
add device 4: /dev/input/event5
name: "fingerprint"
add device 5: /dev/input/event6
name: "hi3xxx_hi6405_card Headset Jack"
add device 6: /dev/input/event2
name: "input_mt_wrapper"
add device 7: /dev/input/event1
name: "hisi_on"
could not get driver version for /dev/input/mouse1, Not a typewriter
could not get driver version for /dev/input/mouse0, Not a typewriter
could not get driver version for /dev/input/mice, Not a typewriter
getevent: invalid option --
Usage: getevent [-t] [-n] [-s switchmask] [-S] [-v [mask]] [-d] [-p] [-i] [-l] [-q] [-c count] [-r] [device]
-t: show time stamps
-n: don't print newlines
-s: print switch states for given bits
-S: print all switch states
-v: verbosity mask (errs=1, dev=2, name=4, info=8, vers=16, pos. events=32, props=64)
-d: show HID descriptor, if available
-p: show possible events (errs, dev, name, pos. events)
-i: show all device info and possible events
-l: label event types and names in plain text
-q: quiet (clear verbosity mask)
-c: print given number of events then exit
-r: print rate events are received
通过getevent 监听一次点击事件
/dev/input/event2: 0003 0035 0000030f
/dev/input/event2: 0003 0036 00000145
/dev/input/event2: 0003 003a 0000023a
/dev/input/event2: 0003 0039 00000000
/dev/input/event2: 0003 0030 000000c0
/dev/input/event2: 0003 0031 000000a1
/dev/input/event2: 0003 0034 ffffffcd
/dev/input/event2: 0003 0038 00000002
/dev/input/event2: 0000 0002 00000000
/dev/input/event2: 0001 014a 00000001
/dev/input/event2: 0000 0000 00000000
/dev/input/event2: 0003 0035 0000030f
/dev/input/event2: 0003 0036 00000145
/dev/input/event2: 0003 003a 0000020e
/dev/input/event2: 0003 0039 00000000
/dev/input/event2: 0003 0030 000000b1
/dev/input/event2: 0003 0031 000000a1
/dev/input/event2: 0003 0034 ffffffd4
/dev/input/event2: 0003 0038 00000002
/dev/input/event2: 0000 0002 00000000
/dev/input/event2: 0000 0000 00000000
/dev/input/event2: 0000 0002 00000000
/dev/input/event2: 0001 014a 00000000
/dev/input/event2: 0000 0000 00000000
/dev/input/event2: 0003 0035 00000349
/dev/input/event2: 0003 0036 000004e0
/dev/input/event2: 0003 003a 000001c3
-adb shell setevent
usage: sendevent DEVICE TYPE CODE VALUE
Sends a Linux input event.
通过以下四条内容,可以进行音量控制,分为四步:
按下音量减->发送同步报告->抬起音量减->发送同步报告。只有发送了同步报告以后事件才能生效
adb shell sendevent /dev/input/event0 0001 0114 00000001
adb shell sendevent /dev/input/event0 0000 0000 00000000
adb shell sendevent /dev/input/event0 0001 0114 00000000
adb shell sendevent /dev/input/event0 0000 0000 00000000
2.2.dumpsys工具
观察当前运行的广播、Activity栈、服务、进程、内存信息、窗体信息、渲染信息、电池信息等
adb shell dumpsys activity /* activity栈信息 */
adb shell dumpsys activity broadcasts
adb shell dumpsys activity services
adb shell dumpsys meminfo /* 内存信息 */
adb shell dumpsys power /* 省电配置 */
adb shell dumpsys SurfaceFlinger /* 渲染信息 */
adb shell dumpsys battery /* 电池信息,【即当前电量、电池状态、电池温度等】 */
adb shell dumpsys /data/anr/traces.txt /* 查看文件内容 */
adb shell dumpsys package /* 查看包名 */
例:获取应用包名
ThinkPad-T470:~$adb shell dumpsys package | grep "ssl"
sslocal:
9dd11b4 com.youku.phone/com.youku.edu.classlist.ClassListActivity
93881c2 com.huawei.intelligent/.main.businesslogic.pending.app.TodoTripEditListActivity
93881bb com.huawei.intelligent/.main.businesslogic.pending.app.TodoTripListActivity
9443299 com.huawei.intelligent/.main.businesslogic.hmspush.ExpressPushRemoteMessageService
com.huawei.intelligent/.main.businesslogic.pending.provider.PendingProvider:
Provider{93881de com.huawei.intelligent/.main.businesslogic.pending.provider.PendingProvider}
[com.huawei.intelligent.main.businesslogic.pending.provider]:
Provider{93881de com.huawei.intelligent/.main.businesslogic.pending.provider.PendingProvider}
com.huawei.intelligent/.main.businesslogic.hmspush.ExpressPushRemoteMessageService: com.huawei.intelligent.permission.PROCESS_PUSH_MSG
