OkHttp 3.x 源码解析之Interceptor 拦截器
Tamic /
http://blog.csdn.net/sk719887916/article/details/74308343
#OkHttp拦截器原理解析
拦截器
Java里的拦截器是动态拦截Action调用的对象。它提供了一种机制可以使开发者可以定义在一个action执行的前后执行的代码,也可以在一个action执行前阻止其执行,同时也提供了一种可以提取action中可重用部分的方式。
在AOP(Aspect-Oriented Programming)中拦截器用于在某个方法或字段被访问之前,进行拦截然后在之前或之后加入某些操作。
过滤器
过滤器可以简单理解为“取你所想取”,忽视掉那些你不想要的东西;拦截器可以简单理解为“拒你所想拒”,关心你想要拒绝掉哪些东西,比如一个BBS论坛上拦截掉敏感词汇。
- 1.拦截器是基于java反射机制的,而过滤器是基于函数回调的。
- 2.过滤器依赖于servlet容器,而拦截器不依赖于servlet容器。
- 3.拦截器只对action起作用,而过滤器几乎可以对所有请求起作用。
- 4.拦截器可以访问action上下文、值栈里的对象,而过滤器不能。
- 5.在action的生命周期里,拦截器可以多起调用,而过滤器只能在容器初始化时调用一次。
Android里面过滤器大家用的已经无法再陌生了,Filter就是一个很好的列子,在清单文件注册Filter就可以过滤启动摸某个组件的Action.
Okhttp拦截器因此应运而生,处理一次网络调用的Action拦截,做修改操作。
![]()
OKHTTP INTERCEPTOR
使用
okhttp拦截器用法很简单,构建OkHttpClient时候通过.addInterceptor()就可以将拦截器加入到一次会话中。
OkHttpClient client = new OkHttpClient.Builder()
.addInterceptor(new LoggingInterceptor())
.build();
拦截器
拦截器是Okhttp一种强大的机制,可以监视,重写和重试每一次请求。下面示列了一个简单的拦截器,用于记录传出的请求和传入的响应。
class LoggingInterceptor implements Interceptor {
@Override public Response intercept(Interceptor.Chain chain) throws IOException {
Request request = chain.request();
long t1 = System.nanoTime();
logger.info(String.format("Sending request %s on %s%n%s",
request.url(), chain.connection(), request.headers()));
Response response = chain.proceed(request);
long t2 = System.nanoTime();
logger.info(String.format("Received response for %s in %.1fms%n%s",
response.request().url(), (t2 - t1) / 1e6d, response.headers()));
return response;
}
}
呼叫chain.proceed(request)是每个拦截器实现的关键部分。这个简单的方法是所有HTTP工作发生的地方,产生满足请求的响应。
拦截器可以链接。假设您同时拥有一个压缩拦截器和一个校验和拦截器:您需要确定数据是否已压缩,然后进行校验和,或校验和然后压缩。OkHttp使用列表来跟踪拦截器,拦截器按顺序调用。
应用拦截器
拦截器被注册为应用程序或网络拦截器。我们将使用LoggingInterceptor上面定义来显示差异。
注册一个应用程序通过调用拦截器addInterceptor()上OkHttpClient.Builder:
OkHttpClient client = new OkHttpClient.Builder()
.addInterceptor(new LoggingInterceptor())
.build();
Request request = new Request.Builder()
.url("http://www.publicobject.com/helloworld.txt")
.header("User-Agent", "OkHttp Example")
.build();
Response response = client.newCall(request).execute();
response.body().close();
URLhttp://www.publicobject.com/helloworld.txt重定向到https://publicobject.com/helloworld.txt,OkHttp自动跟随此重定向。我们的应用拦截器被调用一次,返回的响应chain.proceed()具有重定向的响应:
INFO: Sending request http://www.publicobject.com/helloworld.txt on null
User-Agent: OkHttp ExampleINFO: Received response for https://publicobject.com/helloworld.txt in 1179.7ms
Server: nginx/1.4.6 (Ubuntu)
Content-Type: text/plain
Content-Length: 1759
Connection: keep-alive
我们可以看到,我们被重定向是因为response.request().url()不同request.url()。两个日志语句记录两个不同的URL。
网络拦截器
注册网络拦截器是非常相似的。调用addNetworkInterceptor()而不是addInterceptor();
OkHttpClient client = new OkHttpClient.Builder()
.addNetworkInterceptor(new LoggingInterceptor())
.build();
Request request = new Request.Builder()
.url("http://www.publicobject.com/helloworld.txt")
.header("User-Agent", "OkHttp Example")
.build();
Response response = client.newCall(request).execute();
response.body().close();
当我们运行这个代码时,拦截器运行两次。一次为初始请求http://www.publicobject.com/helloworld.txt,另一个为重定向https://publicobject.com/helloworld.txt。
INFO: Sending request http://www.publicobject.com/helloworld.txt on Connection{www.publicobject.com:80, proxy=DIRECT hostAddress=54.187.32.157 cipherSuite=none protocol=http/1.1}
User-Agent: OkHttp Example
Host: www.publicobject.com
Connection: Keep-Alive
Accept-Encoding: gzip
INFO: Received response for http://www.publicobject.com/helloworld.txt in 115.6ms
Server: nginx/1.4.6 (Ubuntu)
Content-Type: text/html
Content-Length: 193
Connection: keep-alive
Location: https://publicobject.com/helloworld.txtINFO: Sending request https://publicobject.com/helloworld.txt on Connection{publicobject.com:443, proxy=DIRECT hostAddress=54.187.32.157 cipherSuite=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA protocol=http/1.1}
User-Agent: OkHttp Example
Host: publicobject.com
Connection: Keep-Alive
Accept-Encoding: gzipINFO: Received response for https://publicobject.com/helloworld.txt in 80.9ms
Server: nginx/1.4.6 (Ubuntu)
Content-Type: text/plain
Content-Length: 1759
Connection: keep-alive
网络请求还包含更多的数据,例如Accept-Encoding: gzip由OkHttp添加的标题来广播支持响应压缩。网络拦截器Chain具有非空值Connection,可用于询问用于连接到Web服务器的IP地址和TLS配置。
##在应用拦截器和网络拦截器之间如何让进行选择?
每个拦截链有相对优点。
应用拦截器
- 不需要担心中间响应,如重定向和重试。
- 总是调用一次,即使从缓存提供HTTP响应。
- 遵守应用程序的原始意图。不注意OkHttp注入的头像If-None-Match。
- 允许短路和不通话Chain.proceed()。
- 允许重试并进行多次呼叫Chain.proceed()。
网络拦截器
- 能够对重定向和重试等中间响应进行操作。
- 不调用缓存的响应来短路网络。
- 观察数据,就像通过网络传输一样。
- 访问Connection该请求。
重写请求
拦截器可以添加,删除或替换请求头。还可以转换具有一个请求的正文。例如,如果连接到已知支持它的Web服务器,则可以使用应用程序拦截器添加请求体压缩。
final class GzipRequestInterceptor implements Interceptor {
@Override public Response intercept(Interceptor.Chain chain) throws IOException {
Request originalRequest = chain.request();
if (originalRequest.body() == null || originalRequest.header ("Content-Encoding") != null) {
return chain.proceed(originalRequest);
}
Request compressedRequest = originalRequest.newBuilder()
.header("Content-Encoding", "gzip")
.method(originalRequest.method(), gzip(originalRequest.body()))
.build();
return chain.proceed(compressedRequest);
}
private RequestBody gzip(final RequestBody body) {
return new RequestBody() {
@Override public MediaType contentType() {
return body.contentType();
}
@Override public long contentLength() {
return -1;
// We don't know the compressed length in advance!
}
@Override public void writeTo(BufferedSink sink) throws IOException {
BufferedSink gzipSink = Okio.buffer(new GzipSink(sink));
body.writeTo(gzipSink);
gzipSink.close();
}
};
}
}
重写响应
对称地拦截器可以重写响应头并转换响应体。这通常比重写请求头更危险,因为他可以篡改违反了网络服务器的数据的本意!
如果在棘手的情况,并准备应对后果,重写响应标头是解决问题的有效方式。例如,可以修复服务器配置错误的Cache-Control响应头以启用更好的响应缓存:
private static final Interceptor REWRITE_CACHE_CONTROL_INTERCEPTOR = new Interceptor() {
@Override public Response intercept(Interceptor.Chain chain) throws IOException {
Response originalResponse = chain.proceed(chain.request());
return originalResponse.newBuilder()
.header("Cache-Control", "max-age=60")
.build();
}
};
通常,这种方法在补充Web服务器上的相应修复程序时效果最好!
#工作原理
1 Interceptor代码本质:
拦截器源码:包含基础的Request和Response 获取接口,并有Connection接口
public interface Interceptor {
Response intercept(Chain chain) throws IOException;
interface Chain {
Request request();
Response proceed(Request request) throws IOException;
/**
* Returns the connection the request will be executed on. This is only available in the chains
* of network interceptors; for application interceptors this is always null.
*/
@Nullable Connection connection();
}
}
2 .Connection是神马东西?
Connection是一次面向连接过程,这里包含基础的协议Protocol , Socket , Route, Handshake,
`public interface Connection {
Route route();
Socket socket();
@Nullable Handshake handshake();
Protocol protocol();
}
Handshake是ohkttp自己的握手机制,里面包括了SSL验证过程,这里不做源码分析,这里提供了基础Https的认证的基础根方法,本文不做探讨。
Interceptor怎么被调用:
发起请求
OkHttpClient mOkHttpClient = new OkHttpClient();
Request request = new Request.Builder()
.url("https://github.com/hongyangAndroid")
.build();
//new call
Call call = mOkHttpClient.newCall(request);
进行newCaLL
RealCall(OkHttpClient client, Request originalRequest, boolean forWebSocket) {
final EventListener.Factory eventListenerFactory = client.eventListenerFactory();
this.client = client;
this.originalRequest = originalRequest;
this.forWebSocket = forWebSocket;
//这里就是处理拦截器的地方!
this.retryAndFollowUpInterceptor = new RetryAndFollowUpInterceptor(client, forWebSocket);
// TODO(jwilson): this is unsafe publication and not threadsafe.
this.eventListener = eventListenerFactory.create(this);
}
处理请求拦截
@Override public Response intercept(Chain chain) throws IOException {
Request request = chain.request();
streamAllocation = new StreamAllocation(
client.connectionPool(), createAddress(request.url()), callStackTrace);
int followUpCount = 0;
Response priorResponse = null;
while (true) {
if (canceled) {
streamAllocation.release();
throw new IOException("Canceled");
}
Response response = null;
boolean releaseConnection = true;
try {
//也就是这里进行上层注入的拦截拦截
response = ((RealInterceptorChain) chain).proceed(request, streamAllocation, null, null);
releaseConnection = false;
} catch (RouteException e) {
......
continue;
} catch (IOException e) {
// An attempt to communicate with a server failed. The request may have been sent.
boolean requestSendStarted = !(e instanceof ConnectionShutdownException);
if (!recover(e, requestSendStarted, request)) throw e;
releaseConnection = false;
continue;
} finally {
// We're throwing an unchecked exception. Release any resources.
if (releaseConnection) {
streamAllocation.streamFailed(null);
streamAllocation.release();
}
}
.......
}
Response proceed()方法很简单,内部使用集合进行遍历,一个反射进行真实数据处理! 其通过内部的Response response = interceptor.intercept(next);
其实就回调到了你实现的intercept(Chain chain)的接口,一次闭环结束!
处理返回拦截
使用者都知道我们每次进行一次请求调用call.execute() ,真正的response也在这里开始,拦截器也从这方法为导火索。
Override
public Response execute() throws IOException {
synchronized (this) {
if (executed) throw new IllegalStateException("Already Executed");
executed = true;
}
captureCallStackTrace();
try {
client.dispatcher().executed(this);
//处理拦截了
Response result = getResponseWithInterceptorChain();
if (result == null) throw new IOException("Canceled");
return result;
} finally {
client.dispatcher().finished(this);
}
}
如果到这里你还未能猜出内部机制,这里也不用在介绍,通过处理请求拦截的介绍,你一也应该明白内部进行拦截器集合循环遍历,进行的具体处理。
到此明白了Interceptor的工作原理我们就可以愉快的使用他来完成一些功能了。
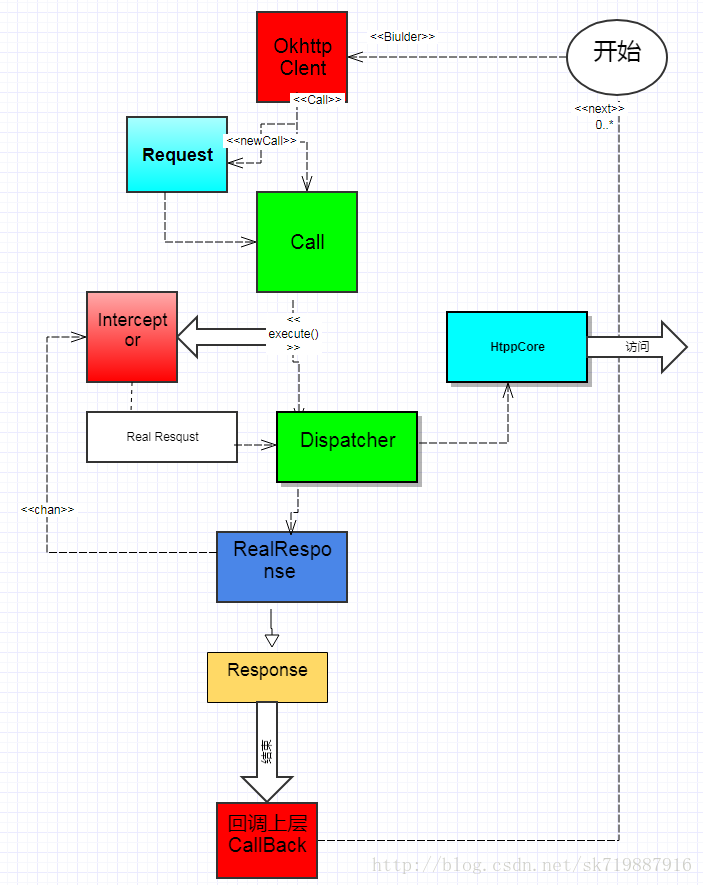
这里我我做了一个图 更能理解整个过程,只理解拦截机制,Okhttp源码流程带后续继续分析。
#更多功能
增加同步cookie
Retrofit2.0 ,OkHttp3完美同步持久Cookie实现免登录(二)
实现OKhttp的Interceptor器,用来将本地的cookie追加到http请求头中;采用rxJava的操作
public class AddCookiesInterceptor implements Interceptor {
private Context context;
private String lang;
public AddCookiesInterceptor(Context context, String lang) {
super();
this.context = context;
this.lang = lang;
}
@Override
public Response intercept(Chain chain) throws IOException {
if (chain == null)
Log.d("http", "Addchain == null");
final Request.Builder builder = chain.request().newBuilder();
SharedPreferences sharedPreferences = context.getSharedPreferences("cookie", Context.MODE_PRIVATE);
Observable.just(sharedPreferences.getString("cookie", ""))
.subscribe(new Action1() {
@Override
public void call(String cookie) {
if (cookie.contains("lang=ch")){
cookie = cookie.replace("lang=ch","lang="+lang);
}
if (cookie.contains("lang=en")){
cookie = cookie.replace("lang=en","lang="+lang);
}
//添加cookie
// Log.d("http", "AddCookiesInterceptor"+cookie);
builder.addHeader("cookie", cookie);
}
});
return chain.proceed(builder.build());
}
}
实现Interceptor器,将Http返回的cookie存储到本地
public class ReceivedCookiesInterceptor implements Interceptor {
private Context context;
SharedPreferences sharedPreferences;
public ReceivedCookiesInterceptor(Context context) {
super();
this.context = context;
sharedPreferences = context.getSharedPreferences("cookie", Context.MODE_PRIVATE);
}
@Override
public Response intercept(Chain chain) throws IOException {
if (chain == null)
Log.d("http", "Receivedchain == null");
Response originalResponse = chain.proceed(chain.request());
Log.d("http", "originalResponse" + originalResponse.toString());
if (!originalResponse.headers("set-cookie").isEmpty()) {
final StringBuffer cookieBuffer = new StringBuffer();
Observable.from(originalResponse.headers("set-cookie"))
.map(new Func1() {
@Override
public String call(String s) {
String[] cookieArray = s.split(";");
return cookieArray[0];
}
})
.subscribe(new Action1() {
@Override
public void call(String cookie) {
cookieBuffer.append(cookie).append(";");
}
});
SharedPreferences.Editor editor = sharedPreferences.edit();
editor.putString("cookie", cookieBuffer.toString());
Log.d("http", "ReceivedCookiesInterceptor" + cookieBuffer.toString());
editor.commit();
}
return originalResponse;
}
}
修改请求头
Retrofit,Okhttp对每个Request统一动态添加header和参数(五)
okHttpClient.interceptors().add(new Interceptor() {
@Override
public Response intercept(Interceptor.Chain chain) throws IOException {
Request original = chain.request();
// Request customization: add request headers
Request.Builder requestBuilder = original.newBuilder()
.addHeader("header-key", "value1")
.addHeader("header-key", "value2");
Request request = requestBuilder.build();
return chain.proceed(request);
}
});
实现缓存
Rxjava +Retrofit 你需要掌握的几个技巧,Retrofit缓存,
兼容的库
OkHttp的拦截器需要OkHttp 2.2或以上版本。但是是,拦截器不支持OkUrlFactory,或者依赖Okhttp的其他库,包括Retrofit≤1.8和 Picasso≤2.4。
参考资料
Okhttp官方GitHub Wiki以及APi文档
Tamic /
http://blog.csdn.net/sk719887916/article/details/74308343
第一时间获取技术文章请关注微信公众号!
![]()