信息说明
笔者k8s环境是v1.16版本,Jenkins以pod形式在kube-ops的命名空间中运行,在通过动态Jenkins slave实现CI/CD时,通过Jenkinsfile自定义pod模板信息,在Jenkins slave中执行kubectl命令时,出现权限不够的报错。
经过笔者多次调试,出现不同的权限报错信息,如下:
### 1
+ kubectl get pods
Error from server (Forbidden): pods is forbidden: User "system:serviceaccount:kube-ops:default" cannot list resource "pods" in API group "" in the namespace "kube-ops"
### 2
Error from server (Forbidden): pods is forbidden: User "system:serviceaccount:kube-ops:default" cannot list resource "pods" in API group "" in the namespace "kube-ops"
问题解决
笔者之前在Jenkins的系统配置里添加过kubernets的pod模板信息,能正常执行kubectl命令,但是将其整合到自定义的Jenkinsfile文件中,便出现此报错。
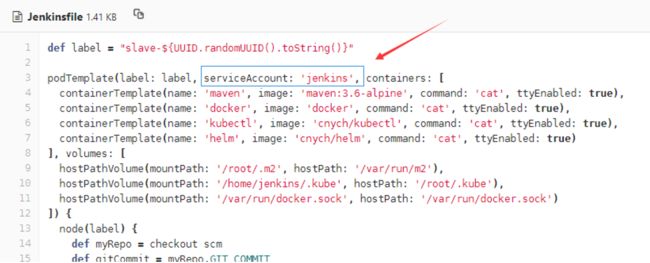
个人根据原有的页面pod配置和Jenkinsfile中的pod配置对比,发现前者比后者多了项 serverAccout 的配置,故我试着在Jenkinsfile的podTemplate中添加 serverAccout,如图:
因为在不同的kubernets集群中,jenkins的rbac权限可能不同,故有些人加了 serviceAccount: 'jenkins' 也没解决问题,究其原因是 jenkins 的rbac权限配置未达到执行kubectl命令的要求,故提供下述yaml文件,并在k8s中应用即可。
# cat rbac-jenkins.yaml
apiVersion: v1 kind: ServiceAccount metadata: name: jenkins namespace: kube-ops --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1beta1 metadata: name: jenkins rules: - apiGroups: ["extensions", "apps"] resources: ["deployments"] verbs: ["create", "delete", "get", "list", "watch", "patch", "update"] - apiGroups: [""] resources: ["services"] verbs: ["create", "delete", "get", "list", "watch", "patch", "update"] - apiGroups: [""] resources: ["pods"] verbs: ["create","delete","get","list","patch","update","watch"] - apiGroups: [""] resources: ["pods/exec"] verbs: ["create","delete","get","list","patch","update","watch"] - apiGroups: [""] resources: ["pods/log"] verbs: ["get","list","watch"] - apiGroups: [""] resources: ["secrets"] verbs: ["get"] - apiGroups: [""] resources: ["events"] verbs: ["get","list","watch"] --- apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: jenkins namespace: kube-ops roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: jenkins subjects: - kind: ServiceAccount name: jenkins namespace: kube-ops
# kubectl apply -f rbac-jenkins.yaml
# 添加完成后触发构建,显示正常,如图:
参考文档
https://github.com/jenkinsci/kubernetes-plugin/blob/master/README.md